As the world moves more and more to the cloud, we’ve seen a common trend: Organizations are unsure how to use their Cloud Identity providers for 802.1X / WPA2-Enterprise network authentication. Many relied on LDAP historically to connect their applications to Active Directory, but as they moved to the cloud they quickly realized that certain applications, such as Wi-Fi and VPN, would not work with Azure AD.
So the question remains: how do you use Azure AD with 802.1X?
You can go about it in a couple of ways: you can sync your Azure AD with an LDAP server or use Azure AD (Microsoft Entra ID) to enroll each network device with an x.509 certificate which can be used for passwordless Wi-Fi and VPN authentication. For the former, you can choose an on-prem LDAP server or cloud-based LDAP server, but you’d likely still be using passwords. The latter is a passwordless solution that leverages certificates (better decision-making context, user experience, over-the-air security, and future-proofing) and also doesn’t require any on-prem servers.
Sync your Azure AD (Microsoft Entra ID) with an LDAP Server
Some organizations have adapted by performing an LDAP sync, duplicating their Azure AD on-premise so LDAP applications can continue on. For organizations with existing credential-based 802.1x, this can be a good temporary solution that allows them to move to Cloud Azure AD, but continue to use their legacy servers.
However, as one Microsoft employee expressed in a forum about the Azure AD-LDAP synchronization, configuration guides are hard to find and what you can find are difficult to configure. At a high level, you need to build an OpenLDAP server, install Azure AD Connect, and manually configure an Azure AD federation. The employee implored the audience to find an easier method.
There are third-party solutions that handle the LDAP sync by providing cloud-based LDAP servers. While you are able to migrate away from your on-prem infrastructures, it still seems like a step back because you’re authenticating with passwords and using vulnerable authentication protocols like PEAP-MSCHAPv2, which industry titans have recommended moving away from.
So to summarize, an LDAP sync can be a good temporary solution for organizations that want to move their AD to the cloud, but it’s difficult to set up and due to security concerns it’s not a long-term solution.
Leverage Azure AD to Enroll x.509 Certificates
The second option is adopting a passwordless solution by using Azure AD to issue and manage x.509 Digital Certificates, which can be used for a number of applications like Desktop Login, VPN, and 802.1X Wi-Fi. Authenticating via certificates is similar to passwords; you present identification to your Access Point (AP), it forwards it to the RADIUS server, and then the RADIUS tells your AP whether you are allowed access or not.
However, there are a few key differences. For starters, certificates are more secure than passwords. Certificates provide much more context that is used for security decisions. They give a ton of information about the device: who owns it, type of user attached to it, make, model, and conditional access in your organization. User experience and security are improved simultaneously because there are no more password-related disconnects and no threat of evil-twin attacks that steal credentials over-the-air. These are just a few of the reasons why the NSA and CISA have both recommended certificates.
Lastly, for organizations that use Azure AD as their Identity Provider, it eliminates the need for on-premise servers. Windows servers have been the victim of multiple zero-day attacks in the past year, and are among the most targeted vulnerabilities in organizations. .
Historically, organizations shied away from using certificates. They required Public Key Infrastructures (PKI) which were difficult to setup, and certificates were impossible to manage. Today, however, PKIs can be configured as an extension of Identity Providers and Device Management Software (MDMs), making certificate enrollment and management a mostly automated process.
With the right onboarding software, BYOD devices can self-service themselves using their Azure AD credentials to receive a certificate and 802.1X settings. For environments that use Intune or other MDM/EDMs, you can push out configuration profiles that instruct devices to auto-enroll themselves for certificates using an API.
Want to learn how to set up certificate-based 802.1X authentication (EAP-TLS) with Azure AD? Below we laid out a basic overview. For the full documentation, check out our page on how to configure WPA2-Enterprise with Azure..
How to Use Certificates to Tie Network Security with Azure AD
The process is broken down into two phases: one-time enrollment and runtime authentication. We’ve provided a high-level overview of how you can set up certificate auto-enrollment for your Intune or other MDM devices.
- One-Time/Renewal: Configure your MDM platform with our PKI services to send out configuration profiles directing managed devices to auto-enroll and auto-renew for a certificate and self-service for 802.1X.
