IEEE 802.1x authentication is a standard for port-based network access control. It essentially requires devices to authenticate themselves before gaining access to network resources. This standard is versatile, working seamlessly with both wired Ethernet networks and wireless networks. Incorporating IEEE 802.1x into your network architecture strengthens security and simplifies network management. It validates users and devices, providing a safer environment for both data and applications. How awesome is that?
This article examines 802.1x authentication in depth. It defines its security and outlines how it is implemented in a wired and wireless network.
What is IEEE 802.1x Authentication?
IEEE 802.1x is a standard established by the Institute of Electrical and Electronics Engineers (IEEE) for port network access control, primarily designed to enhance security in both wired and wireless networks. It operates on verifying user credentials before granting network access, ensuring that only authorized devices can connect.
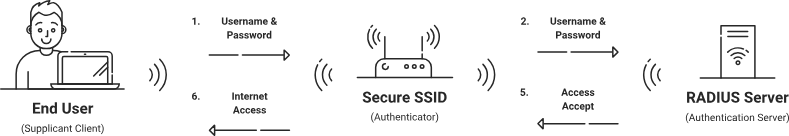
802.1x authentication involves a client device, the authenticator, and the authentication server (typically a RADIUS server). The client device initiates the authentication process by sending credentials to the authenticator, which acts as an intermediary, forwarding these credentials to authentication servers. Authentication servers evaluate the credentials and determine whether to grant access. This entire process is facilitated through the Extensible Authentication Protocol (EAP), which allows for multiple authentication methods like EAP-TLS, PEAP, and EAP-TTLS. IEEE 802.1x is critical in ensuring network security by preventing unauthorized access, thereby protecting sensitive data from potential breaches. Its implementation is a strategic approach to compliance with security standards and enhances overall network integrity.
How Secure is 802.1X?
When used correctly, it is the golden standard of network authentication security. It can prevent over-the-air credential theft attacks like Man-in-the-Middle attacks and Evil Twin proxies. It is much more secure than pre-shared key networks, typically used in personal networks.
However, 802.1X security can vary greatly depending on two factors. The first variable occurs if end users cannot configure their devices manually. The configuration process requires high-level IT knowledge to understand; if one step is incorrect, they are left vulnerable to credential theft. We highly recommend using dedicated 802.1X onboarding software instead.
The second variable depends on whether an organization uses credential-based or certificate-based authentication. Certificate-based EAP-TLS significantly reduces an organization’s risk for credential theft and is the most secure way to use 802.1X. Not only does it stop credentials from being sent over the air where they can be easily stolen, but it forces users to go through an enrollment/onboarding process that ensures their devices are configured correctly.
Components of 802.1x Authentication
IEEE 802.1x authentication is intricately designed to ensure that only authorized devices gain access to network resources. It leverages a trio of critical components, each playing a specialized role in the authentication and working in unison to maintain network security and integrity. Understanding these components is essential for implementing an effective and secure network authentication system.
The Supplicant (Client Device)
The supplicant is the client device attempting to connect to the network. This could be any device, such as a laptop, smartphone, or tablet. The supplicant initiates the 802.1x authentication by sending its credentials to the authenticator. It acts as the requesting entity, much like a visitor seeking permission to enter a secured facility.
The Authenticator (Network Switch or Access Point)
The authenticator serves as the intermediary between the supplicant and the authentication server. It is typically a network switch or access point that controls the port-based network access. The authenticator receives the credentials from the supplicant and forwards them to the authentication server for validation. Upon receiving a response from the authentication server, it either grants or denies access to the supplicant based on the validation outcome.
The Authentication Server
The authentication server is the decision-making authority in the 802.1x authentication. It validates the credentials forwarded by the authenticator and determines whether to allow or deny access. The authentication server is critical in verifying user details against a database, ensuring that only legitimate users can connect to the network. Its configuration and management are vital for maintaining a secure and reliable network authentication system.
How Does 802.1x Authentication Work?
The 802.1x authentication process starts when a supplicant (client device) attempts to connect to the network, sending an initial request to the authenticator. The authenticator, a network switch or access point, responds by placing the port in an “unauthorized” state. This means no data traffic, except for 802.1x frames, is permitted until the process is completed. This step acts as the first line of defense, ensuring that only devices undergoing authentication can proceed.
Extensible Authentication Protocol (EAP) Over LAN (EAPOL) Communication
Once the port is in an unauthorized state, communication between the supplicant and the authenticator happens using the EAPOL. EAPOL is a critical part of the 802.1x framework, enabling secure transmission of authentication information. The supplicant sends EAP-Start messages, which the authenticator forwards to the authentication server. This communication ensures that credentials are securely transmitted for validation.
