*Updated Feb 2021
The dust has settled on the Dec 2020 Android 11 update and, for better or worse, the effects on network authentication have not been as drastic as predicted.
It appears that the requirement for server certificate validation is not being rolled out to all Android 11 devices simultaneously. As of this update, only Google Pixel 3 and newer Pixel models have been affected.
The remaining majority of Android devices are expected to be phased in over an undetermined length of time, probably dependent on make/model/carrier of the device. Our original, unaltered article is preserved below:
***
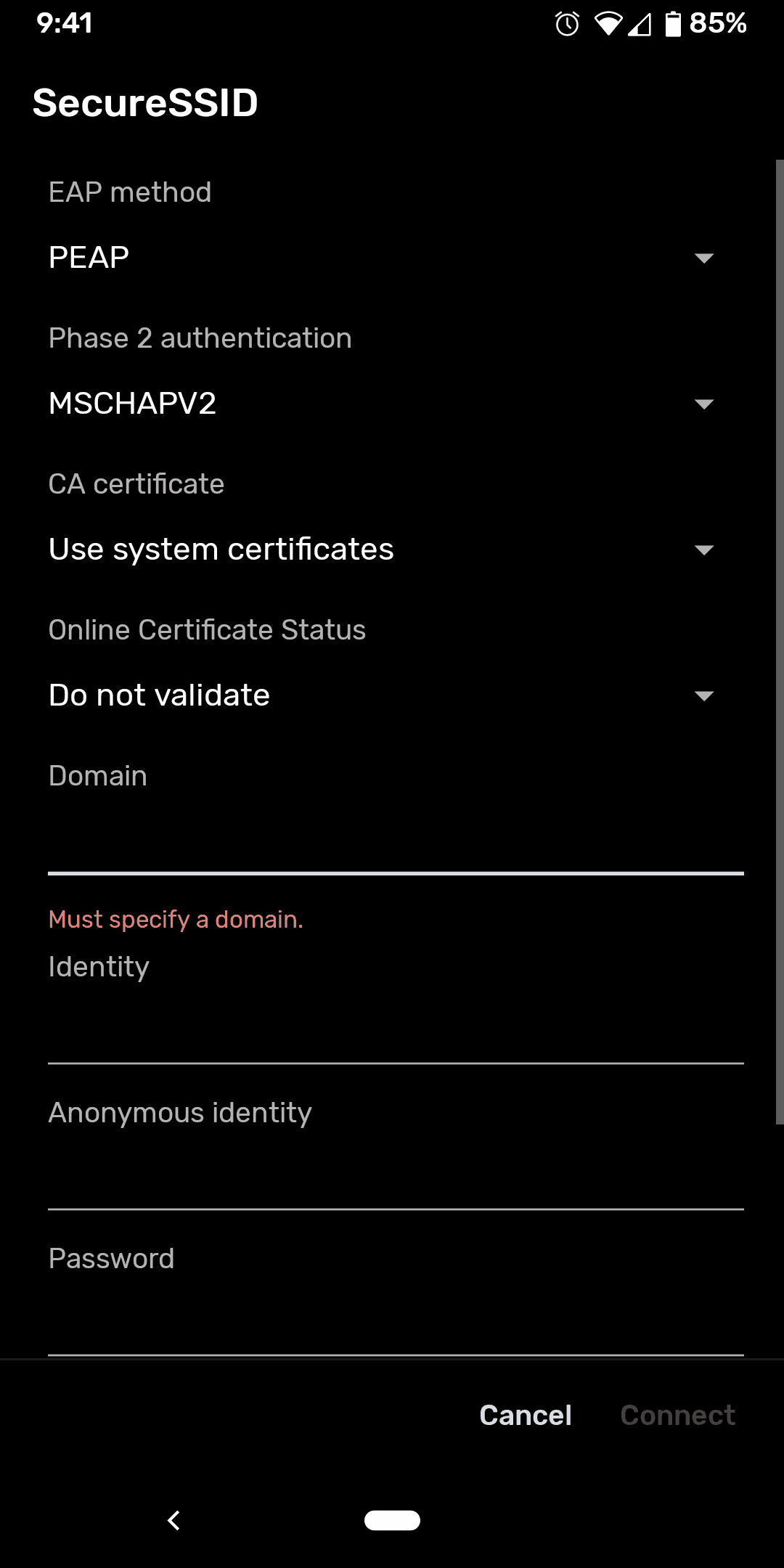
In December 2020, the planned Android 11 QPR1 security update will disable the ability to select “Do not validate” for the “CA Certificate” dropdown in network settings for a given SSID. Details can be found in the WPA3 Specification from the Wi-Fi Alliance.
Note that the changes are in the WPA3 specification, not in Android documentation. This implies that server certificate validation will be required for other operating systems in the future.
While the change itself is a minor one, it will have a disproportionately far-reaching impact. Many organizations use this setting to avoid implementing proper EAP server certificate validation due to the perceived difficulty of configuring x.509 digital certificate authentication.
