X.509 certificates play a crucial role in guaranteeing the authenticity and integrity of communications. However, organizations that rely on the security provided by certificates also need to address a concern: how to store their X.509 private keys securely. Private keys, counterparts to public keys in X.509 certificates, are central to maintaining data security.
Private keys are used to decrypt data that has been encrypted with the corresponding key. They must remain confidential and accessible to their owner. The consequences of a stolen key can be devastating, leading to data breaches, identity theft, and compromised communications. Therefore, safeguarding private keys is crucial for preserving an organization’s reputation and security. This article outlines strategies to ensure the storage of X.509 private keys while mitigating the associated risks.
What is an X.509 Private Key, and How Does It Work?
An X.509 private key is one-half of the pair of keys used in asymmetric cryptography. To understand how it works and why it matters, you’ll need first to understand the cryptography it’s based on.
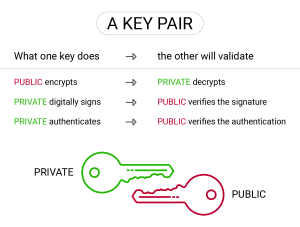
Asymmetric cryptography, frequently denoted as public-key cryptography, is indispensable in safeguarding electronic communications and transactions. This cryptographic method is fundamentally predicated on a pair of keys—a public and a private one. Every individual key in the duo fulfills a unique yet complementary function, enhancing the system’s security and integrity.
The public key is distributed and openly shared; it functions as an encryption lock. The principal function of this component is to enable secure correspondence with the entity that possesses the requisite private key. Conversely, the private key is maintained in strict confidence and functions as the corresponding key for the public lock. Decrypting the information encrypted with its corresponding public key requires this key.
The ingenuity of asymmetric cryptography lies in meticulously securing the private key while permissibly distributing the public key. To transmit sensitive data to the holder of a public key, one encrypts the data using said key. The original information can only be decrypted and accessed by the individual who possesses the assigned private key.
Employing two mathematically related keys—one designated for encryption (public) and the other for decryption (private)—establishes a strong and reliable basis for ensuring secure communication and authentication. It serves as the foundation for many cryptographic protocols, notably the X.509 certificates we previously deliberated upon, digital signatures to ensure the integrity of documents, SSL/TLS for secure web navigation, and others. In examining optimal methods for preserving X.509 private keys, it is critical to possess a foundational knowledge of asymmetric cryptography to comprehend the significance of secure key management.
X.509 private keys protect sensitive data and communications.
How are X.509 Private Keys Used?
In digital security, X.509 private keys have several uses. SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates, which protect online interactions such as web surfing, email, and instant messaging, are among the most used applications. When you visit a secure website (marked by “https” in the URL), the server’s X.509 private key protects the connection by encrypting the data passed between your browser and the server.
Furthermore, X.509 private keys are required to produce and verify digital signatures. They enable individuals and organizations to authenticate and validate documents, communications, and code. Users can demonstrate that the material has not been changed and originates from the claimed source by signing with their private keys.
⦁ Client Certificates: These certificates make it easy to prove identity because they are linked directly to known accounts like email addresses or employee files. Client Certificate Authentication uses these certificates to prove that a person or device is who they say they are.
⦁ Server Certificates: Server certificates are an important part of setting up secure channels, especially for TLS links, because they are used for identification. Because this setup is atomic, there is cryptographic proof that the private route is connected to a certain party, usually an organization that has been audited.
⦁ Codesign Certificates: As a server certificate type, codesign certificates show who published software and ensure it hasn’t been messed with, protecting its security. It gives a tamper-resistant way to deliver software by acting as a delayed secure channel.
⦁ CA Certificates: While the CA certificate shows that the CA is who they say they are, the private key is mostly used to sign other certificates. This important feature lets other people check the validity of certificates the CA gives, demonstrating its important part in the Public Key Infrastructure (PKI).
Why is Secure Storage Crucial?
It is of the utmost importance to safely store X.509 private keys because they are crucial to keeping digital interactions safe and reliable. Furthermore, private keys have a range of use cases that require varying levels of security.
Client certificates, for example, authenticate users or devices by being directly linked to a recognized account. During an SSL connection, server certificates are used to establish secure channels, verifying the identity of a party. Coding certificates serve the purpose of verifying the integrity of software by identifying its publisher. Certificate Authority (CA) certificates are used to sign other entities’ certificates, verifying that those certificates, in turn, came from a trusted CA.
