Network traffic monitoring is essential for IT professionals to protect the company’s environment against potential vulnerabilities. It tracks data movement across different networks, ensures the network operates efficiently and identifies performance issues. Reliable network traffic monitoring improves network performance, increases security, and provides valuable insights for network management.
When networks grow, network monitoring becomes very challenging. Network engineers must use several devices, applications, and protocols to generate vast data. Without proper network monitoring, network performance may degrade, impacting an organization’s productivity.
This article will provide a comprehensive guide to network traffic monitoring. We’ll explore fundamental concepts, discuss essential tools, and share the best tips for monitoring network traffic effectively. Additionally, we’ll highlight the benefits of using a Cloud RADIUS service for enhanced network monitoring.
What is Network Traffic Monitoring?
Monitoring network traffic enables you to collect, evaluate, and report on network activity. It also allows you to troubleshoot and optimize network performance issues. Network monitoring provides insights into various network aspects, such as bandwidth usage, traffic patterns, and the behavior of different network devices. It helps maintain an efficient, secure, and reliable network environment.
Key Concepts in Network Traffic Monitoring
The following are some key concepts that are used in network monitoring:
Bandwidth Usage
Monitoring bandwidth usage allows IT administrators to see how much data traffic is transmitted over the network at a specific time. This information helps identify the overuse or underuse of network resources. Network administrators can analyze bandwidth consumption to make informed decisions about capacity planning and resource allocation.
Traffic Patterns
Analyzing traffic patterns allows you to examine data flow across the network to identify trends and anomalies. This can include peak usage times, commonly accessed resources, and the typical behavior of networked devices. Understanding traffic patterns helps optimize network performance and anticipate potential issues.
Anomalies Detection
Anomalies in network traffic highlight various issues, such as security breaches, malfunctioning devices, or misconfigured network settings. It involves identifying unusual patterns or behaviors that deviate from the standard. IT professionals can prevent security threats and maintain network stability by addressing anomalies.
How Do I Monitor the Traffic in My Network?
As discussed in the previous section, monitoring network traffic in your environment is very important. You can do it by implementing the following methods:
Select Data Source
To effectively explore your network, you should have clear data visibility. There are 3 main data sources that you can consider for monitoring network traffic:
- Flow Data: This common data source enables you to monitor bandwidth and network packets.
- Packet Data: Extracted from network packets, data packets allow you to monitor how users utilize your services and be vigilant for any suspicious activity.
- Wi-Fi Data: This data source utilizes high-speed 802.11ac WiFi to monitor networks, allowing you to analyze Wi-Fi traffic effectively.
Identify Applications and Devices for Network Monitoring
Identify the applications and devices you want to monitor, such as network switches, routers, Wi-Fi routers, client-end devices, etc. You can obtain the IP addresses of network devices and provide them to the network monitoring tools to identify them, along with inbound and outbound traffic.
Visualize Critical Metrics
You can integrate third-party dashboards to visualize key metrics such as security events, bandwidth, latency, certificate expiry, etc. Data visualization allows you to detect and investigate your network issues efficiently.
Analyze Network Traffic Data
You can configure an intelligent alerting system to analyze your data, which impacts its integrity, performance, and overall network health. You can further provide those analytics to management or key stakeholders for decision-making and to enhance the organization’s operational activities.

Figure: Thanks to freepik
Choosing the Right Network Traffic Monitoring Tool
The right network traffic monitoring tool will help you to provide real-time insights, detailed analytics, and automated alerts. This helps in managing network performance and security. When choosing network monitoring tools, you can consider factors such as ease of use, clear dashboards, data visualization, scalability, and the specific needs of your network.
The following are some of the best network monitoring tools used to monitor network traffic:
Wireshark
Wireshark is an open-source network analyzer and one of the best tools for network monitoring. It quickly detects network anomalies and allows network administrators to troubleshoot them. It captures packets in real-time and displays them in a readable format.
Some of the key features of the Wireshark protocol analyzer are detailed packet analysis, packet color-coding for quick identification, and real-time and offline analysis.
Nagios
Nagios is another open-source network monitoring tool that provides network tracking and performance capabilities. Its modular architecture allows for customization and scalability to meet diverse network monitoring needs.
