If you are an Apple device user, you must know about the Airdrop feature, which lets you share files. You can also use the Airdrop feature to share your WiFi password with other Apple device users nearby. However, sharing your Wifi password on other Apple devices can leave your network vulnerable to exposing critical data.
As per Hexway’s report, the Airdrop technology broadcasts a cryptographic hash (SHA256) that can be misused to obtain the MAC address of a MacBook device. This may be innocuous in a home network. In a typical organizational setup like a K12, where students are equipped with numerous managed and unmanaged Apple devices, a Wi-Fi network protected with a pre-shared key would be an easy target for phishing and malicious attacks on the network.
This article will take you through the Apple Wi-Fi password-sharing technology in detail, talk about how easy it is to share Wi-Fi passwords on Apple devices, and how they leave your network vulnerable to threats. Then, we will look at SecureW2’s flagship solution to help your organization move away to a more secure, passwordless authentication to secure your network.
What is Apple Wi-Fi password sharing?
Apple devices like iPads and iPhones share Wi-Fi passwords through a technology similar to the Airdrop that helps send a Wi-Fi password from one device to another. A user selects a WiFi network (requestor) and is prompted to enter a password. The Apple device starts a Bluetooth Low Energy (BLE) prompt that advertises the need for a Wi-Fi network password.
Any Apple device in the proximity that is awake and possesses the password for the selected WiFi network connects through the BLE to the requestor.
The Apple device with the WiFi password (grantor) asks for the requestor’s credentials, and the requestor must prove his identity to the grantor. Once the identity is ascertained, the grantor provides access to the password, which the requestor can use to join the network.
How To Share WiFi Passwords on Apple Devices
As you begin to share your Wi-Fi password with another device, you must ensure that both devices have the latest iOS, iPadOS, or macOS version. Next, turn your Bluetooth and Wi-Fi on. Sign into your iCloud with your Apple ID and ensure your email ID is saved in the receiver’s contact and their email ID in your contacts. Now, bring both the devices within the Bluetooth and Wi-Fi range.
Share your WiFi Password Easily
- Unlock your device and connect it to your Wi-Fi.
- Select the Wi-Fi network on the device that you want to connect to the Wi-Fi.
- Tap Share Password on your device, and click Done.
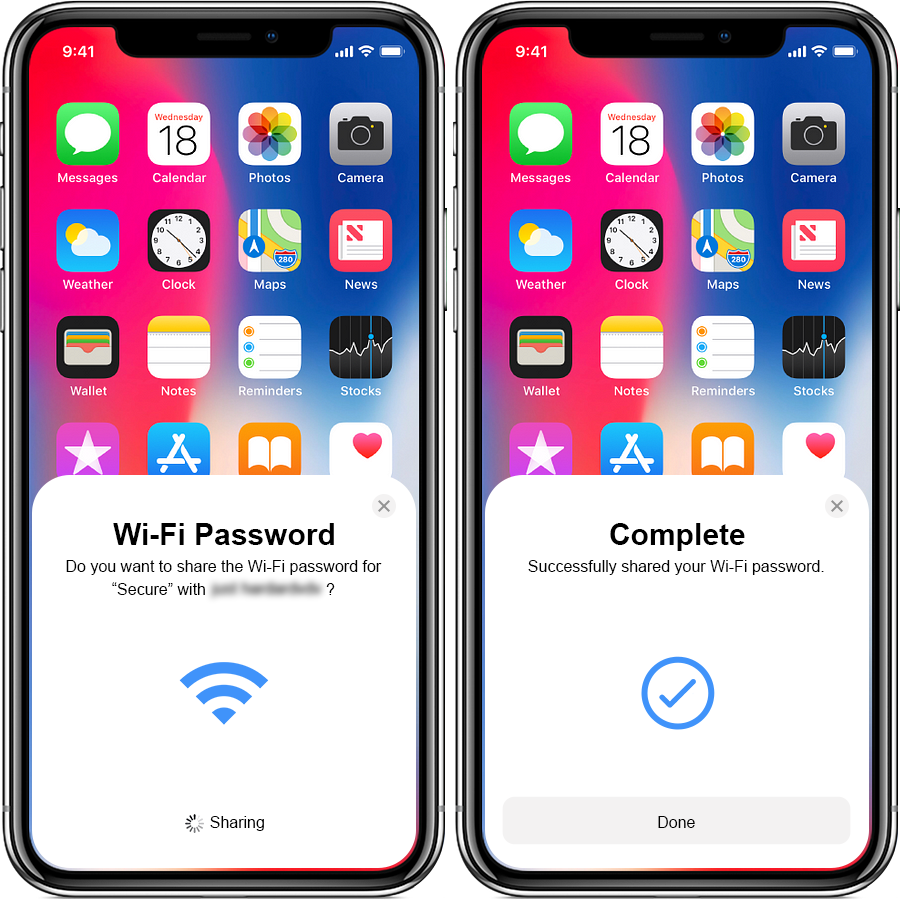
Wifi password sharing on an iPhone
It takes three simple steps to share your Wi-Fi password with another person, but it comes with its perils. It leaves your network vulnerable to phishing and brute-force attacks that could compromise data security.