Stealing the private key of a client certificate belonging to a single user is one thing. When client certificate private keys are compromised, the potential damage is comparatively limited; an adversary could assume the identity of a user, creating a security vulnerability that can be easily remedied by deactivating the compromised user account. Nevertheless, the importance of certificates verifying secure channels to organizations and, more significantly, Certificate Authority (CA) certificates increases dramatically as one climbs the hierarchy of use cases.
The consequences that arise from the compromise of a private key linked to a CA certificate are especially severe. A breach of this nature can potentially facilitate extensive identity fraud, encompassing individual users and entire organizations. The seriousness of this menace is further underscored by the critical function that CA certificates perform: verifying the identities of other entities within the PKI framework. Suppose the private key for a CA is compromised. In that case, every single certificate issued by that CA is no longer trustworthy, as that CA can now be used to issue illegitimate certificates.
Furthermore, the risks of storing private keys are multifaceted, as different subcategories present differing levels of peril. A client certificate employed for network access, although still requiring caution in storage, has a distinct effect compared to one used to access sensitive email accounts.
Notably, public and private root CAs frequently utilize air-gapped devices completely isolated from any network or internet connection. This rigorous precaution is established to prevent severe repercussions in the case of private key deterioration, acknowledging the critical function these keys fulfill in confirming the legitimacy of a multitude of certificates.
Emphasizing the importance of considering the tenure of a certificate, and consequently, its private key, is crucial when assessing security. Long-lived certificates, including certain root CA certificates that have been in effect for decades, necessitate increased security vigilance compared to shorter-lived certificates. This is because the prolonged duration of the certificates increases the time frame during which private key thievery could occur. Fundamentally, protecting private keys does not adhere to a standard approach; rather, it necessitates a sophisticated strategy customized to the particular characteristics and importance of the certificates at stake.
Private Key Storage Options
Various methods have been developed to ensure the secure storage of private keys. Throughout history, encryption has been utilized, whereby the private key is frequently encrypted utilizing a password derived from the user’s account. This approach guarantees that the private key remains encrypted without the user authenticating into the system.
Decrypting the certificate with specific user input, such as a passphrase, provides an additional layer of security. Sophisticated hardware solutions such as Trusted Platform Modules (TPM), Hardware Security Modules (HSMs), and Secure Enclaves, which minimize the risk of unauthorized duplication by performing private key operations on dedicated hardware, are introduced due to technological progress.
Notwithstanding these precautions, obstacles endure, and in the case of exceedingly critical operations, such as those about CA private keys, supplementary measures such as air-gapped devices and private key certificates are frequently employed. Various alternatives exist on the server and cloud sides regarding private key security. These alternatives span from outsourcing entry point security to web servers with restricted access to storing server certificate private keys. This exemplifies a comprehensive approach to safeguarding private keys in the dynamic realm of digital security.
Best Practices for Storing X.509 Private Keys
Properly securing X.509 private keys is critical for maintaining the integrity of digital security. Different storage methods provide varied levels of security, and understanding their intricacies is critical for determining the best option for a specific use case.
Encrypted Storage on Devices
Although private keys are frequently encrypted, this approach has certain drawbacks, particularly in automated machine authentication situations. Vulnerabilities arise when the device must decode the private key independently. However, encryption with a derivative of the user’s account password provides an additional layer of security when coupled to a user account. Decryption becomes nearly unattainable without user authentication, rendering it appropriate for scenarios where semi-automatic operation is to be tolerated.
Passphrase Protected Encryption
Private keys may be encrypted with a passphrase exclusive to the user to bolster security. This reduces the likelihood of theft, assuming strong passphrases that are challenging to deduce through brute force. Enforcing decryption with explicit user input introduces an additional level of security, presenting a formidable challenge for adversaries seeking to acquire the private key without the user’s participation.
Specialized Hardware (HSMs, TPMs, Secure Enclaves etc.)
Secure Enclaves, Hardware Security Modules (HSMs), and Trusted Platform Modules (TPMs) are a few examples. Unlike conventional approaches that utilize memory protection to execute private key operations on the CPU, specialized hardware guarantees that the private key remains within the device at all times, rendering it exceedingly resistant to duplication. Certain solutions incorporate user engagement, such as inputting a PIN or tapping a button, thereby augmenting security.
