Key Points
- An AAA server is needed for network access management, authentication, authorization, and accounting with multi-factor authentication and digital certificates.
- Cloud-based AAA servers simplify network management with scalable and affordable solutions that enforce policy, conduct security audits, and use multi-factor authentication to improve security.
- Cloud RADIUS integrates with Identity Providers to effectively validate user credentials using RADIUS Lookup and restrict access to authorized users.
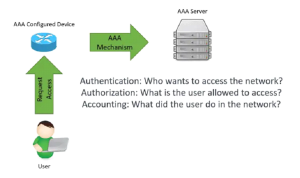
An AAA server processes user requests for access to computer resources and provides an organization’s authentication, authorization, and accounting (AAA) services.
The AAA server typically interacts with network access, gateway servers, and user-information-containing databases and directories. One type of AAA server framework is Remote Authentication Dial-In User Service or RADIUS for short.
Consider the AAA server a digital security monitor for computer networks. It performs three essential functions: verifying your identity, granting you access to specific features, and keeping account of your activities.
In this article, we will examine why the AAA server is crucial for the security of computer networks. We will learn about its three functions and how they contribute to the seamless operation of everything. In addition, we will discover some methods to ensure that the AAA server performs its duties as efficiently as feasible.
The AAA Server and its Functions
Authentication
The AAA server receives an authentication request from the user. It puts the user’s credentials to the test by asking for things like their login and password, which are encrypted using a hashing method. The user’s authentication credentials are checked against those saved for that user in a separate database, such as an Identity Provider (IDP).
Alternatively, RADIUS servers can authenticate digital certificates instead of usernames and passwords. This is more secure for several reasons we’ll discuss later in this article.
Authorization
After the user’s credentials have been verified, the authorization procedure will decide what actions and resources inside the network’s infrastructure a particular user can take and access. Users are separated into distinct groups according to the functions they are authorized to carry out, such as Administrators and Guests. The AAA server is responsible for determining which groups a user or device belongs to and providing the correct access accordingly.
Accounting
The final step in the AAA architecture involves keeping track of everything a user is up to while connected to a network. The AAA servers monitor the resources used during the network access process.
Accounting keeps a record of session statistics as well as auditing consumption information. This information is often used for authorization control, billing invoices, resource utilization, trend analysis, and planning the data capacity of the company’s operations.
The administration of RADIUS event records is a notable aspect of this domain. These records are an invaluable source of information, documenting every event and interaction within the network.
These logs document the network’s pulse, from user logins and logouts to resource consumption and access attempts.You can refer to our comprehensive guide on “How to view RADIUS event logs” to gain insights into network operations.
AAA Protocols and Authentication Methods
AAA Protocols
AAA Protocols are a set of rules and steps that make sure computer networks are safe to use. AAA stands for Authentication, Authorization, and Accounting. These are the three most essential steps in confirming and tracking users. These methods check IDs and rights before letting someone or something into the network.
A RADIUS server is an example of an AAA server, and the terms are sometimes used synonymously. Like a virtual doorman, it “guards” access to your wired and wireless networks by checking each user or device connecting to the network. There are different authentication methods it can use to accomplish this goal.
Authentication Methods

Authentication methods are how people or devices wanting to connect to a network can prove who they are. It’s the equivalent of passing a security check to verify your identity. EAP-TLS, which stands for Extensible Authentication Protocol-Transport Layer Security, is an innovative method in AAA servers.
EAP-TLS corresponds to a digital passport. It ensures that your communication is highly secure. It is as if you were speaking a language only you and the network understood. This method prevents eavesdropping and protects your data from curious eyes. EAP-TLS is the way to go if you want to keep your conversations covert and secure.
However, EAP-TLS is not the only contender in this domain.Additional authentication options, such as PEAP-MSCHAPv2 and EAP-TTLS/PAP, provide a range of choices for password-based authentication. These alternatives offer distinct advantages and are suitable for various scenarios, enhancing security measures and accommodating individual preferences and specific needs.
Best Practices for AAA Server Implementation
-
Secure Onboarding Solutions
A well-protected network starts with reliable onboarding options. The right onboarding technology ensures that every user and device is authorized by verifying them and properly configuring them before allowing them to connect.
Additionally, proper onboarding improves the user experience by making it easier for them to join the network. Just how this works varies depending on whether you are onboarding managed or unmanaged devices/BYODs.
Significant differences arise when examining the onboarding process for managed and unmanaged devices. The latter situation, which involves the implementation of BYODs, presents a distinct and specific issue. Unmanaged devices have an inherent uncertainty in their configuration since ownership does not ensure appropriate setup. onboarding technology likeJoinNow MultiOSacts as a BYOD guardian. This technology facilitates the accurate setup of these devices, empowering end users to configure their own devices in just a matter of seconds..
In the realm of managed devices, implementing an automated onboarding solution, such as SecureW2’s managed device gateways, can alter the landscape significantly. Instead of depending on manual setups performed by end-users or administrators, these gateways integrate seamlessly with the organization’s Mobile Device Management (MDM) system. The Simple Certificate Enrollment Protocol (SCEP) enables the seamless distribution of crucial profiles to devices, optimizing the onboarding procedure and enhancing network security with accuracy.
