Amidst uncertainties in times of war, hackers have frequently upgraded their attack modes and penetrated almost every industry you can think of. The Australian cyber-security head has admitted reporting one cyberattack every seven minutes, accounting for a whopping 13% rise in these crimes in a single year.
It is pretty apparent that to counter these advanced cyberattacks, you must regularly upgrade your network security infrastructure. In doing so, you must evaluate the existing access privileges of your organization’s users and devices. Sometimes admins overlook Device Trust due to placing more emphasis on individual users and their access privileges, which can weaken the security within a network.
In this article, we will learn about device trust – both a concept and a product/feature – and the importance of identity context in any organization’s security.
What is Device Trust?
Device trust, as the name implies, is the methodology of examining whether the devices present within a network can be trusted to authenticate and authorize the enterprise’s resources.
Device trust is vital in categorizing the devices for specific decision-making within an organization. In device trust, each endpoint of the organization is evaluated, and trust is granted based on the needs of the particular device.
For example, the access granted to a managed device like a laptop used exclusively by a unique user will be different compared to a common desktop system which many users handle simultaneously. In a similar manner, the level of trustworthiness of the different devices will vary based on the access levels of users operating them.
Generally, establishing user trust accompanies device trust by verifying the identity of users before allowing them access to the device. But this can sometimes be challenging, especially when using an unmanaged device that must be registered with users.
Difference Between User and Device Trust
User and device trust go hand in hand, but unlike the identity context of users, the device needs a dynamic evaluation to explore its trustworthiness fully. Compared to a user’s identity that needs to be verified only at the time of authentication, a device might change its identity depending on the users operating it.
The state of a particular instrument can also change in due course of time depending on the applications and circumstances, unlike users making it more dynamic and varying in nature. Thus the same device that is trustworthy at a given time might not be trusted at a different time. However, once a user is validated, they do not need to be validated again for a while – unlike a device.
Some organizations also use device trust, like a product or service, either separately or in combination with other prominent Identity and Management solutions. In the upcoming sections, we want to discuss a leading IAM solution, Onelogin, which has helped administrators quickly strengthen their network infrastructure for a long time.
What is OneLogin Device Trust?
As we have discussed, many enterprises do not just implement device trust as a concept but also as a product or feature, and Onelogin is a perfect example of that.
OneLogin has incorporated Device Trust literally as a feature in many of their products and services to install PKI (Public Key Infrastructure) certificates onto desktops for authentication and management. Device Trust is an integral part of their MFA (Multi-factor Authentication) package, which combines its strengths with its Identity solutions to enhance the security of existing users.
OneLogin enforces IT identity policies that immediately restrict access to apps for employees who leave or change positions by deleting them from Active Directory. It also controls the access of multiple applications, swiftly onboards and offboards multiple users, and provides end users simple access to all of their apps on all devices.
OneLogin, in addition to many services, functions as an Identity Provider. It can sync with your Active Directory according to their site but ultimately replaces Active Directory. Also, OneLogin desktop has been one of the leading Identity and Access Management (IAM) service providers for enterprises around the globe and has been using the concept of Zero Trust in combination with context-based authentication.
Context-Based Identity Management
Identity is the new backbone for conditional access and is fundamental for Zero Trust network architecture. Identity is the foundation for Zero Trust and is the best solution to secure connectivity to a contemporary business’s applications, data, mobile devices, and other corporate resources.
Context-Based Identity Management is a security concept that assists organizations in overcoming rising security threats by employing conditional access policies and authorization features in the organization’s database.
Context-based identity management is an automated feature of authentication and authorization that enables you to gather contextual information whenever a user logs onto your network. These contextual data and information are obtained instantly by using various dynamic attributes, such as:
- Location
- IP Address
- Device History
- Personal Information
- Gender
- Age
- Behavior
These attributes usually enhance the security of the organization by validating the users’ identities more precisely before authenticating and authorizing them access. For instance, if an end user attempts to access the system through a public Wi-Fi network instead of their office or home network, access may be refused if this is not consistent with the user’s usual behavior.
Now we will see how you can create and download certificates manually using OneLogin Identity Context.
