Apple Managed Device Attestation (MDA) was announced at WDC22 to a lot of excitement among the security community. MDA is something that Apple has developed so that organizations can get higher assurance about the devices they are trying to authorize access to. This is pretty awesome because everyone is struggling to adopt Zero Trust philosophies, and Device Trust, the act of identifying devices that are managed by your organizations are compliant with your security policies, is a foundational part of Zero Trust security.
Many blogs are talking about what Apple Managed Device Attestation is, but we didn’t feel they explained the core concepts in a way that everyone could understand. So we actually met with one of the Security Engineers at Apple who has been helping organizations adopt Apple MDA, who helped us understand MDA to develop our support for the feature and write this blog.
What is Apple Managed Device Attestation?
In the most simple way we can explain it, Apple MDA is a combination of a protocol and Apple Servers that give macOS and iOS devices the ability to accurately say things like “I am an authentic Apple Device” or “My unique ID is 1123XYZ, and that exists in your Jamf MDM”. As you can imagine, the Device Trust that this gives organizations is super powerful and can be used to create security policies for a lot of things.
What was announced in WWDC 2022, was that Apple has created a process that their devices can use so that third parties can have their legitimate Apple devices validate their identity by talking to Apple Servers. The graphic below gives a high-level overview of how this works:
Essentially, Apple devices when prompted can use their Secure Enclave to securely communicate with Apple’s servers. The Secure Enclave is a critical component, as it keeps a unique identifier and certificates hardware-locked to the device. It can use this to securely communicate with Apple Servers, and the servers can attest to the authenticity and identity of the device. According to Apple’s own documentation, you can get the following data using Managed Device Attestation:
- The device is a genuine Apple device
- The device is a specific device
- The device has certain properties (for example, the serial number)
- The private key is hardware bound to the device
As a Public Key Infrastructure (PKI) vendor, we are working with Apple so we can use the Device Trust that is gained using Apple MDA to enroll devices for certificates that can be used to prove to other systems (Wi-Fi, VPNs, Application Firewalls), that the device that is requesting access is in fact a trusted device. To do that, we use the Automated Certificate Management Environment (ACME) protocol, and we will explain how that works with MDA in the next section.
ACME + MDA = Super Secure Certificate Management
Automated Certificate Management Environment (ACME) is a protocol, with a pretty self-explanatory name. It allows a PKI to automate the management of certificates. In this case, our JoinNow Connector PKI can use it to create unique certificate enrollment policies that factor in the information received from Apple MDA. The diagram below outlines how the JoinNow Connector PKI works with an MDM to distribute the ACME Payload, which will use Managed Device Attestation during the certificate enrollment process.
Using Managed Device Attestation during the certificate enrollment process makes it so only trusted and authentic devices can receive a certificate. Then, this certificate can be given to other systems that can also use this proof of Device Trust to authorize high levels of access. Wi-Fi is a very common use case for Certificates created using MDA. Network Administrators can make sure that all their trusted devices are segmented away from untrusted devices, preventing them from any viruses that untrusted devices might bring in.
Does Jamf Support Apple Managed Device Attestation?
In theory, any MDM can support Managed Device Attestation. This is because Apple designed the attestation to go through the device. All authentic Apple devices are capable of using its Secure Enclave to request and receive an official attestation from Apple’s servers, it’s just up to the MDMs to prompt the device to perform an Attestation check and store the data.
Jamf created a blog that talked about Apple Managed Device Attestation in October 2022, in response to Apple’s announcement in WWDC22. In this blog, they generally explain what Apple MDA is, and how it relates to Jamf, but there weren’t any details of how it would be implemented. However, in this recent video published in April 2023, Jamf stated the following:
“The device performs a check-in with Apple attestation servers, and ultimately returns a certificate that is signed by Apple that attests that the device is genuine. The certificate is validated by Jamf Pro, and stored with other inventory data. The results will be shared with Jamf’s security tools, and available for consumption for other third-party systems and tools via the Jamf Pro API.”
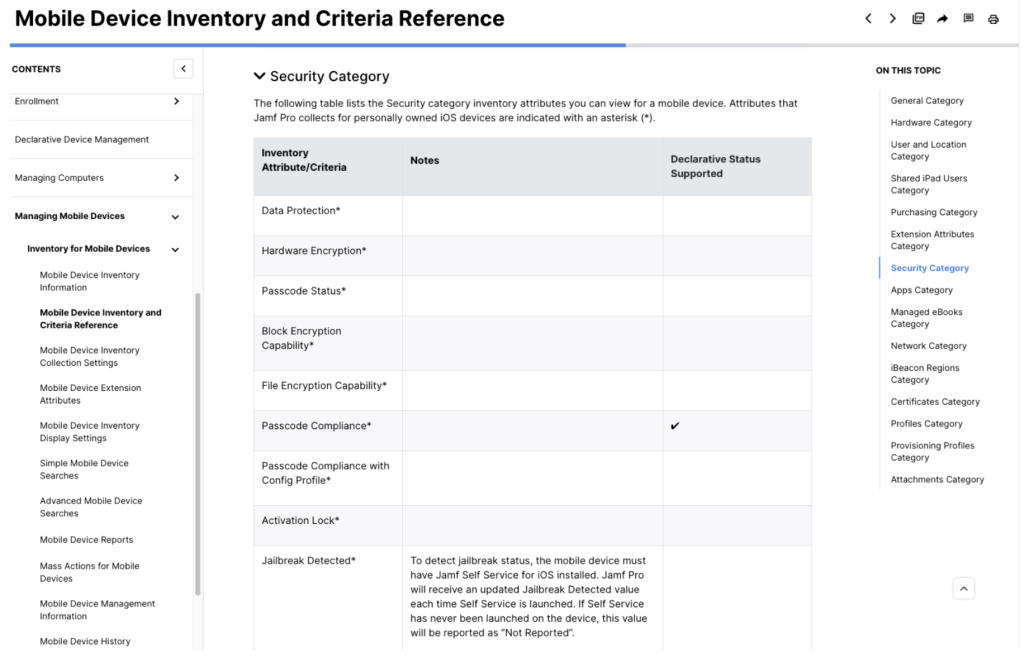
While it’s not clear what data Jamf collects from Apple Managed Device Attestation (as of May 16th, 2023), a logical assumption would be that it would be clarified in the Security Category of Jamf’s Inventory Data which can be found here.
Is Managed Device Attestation Supported on iOS?
Yes, Managed Device Attestation is supported on iOS and macOS. According to Apple’s own documentation (published on March 27th, 2023), Managed Device Attestation is available from the following operating system versions:
- iOS 16 +
- iPadOS 16.1 +
- macOS 13.1 +
- tvOS 16 +
How do Organizations Adopt Apple MDA?
The most common way organizations will adopt Apple MDA is through their MDM and PKI providers. Storing the data that Apple Managed Device Attestation provides in your MDM, or in the form of a Digital Certificate gives organizations a way to tell all their systems that devices are trusted, legitimate, and corporate-owned.
Most organizations we talk to are eager to use Managed Device Attestation for the following use cases:
- Issuing unique certificates to trusted, managed devices, for Wi-Fi, VPN, and Application Security
- Segmenting untrusted and trusted devices on the network
- Making sure MDM-managed devices are legitimate and not rooted
If your organization is interested in adopting Apple MDA, click this link for a Free Demo of our platform, and one of our engineers can walk you through how the solution works.