Common Risks Associated With Sharing Wi-fi Passwords
In an organizational setup, sharing Wi-Fi passwords could lead to many problems, like losing your account security access, and more severe threats, like stealing confidential data for evil gains. Some common risks associated with sharing your Wi-Fi password are:
- Compromising network security
- Legal and ethical complications
- Privacy breach
- Affects productivity
1. Compromise of Network Security
A pre-shared key on a network is inherently a weak link in your network security layer. As a managed device owner, your device must be secure with apt antivirus software, but an unmanaged device may not be as safe. Now, if they click on a malicious link on their device through your network, it could leave your whole network vulnerable to attacks where a hacker can intercept and manipulate data transmission.
2. Legal And Ethical Complications
Sharing your Wi-Fi passwords could lead to potential misuse and data compromise. If a person with malicious intent gains access to your network, it becomes easy for them to access all the information on your network. If confidential customer data gets leaked or compromised, it becomes a legal issue for your organization. Sharing Wi-Fi passwords makes your network vulnerable to MITM and DNS attacks down the line, as your network is the entry point to all confidential data.
3. Privacy Breach
Sharing your Wi-Fi password could expose all your data, work apps, and sensitive work information to anyone. At a time when remote work is becoming more popular, and there is the ease of data access on any device, a privacy breach can lead to dire consequences like loss of your job and heavy penalties on your organization for breach. Sensitive data can be leaked and misused from your device by a former disgruntled employee with access to the Wi-Fi password or anyone looking to play mischief with your information and work.
4. Decline in Productivity at the Workplace
If you share your Wi-Fi passwords regularly, the admin has to look for potential breaches or attacks. It also means that each system should have regular checks for more robust antivirus software. If there is a threat of breach, the admins would also be burdened with regularly changing passwords. This would automatically mean more time would be spent securing the network through stringer means than actually spending time on productive work, and more expenses would eventually accrue on experimenting with security for your network with methods like MFA’s, two-factor authentication, etc.
Multi-factor and two-way authentication are more prominent ways to secure your network, but use passwords as a means of authentication. This starts the cycle of sharing passwords and brings another factor into the authentication process. Digital certificates, however, can’t be duplicated, transferred, or tampered with, making them the most secure factor in securing your network.
How to Reduce Vulnerability On A Wi-Fi Network
The Wi-Fi in the network is an attack vector that can follow your data thoroughly from one point to the end. Any device connected to your organization can track locations, leak sensitive data, or broadcast confidential work you want to keep private and secure. You can follow these steps to reduce the risks that could arise on your network due to unsecured or shared Wi-Fi connections.
- Opt For a Passwordless Solution Like Digital certificates
- Restrict Network Access
- Implement high-level security strategies like multi-factor authentication, privilege access management, and role-based access policies.
- Use a Firewall to protect your network from hackers
- Use a Managed Device solution for mobile devices.
Opt For a Passwordless Solution Like Digital Certificates.
The first line of defense to protect a network with pre-shared keys or passwords is to keep changing the passwords occasionally. Network devices and wireless access points come with default passwords preconfigured by the admin for easy setup. These are readily available and more accessible. Changing your default password to a more complex password would make it harder to remember and share with others.
