One of the biggest hurdles in certificate management is the lack of experience in finding the proper certificate management solutions. Often, administrators are of the notion that their only option for certificate management is pricey PKIs exclusive for enterprise, that have all the tools their organization needs, or a hard to manage and expensive custom PKI, which requires manpower and expertise to run.
Whether it’s a misconfigured setting or lost credentials, simple mistakes can prove costly when considering network security. Especially when a lapse in judgment can cost companies thousands of dollars.
In order to combat this, cybersecurity experts have been diligently working to maximize automation throughout the certificate lifecycle thus minimizing the chance of a security breach caused by an avoidable accident.
Manually managing certificates can be costly due to the hours of maintenance and costly expertise that’s required to sufficiently manage your own custom-built PKI. It is much simpler and more cost-effective to use a Managed PKI that comes with automated tools such as Identity Lookup and Certificate Revocation Lists (CRL). This article will detail the best practices used in the field regarding Certificate Management, and how they can be automated.
Managing Certificates with a Certificate Revocation List (CRL)
A CRL is a list of certificates that have been revoked by the certificate authority that issued them before they were set to expire. This is especially helpful if a device is stolen that contains a certificate. A RADIUS server rejects a connection request from a device if the device’s certificate serial number is contained in the CRL. The Certificate Authority is the one that maintains this list, and the RADIUS server periodically downloads this list by sending a query to the CA.
There are two types of CRLs: A Delta CRL and a Base CRL.
- Base CRL: Large file that contains all non-expired revoked certificates.
- Delta CRL: Small file that contains all non-expired revoked certificates that have been revoked since the last base CRL was published.
A well-configured CRL ostensibly runs autonomously, meaning you rarely need to interact with the CRL directly. SecureW2’s PKI solution allows you to manage and revoke certificates in minutes vastly increasing your network’s security.
Managing Certificates with Identity Lookup
During the authentication process, identity lookup validates that a user is active within the organization by checking the identifying information against the existing users in the Identity Provider. This helps as a last line of defense if a disgruntled employee were to perform any malicious activity before the CRL was updated to revoke their network access.
