Key Points
- Active Directory Certificate Services (AD CS) allows organizations to build their own PKI and issue X.509 certificates for secure, passwordless 802.1x network authentication.
- While AD CS enables certificate-based 802.1x, managing your own PKI is often limiting, costly, and complex for administrators.
- Integrating AD CS with SecureW2’s Managed Cloud PKI and Cloud RADIUS simplifies secure 802.1x deployment, making it more scalable, flexible, and cost-effective than traditional on-prem setups.
Keeping your network secure from unwanted intruders is increasingly difficult with the advancements in technology. It’s relatively easy for malicious actors to obtain network access and steal all the data on that network.
Although 6 in 10 businesses are victimized by a cyber attack, many still underestimate the danger they pose. Threats like the infamous man-in-the-middle attack (MITM) are designed to trick unsuspecting victims into unknowingly sending their user credentials to a bad actor and compromising the entire network. These attacks commonly happen when a user attempts to connect to the network and accidentally connects to rogue Access Points. Luckily, these threats can be prevented if a network uses x.509 digital certificates (instead of passwords) with 802.1x authentication.
Active Directory Certificate Services (AD CS) was developed by Microsoft because they knew that digital certificates offered far better security standards since they’re encrypted, protecting all the data input onto them. Certificates need a Public Key Infrastructure (PKI) to operate and AD CS provides the blueprints for admins to build their own PKI. The certificates generated by AD CS can then be used for 802.1x authentication so organizations don’t have to rely on insecure credential-based authentication.
However, admins may want to hold off on building their own PKI with AD CS because it’s restrictive and expensive. Plus, just because you have 802.1x doesn’t mean your network is completely protected. This article covers what 802.1x is and how AD CS admins can use certificate-based authentication with 802.1x to ensure strong wireless security.
What is 802.1x?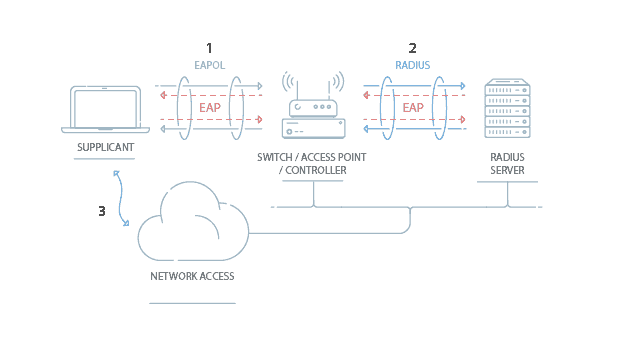
IEEE 802.1x falls in the IEEE 802.1 group of networking protocols and can authenticate devices attempting to connect to a network.
802.1x differs from standard home or open networks because it uses a RADIUS server. RADIUS servers are a huge factor in why 802.1x is considered to be one of the safest forms of network authentication.
When a device requests network access, the RADIUS server verifies the user credentials by checking the IDP to see if that user is still active in the network. If so, the RADIUS server will check for any network policies administered to the device based on the user’s standing in the organization.
The RADIUS server can also be configured to authenticate certificates, instead of credentials. In order for this to work, the RADIUS server needs to be equipped with the Certificate Authority (CA) that has issued the client certificates the devices are using for network authentication.
In order for credential-based RADIUS server authentication to work, the RADIUS needs access to the organization’s directory, which is usually done through a SAML or LDAP protocol. With certificate-based authentication, you don’t have to set up a connection between the RADIUS and directory, which gives you a lot more flexibility in choosing your infrastructure. SecureW2 can integrate with any major RADIUS server to enable secure 802.1x authentication.
PEAP-MSCHAPv2 is the authentication protocol used with Active Directory and RADIUS servers, but recent issues with the protocol have caused a lot of organizations to switch to certificate-based authentication.
Don’t Authenticate with PEAP-MSCHAPv2
PEAP-MSCHAPv2 is a credential-based authentication protocol that relies on passwords for access to the network. Since it’s a Microsoft service, many Windows environments will use PEAP as their authentication protocol. If you’re currently using it, you should seriously consider using AD CS (or a Managed PKI) certificate for authentication instead of PEAP-MSCHAPv2.
First off and as stated earlier, PEAP-MSCHAPv2 is a credential-based protocol. Passwords have proven to be a weak form of security, especially when an organization only uses one password for network access. Shared passwords can easily be stolen by internal and external actors: a disgruntled employee who wants revenge, or a hacker executing a MITM attack. It takes just one malicious actor to acquire the password and the entire network and all of the data can be compromised.
While PEAP is an EAP method that utilizes the encrypted tunnel, cyber attacks like the MITM attack render the tunnel useless by impersonating the server and receiving user credentials.
Secondly, there is a well-known vulnerability with PEAP’s encryption method that can be exploited by malicious actors and still leave networks susceptible to over-the-air credential theft.