Air-Gapped Devices and Private Key Ceremonies
Air-gapped devices and private key ceremonies are utilized in critical operations, particularly those involving private keys issued by Certificate Authorities (CAs). Physical isolation of air-gapped devices reduces the vulnerability to remote attacks. At private key ceremonies, procedures are tangibly verified by several individuals to guarantee the highest level of security.
Server and Cloud Storage Options
Depending on the cloud or server environment, storage options vary. Several methods include outsourcing entry point security to cloud providers and holding server certificate private keys on web servers with restricted access. Automatic renewal and the reduction of server certificate lifetimes are acquiring traction as measures to mitigate the impact of stolen private keys.
Increased Security Measures for Important Certificates
Enhanced security measures are indispensable for codesigning certificates and private CA certificates, which are critical. This entails the implementation of secure cryptographic storage, role-based access policies, and on-network solutions such as Hardware Security Modules (HSMs). Although the aforementioned measures effectively deter direct theft, supplementary audit capabilities serve to detect and address malicious activities.
When determining the most suitable storage method, it is critical to comprehend the certificate’s characteristics and significance. An all-encompassing strategy integrating encryption, user engagement, and specialized hardware offers a resilient barrier against potential perils that may compromise X.509 private keys.
Generating Strong Private Keys
Generating your X.509 private keys is the starting point for their security. Always use a reputable and secure key generation process that employs cryptographic libraries and algorithms with a track record of reliability. Generate lengthy, complex keys with enough entropy to withstand brute-force attacks. Avoid common pitfalls, including easily guessed passphrases and defective random number generators.
Implementing Access Controls
Implement stringent access controls to protect your X.509 private keys from unauthorized access. Access should be restricted to authorized personnel, and authentication mechanisms, such as robust passwords or multi-factor authentication, should be in place. Role-based access control (RBAC) can ensure that individuals only have access to the keys required for their duties. Audit and monitor key access regularly to detect and respond promptly to any suspicious activity.
Regularly Updating and Rotating Keys
Private keys for X.509 should not be static over time. Instead, organizations should create a key rotation strategy that produces new keys and retires old ones regularly. The frequency of key rotation should be selected depending on the appropriate degree of security and your organization’s particular demands. However, rotating keys at regular intervals is commonly recognized as excellent practice.
The rotation of keys is an essential defense against possible security breaches. A well-defined key rotation procedure mitigates the potential harm if a private key is compromised. You can prevent hostile actors from exploiting stolen credentials to access sensitive data or impersonate legitimate businesses by quickly replacing compromised keys with fresh ones.
Furthermore, upgrading and rotating keys are closely related to the administration of the X.509 certificate. Certificates often have a limited validity duration, and organizations must efficiently manage certificate lifecycles. This includes canceling and renewing certificates as needed to keep them safe and trustworthy.
This is where SecureW2’s product suite comes into play. We provide managed device gateways that enable managed device certificates to be renewed automatically. This guarantees that certificates are kept up to current without human intervention, lowering the risk of certificate expiration and the resulting security issues. Furthermore, our JoinNow MultiOS streamlines the certificate enrollment process for users, making it simple for them to get and renew certificates as needed, boosting the security and efficiency of your organization’s certificate administration.
Backing Up Private Keys Securely
There are numerous causes of data loss, including hardware failure, accidental deletion, and disaster scenarios. Therefore, backing up your X.509 private keys is essential. However, these alternatives should be given the same level of protection as the primary credentials. Ensure backups are stored in secure, off-site locations and their access is strictly regulated to prevent unauthorized retrieval and misuse.
By adhering to these best practices, you can substantially increase the security of your X.509 private keys, thereby minimizing the risk of data breaches and preserving the integrity of your digital communications and transactions.
Prioritizing X.509 Private Key Security
Protecting X.509 private keys is essential for solid digital security. In this blog, we have discussed the significance of these keys, the dangers of inappropriate storage, and the recommended practices for keeping them secure. To strengthen the security of these vital assets, it is essential to use the proper storage technique, private solid key generation, implementation of access restrictions, frequent key rotation, encryption, and safe backup procedures. It is critical to understand that losing X.509 private keys may have serious consequences, including data breaches, financial losses, and reputational harm.
SecureW2 can greatly help X.509 private key management and security through our managed cloud PKI. We offer various solutions and software for organizations to securely maintain and use X.509 certificates. You can easily manage access restrictions, expedite certificate issuing, and assure industry compliance with SecureW2.
Our experienced team helps organizations of all sizes optimize their X.509 certificate-based security, including secure key storage. Contact us today to streamline your certificate management.