This tool is invaluable to organizations that value security, however historically it was only available to companies that possessed an LDAP. SecureW2 is able to eliminate the need for an outdated Active Directory or LDAP Server by developing industry-exclusive Identity Lookup Technology for SAML-based Identity Providers.
The entire process being automated makes managing certificates far easier and more efficient for the end-user and IT personnel.
Configuring Custom Certificate Expiration
Certificate expiration is an automated response that occurs at the end of a predefined certificate lifecycle. When the certificate was generated, it was given a certain amount of time that it will remain valid for – typically between 1 and 5 years. At the end of this period, the certificate will become invalid automatically.
This allows you to set a predetermined amount of time that a given certificate is valid and immediately revokes the certificate’s ability to access a network after the time has elapsed.
Certificate Expiration Notifications
Sending out automated certificate expiration notifications is critical to maintaining a secure network. When we broke down how the Experian Data Breach occurred in 2017, one of the big reasons why it happened was a certificate expired and no one noticed.
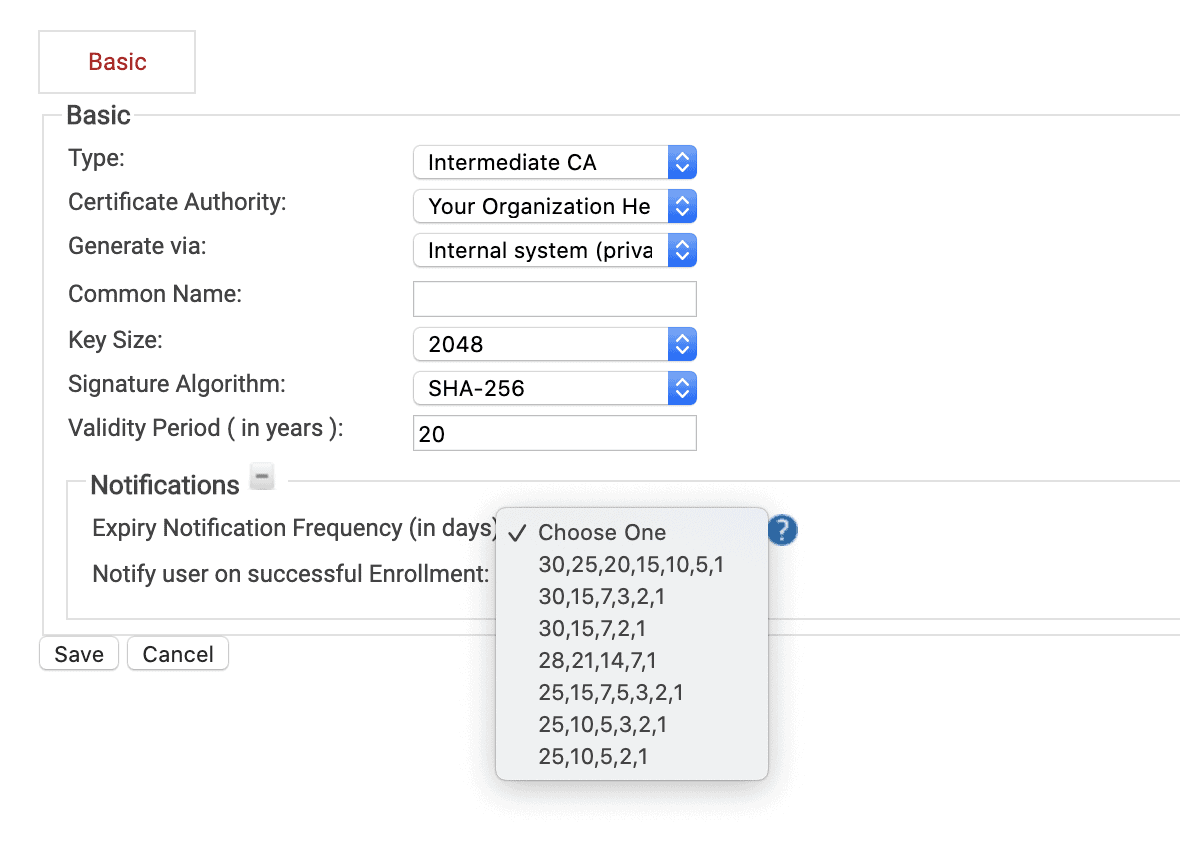
That’s why we recommend all our customers take advantage of our automated certificate expiration notification emails. When you generate a CA in SecureW2, you can select when and how often end-users will be notified when their certificates are about to be expired. The screen above shows the options you have available. SecureW2 will automatically email your end-users at the intervals (shown in days) above and direct them on how to renew their certificates.
Using a GUI to Index and Manage Certificates
While it may seem simple, and definitely isn’t following our theme of automation, having an easy-to-use Graphical User Interface (GUI) can streamline your IT operations just as effectively as any automation could!
Take for example our Certificate Management GUI:
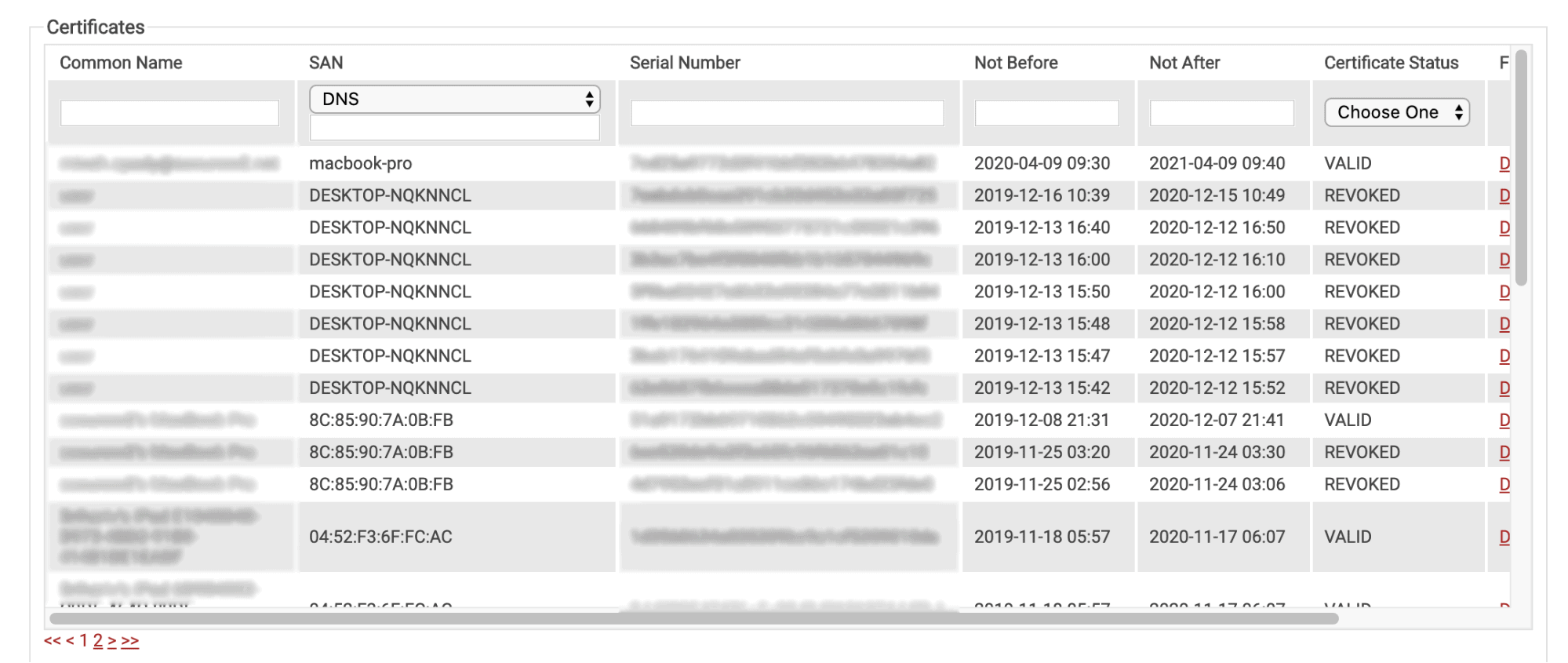
When you’re setting up the most time and cost-effective solution to manage certificates, one of the best things you can do is provide a great user experience. Having a GUI is great because it makes certificate management simple enough for your helpdesk. You can easily search for a person by name, MAC Address, Computer Model, or any other attribute you choose to populate your certificates with.
