The traditional network perimeter is a relic of the past. With remote work now common, users need secure access from anywhere, making outdated security models ineffective. Relying on perimeter-based defenses exposes organizations because threats no longer come only from the outside. It’s time to shift to a model where access is verified at every step, ensuring only trusted devices and users connect to critical resources.
Because of all of this, device trust is incredibly important. Device Trust is designed to ensure that only trusted users can connect to the network. Below, we’ll show how it can be easily configured with the most used device operating systems and one of the most used identity providers out there, “Okta.”
What Is Okta Device Trust?
Device trust means verifying both the user and their device before granting access. It moves beyond outdated credential-based authentication to ensure only trusted devices connect to critical resources. Once trust is established, users get seamless, secure access without adding complexity for IT or end users. Okta Device Trust is a security feature that controls access to Okta-integrated applications.
Okta Identity Engine (OIE) and Okta Classic are well-known identity and access management platforms that manage identities using a variety of approaches. With the Okta Identity Provider, you can ensure the device and user are authenticated accurately because the Okta Identity Engine will need to verify both. This allows you to centralize and manage all your devices and users in a single control panel using the Okta Universal directory.
Okta Device Trust also allows admins to enforce device trust capabilities on managed devices. Through the admin console, they can confirm that every device is managed by an endpoint management tool before users can access the network and Okta-managed apps.
Any SAML-based app supports Okta Device Trust and can be configured to work with Windows, Android, MacOS, and iOS.
Setting Up Okta Device Trust With Windows
Okta suggests a couple of essential prerequisites before you start configuring Okta device trust on Windows, including:
- An Active Directory Domain-Joined Windows System working on a supported version of Windows.
- Digital certificates installed on the targeted PCs
- You are connected to the organization’s network.
In the admin console, enable Windows Device Trust and enroll the Device Trust certificate on a Windows device. Here, you will use the IWA web app to confirm the security posture of Windows devices and users by validating that they have joined the Active Directory Domain. Okta will then issue a certificate to the device to enable device trust in Okta apps such as Okta Verify and Okta Fastpass.
Next, admins will install the Device Registration task that sets the rules for certificate issuance, renewal, and revocation. Then, they can verify the trusted option for apps. This ensures that certificates are installed in the certificate store of devices and that the Trusted setting is enabled. This allows users to authenticate to apps safely. An optional step is to enable GPO to select the device trust certificate automatically.
Finally, the SSO policy rules the organization will follow can be configured in Okta to allow for streamlined and secure authentication of all Windows devices.
Okta Device Trust for Windows ensures only trusted, domain-joined PCs can access cloud apps, protecting corporate data without relying on network perimeters. It supports multi-forest environments for seamless authentication, enforcing security without adding complexity.
Setting Up Okta Device Trust With Android
Enable the Android Device Trust setting in the admin console and update your MDM provider. Your MDM must support managed app configuration, and the Android device must be enrolled with Okta Mobile installed. This ensures that only trusted devices gain access, reinforcing security without adding complexity.
Next, configure your key pairs through your MDM’s managed app configuration. Then, configure the application’s Sign On policy rules. These rules will determine policies such as:
- Which users belong to which groups
- Determining whether they are on or off-network or within a defined network zone
- Which platform the device is using
- Whether or not a device is trusted
Once you have configured the trust settings for signing into apps, users are ready to authenticate their trusted Android devices.
Setting Up Okta Device Trust With MacOS
Admins need to enable Device Trust in the MacOS Device Trust section. Okta then verifies that Jamf Pro manages the devices. Next, you will need to modify the Okta Device Registration Task to make sure you can complete the certificate exchange.
Admins will need to install Python 3 and Device Trust Dependencies in order to make any modifications. The Okta Device Registration Task should be switched to Jamf Pro, and that will allow the admin to complete the final steps:
- Register the device with Okta to obtain the Device Trust certificate.
- Configure Chrome and Safari and test native apps to present the certificate automatically when gaining access.
- Schedule a lightweight task to check whether a certificate is expired and attempt to renew the certificate before expiration.
- Check whether the device is trusted before issuing a certificate.
The last step is configuring application Sign On policies (as seen in the Android configuration section).
