Secure Shell (SSH) certificate authentication provides a robust method for authenticating users and hosts connecting to an SSH server. As a protocol, SSH prevents unauthorized parties from accessing systems remotely. But how does SSH implementation look in an organization environment?
This article delves into the intricacies of SSH certificate authentication, explaining its fundamentals, comparison with other authentication methods, and the implementation process.
What is an SSH Certificate?
At its core, an SSH certificate is a mechanism that uses public key cryptography for authentication. It is a digitally signed mutable blob of data containing a public key and metadata that identifies an SSH user or host. You can establish a secure and authenticated SSH connection with an SSH certificate.
SSH certificates are related to SSH keys as they contain the public key. SSH keys typically comprise two parts: a private and a public key. The private key remains confidential, while the public key is available to others. The SSH certificate binds a public key with the user’s identity.
SSH certificates play an integral role in network security. They are used to authenticate the identity of users and hosts in an SSH connection. With SSH certificates, you can ensure the integrity and confidentiality of data, facilitate secure access to remote hosts, and prevent unauthorized access. The importance of SSH certificates extends to establishing trust, controlling access, and contributing to an overall secure network environment.
SSH certificates also help protect against threats like IP address spoofing and man-in-the-middle attacks that involve intercepting and altering communications between two parties. Organizations can enhance their security by employing SSH certificate authentication and shielding their networks from threats.
What is SSH Certificate-based Authentication?
SSH certificate-based authentication employs digital certificates signed by a trusted certificate authority (CA) to verify the identity of users or hosts connecting to an SSH server. Unlike traditional methods relying solely on passwords or private keys, SSH certificate authentication offers enhanced security and scalability.
Types and Components of SSH Certificates
There are two main SSH certificate types: user and host certificates. User certificates authenticate the user trying to connect to the server. The user certificate involves a public key and metadata signed by a trusted certificate authority. Host certificates, on the other hand, authenticate the server to the user. These certificates help maintain a trustworthy relationship between the server and the user, providing secure access and preventing unauthorized access. The components of SSH certificates include:
Private Key
The private key is a critical component of an SSH certificate, kept secret by the user or system. It is unique to the user or host certificate and is critical in SSH certificate-based authentication. When paired with the corresponding public key, the private key allows the secure execution of commands on a remote server.
Public Key
The public key is another pivotal component of an SSH certificate. It pairs with the private key to enable key-based authentication. This public key is embedded in the SSH certificate and shared freely. The server can validate the client’s identity using public key authentication without requiring the private key.
How are SSH Certificates Generated?
Generating SSH certificates is a structured process that involves creating a key pair, forming a certificate request, and signing it by a trusted certificate authority. Here’s a step-by-step guide on how SSH certificates are generated:
| Step 1: Create the Key Pair | The very first step in creating an SSH certificate is generating a key pair – a private and a public key. Various algorithms, such as RSA, DSA, and ECDSA, can create these keys. The private key is kept secret and stored securely on the SSH client, while the public key is later embedded into the SSH certificate. |
| Step 2: Create a Certificate Request | After creating the key pair, you need to create a certificate request. This request includes the public key and identifying information about your SSH client, such as a username. This certificate request serves as an application to the certificate authority to issue a certificate for the public key. |
| Step 3: Sign the Certificate | Once the certificate request is created, it’s sent to a Certificate Authority. The CA verifies the information in the certificate request, and if everything checks out, the CA signs the certificate using its private key. This signature is the CA’s guarantee that the public key belongs to the SSH client listed in the certificate. |
| Step 4: Distribution | After the certificate is signed, it’s distributed to the relevant parties. The client can now use this certificate to authenticate to an SSH server. The server can also distribute its server certificate to any clients that need to verify its identity. |
| Step 5: Verification | When an SSH client tries to connect to a server, the server presents its SSH host certificate. The client verifies the server’s host certificate using the public key of the CA that signed it. If the verification is successful, the client knows it’s safely communicating with the correct server and not a malicious imposter. |
How SSH Certificate Authentication Works
To sum up, SSH certificate authentication is a complex yet efficient process that ensures secure and reliable communication between an SSH client and an SSH server. The steps involved in SSH certificate authentication work in unison to verify identities, enforce security measures, and establish a secure connection, ultimately ensuring a robust security environment. These steps include:
Initiation
The SSH client starts the authentication process by sending their public key, a random number, and a signature made with their private key to the SSH server. This initial step serves as a declaration of the client’s identity and a request to establish a secure SSH connection.
Validation
Upon receiving the client’s information, the server validates the signature using the user’s public key. The server ensures the client possesses the corresponding private key, without which the secure connection cannot be established.
Recognition
The server checks the public key against its list of authorized keys. The server acknowledges the client’s identity if the key matches one on the list.
Authentication
The server authenticates the client by checking the SSH certificate’s validity, issued by a trusted certificate authority, for existence in its authorized list.
Connection
Once these steps are completed, the SSH client and server establish a secure communication connection. This process ensures that only authorized clients can access the server and helps prevent potential security threats.
