Key Points
- Intune simplifies 802.1X configuration by providing secure Wi-Fi authentication with various EAP protocols.
- EAP-TLS offers superior security through digital certificates, minimizing credential theft and MITM attacks.
- Misconfigurations in 802.1X setups can pose risks; choosing the right protocol like EAP-TLS ensures secure authentication.
- SecureW2’s managed PKI leverages advanced integrations with Intune to issue certificates and configure Intune-managed devices for secure 802.1X network access.
The 802.1X standard provides secure authentication for users and devices looking to connect to wired and wireless networks. It uses an authentication server known as the RADIUS server that validates the users against their credentials and network policies to provide access to various applications every day. It also encompasses security aspects like server security validation, utilizing any EAP protocol, and optimizing organizational processes through more efficient authentication.
This guide will take you through a comprehensive setup to configure 802.1X with Intune, the different EAP protocols, and their authentication process so you can choose and configure without fear of any misconfiguration or server validation issues you may face when you set it up.
What is the Extensible Authentication Protocol?
EAP is an authentication mechanism that builds on the Point-to-Point Protocol (PPP) authentication method to secure a network. It connects a device to both wired and wireless networks through secure channels for sending information over the air. The EAP protocol provides extensibility and the operational structure for various authentication servers to enhance security requirements per operational need.
EAP provides various authentication methods and can be used per organizational requirements. Some standard EAP protocols are:
- PEAP-MSCHAPv2
- EAP-TTLS/PAP
- EAP-TLS
PEAP-MSCHAPv2
The Protected Extensible Authentication Protocol (PEAP) establishes a secure encrypted channel. It creates a secure tunnel, which the client authenticates to the authentication server using a public key certificate. This creates an encrypted pathway between the authentication server and the client via the PEAP authentication. Any user credential is safeguarded as it is encrypted in the tunnel during the authentication process.
Although relatively simple to configure due to its reliance on credentials for authentication, PEAP-MSCHAPv2 is a dated protocol that has seen many vulnerabilities over the years. This is why a growing number of organizations are moving past PEAP-MSCHAPv2 and looking toward more secure alternatives for authentication.
EAP-TTLS/PAP
EAP-TTLS is also known as Extensible Authentication Protocol-Tunneled Transport Layer Security. It is built on the EAP framework and allows several authentication techniques over the same protocol. In EAP-TTLS/PAP authentication, the authentication server uses two main functions, i.e., the TLS handshake and the TLS tunnel phase. However, EAP/TTLS-PAP is vulnerable to man-in-the-middle (MITM) attacks as the credentials are sent over clear text and are not encrypted. This means it can be deciphered easily.
EAP-TLS
EAP-TLS means Extensible Authentication Protocol-Transport Layer Security and uses digital certificates to secure your network using public-private cryptography so that only authorized users can access resources, data, and applications. EAP-TLS uses X.509 certificates that are phishing-resistant, thus making them very secure. Organizations can use these digital authentication certificates to provide single sign-on (SSO) across different network devices or VPNs.
The EAP-TLS is a mutual authentication method where both the client and the server need certificates to authenticate each other to an authentication server. Mutual authentication is the most secure way to protect an 802.1X network.