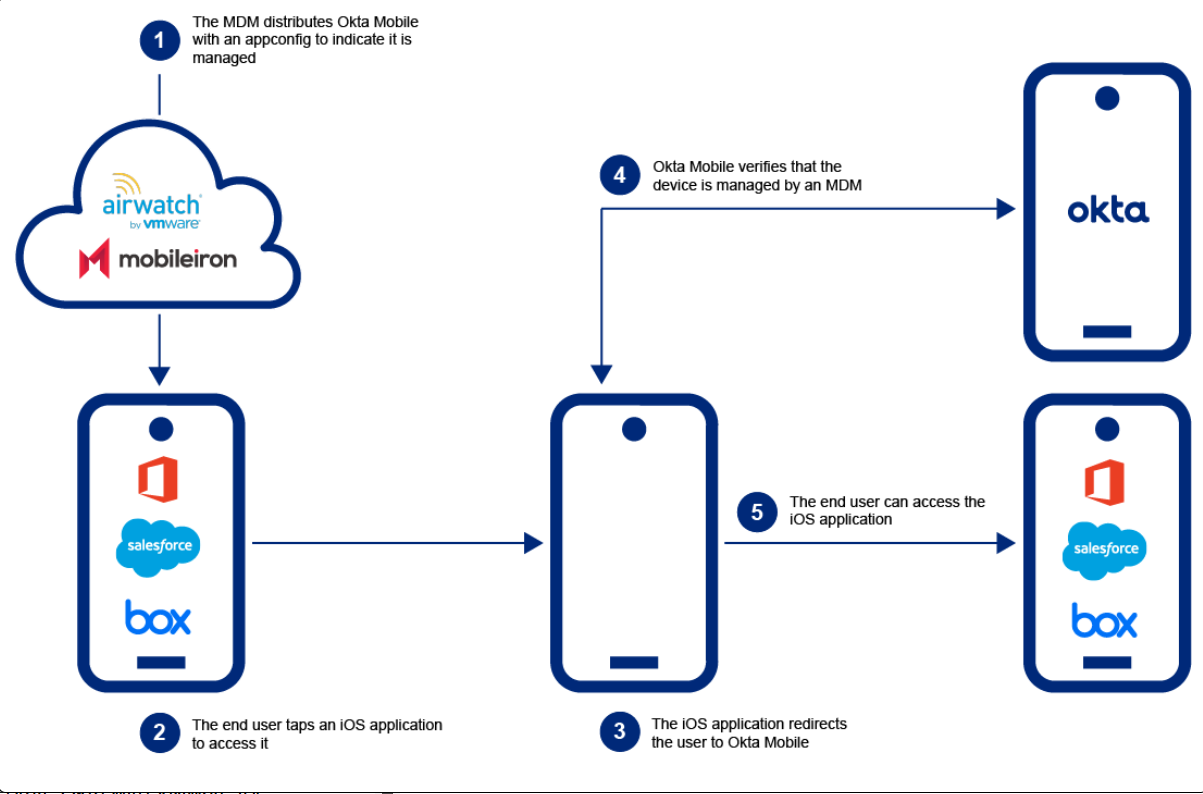
Setting Up Okta Device Trust With iOS
Admins should first enable your organization’s global Device Trust setting in the admin console’s iOS Device Trust section. You should then integrate Okta into your MDM provider to allow Okta to manage and track devices.
You simply have to configure the app Sign On policies and allow users to begin onboarding their trusted devices. These rules will determine policies such as:
- Which users belong to which groups
- Determining whether they are on or off-network or within a defined network zone
- Which platform the device is using
- Whether or not a device is trusted
Role of Certificates and RADIUS in Device Trust
Digital certificates provide stronger security than credentials ever can. Each certificate ties directly to both the user and their device. When a user authenticates with a certificate, admins know that both the user and device are verified—eliminating the risk of unauthorized access. Unlike passwords, certificates can’t be stolen, phished, or reused, ensuring only trusted devices connect to the network.
Digital certificates, along with a reputable Cloud RADIUS, play an essential role in establishing device trust by authenticating and authorizing the identity of devices within a network. At the same time, Cloud RADIUS complements it by acting as a centralized authentication server and performing the Identity lookup with IDPs such as Okta, thus reducing the risk of security breaches.
Okta is unique because it’s the only identity provider that allows end-users to use PIV Certificate Authentication as the first form of authentication. Organizations that use PIV for authentication distribute a physical smart card configured with identifying information used for authentication. It significantly improves protection against phishing attacks.
Okta enables one set of credentials to log in to various web applications within a network. Considering that (55%) of IT security respondents and individuals would prefer a method of protecting accounts that doesn’t involve passwords, it’s safe to say people forgetting their passwords or losing their credentials is a major hassle.
Digital certificates, along with the Cloud RADIUS, eliminate the need for shared credentials, thus reducing the risk of identity theft and unauthorized access for attackers. The Identity lookup by the RADIUS server is an extra layer of security. Identity Lookup confirms again that a user/device is valid by cross-referencing with the IDP at the time of authentication in addition to authenticating the certificate.
This also means that any changes to a user/device before a certificate is revoked can be applied dynamically. For example, suppose a device belonging to someone who leaves the company in the middle of the day attempts to access the network. In that case, Cloud RADIUS can see that even if the certificate hasn’t been revoked yet and prevent access. It can also revoke the certificate at that time.
Stronger Okta Device Trust With SecureW2
SecureW2 works with Okta to enable efficient and accurate certificate issuance and management. By replacing credentials with certificate-based EAP-TLS authentication and providing world-class onboarding software, SecureW2 can easily prepare every managed device for a trusted network connection.
Using SCEP and WSTEP gateways, SecureW2 can configure managed devices for EAP-TLS, email security, application security, and more without interaction from the end user. The most common cause of support tickets is human error, so we simply removed the end user from the configuration equation. Additionally, SecureW2 provides the capability for dynamic RADIUS authentication. This allows the Cloud RADIUS to communicate directly with the IDP during authentication. If a user needs to update their network permissions, they no longer have to revoke and replace every certificate; simply update their IDP permissions, and they can be authenticated in real-time.
Okta Device Trust allows admins to provide stronger security by authenticating the identity of the device and the user using Okta Universal Directory. When every network user is authenticated correctly, it greatly reduces the risk of an outside attack. Check out SecureW2’s pricing page to see if our MDM solutions can work with your Okta network.