SSH Certificate vs. SSL Certificate
While SSH and Secure Sockets Layer (SSL) certificates are crucial for digital security, they serve distinct purposes and are utilized in different contexts. An SSH certificate is a tool to authenticate and establish secure connections between an SSH client and server. It contains a public key and metadata identifying the user or host, digitally signed by an SSH CA. SSH certificates are primarily used in secure shell environments for tasks like remote server administration, file transfers, etc.
On the other hand, an SSL certificate is used to authenticate and establish an encrypted link between a web server and a client, typically a web browser. This certificate includes a public key and additional information about the identity of the website and the entity that controls the website. SSL certificates are integral for secure web communications, such as online transactions, data transfers, and login information.
While SSH and SSL certificates employ public key cryptography, their primary difference lies in their purposes. An SSH certificate is used for secure shell connections in network administration, whereas an SSL certificate is vital for securing web-based communications. Hence, while both foster secure digital connections, they are not interchangeable and must be utilized in their respective contexts for optimal security.
SSH Certificate vs. SSH Key
An SSH key is a pair of cryptographic keys used to authenticate the SSH protocol. The key pair consists of a private key that remains secret and a public key that is freely shared. SSH keys are used to authenticate an SSH client with an SSH server. As we have seen in the earlier sections, both SSH certificates and SSH keys play a crucial role in SSH certificate-based authentication. They both involve a public and private key for encryption and authentication. Additionally, both allow secure access to servers by establishing the parties’ identity in the connection.
Differences between SSH Certificates and SSH Keys
While SSH keys and SSH certificates share similarities, they are not identical. Some differences include:
| SSH Certificates | SSH Keys | |
| Generation and Management | SSH certificates are issued by a certificate authority and signed with its private key. Users’ public keys and additional metadata are embedded in the certificate, and the CA signs the certificate. | SSH keys are typically generated by users or administrators using tools like ssh-keygen. Each key pair consists of a public key and a private key. |
| Lifetime and Expiration | SSH certificates can have a longer validity period and can be configured to expire after a specific duration or based on other conditions specified by the CA. | SSH keys have a fixed lifetime and must be periodically rotated for security. |
| Granular Access Control | SSH certificates can include additional metadata such as user roles, principals, or specific conditions under which access is granted. This allows for more granular access control policies. | SSH keys provide access based on the public key alone. Access control is managed by distributing public keys to authorized servers or users. |
| Revocation | Certificate revocation can be managed centrally by the CA. If a certificate needs to be revoked, the CA can issue a Certificate Revocation List (CRL) or use Online Certificate Status Protocol (OCSP) to inform servers of the revocation. | If a private key is compromised or an employee leaves an organization, keys must be manually revoked and removed from authorized systems. |
| Auditing and Logging | SSH certificates provide better auditing capabilities since all certificate-based authentication attempts can be logged centrally, including information about the user, the certificate used, and any additional metadata included in the certificate. | Managing and auditing SSH key usage across a large infrastructure can be challenging. |
So, Does SSH need an SSL Certificate?
The short answer is no; SSH does not inherently require an SSL certificate. While SSH and SSL are protocols designed for secure connections, they serve different purposes and operate in diverse contexts. SSH is mainly used for secure remote login, while SSL is typically used for secure internet data transmission. While SSL certificates could be used in some SSH contexts for an additional layer of security or encryption, they are not generally required or used in SSH.
Therefore, while SSH and SSL certificates aim to ensure secure connections, they are applied in different communication protocols and security.
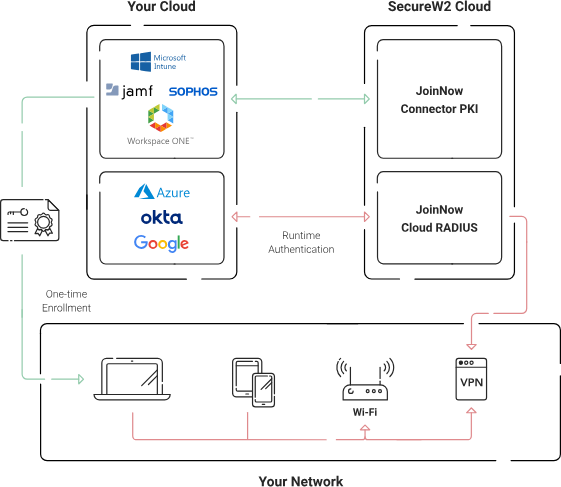
Leverage SecureW2’s Managed Cloud-based PKI for Robust SSH Authentication
SecureW2’s Managed Cloud PKI can provide a robust foundation for your SSH certificate authentication, adding an extra layer of security and simplifying the management process. SecureW2 facilitates a simplified SSH certificate authentication, offering a comprehensive package that efficiently manages the entire lifecycle of your PKI.
With SecureW2, you can securely generate, manage, distribute, and revoke your SSH certificates, ensuring their validity and timeliness in your network environment. Their managed PKI handles issuing, validating, and revoking SSH certificates, negating the complexities of manual management.
Unlike traditional on-premise PKI solutions, SecureW2’s Cloud PKI enables remote users to enroll and authenticate to network resources from anywhere securely. Moreover, SecureW2’s PKI solution can efficiently handle SSH keys and certificates, considerably simplifying the key approval process. As a result, it improves the security posture of your environment by reducing the risk of misplaced keys or unauthorized access. Schedule a free demo and get a quote today.