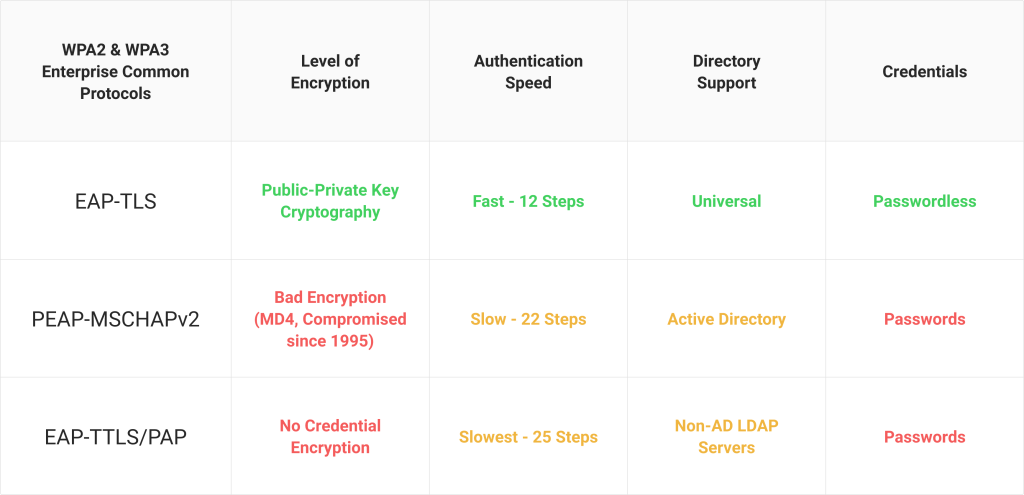
EAP Protocols With Intune 802.1X Configuration
PEAP-MSCHAPv2, EAP/TTLS-PAP, and EAP/TLS are the recommended 802.1X authentication protocols for organizations setting up their network. While PEAP-MSCHAPv2 and EAP/TTLS are credential-based and, therefore, easier to configure, they come with security considerations, such as the potential for Evil Twin attacks. However, you can confidently navigate these protocols with the proper knowledge and tools.
If you have chosen PEAPMSCHAPv2 for your 802.1X network, you need the following to set it up:
- RADIUS authentication server to communicate with Active Directory.
- An MDM like Intune to configure 802.1X on managed devices.
- LDAP server to sync Azure with Active Directory (if you’re using on-premise Active Directory).
It’s important to note that the configuration process, particularly without onboarding software, can be complex and carries the risk of misconfiguration. However, with the following instructions and a clear understanding of the process, you can mitigate these risks and successfully set up your 802.1X network.
EAP-TLS is widely recommended for organizations as a secure authentication protocol that supports digital certificates, but it requires a PKI to support certificate management effectively. You would need the following:
- A RADIUS server to talk to Azure.
- SCEP or an onboarding software for enrollment.
- A Public Key Infrastructure (PKI).
Deploying 802.1X using EAP-TLS for Intune Managed Devices
If you want to manage your mobile devices for successful passwordless authentication, then the EAP-TLS protocol is the way to go. EAP-TLS uses digital certificates, which can be distributed via Intune using a Wi-Fi profile for server certificate enrollment through your organization’s AD domain.
The pre-requisites for EAP-TLS with Intune set-up are as follows:
- PKI software that ensures device authentication through certificates on Intune.
- Certificate Chain of Trust. A root certificate for server validation to authenticate the network for the RADIUS authentication server.
- An intermediate CA from the ROOT CA to authorize certificates for users and devices.
- Server names to issue certificates by a trusted CA.
- A trusted certificate profile for the RADIUS authentication server will be configured with the RADIUS server certificate CA. This ensures that the RADIUS server certificate is validated by the RADIUS authentication server. You can enable RADIUS server certificate validation by adding the Root/ Intermediate CA so that Intune-managed devices receive a trusted certificate.
- SCEP client certificate profile for automated certificate distribution.
Click here to learn more about configuring Wi-Fi profiles for Intune Managed devices.
How to Configure Wi-Fi Profile in Intune for Authentication
Log into Intune and create an organizational profile that applies to your device upon connecting to the network.
