When organizations establish their IT infrastructure, it’s essential to protect it, including network-connected devices and wired and wireless access points. Printers often fly under the radar among these devices regarding security measures. However, these printers can be vulnerable if not properly secured. They handle sensitive documents and communicate with the network, making them potential cyberattack entry points. Here’s where the IEEE 802.1x authentication system works.
IEEE 802.1x authentication is a powerful network access control system designed to improve the security of wired and wireless networks. It ensures that network access is granted only to authorized devices. This protocol plays a vital role in enhancing the security of networked devices, including network printers.
In this article, we’ll walk you through the configuration process of 802.1x authentication for printers and ensure the security of your wired and wireless networks. We’ll also review the high level of 802.1x authentication, its components, and a step-by-step guide for configuring your printers using this advanced security protocol.
What is 802.1x Authentication?
IEEE 802.1x authentication is a network access control protocol that ensures the security of wired and wireless network connections by requiring network devices to authenticate themselves before granting access. This protocol was initially designed to secure wireless networks but now works for wired and wireless connections.
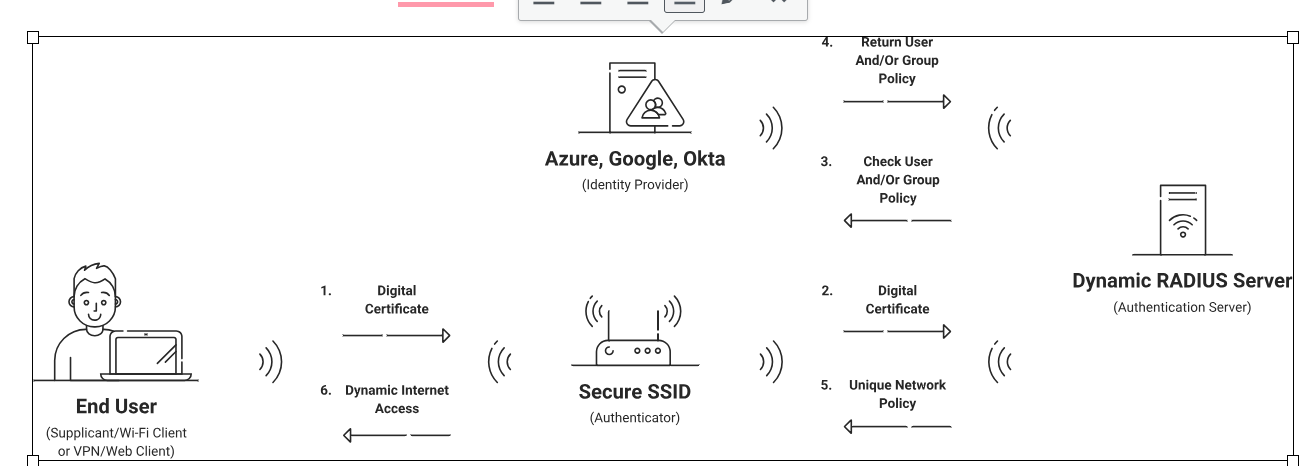
How 802.1x Authentication Works?
