Key Points
- YubiKeys alone support native credential-based auth, but adding digital certificates makes them much more versatile—for network access, VPN, desktop logon, and any PKI-able service.
- A certificate on a YubiKey means that losing the physical key is less risky: only the certificate needs to be revoked and reissued to a new key, rather than re-registering each service manually.
- SecureW2’s solution simplifies certificate provisioning and management on YubiKeys through its Cloud PKI, Cloud RADIUS, and management tools—making large-scale deployment practical and secure.
Yubikeys are an incredibly secure method of protecting yourself from data theft, but you’re probably not using them to their full potential.
Natively, Yubikeys only support credential-based authentication through keypairs and one-time passwords. However, SecureW2 has developed an industry-first solution for enrolling the security keys for digital certificates – a vastly superior authentication method.
The Advantages of Certificates on Yubikey
Certificates Allow Yubikey to Authenticate More Services
There’s a shortcoming of Yubikeys that is important to note – they aren’t universally supported. Here’s a list of the sites and services that are currently supported. Outside of those applications, they’re useful for controlling access to your devices.
Yubikeys can secure those adequately with their native credential capabilities, but when equipped with certificates, a Yubikey becomes even more versatile.
Using SecureW2’s Yubikey certificate solution, you can configure your keys to access your WPA2-Enterprise network. Restricting Wi-Fi access to just people with a certificate-configured key makes your network virtually impenetrable to over-the-air attacks (like the notorious man-in-the-middle attack).
In addition to Wi-Fi access, you can also use our Yubikey solution to sign into desktop and VPN services.
Furthermore, the use of certificates has the potential to expand the scope of Yubikey integrations to any application or service that has PKI infrastructure.
In order to utilize certificates on Yubikeys, you’ll need the appropriate network infrastructure to support certificate issuance and revocation. SecureW2 can help transition your WPA2-Enterprise network to EAP-TLS that supports certificates.
We offer all the necessary components to build an EAP-TLS network from scratch, including Cloud RADIUS and full PKI services. We can also integrate into any existing infrastructure you might have, including RADIUS servers and any major access points.
Certificates on Yubikeys Harden Your Network Against OTA Attacks

Security keys, like the Yubikey, are primarily a defense against phishing and other strategies that rely on human fallibility. After all, you can’t be fooled into giving away your credentials if you don’t know what they are in the first place.
However, Yubikeys don’t protect you from more advanced over-the-air hacking techniques, such as the infamous man-in-the-middle attack. The credentials are securely passed to the device, but that’s as far as security key protection goes. They’re communicated over the same network as all of the other potentially insecure traffic.
Yubikeys and certificates both rely on asymmetric cryptography to protect their data, but the scope of their protection differs.
Certificates ensure that the authentication process is protected from start to finish. The private keys are invulnerable from the moment they’re generated on the Yubikey until they are authenticated by the recipient application.
Lose your Yubikey? No problem.
Losing a security is a big deal.
No, it’s unlikely a person could pick it up and use it to access your accounts. After all, they’d still need to know your PIN. The real issue with losing a security key is that you’ll have to replace it and re-register it with every application you’ve been using it with.
For some, that might just be their email. For other people, it could be up to 20 or 30 services across the web. On an enterprise level, employees might lose a key or two every day – the time lost recovering keys or re-pairing them to services would add up quickly.
If your Yubikey is equipped with a certificate, however, replacing it is a non-issue. The services it’s registered to aren’t actually registered to the physical key – they’re tied to the identity stored in the PKI. All you have to do is revoke the old certificate so it can’t be used, then issue a new certificate to a new key and sign it with the identity of the same employee. It will be ready for use immediately.
How to Use Certificates on a Yubikey
Configuring Yubikeys for certificates is simple with SecureW2. With just a few clicks in our world-class management portal, you can create a custom client that will configure your Yubikey for certificate enrollment.
