In an age where people have migrated to conducting business online, organizations must ensure their Wi-Fi networks are protected from outside threats.
Cyber attacks, including the infamous man-in-the-middle attack, prey on unsecured Wi-Fi networks and farm credentials without admins or the organization even realizing until it’s too late. 6 in 10 businesses that are victimized by a cyber attack will go bankrupt in as little as 6 months.
Digital certificates provide the best method for securing wireless authentication because they encrypt user information as it’s sent through the air, keeping it protected from outsiders. Plus, certificates make it easier for organizations to deploy WPA2-Enterprise with 802.1x authentication, the gold standard for wireless security.
Microsoft understood this and created Active Directory Certificate Services (AD CS), a mechanism for Microsoft admins to build their own PKI. Public Key Infrastructures are what certificates need to function. PKIs manage every function of certificates, including storage, issuance, revocation, and configuring network policies.
Limitations of AD CS
Since AD needs to be set up on-premise, many Microsoft admins feel that their only option is building an on-premise PKI, which is incredibly expensive and labor-intensive to implement.
Luckily, you can use your AD CS Certificate Authority (CA) with SecureW2’s Managed Cloud PKI, which relieves admins from the grunt work of implementation and doesn’t require a team of trained experts to manage. It also adds a slew of certificate enrollment and management features, which further reduces the cost and effort to use certificates. This page will show you how to use AD CS certificates for Wi-Fi authentication security to replace passwords.
Integrating AD CS with SecureW2’s PKI Services
Admins can replace the AD CS backend with SecureW2’s easy-to-use Management Portal where they can issue, view, and revoke certificates with ease.
Backup CA on ADCS
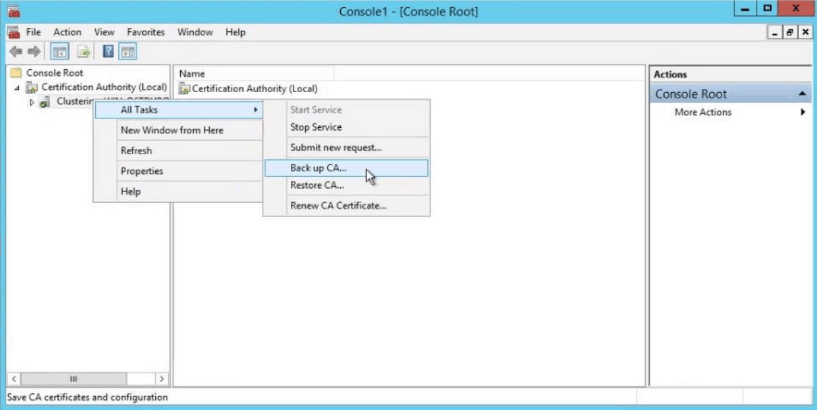
- Open the Certification Authority snap-in. In the console tree, right click the name of the CA. On the Action menu, point to All Tasks, and click Back up CA.
- A popup wizard will be opened. Click Next.
- A new screen with Dialogue Box appears. Select Private Key and CA certificate. Select a folder in which you want to save the certificate.
- When the new screen appears to enter password, please enter the password.
- Click Finish.
Import CA in Cloud Connector
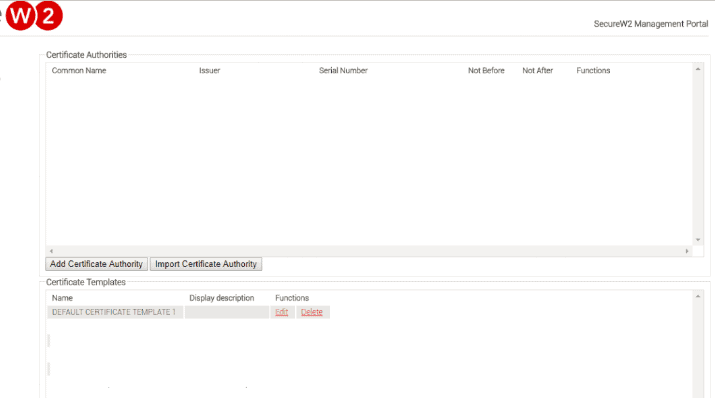
- Log in to JoinNow MultiOS Management Portal. Navigate to PKI management -> Certificate Authority and click on Import Certificate Authority.
- The basic certificate authority page is displayed.
- Select the p12 file in Certificate.
- Enter Password that was created when exporting the Certificate Authority.
- Once completed, ensure the certificate is created.
Enabling WPA2-Enterprise and 802.1x in AD CS
WPA2-Enterprise and 802.1x provide over-the-air encryption and are essential for protecting online communications from cyber threats.