Role of the Authenticator in the Authentication
The authenticator acts as the gatekeeper and intermediary in the 802.1x authentication. It forwards EAP messages between the supplicant and the authentication server. Upon receiving the credentials from the supplicant, the authenticator wraps them in a RADIUS packet and forwards them to the authentication server for validation. If the response from the server is positive, the authenticator transitions the port to an “authorized” state, allowing the supplicant to access the network. Conversely, if the validation fails, the authenticator keeps the port in the unauthorized state, denying access.
Authentication Methods Supported by IEEE 802.1x
Authentication methods supported by IEEE 802.1x include:
| EAP-TLS | EAP-Transport Layer Security (EAP-TLS) is one of the most secure authentication methods supported by 802.1x. It uses certificates for mutual authentication between the client and the server, ensuring a high level of security. The process involves the exchange of digital certificates, creating a secure and trusted communication channel. |
| PEAP | PEAP involves encapsulating EAP within an encrypted and authenticated Transport Layer Security (TLS) tunnel. This method enhances security by protecting the EAP exchange within the tunnel, thus shielding it from potential eavesdropping or tampering. |
| EAP-TTLS | EAP – Tunneled Transport Layer Security (EAP-TTLS) provides flexibility by allowing a secure tunnel to carry other authentication protocols. This authentication method supports additional inner authentication methods, making it a versatile option for various network environments. |
The Authentication Server: The Heart of IEEE 802.1x Auth
The authentication server is the cornerstone of the 802.1x authentication framework. Typically implemented as a RADIUS server, it acts as the decision-making authority that handles the validation of user details. The authentication server processes authentication requests from authenticators (network switches or access points), determining whether to grant or deny access based on the credentials presented. It ensures that only legitimate users can access the network, thereby critical to maintaining network security.
How to Configure a RADIUS Server for 802.1x
Configuring a RADIUS server for 802.1x authentication involves several crucial steps to ensure secure, reliable, and efficient operations. The steps include:
- Install RADIUS Software: Download and install RADIUS server software on a dedicated server. Popular options include FreeRADIUS and Microsoft NPS.
- Integrate with User Directory: Connect the server to an Active Directory (AD) or other user databases to manage user accounts and credentials.
- Configure Network Policies: Define policies that determine the conditions under which access to the network is granted. This includes setting up EAP methods and user group policies.
- Set Up Server Certificates: Install server certificates to enable secure communication between the server and the authenticators.
Why is Server Certificate Validation Important?
Certificate validation is a critical aspect of the 802.1x authentication. It ensures that the communication between the supplicant (client device) and the authentication server is secure and authentic. By validating server certificates, the client device can confirm that it communicates with a legitimate RADIUS server, not an imposter. This process involves verifying the server’s digital certificate and adding an extra layer of security to prevent man-in-the-middle attacks.
How Does The Server Handle Authentication Requests?
The RADIUS server handles incoming authentication requests from authenticators by following these steps:
- Receive Request: The server receives an authentication request encapsulated in a RADIUS message.
- Validate Credentials: It checks the credentials against its user database or directory service (e.g., Active Directory).
- Response Generation: Based on the credentials’ validity, the server generates an “Access-Accept” or “Access-Reject” response.
- Send Response: The RADIUS server sends the response back to the authenticator, which either grants or denies access to the supplicant based on the server’s decision. The efficiency and accuracy of this process are critical for maintaining robust network security and seamless user experiences.
How to Implement 802.1x in a Wired Network
To successfully implement 802.1x authentication in a wired network, ensure your infrastructure supports the 802.1x protocol. Verify that your network switches and routers are compatible and have the necessary firmware updates. This preparation phase is essential to avoid technical hiccups later on and ensure smooth integration and operation.
Configuring Network Switches for 802.1x
Configure your network switch by:
a) Setting up the Supplicant
Start by configuring the supplicant, which is the client device. Ensure that the operating system and network adapter support 802.1x authentication. For instance, navigate to the network adapter settings in a Windows environment under the “Authentication” tab and enable 802.1x. Choose the appropriate EAP authentication method, such as EAP-TLS, to ensure robust security.
b) Defining Authenticator Roles
Next, configure the network switches to act as authenticators. This involves enabling 802.1x authentication on individual switch ports. Follow these steps:
- Access Switch Management Console: Log in to the switch’s management interface.
- Enable 802.1x Authentication: Use commands like `dot1x system-auth-control` on Cisco switches to enable 802.1x globally.
- Configure Ports: Enable 802.1x on specific ports using commands such as `interface GigabitEthernet0/1` followed by `dot1x port-control auto`.
- Specify RADIUS Server Details: Enter the server’s IP address, shared secret, and port numbers.
