Key Points
- Traditional password-based authentication is no longer sufficient to secure modern wireless networks against evolving cyber threats.
- The Extensible Authentication Protocol (EAP) offers a dynamic, adaptable framework with various authentication methods to improve network security beyond simple passwords.
- ecureW2 simplifies EAP implementation with its Managed Cloud PKI and Cloud RADIUS, automating the certificate lifecycle to provide robust, passwordless authentication.
Network security is crucial in the modern digital world, where wireless communication is commonplace. Security risks such as unauthorized access, data eavesdropping, and network breaches can affect wireless networks. Because of this, strong authentication procedures are essential to protecting sensitive data and preserving the integrity of network infrastructure.
The Extensible Authentication Protocol (EAP) offers a standardized and adaptable framework for authenticating users and devices trying to join a network. In contrast to static password-based authentication methods, EAP provides a dynamic approach that allows various authentication methods suited to certain security requirements.
By using EAP, organizations may improve the security posture of their wireless environments, reducing the risks associated with unauthorized access and data compromise. Because of its flexibility and extensibility, EAP is a vital tool for guaranteeing safe network access across various sectors and use cases. In the following sections, we will explore the nuances of EAP, looking at its various applications, features, and security concerns for wireless networks.
Understanding EAP Protocol
The Extensible Authentication Protocol (EAP Protocol) is a wireless network that builds on the authentication method used by the Point-to-Point Protocol (PPP). This protocol is commonly used to connect a computer to the Internet. To offer a safe means of sending identifying information for network authentication, EAP is utilized over encrypted networks. It’s compatible with several authentication methods, such as public key encryption, smart cards, certificates, token cards, and one-time passwords.
EAP protocol safeguards a particular portal, limiting network access to only those with an authentication key or password. These techniques improve network speed and security by limiting the user base and preventing congestion. Employing EAP protocols allows organizations to adjust to privacy requirements and company guidelines.
One essential component of the EAP protocol is extensibility. The following are some of the protocol’s primary features:
- It offers the structure that the different authentication methods operate inside.
- It adjusts to new security requirements.
- If simplicity is desired, it can be maintained.
Exploring EAP Methods
The Extensible Authentication Protocol (EAP) includes several authentication techniques to address security and infrastructure requirements. It’s essential to comprehend these EAP techniques to build strong authentication systems in wireless networks. We go over each EAP type’s specifics and explain how it works below:
EAP-TLS
EAP-TLS stands for Extensible Authentication Protocol-Transport Layer Security. Even though the name is a mouthful, EAP-TLS’s primary goal is to improve network security using digital authentication. With EAP-TLS, your network is secured, and only authorized users may access business information, resources, and apps.
EAP-TLS uses X.509 digital authentication certificates, which are versatile and highly secure. Organizations can use these digital authentication certificates to provide single sign-on (SSO) across different network devices or VPNs.
The specifics of EAP-TLS’s functioning will be covered in more detail in the following section, but public-key cryptography generally forms the protocol’s basis. This method allows authenticated parties to enter networks without having to pre-share keys with one another.
How Does EAP-TLS Work?
As previously mentioned, EAP-TLS is a certificate-based mutual authentication protocol. This means that certificates are required for effective authentication on both the client and the server. After those certificates have been recognized, EAP-TLS will generate session-based keys that each side may use to finish the login process.
The procedure works as follows:
- A user seeks access to a network by using an authenticator app or wireless access point (AP).
- The AP requests the user’s identity.
- After being obtained, user data is sent from the AP to an authentication server.
- The authentication server asks the AP to verify their identity.
- After obtaining validation, the AP replies to the authentication server with it.
- The user establishes a direct network connection.
