Relying on passwords alone to safeguard access to your resources (including Wi-Fi, applications, and email security) is no longer secure. Cyber attacks designed to harvest credentials become increasingly complex by the day. Stealing a single set of credentials can have massive consequences, including loss of privacy, leaks, and damage to an organization’s reputation.
SecureW2’s platform was created to address this issue by making certificate-driven and context-rich security accessible to all organizations. In a nutshell, we provide all the tools an enterprise needs to tie each connection – whether it’s to Wi-Fi, a cloud application, or something else – to a detailed, non-exportable, digital ID called a certificate. We also provide additional ways for administrators to determine who and what has access to the company network and resources, and provide easy-to-use software that enables personal devices to self-connect themselves to secure Wi-Fi networks.
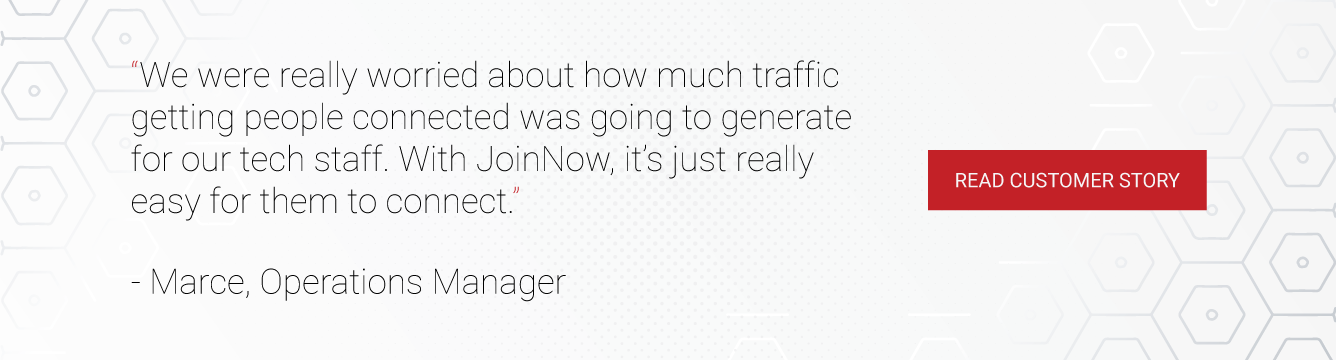
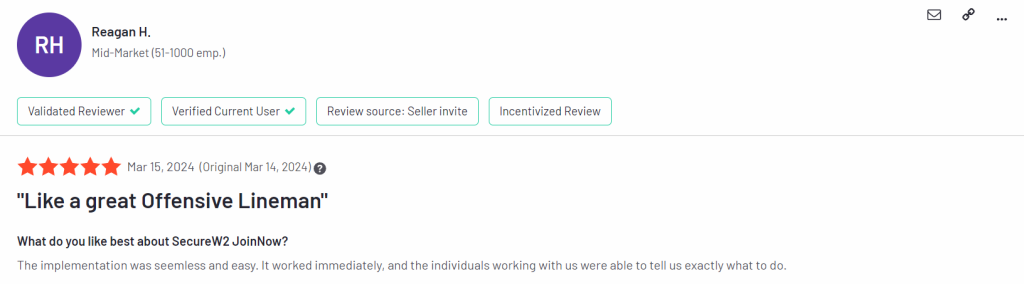
What Do Real Customers Have to Say About Deploying SecureW2?
Making changes to security policies as integral as authentication requirements can be daunting. Fortunately, we’ve worked with over a thousand different organizations over the years, and they’ve had great things to say about rolling out our solutions.