Intune EAP-TLS configuration
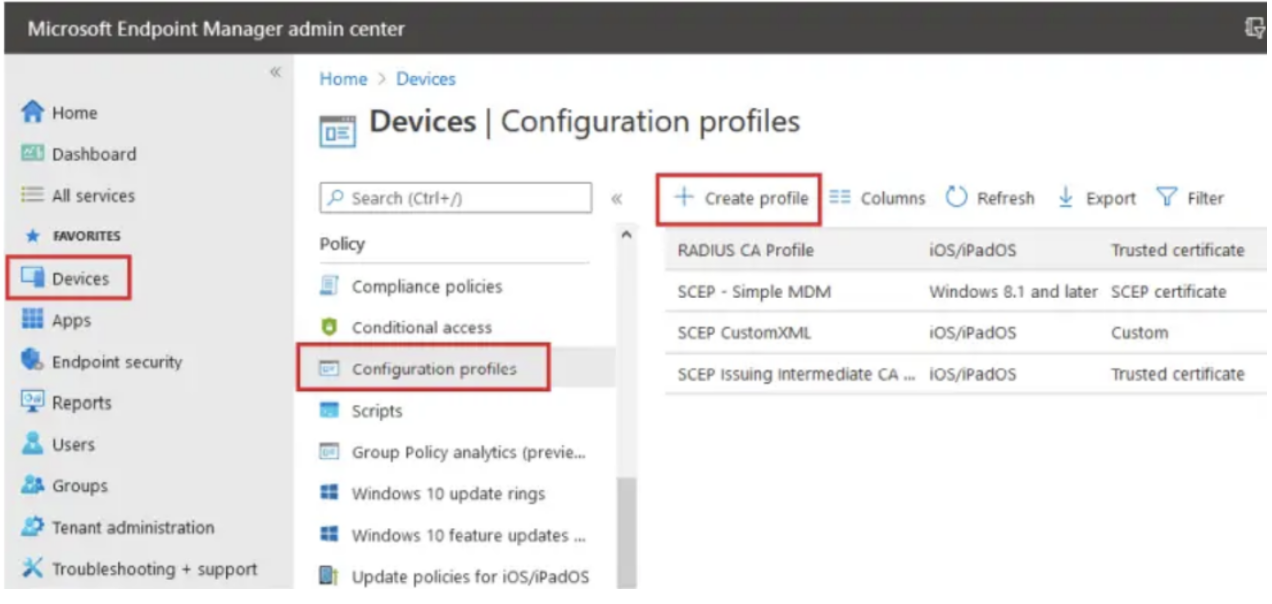
- Sign in to the Intune (Microsoft Endpoint Manager) portal.
- Select Devices > Configuration profiles > Create profile.