Come December, Androids configured with this workaround will find their Wi-Fi services interrupted. Organizations need to address this issue now to prevent chaos as updates gradually roll out to Android devices throughout the month.
This article discusses why Androids are being forced to use server certificate validation and a solution for easily implementing the validation in your own network.
What is Server Certificate Validation?
Server certificate validation is a security feature of WPA2-Enterprise that makes devices check the identity of a server before they attempt to authenticate to a network. Devices are able to verify the server by checking the CA (Certificate Authority) that signs the RADIUS server and confirming that it is trusted.
Devices typically have a “root store”, a preinstalled list of trusted CAs. In order for server certificate validation to function, the device and the RADIUS need to both trust the same CA that issued the server validation certificate.
Why Does Android 11 Require Server Certificate Validation?
This change will address two issues:
- Removing the “Do not validate” option will prevent users from accidentally misconfiguring their network settings with the option, leaving them particularly vulnerable to over-the-air credential theft.
- Requiring correctly configured server certificate validation on Android forces organizations to either implement the more-secure certificate-based authentication protocol (EAP-TLS) or to at least configure their managed supplicants properly.
It’s unlikely that forcing organizations to update their Android security is simply the collateral damage of resolving the former issue. It’s a calculated move by Android and the Wi-Fi Alliance to send a message to the industry “Quit slacking on certificate-based authentication.”
And, frankly, it’s needed. There are many examples of publicly-accessible documentation from universities and the like that instruct end-users to select “Do not validate”. That might as well be an invitation for hackers to set up a fake access point with a spoofed SSID to harvest valid user credentials.
Even if organizations weren’t actively advertising their network vulnerabilities, the change would still be necessary. Most organizations with WPA2-Enterprise networks are still using relatively-ancient legacy EAP methods (such as PEAP and EAP-TTLS) and credentials. That’s likely due to the lingering misconception that EAP-TLS and certificate-based authentication is difficult to deploy.
That hasn’t been the case for years now. Managed PKI providers like SecureW2 have turnkey solutions that provide everything an organization needs for certificate-based authentication. We can integrate with and utilize your existing infrastructure for an efficient and speedy deployment of certificate authentication.
How to Implement Server Certificate Validation on Android
Unfortunately, there is no easy solution to the Android 11 Server Certificate Validation requirement. One way or another, public key cryptography is becoming a staple for secure network authentication and Google is making it clear that it’s required for secure Android browsing.
Those organizations operating their own WPA2-Enterprise networks will need to provide great documentation for their end users and employ more people at the IT helpdesk to help when users inevitably misconfigure their devices. Or, if that doesn’t sound appealing, use a device onboarding solution so end users can self-configure server certificate validation.
You can expect most public CA vendors to have a productized solution by the time this security patch hits. However, this is a golden opportunity to fully upgrade your network to EAP-TLS certificate-based authentication and take advantage of the greatly enhanced security and user experience it provides.
EAP-TLS Certificate Authentication for Android
The persistent myth regarding the hassle of digital certificates is outdated. It’s true that it used to be difficult and expensive to implement on-premise, but cloud PKI has adequately addressed those issues. PKIs are cheaper to build now than they were a decade ago and cloud-based options are cheaper still.
The security provided by certificates is exponentially stronger than credentials – that has never been a question. The principles of public-private cryptography that underpin x.509 digital certificates renders a network almost immune to both over-the-air attacks and phishing – a far cry from the commonly used EAP-TTLS/PAP protocol that literally sends credentials in cleartext.
And, in this instance at least, the increased security and reduced price tag don’t have to come at the cost of user experience. Certificate authentication is far more user-friendly than credential-based auth because it’s automatic. Certificates are saved to a device and presented automatically during the network handshake – no user involvement required.
That also means the elimination of password-reset policies and the constant headache of password-related support tickets. Our customers have seen up to a 50% reduction in IT support tickets after switching, a blessed relief for beleaguered help desk jockeys everywhere.
Automatic Enrollment of Android Devices for Server Certificate Validation
A final reason to go the extra mile and use a full PKI is that buying licenses from a public certificate authority won’t solve the final hurdle: enrolling Android devices for server certificate validation.
Managed devices are easy to configure and enroll, but most Android devices on a network are (understandably) BYOD. That means that, at some point in the process of configuration, the end user has to be involved. There are a myriad of different types of Androids and, despite their common operating system, they rarely all follow the same configuration blueprint.
That would be a recipe for disaster if you weren’t already reading a blog from the #1 rated device onboarding solution. We were provisioning certificates to Androids long before it was mandatory. Our BYOD onboarding solution allows you to push a customizable configuration client with a foolproof self-enrollment wizard that guides the end user through the confusion of configuring Android.
While it certainly feels like an inconvenience now, mandatory server certificate validation will prevent an enormous number of attacks on Android devices. Make the transition even easier with one of our affordable pricing options.