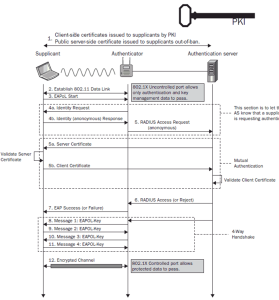
EAP-TTLS
EAP-TTLS stands for Extensible Authentication Protocol-Tunneled Transport Layer Security. This authentication technique is employed in computer networks to offer safe and encrypted authentication for wired or wireless network connections. EAP-TTLS is built on the EAP framework, which permits several authentication techniques to be used within the same protocol.
EAP-TTLS was created to enhance the previous EAP-TLS (Transport Layer Security) protocol and solve some drawbacks. It offers a means of maintaining the security of the authentication procedure while utilizing the current username/password-based authentication methods.
EAP-TLS and EAP-TTLS differ primarily in that EAP-TLS requires certificate-based self-identification from both the client and the server. In EAP-TLS, a TLS handshake that verifies the client’s identity performs the authentication.
The TLS handshake is a procedure wherein the client and server converse and negotiate during the connection to exchange encrypted keys for data. In this scenario, the peer and server must agree upon the TLS protocol and cipher suite to validate digital certificates.
In EAP-TTLS/PAP, the server generally employs two phases, the TLS handshake and the TLS tunnel phase, to create a secure connection to the client. According to the RFC standard, client authentication is optional, and only a server certificate is needed.
During the TLS handshake phase, the TTLS server authenticates with the client using common TLS protocols. During the tunnel phase, the client authenticates itself to the server using an arbitrary protocol, such as EAP, PAP, MS-CHAP, or another.
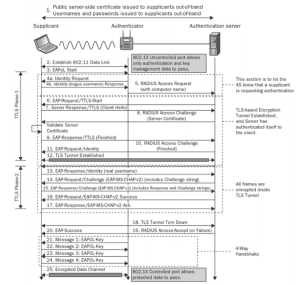
PEAP
The EAP-Protected Extensible Authentication Protocol (EAP-PEAP) establishes a more secure encrypted channel before password-based authentication. PEAP is an 802.1X authentication technique that creates a secure tunnel via which the client authenticates with the server using a server-side public key certificate. An encrypted SSL/TLS tunnel is established between the authentication server and the client via PEAP authentication. User credentials are kept safe since the information is encrypted and stored in a tunnel during the transaction.
How Does PEAP Work?
When a PEAP conversation starts, the EAP server and the EAP peer (client) agree to utilize PEAP as the communication protocol. Then, the EAP client assumes the role of a PEAP peer, and the EAP server assumes the role of a PEAP server. The dialogue between the peer and the server then starts, and it goes through two stages:
Phase 1: In this stage, a TLS connection is formed between the PEAP peer and server, and the PEAP server is authenticated. An identity exchange usually starts the interaction, in which the client sends a request and identity packet to the authenticator, and the authenticator sends back a response and identity packet to the client. By including TLS records in the message payload, the server and peer exchange TLS communications.
Phase 2: During this phase, a whole EAP conversation occurs within the TLS connection. The discussion only occurs if the TLS connection was successfully formed in the first phase. The security required to safeguard the authentication data is provided by the PEAP server, which authenticates the PEAP peer inside the TLS connection. As part of this process, the server and client decide which inner EAP technique to utilize for the authentication procedure. The second phase ends, and the PEAP conversation is concluded after the authentication.
The PEAP server initiates the agreed-upon inner EAP method during the second phase. The inner method does the real authentication within the TLS session. Although PEAP has several inner methods, the EAP Microsoft Challenge Handshake Authentication Protocol version 2 (EAP-MSCHAPv2) is the most utilized.
The Microsoft-defined EAP technique known as EAP-MSCHAPv2 encapsulates MSCHAPv2, an authentication mechanism that verifies access to accounts using users and passwords. Windows operating systems support EAP-MSCHAPv2 natively in addition to other EAP techniques. PEAP-MSCHAPv2 is used when MSCHAPv2 is utilized as an inner technique in PEAP communication.