Here’s a brief .GIF of the process:
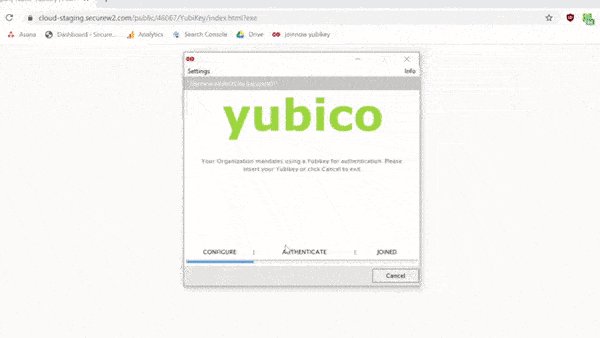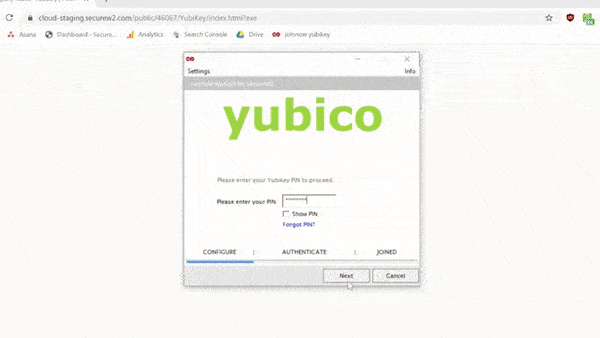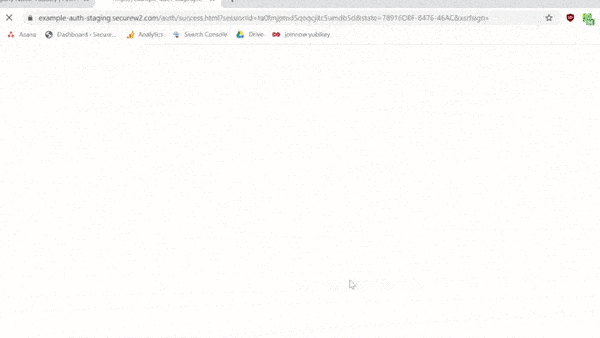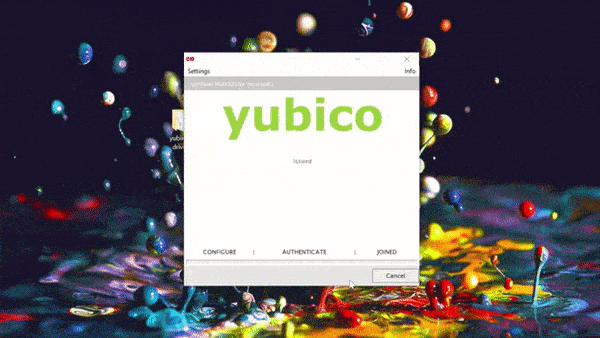
Using certificates with Yubikey undoubtedly enhances your network security to a great degree. However, Yubikey may still be susceptible to an attack because of a security vulnerability that may leave your network vulnerable.
Let us take a quick look at a Yubikey vulnerability that often gets neglected and can potentially become a gateway for a malicious attack on your network.
Security Vulnerability of Management Key in Yubikey
Yubikey requires users to authenticate using PIN, PUK, and Management Key. The Management key is used to authenticate for completing specific administrative tasks, such as enrolling in a new certificate.
This key or passphrase is quite long and does not have the three-times-lock-out security feature. This vulnerability often goes unaddressed since the management key is less critical and has limited usage.
Nonetheless, it’s a vulnerability that has the potential to cause some damage to your network security. The Management key and PIN are derived almost similarly to how a WPA PSK encryption key is derived from the passphrase. If one has access to either the PIN or management key, the other can be cracked. Though the combination will be time-consuming and complicated to crack, there is a possibility that a hacker could potentially brute-force the management key and recover the PIN itself.
SecureW2 Solutions for Management Key Security
SecureW2 uses a feature to randomize and store the management key in the PIN itself, thereby eliminating the risk of any security breach through a brute-force attack. To retrieve the management key, you will need to authenticate using the PIN.
This means the admin will need to ask the user for the PIN every time they perform an administrative task on the Yubikey. It does add a few extra steps for the admin, but the end user will not experience any difference in their user experience.
It is always safer to use a strong PIN, but it does have the security feature of a lock-out after three failed authentication attempts, and that includes authentication to access the management key. This feature mitigates the security risk attached to the management key by storing it securely inside the Yubikey instead of running the risk of it falling into the wrong hands.
Yubikey Certification Management With SecureW2
Using credentials for authentication leaves your network susceptible to all kinds of attacks. Therefore, a lot of organizations are moving away from it and opting for certificate-based security. Enrolling Yubikey with digital certificates is a sure way to make your network more secure.
As a Yubico Partner, SecureW2 has developed tailored solutions that advance the security and convenience offered by Yubikeys by integrating them with our robust certificate management platform.
We are the only one in the industry that offers a solution for using digital certificates with YubiKeys that facilitates user onboarding and configures security keys with certificates within minutes. This eliminates the need for the IT department to manually enroll Yubikeys with certificates which in turn reduces the burden on IT, eliminates any human error, and makes certificate enrollment scalable. Click here to check out our pricing.