Here are some recent G2 reviews we’ve received that mentioned the speed, and quality of support provided during deployment:
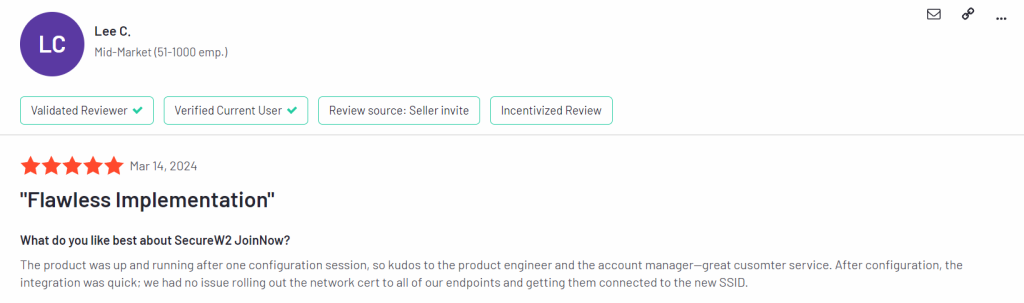
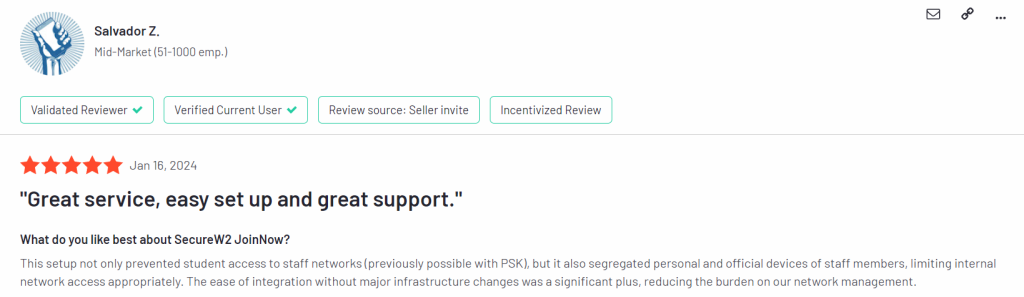
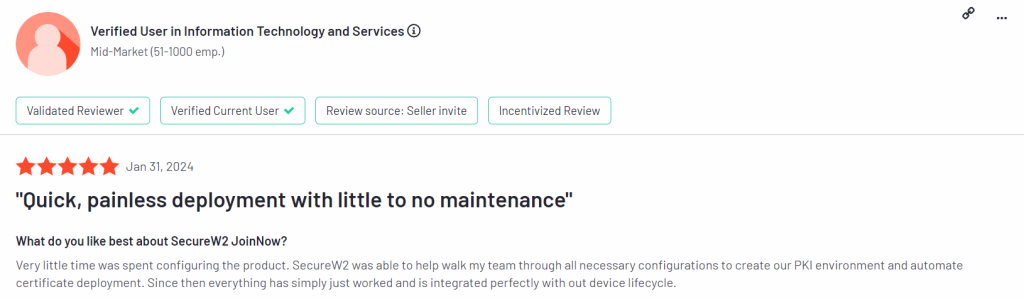
What is the Daily Experience Like for Your Users?
There’s a common sentiment among IT professionals that increased security usually needs to come at the expense of the user experience. In other words, the more rigorous your security and authentication requirements, the more frustrating it is for the employees who need to meet those requirements. With SecureW2’s platform, this isn’t the case.
If you’re using certificates for Wi-Fi authentication, application security, or any other use case, your employees likely won’t even notice the difference. In fact, if they notice anything, they will likely notice positive changes. Authenticating to wireless networks with certificates, for example, is slightly faster than with passwords because the protocols used are more efficient. Additionally, employees won’t be disconnected from resources because of passwords expiring; instead, our technology can automatically enroll them for a new certificate to ensure uninterrupted access.
The most work an end-user will have to do comes when they enroll for certificates – and we’ve tackled that stage of the lifecycle to simplify it, too. For employees on company-owned and managed devices, the certificates are issued automatically on the backend through your Mobile Device Management (MDM) system.
If your employees are using personal devices for work, then they can enroll for certificates through our self-service JoinNow MultiOS application. The application confirms their identity by having them input their credentials once and then runs on their device to configure it and install the certificate for them. This whole process, from start to finish, generally takes less than a minute.
What Threats Does SecureW2 Protect Your Network From?
SecureW2, at our core, provides a platform designed to grant administrators greater control and visibility over the people and devices connecting to company resources and networks. The exact threats this type of visibility protects an organization from depends on the specific SecureW2 product the organization is subscribed to, but in general, we make certificate-based security more accessible.
Passwords are a massive threat to network security. If you rely on a single password for controlling your Wi-Fi access (like on a home network), you can be certain that the password has been shared with unauthorized third parties, including friends and family. And even if you have individual usernames and passwords for employees to log into your Wi-Fi with, you’re still at risk; many people reuse their passwords, and once a password is compromised, hackers can propagate a plethora of attacks on your network.
Even if your employees practice perfect password management, those passwords are still a risk, thanks to increasingly complex cybersecurity attacks designed to target passwords. Attacks like Man-in-the-Middle (MITM) attacks are common and can snatch usernames and passwords as they’re sent over-the-air.