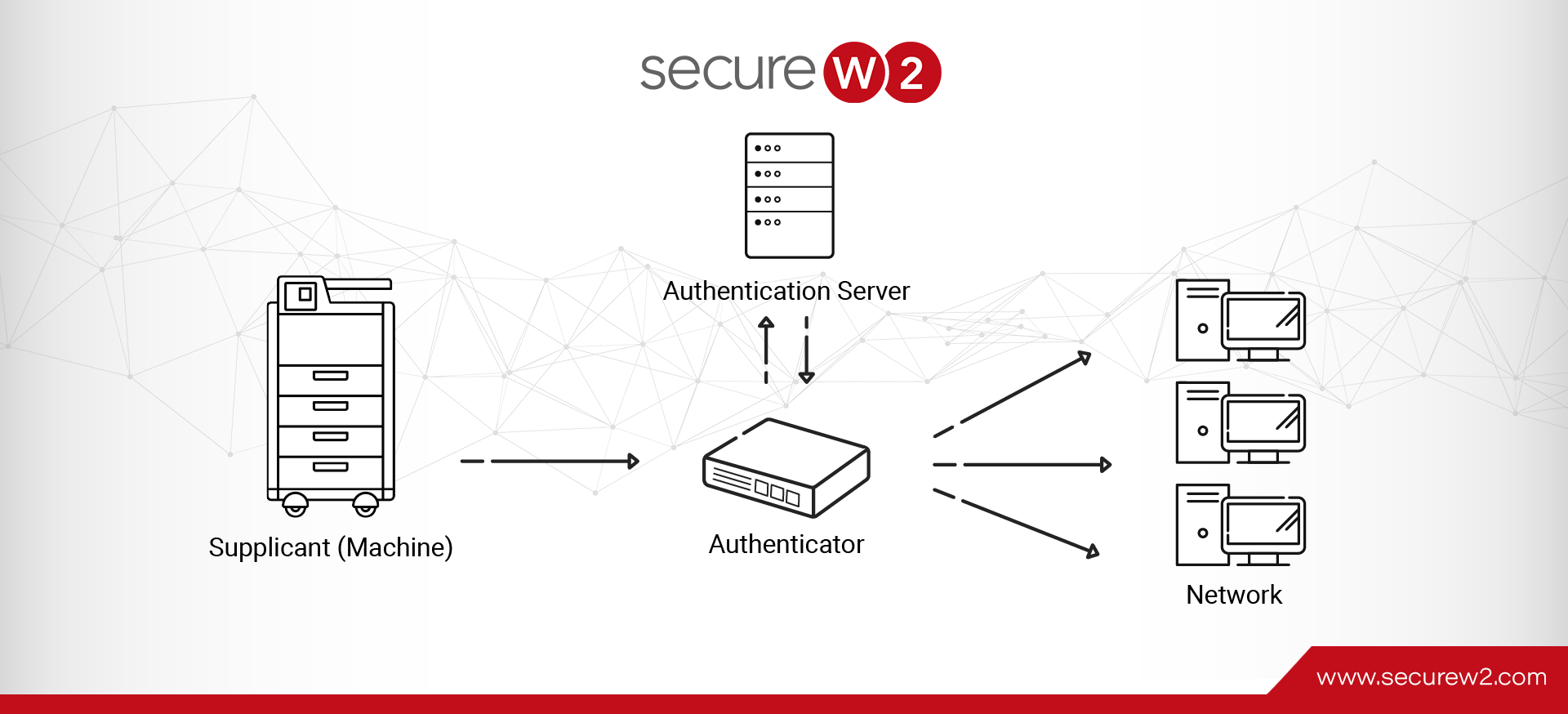
Unlike a simple password system, 802.1x uses a centralized server to verify the identity of each network device that wants to connect. This server, called the RADIUS server, is the authority for granting or denying network access.
Understanding the critical components of 802.1x authentication is essential for successfully implementing it. The key elements of the protocol are:
- Supplicant: The supplicant is the network device that requests network access. In our case, it’d be a network printer. The supplicant or a network printer should have 802.1x capabilities and be configured to provide the necessary credentials for the authentication process.
- Authenticator: The authenticator is a networking device, such as a wireless access point or a network switch, that controls network access. It acts as an intermediary between the supplicant and the authentication server.
- Authentication Server: The RADIUS server typically responds to verify the login details supplied by the supplicant. It maintains a database of authorized users and devices for granting or denying network access.
By working together, these components establish a reliable and effective system for managing network access for devices and ensuring that only authorized devices can connect.
Why Use 802.1x Authentication for Printers?
Implementing the IEEE 802.1x authentication process for printers provides several benefits in network security, including:
- Improved Security: Unprotected printers can act as gateways for unauthorized intrusion. IEEE 802.1x is a security measure that prevents unauthorized individuals from accessing your network. This helps protect uninterrupted printing and sensitive data.