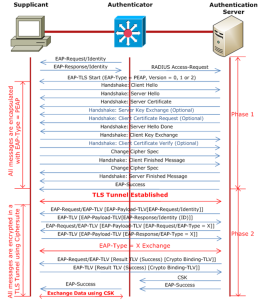
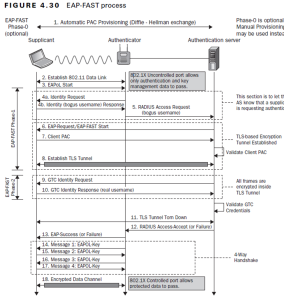
EAP-FAST
EAP-FAST uses Transport Layer Security (TLS) to create a mutually authenticated tunnel, allowing safe communication between a client and an authentication server. Additional authentication-related data is sent between the client and the authentication server over the tunnel using type, length, and value (TLV) objects.
To facilitate the quick re-establishment of the secure tunnel without requiring the server to retain its per-session state, EAP-FAST supports the TLS extension as specified in RFC 4507. Credentials for the TLS extension are provisioned using EAP-FAST-based procedures. These credentials are called Protected Access Credentials (PACs).
How Does EAP-FAST Work?
EAP-FAST uses a two-phase tunneled authentication procedure to function. To create a secure tunnel between the client and the authentication server and protect client identification information, EAP-FAST initially uses the TLS handshake during the first phase. Version negotiation guarantees concurrent protocol compliance between the client and server. Afterward, further communication takes place in the second phase to specify the permission and authentication policies included in TLV objects, along with the selected EAP method. Flexible configuration options, including server certificate use, authentication method choices, and automated or manual PAC provisioning, are available inside the EAP-FAST module. Furthermore, clients receive Protected Access Credentials (PACs), which are disseminated and hold shared secrets and other relevant information that allows for optimal network authentication within the tunnel that has been constructed. Furthermore, TLS negotiation depends on server certificate validation, which guarantees the reliability of the authentication server.
EAP-SIM and EAP-AKA
EAP-AKA stands for Extensible Authentication Protocol-Authentication and Key Agreement. It is centered on the 3GPP AKA protocol, which shares a secret key between the network and the subscriber and has a challenge-response system. The key is contained on the Subscriber Identity Module (SIM) card or the Universal Integrated Circuit Card (UICC) and is obtained from the subscriber’s International Mobile Subscriber Identity (IMSI). Wi-Fi networks that support EAP and 3G and 4G networks can employ EAP-AKA.
EAP-SIM stands for Extensible Authentication Protocol-SIM. Its foundation is the GSM SIM authentication protocol, which uses a shared secret key between the user and the network and a challenge-response system. The SIM card stores the key obtained via the subscriber’s IMSI. Wi-Fi networks that support EAP and 2G and 3G networks can employ EAP-SIM.
The methods EAP-AKA and EAP-SIM use to authenticate the subscriber and the device are identical.
- First, the device sends the subscriber’s identification (either IMSI or a pseudonym) to the network as an EAP-identification-Request message.
- Subsequently, the network sends an EAP-Request message with an authentication mechanism and a random challenge.
- The device generates a response and a session key using the algorithm and the shared secret key, then sends them back to the network via an EAP-Response message.
- After confirming the answer, the network signals that the authentication process is over and the session has been formed by sending an EAP-Success message.
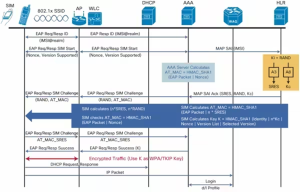
EAP-GTC
EAP-GTC is an inner authentication technique that uses a security token. It was initially described in RFC 2284. The protocol is frequently used in the PEAPv1/EAP-GTC TLS tunnel that PEAP creates. Token cards create one-time passwords, which EAP-GTC specifies as an EAP envelope. The server must authenticate using a certificate.
Organizations that employ two-factor authentication to prevent typical password breaches, including shared passwords or poor password hygiene, should choose EAP-GTC.