Putting aside the very real cybersecurity risks posed by password-based authentication, passwords present a range of daily frustrations that are also threatening to an organization. Consider, for example, the drop in productivity that occurs every time an employee forgets their password and needs to wait on calls with your helpdesk to regain access to a resource. The flip side of this scenario is the time investment your helpdesk staff also needs to put in to resolve the employee’s issue.
Moving to certificate-based authentication prevents these threats. We even ease the move to certificates with advanced onboarding technology for both company-managed devices and employee-owned devices.
What are the Business Benefits of Our Platform?

Our passwordless authentication suite does more than just provide security. It has tangible returns that any organization can benefit from.
One example is the time your IT team can save. Password-based support tickets take time to resolve, and many of our customers report as much as a 20% drop in support tickets when password-related issues are eliminated. This allows them to focus on things that matter. There’s also a significant financial gain to this drop in support tickets; Deloitte found that in 2020, the average cost of a password reset was $2,700.
Additionally, employees who no longer need to worry about being disconnected from important resources when a password change occurs see the benefits, as well. Seamless connection to Wi-Fi and other resources prevents unnecessary drops in productivity. Furthermore, the authentication experience is frictionless; instead of having to log in with a complex password every time, your employees can quickly connect with a digital certificate and oftentimes a single click.
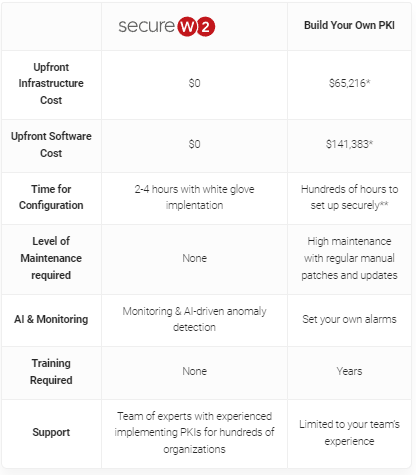
Building a similar solution on your own would be costly. Most organizations report configuring and managing your own RADIUS server costs well into 6 figures. SecureW2 offers a cost-effective, fully managed Cloud RADIUS service with SLAs up to 99.999%. Also, while it’s technically possible to create your own Public Key Infrastructure (PKI) for issuing certificates, it tends to cost hundreds of thousands of dollars and hundreds of hours to set up correctly. By going with a managed PKI solution such as ours, you are saving up to 70% when compared to solutions such as Microsoft’s Active Directory Certificate Services (AD CS). Most PKI professionals we work with say that the more experience they have with PKI, the less they want to manage it.
Overview of the Deployment Process
For some organizations, the process of deploying a new solution is intimidating. This can prevent them from moving forward when it doesn’t need to.
At SecureW2, we pride ourselves on having a simple, straightforward deployment process handled by experienced engineers. You’ll start by filling out a questionnaire that tells us what your goals are, how soon you’d like to accomplish deployment, what types of infrastructure we’ll be integrating with, and more.
After that, you’ll have a call with our support team. They’ll work on helping you distribute certificates to your endpoints and connecting our platform to your infrastructure. Generally, the people who will need to be on these calls include the following:
- Someone who works with your Identity Provider
- Someone who works with your MDM platform
- Someone who works with your wired and wireless networks
- A project principal
As a brief summary, the things that are configured during these calls include the following:
- Creating necessary applications and permissions in your Identity Provider and MDM
- Setting up our PKI services, including a Certificate Authority, network profiles, and certificate templates
- Adding your Identity Provider to the JoinNow Management Portal
- Creating role, enrollment, and network policies as necessary
- Configuring the MDM to enroll company-managed devices for certificates automatically
These integrations are typically completed over a few calls. Afterward, fully rolling out our products is entirely up to the preference of customers and can be done in a matter of a couple of weeks if desired.
SecureW2: Partners for Passwordless Security
We believe that improving the security of your organization’s network by going passwordless shouldn’t be challenging. It should be simple, fast, and headache-free for everyone involved – especially for your IT professionals.
That’s why we’ve focused on creating detailed documentation, building a knowledgeable team of engineers with years of experience, and listening to our customers’ feedback. When you make a simple, effective platform like ours, the end results speak for themselves.
If your organization is considering doing away with insecure PSK networks or wants to secure other resources with certificate-based authentication, we’re ready to help. Chat with us today to learn more about our products and how we can help you go passwordless.