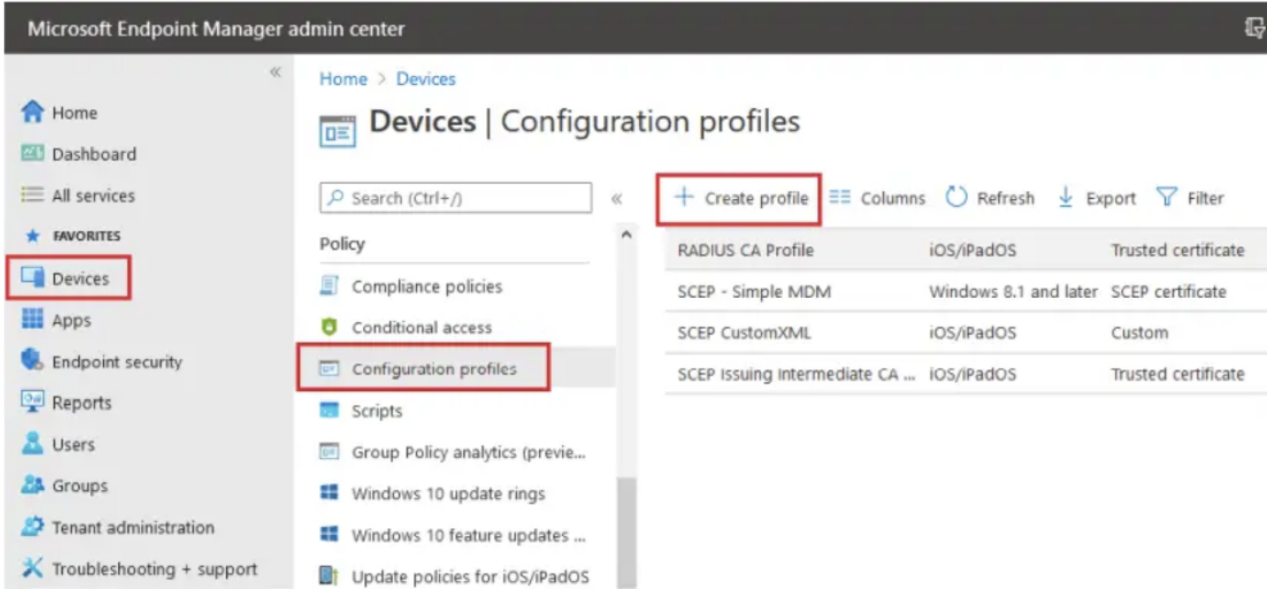
3. Select the device platform, Windows 10 or later, from the Platform dropdown list.
- Under the Profile Type, you’ll select Templates and then Wi-Fi.
- Select Create.
4. In Basics, enter the name and description of your Wi-Fi profile.
- Click Next.
5. Choose your organization’s settings and security protocol in the Configuration Settings tab. Click on Finish.
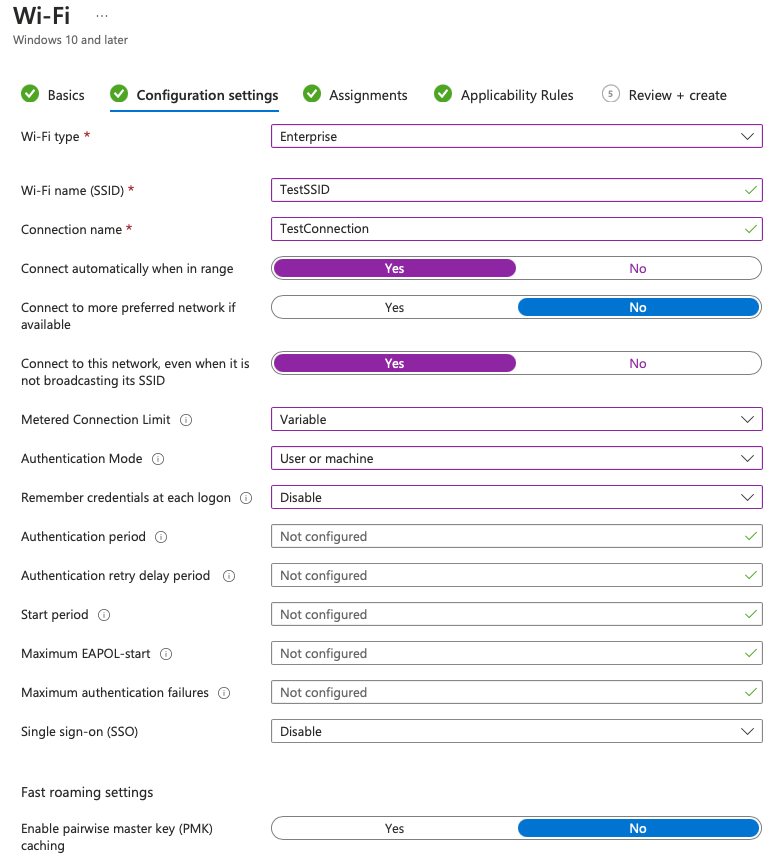
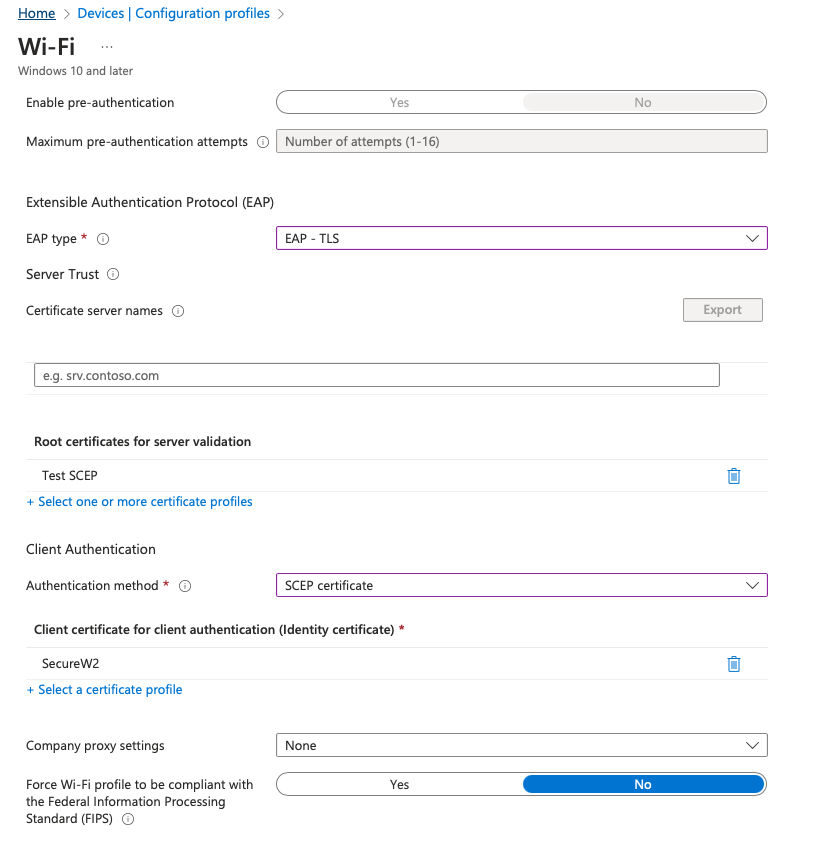
If you select the EAP-TLS authentication, you should ensure that the following settings have been created for smooth configuration.
- Root CA for server validation and establishing device trust.
- EAP-TLS for EAP type to ensure certificate protocol is deployed accurately.
- SCEP profile for automated certificate distribution.
6. Go to the Assignment section and choose the user/groups for the Wi-Fi profile. Click Next.
7. Next, select the profile the user would be assigned upon signing into the Wi-Fi network.
8. Click next for Review+Create. You will then be able to view the Wi-Fi profile you created for your organization, which will push out all of your Intune policies as soon as they connect to your Wi-Fi.
Intune with Peap-MSCHAPv2
For Peap-MSCHAPv2, follow the steps here to authenticate your organization through credentials.
- Login to your Intune portal.
- Select Devices > Configuration profiles > Create profile.
- From the Platform dropdown list, select the device platform, Windows 10 or later.
- Under the Profile Type, you’ll select Templates and then Wi-Fi.
- Select Create.
- In Basics, enter the name and description of your Wi-Fi profile.
- Click Next.
- In the Configuration Settings tab, you will choose what settings your organization should configure and what security protocol to use.
- Click Next.
- Move to the Assignments Section.
- Select the user/groups you want to assign for this Wi-Fi profile to be given to their devices.
- Click Next.
- You will be redirected to the Applicability Rules. Choose what OS this profile will be assigned to so that it automatically updates when the user signs onto the Wi-Fi.