EAP-POTP
EAP Protected One-Time Password (EAP-POTP) is an EAP method created by RSA Laboratories that generates authentication keys using one-time password (OTP) tokens, such as a portable hardware device or a hardware or software module operating on a personal computer. It is detailed in RFC 4793. In protocols that employ EAP, EAP-POTP can be used to provide key material and unilateral or mutual authentication.
Two-factor user authentication is provided using the EAP-POTP technique, which means that a user must have physical access to a token and knowledge of a personal identification number (PIN) to authenticate.
EAP-PSK
RFC 4764 defines EAP Pre-shared Key (EAP-PSK) as an EAP method for pre-shared key (PSK)-based mutual authentication and session key generation. It’s intended for authentication across insecure networks like IEEE 802.11 and offers a secure communication channel for both parties to use when mutual authentication is successful.
Public-key cryptography is unnecessary for the lightweight and flexible EAP approach known as EAP-PSK, outlined in an experimental RFC. At least four messages are exchanged during the EAP method protocol exchange.
EAP-TLS: A Deeper Dive
EAP-TLS is the most secure authentication method and has been acknowledged by many for more than 15 years. Because EAP-TLS requires reciprocal authentication, it’s a particularly effective method of protecting 802.1X networks.
EAP-TLS dramatically lowers the likelihood of cybercrime, particularly man-in-the-middle attacks. Cybercriminals would impersonate legitimate access points in those assaults, allowing them to quickly get user credentials through spoofing and authentication. Yet over-the-air assaults are practically unfeasible due to the requirement for users to authenticate themselves for mutual authentication.
What are EAP-TLS Benefits?
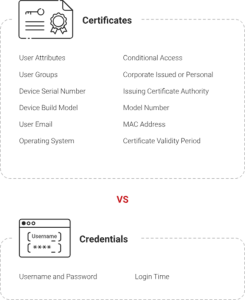
EAP-TLS has several clear benefits, especially in terms of security. It immediately increases network visibility by associating digital certificates with certain devices. Passwords are easily guessed or stolen, but EAP-TLS’s mutual authentication feature lets you know exactly which device is connected to your network at any moment. Additionally, problems can be linked to a particular device if they occur.
Lastly, the end-user experience is substantially improved with EAP-TLS. Users do not need to establish and memorize hundreds of different passwords because certificates cannot be removed from a device or manipulated in any manner. Alternatively, users may log in directly to the network, which is simpler, quicker, and more secure.
What Do You Need to Implement EAP-TLS?
To implement EAP-TLS on your network, you’ll first require a Public Key Infrastructure (PKI) to manage digital certificates. Traditionally, establishing and maintaining a PKI has been difficult and time-consuming, with activities such as producing and distributing certificates, managing revocation lists, and assuring the security of private keys. SecureW2 streamlines this process, making it more accessible and manageable for businesses of all sizes. SecureW2 enables you to create and administer a PKI, automate certificate enrollment and renewal, and seamlessly interact with your existing network infrastructure. This simplicity allows organizations to benefit from the solid security of EAP-TLS authentication without the burden often associated with PKI maintenance, making it an appealing alternative for safeguarding network access.
Fortifying Wi-Fi Security with EAP and RADIUS Authentication through SecureW2
Understanding the various EAP methods is critical for developing strong authentication mechanisms suited to specific security needs. Furthermore, incorporating a RADIUS authentication server, such as SecureW2’s Cloud RADIUS platform, improves Wi-Fi security by allowing passwordless authentication and implementing the most recent network policies based on information from your identity infrastructure. SecureW2 provides a smooth and resilient approach to network security, protecting organizations from cyber threats while simplifying authentication processes.
In addition to our RADIUS authentication solutions, SecureW2 provides a full PKI (Public Key Infrastructure) solution to enhance network security. Our public key infrastructure (PKI) simplifies certificate enrollment, renewal, and revocation operations. Organizations may use SecureW2’s PKI to provide a secure basis for network authentication, assuring data communications’ confidentiality, integrity, and authenticity.
Contact us today to learn more about how we can safeguard your network against cyber threats.