2. Cloud-based AAA Server Deployment
Choosing to put AAA servers in the cloud has a lot of benefits. One of the most important perks is that it is cost-effective. Unlike standard hardware setups, cloud computers don’t need a significant investment upfront. Instead, organizations can only pay for what they use or need. With cloud implementation, it’s also easy to make things bigger or smaller. As the needs of the network change, it is easier to scale up or down. This ensures the network can handle more data without affecting how well it works.
Additionally, cloud-based AAA servers are highly accessible. Your network can be managed and monitored virtually anywhere. It’s as if you had the network’s command center in your pocket.
Because building yourown cloud-based RADIUS server can be difficult, there are RADIUS service providers to choose from that can help you ensure a speedy deployment. For example,Cloud RADIUSis a managed RADIUS service that’s cloud-based and be deployed rapidly.
3. Use of Digital Certificates
Digital certificates ensure that only authorized users can access a network and provide increased identity context for every connection. Organizations can use digital certificates to stop people from getting into the network without permission. Also, by securing data transfers, these certificates make contact safe. This encryption adds an extra layer of safety against online dangers and snooping.
Digital certificates do more than just verify names; they are powerful information repositories. These documents offer a rich web of information about a person’s identity that can be carefully checked. Consider a few examples: user roles and permissions, user groups with specific permissions, device serial numbers for hardware identification, device build models that show how the technology ecosystem works, user emails for communication and contact, and even details about the operating system to understand the technology landscape of the devices. Certificates are made up of information that verifies several things and helps the network figure out who is trying to get in. This makes sure that only the right people and devices are allowed in.

Digital certificates also aid in encrypting communications between devices, adding a layer of security against surveillance. If you want your network to be a secure fortress, digital certificates are akin to protecting the entrances.
4. Policy Enforcement
In network management, making strong access control policies is vital to security. These rules act as a set of boundaries determining a safe network for who can get in, what they can get into, and under what conditions they can get in. Organizations can create a complex fabric of different and focused policies by combining user jobs, device characteristics, and context clues. This is a key step in improving network security and control.
Policy enforcement is at the heart of this approach, which is how these rules will be followed. This method gives organizations two benefits: First, it gives them complete oversight over network access, which protects valuable assets from being used without permission. Second, it gives networks the flexibility to quickly adapt to changing user needs, which is a key part of improving security and the user experience.
Different AAA servers have built-in ways to implement policies, but Cloud RADIUS, for example, stands out because of its unique policy engine. This engine shows how these features can improve network administration by making it easier to implement custom access rules and bringing control and freedom together in the network structure. The use of policy enforcement concepts in network management not only improves security but also promotes a network environment that is flexible and centered on the user.
5. Regular Security Audits and Updates
Keeping a network safe over time takes constant monitoring. Security audits check the network’s weaknesses and strengths regularly. By finding possible security holes, organizations can close them before they are used against them. At the same time, keeping software and systems up to date protects against known flaws. With regular improvements, patches, and fixes are added that make the network more resistant to new threats. By incorporating security audits and updates into the routine network maintenance process, organizations establish a proactive strategy for protecting their digital infrastructure.
6. Multi-Factor Authentication
Multi-factor authentication (MFA), which goes beyond an account and password, gives an extra layer of security. Before getting entry, users must provide multiple ways to prove their identity. MFA makes it much harder for someone else to get in by mixing something the user knows (like a password) with something they have (like a smartphone) or something they are (like a fingerprint).
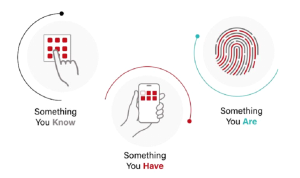
With this approach, hackers must get past multiple identification hurdles before getting into the network. Implementing Multi-Factor Authentication (MFA) as part of AAA server practices is a solid way to protect against many online risks.
Strengthening Network Security with AAA Server Best Practices
An AAA server requires maintenance and other security practices to keep it secure. Implementing onboarding technology to prevent misconfiguration, developing thorough access policies, using certificate-based authentication, and deploying your RADIUS server in the cloud are just a few ways to ensure a healthy zero-trust network.
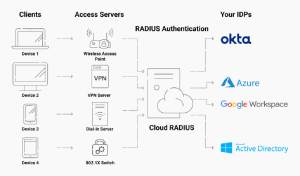
SecureW2 is at the top of network security innovation, offering solutions that improve your network’s safety and efficiency. SecureW2 brings a plethora of knowledge and experience as pioneers in RADIUS(AAA) authentication. Our seamless integration with different Identity Providers (IDPs) and Mobile Device Managers (MDMs) ensures your access to your network is only granted to those who need it and also ensures you can see detailed information on every connection.. We have cutting-edge technology with a committed team who knows much about it. We’re here to help you switch to Cloud RADIUS so that your network’s journey to better security is smooth and easy.
Contact usto learn more about Cloud RADIUS.