- Prevent Against Cyber Threats: Unsecured printers can allow unauthorized users to infiltrate your network. 802.1x authentication system guarantees that only devices with proper authorization can establish a connection. This enhances the privacy and reliability of important information transmitted through printers.
- Enhanced Data Encryption: Many 802.1x implementations support advanced encryption protocols that encrypt data between the printer and the network. This encryption prevents eavesdropping and data theft.
- Centralized Management: The authentication server centrally stores credentials and access permissions, eliminating the need to configure individual printers with distinct passwords. This improves overall control and maintains consistent security for printers in your environment.
- Compliance: Businesses comply with GDPR, HIPAA, and PCI-DSS network security and data protection regulations. 802.1x authentication helps organizations comply with these regulations by ensuring only devices with permission can access their networks.
- Consistent Security Policies: You can apply consistent security policies with centralized control to all printers on your network. It ensures that all devices follow the same security standards, reducing the possibility of configuration errors and vulnerabilities.
Implementing 802.1x printer authentication improves network security and ensures regulatory compliance. This robust security protocol helps protect against unauthorized access, supports centralized management, and allows for more efficient network operations. It is an essential component of a secure and dependable IT infrastructure.
Benefits of 802.1x Authentication for Printers
Implementing 802.1x printer authentication offers several advantages, such as increasing network security and operational efficiency. Here are some of the benefits including:
Enhanced Security
802.1x printers need to authenticate before getting access to the network. This feature protects critical data that network printers can send or save.
If 802.1x authentication isn’t adequately protected, it can be a potential cyberattack gateway. By implementing 802.1x authentication, you can minimize this risk by ensuring that only reliable devices can connect to the network.
Data Encryption
Several 802.1x implementations incorporate encryption protocols to guarantee data security between the printer and the network. This offers security against eavesdropping and unauthorized access to data.
Compliance
By employing 802.1x authentication, organizations and businesses can guarantee compliance with several industry standards and regulations, such as PCI-DSS, GDPR, and HIPAA. 802.1x authentication is critical in ensuring these standards are correctly followed, as they often require robust security measures to protect sensitive data.
802.1x authentication guarantees that only devices, according to your organization’s security policies, can establish a connection by implementing network access controls. It helps protect your IT infrastructure’s integrity and promotes compliance with internal security protocols.
Operational Efficiency
As we already discussed, with 802.1x, you can centrally control the network access via the authentication server. This allows more manageable and more effective central management of user authentication and access control policies. 802.1x authentication streamlines network administration by automating the client device authentication procedure. This minimizes the requirement for manual configuration and enables IT staff to focus on other essential responsibilities.
802.1x authentication is highly scalable, making it suitable for organizations of all sizes. It can ensure the security of all connected devices, including printers, regardless of your office or network size.
802.1x authentication provides a comprehensive security solution that enhances the security of valuable data and improves network administration. By implementing this robust protocol, organizations can protect their network infrastructure, enhance performance, and minimize cyber threats.
How to Configure 802.1x Printer Authentication (Step-by-Step)?
The steps for configuring 802.1x authentication vary depending on the printer model and network configuration. However, this guide offers a general framework to help you get started. Consult your printer’s user manual or the manufacturer’s website for specific instructions.
Step 1: Gather Necessary Information and Credentials
Ensure you have all the essential information, such as the RADIUS server information (IP address, shared secret), authentication method EAP-TLS, PEAP, etc.), and the credentials you need for the printer to authenticate with the server.
Step 2: Upgrade the Firmware of Printer (Optional)
Verify your printer’s firmware is up-to-date before configuring it for 802.1x. Manufacturers of printers regularly issue updates to improve security. You can visit the manufacturer’s website and access the printer support page to find the up-to-date firmware.
Step 3: Access Printer’s Network Settings
Enter the printer’s IP address into the installed web browser to access the web interface.
Step 4: Navigate to 802.1x Settings Section
Once you access the settings menu, find the network or security settings for 802.1x.
Step 5: Configuring 802.1x Authentication
Network printers offer different authentication options, such as PEAP, EAP-TLS, and EAP-TTLS. The method you choose will depend on your network security needs and the capabilities of your authentication server software.