Some key features of Nagios are monitoring of network services and host resources, customizable alerts, and detailed reporting.
Implementing RADIUS Servers for Network Monitoring
RADIUS (Remote Authentication Dial-In User Service) servers are essential for network security and management. They perform three main functions: authentication, authorization, and accounting (AAA). By verifying user identities, controlling network access for resources, and tracking user activities, RADIUS servers provide a comprehensive approach to network monitoring.
RADIUS servers ensure that only authorized entities gain access. Once the users and devices are authenticated, the RADIUS server determines what resources can be accessed. RADIUS servers log user activities, including login times, duration of access, and data usage. This information is crucial for monitoring network usage, detecting anomalies, and conducting cybersecurity audits.
SecureW2’s Cloud RADIUS enhances network traffic monitoring by leveraging certificate-based authentication. This platform simplifies network access policies, ensuring that only trusted network devices and users can connect. By integrating SecureW2’s Cloud RADIUS, organizations can improve their network security posture and gain detailed insights into network activities.
Best Tips for Network Traffic Monitoring
The following are some best practices to enhance the network traffic monitoring process:
Clear Network Policies through NAC Solutions
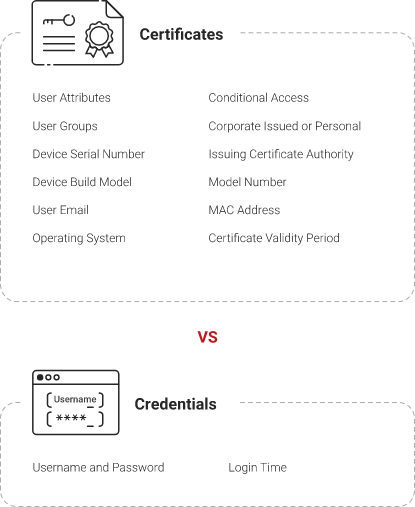
Network Access Control (NAC) solutions help you monitor your network by increasing visibility and setting Network Access Control policies through policy enforcement on users and devices. Digital (X.509) certificates enable policy-based network access control since they integrate with RADIUS servers and access control systems. Digital certificates contain all pertinent device and user information that authenticates them to the Cloud RADIUS based on the access policies of the identity provider.
A clearly defined Network Access Policy lets you segregate users based on departments and groups into respective VLAN segments. VLAN segmentation ensures that only authorized users and devices can access specific applications.
Regularly Analyze Traffic Patterns
Regularly analyze network traffic patterns to identify the behavior of network traffic and its detailed network traffic analysis. With the help of automated analysis tools, you can find real-time insights about abnormal traffic behavior.
Use Event Logs for Network Monitoring
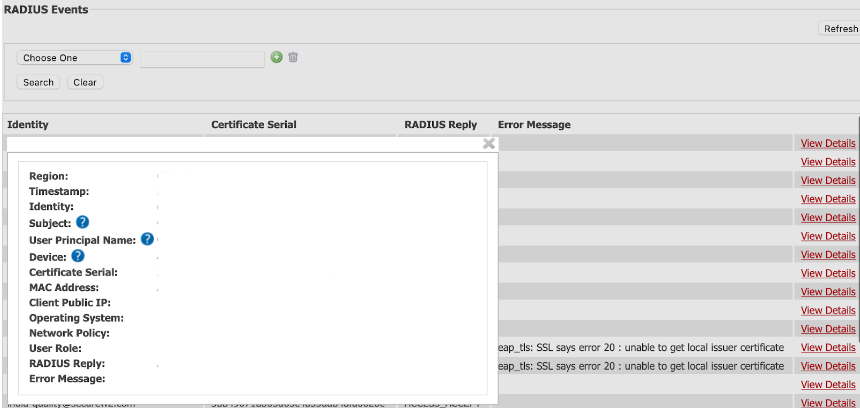
Event logs help you track network activities and diagnose any issues. You can collect and analyze user and device logs to thoroughly understand network behavior. SecureW2’s Cloud RADIUS event logs provide detailed information from a device certificate, like the device location, time of authentication, MAC address, username, email, etc. Administrators can also use this information to troubleshoot when there are connectivity issues.