However, changing passwords or rotating pre-shared keys is cumbersome and can be forgotten easily. It is prudent to shift to passwordless authentication, like phishing-resistant digital certificates that cannot be duplicated, stolen, or misused.
Restrict Network Access
Any hardware comes with a MAC address, and you can control network access by using a filter on the MAC address. The user document to the network hardware consists of a user manual for the specific know-how on setting up user access. The “guest account” is another method of securing your network where a particular guest account is set for outsiders with a separate password and restricted access to information and applications.
The JoinNow NetAuth is a guest access solution that streamlines delivering Wi-fi solutions to guest wireless. It enables organizations to manage their guest BYOD devices for encrypted and unencrypted guest networks.
Implement High-Level Security Strategies
Implementing high-level security strategies like multi-factor authentication, privileged access management (PAM), and role-based access control (RBAC) also add a step in securing your network access. Multi-factor authentication adds additional steps like a secret code, fingerprint scanning, or answering a secret question before they can access a network.
Privilege Access Management (PAM) manages a group of users that need access to sensitive or privilege-based resources in an organization. The authentication process for PAM is stringent and grants only specific users access to privileged information. They monitor users’ activity and report any anomaly on the accounts immediately for action by the admin.
Role-Based Access Management (RBAC) Role-Based Access Control (RBAC) assigns users permissions based on the organization’s designated roles. An engineer should not need to access the payroll information; likewise, a payroll executive probably doesn’t need access to software source code. Restricting access to only the users who require it is an effective way to mitigate damage in the event of a breach.
Use a Firewall To Prevent Network Breach
A host-based firewall is another way of securing your network from malicious attacks or unauthorized access. A firewall can be configured to prevent malicious software from accessing confidential information from your network via the internet. A firewall can also be configured to block data transmission from suspicious addresses, applications, and ports.
At the same time, it allows pertinent data to be used. An attacker can work through the network firewall quickly but will find circumventing a host-based firewall complex as it can be used with other security measures to strengthen your network.
Managed Device Solutions for Mobile Devices
iOS devices can be managed safely by deploying a Mobile Device Management (MDM) solution, allowing organizations to scale mobile device deployments securely. An MDM solution is built on technologies like over-the-air enrollment and configuration profiles. The Apple Push Notification service lets the device communicate directly with the network through a secure connection.
An MDM also allows you to enroll your BYOD securely in the network. A user enrolled in an MDM grants limited privileges to a BYOD user rather than giving them limited privileges and offers cryptographic separation of data. You can add an extra layer of security to your MDM solution using an onboarding solution like SecureW2, which seamlessly integrates with almost any MDM like JAMF and Mosyle for enhanced MDM security.
Go passwordless with a groundbreaking ACME solution for iOS.
Cyberattacks are becoming more innovative and brutal daily as numerous users and devices are added to your network. Sharing passwords between users only adds to your problems, as you cannot control the number of unauthorized users and devices on your network. A robust network security like digital certificates is vital to strengthen network security.
Managed device solutions like Jamf, Kandji, and Workspace One help securely manage iOS devices and users on a network. However, managing digital certificates for each device on an MDM would be tedious. SecureW2 ACME solution automates certificate issuance, renewal, and revocation from start to end, making it seamless and more manageable.
Apple also offers device attestation, a cryptographically signed certificate or a pseudo certificate containing a key from Apple, like a serial number and a newly generated key. The key for certificate enrollment is tied to a secure enclave on the device. It is used to authenticate Wi-Fi, WPN, MDM, and other services like Kerberos, making it a favorable choice for ioS authentication.
SecureW2s MDM Onboarding Solution With ACME Enhances Network Security
Sharing passwords between users is a menace, and the only solution to control this is to opt for an MDM solution that monitors users and devices on the network. A passwordless authentication solution provides an extra layer of security to your network. SecureW2s JoinNow Connector PKI and JoinNow MultiOS integrate seamlessly with any MDM and deliver robust security measures to manage their devices more efficiently.
SecureW2 has exclusively partnered with Apple to bring you the groundbreaking ACME solution to auto-enroll managed devices for digital certificates on any MDM via API Gateways. You can now better control your network by immediately reducing the risks of unauthorized access and data exposure.
Find out more by clicking here.