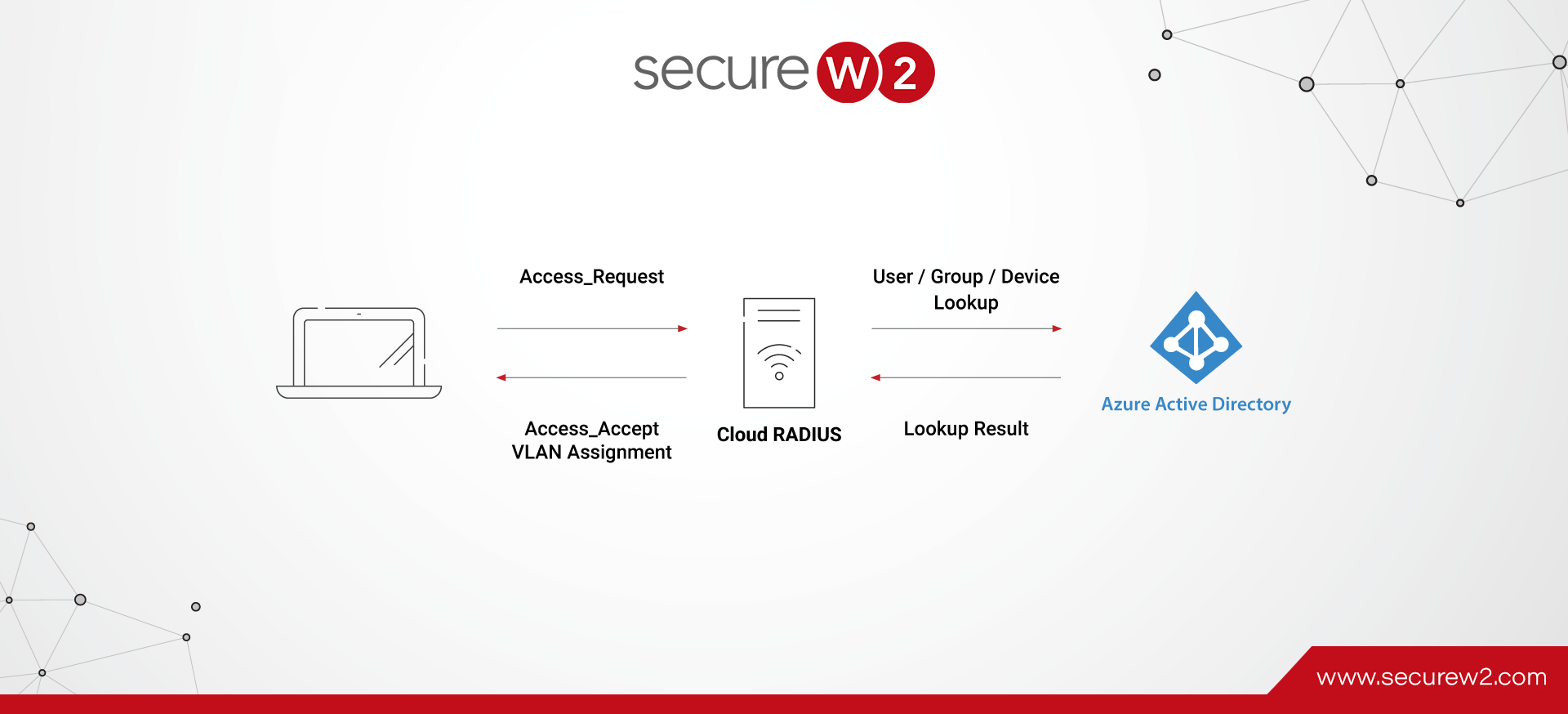
- Ongoing Authentication: Cloud RADIUS will authenticate the device for Wi-Fi access by directly communicating with your Azure AD.
Once the device requests Wi-Fi or VPN access, our Cloud RADIUS will directly communicate with your Azure AD (or whatever Cloud Identity you have) to verify the user and authorize network access at the time of authentication. Now, we have a passwordless 802.1X system tied directly with our Azure AD.
A Quick Guide to Using Azure AD for 802.1X
We’ve constructed a quick guide on how to set up Azure AD as an SSO for Certificate Enrollment and 802.1X Onboarding. Your end-users can easily self-service themselves for certificate-hardened 802.1X with their Azure credentials.
1. Create a SAML Application in Azure Portal
End-users can enter their credentials into the SAML app, which are then sent to and verified by Azure AD. Once Azur AD sends back attributes, the SAML app will share them with SecureW2 PKI to issue certificates.
2. Test the SAML Application
Add yourself as a user to test the SAML app for any bugs. If you go through the onboarding process with no issue, Azure AD and SecureW2 have successfully connected.
3. Mapping Azure AD Attributes
This is where you can map out the attributes sent by Azure AD and encode them onto certificates.
Passwordless RADIUS Authentication with Azure AD
RADIUS is a standard protocol to accept authentication requests and to process those requests. If you use certificate-based Wi-Fi authentication (EAP-TLS) with Azure AD, you can set up Azure AD with any RADIUS server. While you may think that it’s not worth it to set up a PKI just for Wi-Fi, the growing risk of credential theft combined with the improvements in PKI technology have resulted in EAP-TLS becoming the industry standard form of Wi-Fi authentication.
SecureW2 provides both an easy-to-use Managed PKI and a Cloud RADIUS, giving organizations everything they need to set up certificate-backed EAP-TLS on their network and ditch passwords for good.
Along with our Cloud RADIUS, SecureW2 grants access to industry-first technology that allows Cloud RADIUS to talk to any IDP to dynamically update your users and policies. It’s so easy to set up, the average deployment time is often under an hour!
Using our Cloud RADIUS also significantly reduces the costs associated with an on-prem RADIUS server by requiring significantly less time and money needed for maintenance and general upkeep.
Will this mean Azure AD will be used as a Wi-Fi SSO?
Yes! SecureW2’s onboarding clients will use Azure as a Wi-Fi SSO, except the credentials won’t be used for Wi-Fi authentication. Instead, they will be used to enroll for a Wi-Fi certificate, which will then be used for authentication. This not only provides a high level of flexibility but also stronger overall cybersecurity. Certificates work with any RADIUS server and AA and prevent your Azure AD credentials from being stolen over the air.
Can I use Azure AD MFA with 802.1x?
It’s possible that your infrastructure may not support certificate-backed VPN enablement. Luckily, you can still use Azure AD MFA with certificates.
Many end-users complain that MFA is annoying to use when connecting to Wi-FI, especially if they’re students or faculty walking around campus. Certificates prevent end-users from having to enter their credentials every time they near a new Access Point. No matter where they are, their certificate will automatically connect them to Wi-Fi with no interruptions.
So the answer is yes, you use Azure AD credentials to enroll for certificates for 802.1X authentication. You can configure any form of Multi-Factor Authentication (MFA) to be used during the 802.1X certificate enrollment phase.
SecureW2 Can Make Azure Integration Easy
With SecureW2 you can have your secure network set up in a matter of hours and have a support team ready to assist you with any of your questions. We have affordable solutions for organizations of all sizes, check out our pricing here to see if we can be of service.