Choose the authentication method of your choice from the following.
- PEAP: Username and password.
- EAP-TLS: Client certificate and a private key.
- EAP-TTLS: Username, a certificate, and a password.
Step 6: Configure Server Details
Provide your authentication server details, including:
- RADIUS Server IP Address: The IP address of your authentication server.
- Shared Secret: A private key that is shared between the printer and the authentication server for authentication purposes.
- Port Number: The port number used by the authentication server.
Step 7: Save and Apply Settings
Save the settings and apply the changes. The printer may need to restart for changes to take effect.
Step 8: Testing the Configuration
After the printer restarts, check its network connection status to ensure it is connected to your network.
Step 9: Check Authentication Logs
Check the RADIUS server logs to ensure that the printer has successfully authenticated.
Step 10: Print a Test Page
Print a test page to ensure the printer works properly over the network.
By applying these steps, you can successfully configure 802.1x authentication on your printer, ensuring it is secure and following your network’s security policy. This configuration not only protects your printer against unauthorized access but also improves the overall security of your network.
Best Practices for 802.1x Printer Authentication
Implementing 801.1x authentication is an important step towards securing your network. However, maintaining this configuration requires adhering to best practices. In the following section, we’ll discuss some recommendations to keep 802.1x printer authentication running securely.
Regular Updates
You should always check for firmware updates from the company that made your printer. These updates fix bugs, add security patches, and improve 802.1x authentication. Ensure the RADIUS server and related authentication software are up to date.
Check the expiration dates of any certificates used in the 802.1x authentication process. And renew them before they expire to prevent authentication failures.
Use Strong Authentication Method
Use EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) whenever possible due to its strong security capabilities. EAP-TLS uses certificates for mutual authentication, which provides high security.
Also, when using usernames and passwords, make sure they are complex and unique. Don’t use default or easily guessable passwords to avoid unauthorized access.
Monitoring and Auditing
Monitor your authentication server logs regularly to detect unusual authentication requests and promptly investigate any anomalies. Also, conduct regular security audits on your network authentication configurations.
This helps identify vulnerabilities and ensures that your 802.1x printer configurations remain resilient and effective.
Maintain Documentation
Keep a detailed record of your 802.1x configurations, including the RADIUS server, shared secrets, and authentication methods. This document can be handy for future updates and troubleshooting.
You also need to track changes to your 802.1x configurations. Documenting changes helps understand the impact of updates and serves as a reference for resolving issues.
Employee Training and Awareness
Ensure your IT team is properly trained to configure and manage 802.1x authentication. Skilled employees can more efficiently troubleshoot and maintain the system.
You can also educate your employees about the importance of network security. Human error can lead to security breaches; basic to intermediate awareness can help prevent them.
These best practices will help you maintain a secure and efficient 802.1x printer authentication. Regular updates, strong authentication, and monitoring are required to maintain the security benefits of 802.1x authentication. Proper documentation and employee training improve your network’s resilience and operational efficiency.
Automate Certificate Issuance with JoinNow Connector PKI
Organizations and businesses need to secure their network infrastructure. This article discussed the importance of network security for devices such as network printers, which are often overlooked. We introduced 802.1x authentication, a robust security protocol that ensures only authorized devices can access the network.
The guide explained everything from gathering information to accessing printer settings, entering credentials, and testing the configurations. We also outlined some best practices for maintaining a secure and efficient 802.1x authentication setup. This includes regular updates, robust authentication methods, careful monitoring, detailed documentation, and employee training.
SecureW2’s onboarding solutions simplify the migration to 802.1x authentication; we have been doing it for years. The JoinNow Connector PKI works seamlessly with your existing infrastructure and automates certificate issuance to improve management and security on managed and unmanaged devices. JoinNow MultiOS supports many operating systems and offers a simple onboarding experience that ensures secure authentication across multiple device environments.
SecureW2’s automated processes and centralized management platform will help you streamline 802.1x authentication configurations. Our solutions reduce administrative overhead and maintain consistent security for your entire environment.