- Set Timeouts and Retries: Define parameters for how long the switch will wait for responses and how many retries will be attempted.
c) Ensuring Communication with the RADIUS Server
Confirm that no firewalls or network configurations block communication between switches and servers. Successful communication is critical for authentication. Ensure that the necessary ports (usually 1812 for authentication and 1813 for accounting) are open and properly routed.
Testing and Verification
After configuring the network, thoroughly test the setup to ensure it functions correctly. Tests can be conducted using various client devices to verify that they can connect and authenticate successfully. Monitor logs from the RADIUS servers and the switches to identify and troubleshoot any issues. Utilize diagnostic tools to ensure that all components are communicating as intended. This testing phase is crucial to confirm that the 802.1x implementation is robust and operational, securing your wired network effectively.
How to Implement IEEE 802.1x in a Wireless Network
To implement 802.1x authentication in a wireless network, start by ensuring that your wireless access points (APs) support the 802.1x protocol. Check for the latest firmware updates and compatibility with 802.1x features. This step is crucial to avoid interoperability issues and ensure smooth implementation. However, some client devices, such as wireless printers, cannot act as an 802.1X supplicant. You might want to allow them access to an 802.1X-secured network anyway. This can be done using a MAC authentication bypass (MAB). With MAB, your authentication server can authenticate a client device using its MAC address rather than via the EAPOL authentication process.
Configure Wireless Access Points for 802.1x
a) Setting up the Supplicant
Configure the supplicant on client devices just as you would in a wired network scenario. Ensure that the wireless network adapter and operating system support 802.1x authentication. For example, select the wireless connection on a Windows device on “Network and Sharing Center” and enable 802.1x under the wireless security settings.
b) Define Authenticator Roles
Next, configure your wireless access points to act as authenticators. This involves setting up the APs to handle 802.1x authentication and communicating with the RADIUS server. Follow these steps:
- Access AP Management Console: Log in to the access point’s admin interface.
- Enable 802.1x Authentication: Navigate to the security settings and enable 802.1x authentication, often found under “WPA2-Enterprise” or similar configurations.
- Specify RADIUS Server Details: Enter the server’s IP address, shared secret, and port numbers.
- Configure SSID: Assign the 802.1x authentication to the SSID (Service Set Identifier) that users will connect to, ensuring that it is configured for enterprise security.
- Set Timeouts and Retries: Define the necessary timeouts and retry limits to handle authentication traffic efficiently.
c) Ensuring Communication with the RADIUS Server
As with wired networks, ensure unimpeded communication between the access points and the server. Verify that no firewalls or network configurations block the required ports (e.g., 1812 for authentication). This step is essential to ensure that authentication packets can travel freely and securely between devices.
Testing and Verification
Thorough testing is crucial to confirm the correct functioning of the 802.1x setup. Perform the following checks:
- Attempt Connections: Connect multiple client devices to the wireless network to verify that they authenticate without issues.
- Monitor Logs: Check the logs on the access points and the RADIUS server to identify any authentication errors or failures.
- Use Diagnostic Tools: Utilize network diagnostic tools to ensure smooth communication between all components.
Testing ensures that the 802.1x implementation is both secure and operational, providing a robust defense for your wireless network.
Additional Security Measures and Considerations
In addition to 802.1x authentication, leveraging protocols like the Temporal Key Integrity Protocol (TKIP) can enhance wireless network security. Segmenting network traffic using a Virtual Local Area Network (VLAN) for better control is also beneficial. Implement an accounting server to log access events and ensure all operating systems on client devices are up-to-date. Furthermore, consider using MAC address filtering as an added layer of security, though it should not be the sole reliance.
Simplifying 802.1x Authentication with SecureW2
SecureW2’s Cloud RADIUS server is a robust and scalable option that eliminates the need for on-premise hardware and simplifies network authentication management. SecureW2’s JoinNow Connector PKI seamlessly integrates Public Key Infrastructure (PKI) into your existing environment, ensuring secure certificate-based authentication without the usual headaches.
One of the standout features of SecureW2 is our JoinNow MultiOS, a versatile tool essential for organizations dealing with unmanaged devices. With JoinNow MultiOS, managing a diverse range of operating systems becomes straightforward, enabling secure network access across various devices without compromising security. You can effortlessly configure and deploy 802.1x settings, ensuring compatibility and security across different platforms.
Incorporating SecureW2’s solutions can significantly enhance your network security posture. Our Cloud RADIUS server ensures reliable and efficient handling of authentication requests, while JoinNow Connector PKI facilitates the adoption of certificate-based authentication. Additionally, JoinNow MultiOS addresses the challenge of unmanaged devices, making SecureW2 a comprehensive choice for organizations aiming to implement or upgrade their 802.1x authentication framework.
Click here to see our pricing.