Customers often give help desk users the ability to view and search through certificates so they can help troubleshoot issues with end-users. This is a great way to make your IT operations more efficient, without having the risks of giving complete access to your PKI.
Automating Certificate Generation for Managed Devices
Distributing certificates to managed devices can be a daunting task, especially for larger organizations. However, using SCEP (Simple Certificate Enrollment Protocol) can simplify the enrollment process so administrators can automatically enroll any device for a certificate without any end-user actions necessary.
SCEP is a protocol that allows devices to easily enroll for a certificate by using a URL and a shared secret with the CA to communicate with a PKI. Mobile Device Management (MDM) software commonly uses SCEP for devices by pushing a payload containing the SCEP URL and shared secret to managed devices.
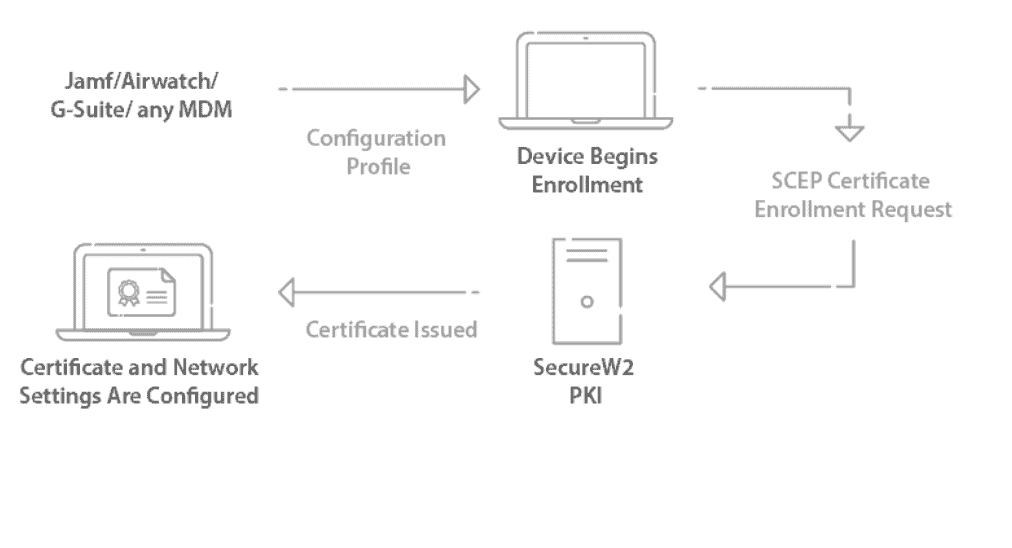
The SecureW2 Management Portal has the necessary components to deploy a SCEP Gateway with any major MDM in less than an hour. You can easily:
- Create a Custom Private Intermediate CA.
- Create a Signing CA, signed by the Intermediate CA.
- Generate the SCEP Gateway API URL and Shared Secret.
- Optional: Configure Custom Certificate Templates and Enrollment Policies.
Enabling End Users to Provision Certificates Themselves
Relying on manual configuration by end-users introduces a bevy of potential missteps and security challenges. 23% of data breaches are caused by human error (IBM) and should a user configure something wrong, the result could be catastrophic for your network as well as causing more load on the IT staff.
Luckily, SecureW2 delivers powerful tools that automate the wireless network onboarding for your users via a self-service method, thus relieving both the end-user and administrators of a tremendous stress inducer. We provide dissolvable clients for every operating system, that integrates with any Identity Provider so that end users can easily provision their devices for certificates and 802.1x network authentication.
Visibility and in-depth reporting are always a challenge with any network, so SecureW2’s products monitor all aspects of the onboarding process and allow network administrators to easily monitor patterns of errors and take full advantage of their network’s security features.
Using SecureW2 to Efficiently Automate Certificate Management
Configuring your certificate management system is of the utmost importance for properly securing your network.
SecureW2 offers an affordable and easy solution for managing your entire PKI, allowing organizations to rely on an efficiently automated system, minimizing human error wherever possible. Check out our pricing page to learn more.