Use the EAP-TLS 802.1x Authentication Protocol
The encrypted TLS tunnel is an excellent security measure, but it’s useless when the tunnel is tricked into connecting to a malicious actor’s software. Instead of authenticating with passwords and leaving user credentials exposed, if you have AD CS you can switch to authenticating devices with digital certificates.
Using certificates for authentication offers better security measures because users can be authenticated through EAP-TLS, which prevents over-the-air credentials theft. Digital certificates encrypt the information put on them so the information stays protected, even if the certificate is compromised. EAP-TLS requires an approved certificate to be equipped on both devices and servers. As a result, both the device and server can verify each other in real time so there’s no risk of connecting to rogue APs. Before requesting network access, the user device can verify the correct server by identifying the certificate on the server.
Setting Up a RADIUS Server for 802.1x with AD CS
802.1x sets itself apart from other authentication methods because it requires a RADIUS server. For credential-based authentication, you will need to establish a connection between your Identity Provider (IDP) and your RADIUS. For certificate-based authentication, you aren’t required to integrate your IDP, granting your organization more freedom when choosing your infrastructure.
SecureW2’s certificate enrollment client can integrate with any SAML or LDAP IDP so you can enroll devices for AD CS certificates and securely authenticate users for network access.
Configuring a RADIUS Server on AD CS:
Here’s a quick overview on how AD CS admins can configure their RADIUS server.
- Import the AD CS Root CA to your RADIUS Server trust list.
- Import your Certificate Revocation List to your RADIUS Server
- (Optional) If you’re using Onboarding software like SecureW2, configure any authentication policies, like segmenting your network into VLANs, by editing your network policies in your Onboarding software.
Click on our RADIUS integration page for specific guides on how SecureW2’s Managed PKI can integrate with any major RADIUS server.
SecureW2 also created Cloud RADIUS, which is more secure and scalable than on-prem RADIUS servers. Cloud RADIUS is designed for certificate-based authentication, so once you create a CA in SecureW2, Cloud RADIUS is ready to authenticate your certificates.
Consider a Managed PKI Services to Issue & Manage AD CS Certificates
AD CS requires an on-premise directory connection because that’s what it was designed for, using AD with AD CS on-premise. This obsolete feature restricts admins from choosing their own infrastructure and prevents many environments from migrating their systems to the cloud.
Cloud computing services offer far better security measures and are more scalable with a growing business. Cloud-based services have come a long way and the market is no longer dominated by on-premise Microsoft infrastructure.
Organizations that use AD CS may think they have to keep their PKI on-premise , but that’s not actually the case. Admins can integrate AD CS with SecureW2’s Managed PKI in the Cloud, a turnkey solution that saves an organization thousands and relieves admins from many of the labor-intensive tasks that managing your own PKI requires.
SecureW2’s Managed Cloud PKI doesn’t require extra hardware to set up (since it’s all on the cloud), can be set up in less than an hour, and comes with tons of certificate automation features that make issuing and managing certificates significantly easier and more cost-effective.. If you’ve been considering switching from your Active Directory to Azure AD, SecureW2 is the only vendor that empowers organizations with 802.1x authentication using Azure AD.
On-prem PKIs can take anywhere from a few weeks to a couple months to complete a full implementation. Plus, the setup is incredibly labor-intensive and left completely to the organization’s sysadmins. On-prem PKIs require a team of trained professionals that understand how to set up and manage, meaning the organization has to spend resources training current admins or hiring new ones.
Organizations only need to task one part-time administrator to manage a cloud-based PKI. The burden of management is lifted from IT admins.
Issuing AD CS Certificates on Every Device
One of the biggest hurdles with certificates is how IT admins can get a certificate onto every user device, especially now that nearly every employee has multiple devices. By integrating AD CS with SecureW2, admins can automatically configure both BYODs and managed devices for 802.1x settings and equip them with certificates.
AD CS admins can deploy SecureW2’s onboarding software to automate certificate enrollment and 802.1x configuration. Our automated services relieve admins from manually configuring every BYOD for a certificate. Plus, end users have a far better experience because all they need to do is press a few buttons and their devices handle the rest.
AD CS admins can also integrate their MDMs, like Microsoft Intune, with SecureW2 to securely distribute certificates to every managed device. Using our Management Portal, admins can set up powerful Certificate Auto-Enrollment Gateway APIs so they can send out payloads containing 802.1x configuration settings. Every managed network device can self-service themselves with a certificate. Check out our page on using SCEP to enroll EAP-TLS certificates with Intune.
Secure 802.1x Authentication for AD CS with SecureW2
In conclusion, using AD CS certificates for 802.1x is a powerful way to improve your network security. The best practice for delivering secure 802.1x authentication is by integrating your AD CS CA with SecureW2’s Managed Cloud PKI and Cloud RADIUS, which are more versatile, scalable, less expensive, and just plain easier than it’s on-premise alternatives. Curious about how much you could save with SecureW2? Check out our pricing page and find out today!