Certificate Authentication for OneLogin Devices
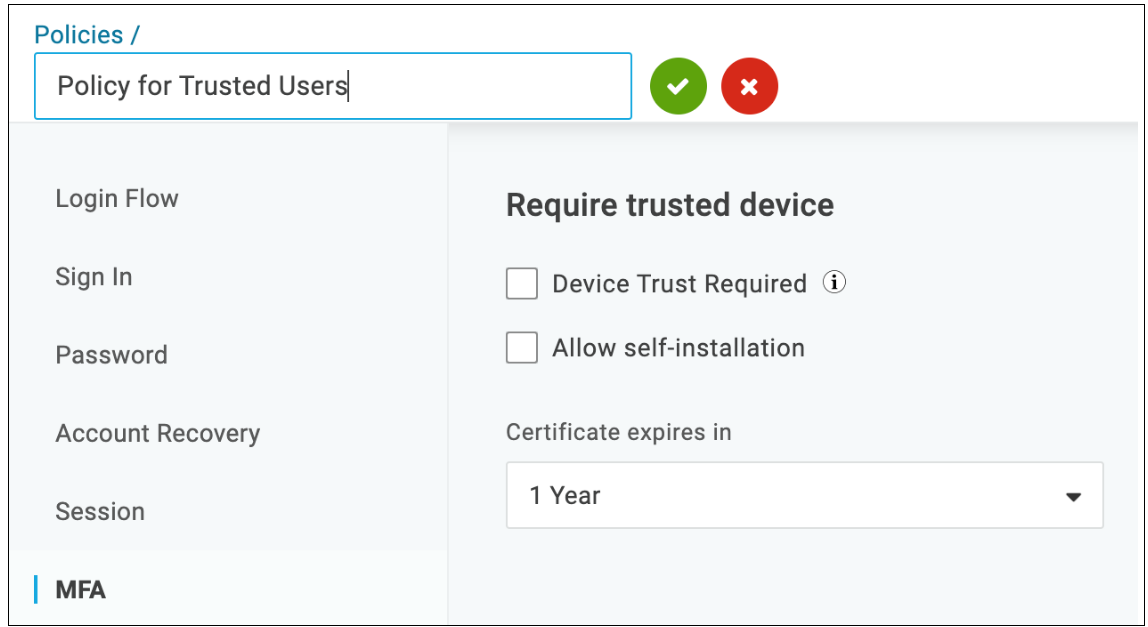
You can apply policies to self-generated digital certificates on the OneLogin platform by performing the following steps:
- Select a user policy to edit under Security > Policies, or click New User Policy to add a new policy.
- Switch to Device Trust Required on the MFA
- Selecting Allow self-installation lets users install certificates themselves the next time they log into OneLogin or manually install them in their browsers. Before signing into any applications, users who need a certificate are requested to install one after authenticating using OneLogin.
- Choose how long before a certificate expires you want it to be valid. You have a choice of 1, 2, or 5 years.
Now, you must manually create and download the certificates for installation by performing the following steps:
- Navigate to Users > Users and select the user.
- Under the More Actions option, choose Download PKI Cert.
- The certificate password dialog box opens.
- Create a new password to use here and click Download if this is your first time downloading this certificate. Keep track of this password since you need it to redownload the certificate.
- Enter the password you already created if you’re downloading this certificate again to replace one lost or expired.
- Install the certificate on the user’s device or provide it to the end user via a secure channel and advise them to do so. Windows automatically does the certificate installation, as well as MacOS X. Use certificate installation procedures tailored to individual browsers on Linux.
Limitation of OneLogin Device Trust
Although the general reviews among the customers of the OneLogin portal have been positive, and it has been a market leader for a very long time, some customers found its password reset requests really cumbersome, according to reviews gathered by G2.
Some users were also concerned about the security aspect of their organization, considering the same passwords were used for multiple applications, so in case of hacking, all the data associated with the applications would be exposed. Also, in case of a password loss, access to all the applications would be compromised, and the OneLogin password reset policy would consume a lot of time.
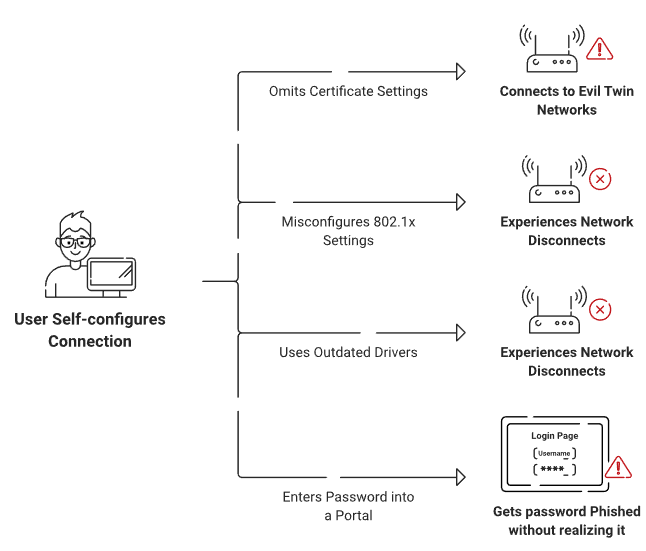
Also, while using OneLogin, you need a reliable onboarding solution to scale the certificate distribution for the entire network since it does not support the scaling itself.
Smooth Onboarding to 802.1x Certificates
Similar to OneLogin, we at SecureW2 have been practicing the concept of device trust from our very inception. In addition to practicing CBA, we have the capability to distribute certificates to your entire network.
We offer numerous innovative solutions that configure and auto-enroll managed devices for certificate-based authentication and can deploy certificates to any MDM via API gateways. It also addresses the entire lifecycle of certificates and has more certificate management features than most IAM solutions. Even for unmanaged devices, we have JoinNow MultiOS that vastly reduces the burden of admins by enabling end-users to self-configure their unmanaged devices/BYODs with just a few clicks.
And guess what! We have been a partner of OneLogin and officially support their Cloud Identity solutions. Our advanced policy engine and Dynamic Cloud RADIUS can easily communicate with OneLogin and enforce user policies at the time of authentication.
You can book a call with us or check out our pricing page to see if SecureW2’s onboarding solutions fit the authentication needs of your organization.