However, deploying 802.1x with credential-based protocols, like PEAP-MSCHAPv2, still leaves your Wi-Fi vulnerable to over-the-air credential theft. This is due to the weak security provided by passwords. They can be shared, forgotten, and stolen, making them easy to bypass for malicious actors. One lost set of credentials means the entire network and everything on it is vulnerable.
SecureW2’s Managed PKI authenticates clients with EAP-TLS. EAP-TLS provides certificate-driven Wi-Fi, which eliminates over-the-air credential theft and password-related issues.
Setting Up a RADIUS Server to Use AD CS
802.1x and WPA2-Enterprise require the use of a RADIUS server. Using a RADIUS server requires you to set up a connection between your Identity Provider (IDP) and your RADIUS, if you’re using credential-based authentication. With certificate-based authentication, you don’t need to integrate your IDP, allowing you a lot more flexibility in the infrastructure you choose. Also, SecureW2 allows you to use any SAML or LDAP Identity Provider to enroll for AD CS certificates so users can easily enroll for secure Wi-Fi access.
AD CS admins can configure a RADIUS server in five easy steps:
- Importing the AD CS Root CA to your RADIUS Server trust list.
- Configuring the RADIUS Server to use the SecureW2 CRL.
- Add Identity Lookup, if supported by your RADIUS Server. (Identity Lookup is supported by SecureW2’s RADIUS Server)
- Configuring any authentication policies, like segmenting your network into VLANs.
- Upload your Root CA to the RADIUS server.
You can visit our RADIUS integration page for a more in-depth look at configuring SecureW2 with any major RADIUS server. However, we created Cloud RADIUS, a cloud-based RADIUS server that offers far better security and versatility than on-prem RADIUS servers, and it’s also designed for certificate-based authentication, so once you upload your CA into SecureW2, Cloud RADIUS is already setup to use your CA.
Distributing AD CS Certificates to User Devices
By integrating your AD CS CA with SecureW2, admins can easily and automatically configure devices for 802.1x and provision each device with a certificate simultaneously, BYOD and Managed. SecureW2 provides dissolvable clients for every Operating System, meaning end users only have to sign-in once and they’ll be automatically configured for secure certificate-based Wi-Fi access until they leave the organization.
BYODs
Our best-in-class onboarding software allows admins to configure BYODs to automatically self-service for 802.1x settings and a certificate by downloading an app and clicking a few buttons. The whole process on their side is done in minutes.
Managed Devices
SecureW2’s software comes with industry-first native integrations with MS-GPO, which allows admins to set up powerful Gateway APIs to push out certificate auto-enrollment payloads, so managed devices are set up for certificate-based authentication at the click of a button. Admins can set network policies, categorize users, and distribute certificates through their MDMs with no end user interaction.

Managing AD CS Certificates
SecureW2’s easy-to-use Management Portal allows admins to effortlessly manage all aspects of their AD CS certificates; issuance, revocation, provisioning, CRLs, and much more.
SecureW2 comes with powerful certificate management features like: Automated email notifications when certificates are about to expire, and custom certificate templates so admins can provision certificates to end users based on their standing in the organization. The HelpDesk can also use SecureW2 to keep better track of everyone on the network since they can search for any user attribute (common name, MAC address, computer model) as well as have full visibility in a user’s onboarding logs so they can easily troubleshoot any enrollment or configuration issues that may arise.
SecureW2 also comes built with Certificate Revocation Lists (CRLs). CRLs are imperative for Wi-Fi security; however, the list can get so long that update times slow down and impede the RADIUS authentication process. Luckily, admins can use SecureW2 to enable smaller lists (Delta CRLs) that update much more frequently and contain all revoked certificates from the last time the big list (Base CRLs) updated. Admins can configure their RADIUS server to authenticate against the smaller lists, maintaining the quick authentication process.
SecureW2 offers industry-exclusive Identity Lookup with LDAP & SAML Identity Providers, allowing our Cloud RADIUS server to look up the identity of a user in real time during the authentication process. Identity Lookup used to only be available for LDAP, but SecureW2 brings proprietary technology so you can use it with your SAML providers as well.
Integrate SecureW2 with AD CS for Strong Wi-Fi Security

Microsoft admins can integrate AD CS with SecureW2’s Cloud PKI and Cloud RADIUS to ensure strong Wi-Fi security and eliminate over-the-air credential theft. Our software encrypts web traffic and device onboarding so no outside threats can penetrate the network. Both BYODs and Managed Devices can be easily and automatically configured for 802.1x settings and auto-provisioned with certificates.
AD CS users don’t have to be stuck with expensive and convoluted on-prem hardware when they can easily implement our cloud-based software in a matter of hours. Plus, it’s incredibly cost effective for organizations of all sizes.