Monitor Network Performance and Bandwidth Utilization
Monitoring network bandwidth utilization allows you to optimize network performance and prevent congestion. High bandwidth usage at specific time intervals can indicate potential network problems. Specific tools can monitor network bandwidth utilization and gain real-time insights into bandwidth consumption.

Set Up Alerts
Configure alerts to monitor unusual network activities, such as traffic spikes, failed login attempts, and unauthorized access. Prioritize alerts based on severity to take timely action.
Implement PKI and Digital Certificates
To enhance network security, you can use Public Key Infrastructure (PKI) and digital certificates. Certificates ensure that only trusted devices access the network and provide secure authentication. SecureW2’s Cloud RADIUS allows you to authenticate your clients using digital certificates.
Protocols for Network Traffic Monitoring
With network monitoring protocols, you can fulfill various network monitoring needs. Here are some network traffic monitoring protocols that we will briefly discuss:
Figure: Thanks to Kentik
SNMP
Simple Network Management Protocol (SNMP) is the most widely used network protocol for monitoring and managing connected devices. It communicates over UDP and enables the identification of connected devices and tracking of changes in real time using SNMP messages.
SNMP allows for active and passive monitoring by sharing system state and configuration data from a device’s management information base (MIB). This includes gathering network performance data such as bandwidth, memory allocation, and CPU usage for real-time assessments.
ICMP
The Internet Control Message Protocol (ICMP) sends error messages regarding data transmission. It helps resolve issues restricting data packets from the source to their destination. Ping and Traceroute use ICMP to detect connectivity and network path issues.
Ping sends ICMP echo request messages to determine a device’s reachability, whereas Traceroute maps the route packets take to reach their destination.
Syslog
Syslog enables connected devices to transmit event data to a central logging server, allowing real-time visibility to help identify potential problems.
It consolidates log data from multiple devices, including network switches, firewalls, client devices, and servers, making it easier for network administrators to track and evaluate events.
If you have a Syslog server, numerous other security platforms can integrate with it. Cloud RADIUS, for example, can integrate with both SIEM and Syslog services to push its event logs to an easily accessible place for administrators.
CDP
Cisco Discovery Protocol (CDP) enables network devices to discover and learn about one another without requiring manual setup. CDP messages include IP addresses, device IDs, and connected interfaces, summarizing the network architecture and each device’s role.
This protocol is especially helpful in complicated networks that contain Cisco devices. It automates the device discovery and connections.
NetFlow
NetFlow creates flow records, which are then exported to a flow collector for analysis. This supplies data on network throughput, packet loss, and traffic congestion. NetFlow supports a variety of monitoring scenarios, including DDoS detection and network troubleshooting.
Analyzing NetFlow data allows network administrators to visualize incoming and outgoing traffic, identify bottlenecks, and address network issues more efficiently.
Streaming Telemetry
Streaming telemetry is an emerging method of network monitoring. It operates on a publish/subscribe model, in which network devices constantly transmit data according to particular events. Data travels in organized formats such as JSON or XML using transport protocols such as gRPC, which produces real-time efficiency.
Streaming telemetry suits high-performance environments like large enterprises and data centers, where fast issue resolution is essential.
Detailed and Granular Network Traffic Monitoring with Cloud RADIUS Security
SecureW2 Cloud RADIUS offers a comprehensive solution for network traffic monitoring through its advanced authentication, authorization, and accounting capabilities. By leveraging certificate-based authentication, Cloud RADIUS ensures that only trusted devices and users can access the network.
SecureW2’s Cloud RADIUS provides detailed event logs that give information on every login attempt, whether successful or failed attempts. As an IT administrator, you can filter logs to know the exact error and troubleshoot faster. Event logs are essential to modern network security as they allow you to be vigilant and facilitate efficient network monitoring. Our CloudRADIUS also lets you export data to an SIEM provider and Syslog servers and monitor connectivity issues with real-time intelligence.
Implementing Cloud RADIUS enhances network security and operational efficiency. Organizations benefit from secure authentication, detailed traffic monitoring, and streamlined policy enforcement. For example, network administrators can quickly detect anomalies and maintain a secure network environment using Cloud RADIUS.
To learn more about SecureW2 Cloud RADIUS, visit Cloud RADIUS.