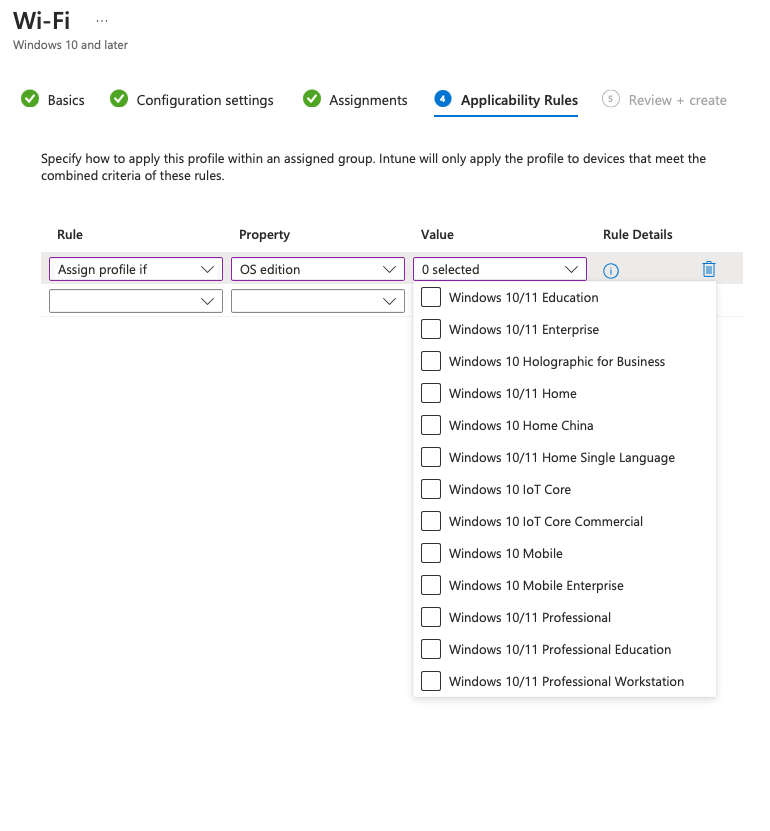
- Click next for Review+Create.
- You will then be able to view the Wi-Fi profile you created for your organization, which will push out all of your Intune policies as soon as they connect to your Wi-Fi.
Benefits of Using EAP-TLS For An 802.1X Network
EAP-TLS provides a host of benefits when used along with the 802.1X network. EAP-TLS lets you leverage passwordless authentication through digital certificates for superior network security, making it a foremost choice for organizations. Here are some benefits of EAP-TLS on an 802.1X network:
Server Certificate Validation
EAP-TLS provides superior network security compared to the other security protocols, as it significantly reduces the risk of attacks like MITM and hacking. The EAP-TLS provides server security validation through mutual authentication, i.e., the user and the server must validate each other to avoid spoofs and authenticate to a fake access point.
Better Network Access Control
EAP-TLS uses digital certificates to improve network access control, as digital certificates provide context information like user type, device information, roles, location information, etc. This provides an identity context that helps the admin see who and what connects to the server.
Cloud RADIUS Identity Lookup & Device Compliance in Intune
Cloud RADIUS facilitates compliance attributes for wired and wireless networks and VPNs in Intune through its identity lookup technology. A client device’s compliance status can be verified by interacting with Azure AD and Intune during authentication. The authentication process starts with the issuance of digital certificates to managed devices.
Distributing certificates is a breeze with SecureW2’s Managed Gateway API, as it uses SCEP to enroll certificates for Intune-managed devices automatically. These certificate templates can be populated with the Azure ID to determine managed devices’ compliance and network access status. The device provides its certificate to the authentication server and is verified on Azure Ad with its Mac address. Azure AD verifies the MAC address and determines if it should gain access to the network.
How to Configure Network Policies For Intune Device Compliance
Prerequisites
If you want to use SecureW2’s managed Gateway API for Intune Device compliance, you should obtain the following licenses and subscriptions:
- Azure AD License
- Intune License
- Microsoft 365
- Cloud RADIUS
- JoinNow Connector PKI
Basic Steps To Configure Before Setting Up Intune Device Compliance
- Established groups in Azure AD to apply compliance policies.
- Creating a notification template in Intune to notify non-compliant devices.
- Adding your Intune as an Identity Provider in SecureW2.
- Adding Azure as an Identity Lookup Provider in SecureW2.
- Creating a SCEP certificate profile in Intune with the Azure Device ID in the subject alternative name (SAN) field.
Configuring Policies Based on Intune Device Compliance in SecureW2
Once the basic compliance steps have been configured on Intune, you should integrate them with SecureW2s Managed Gateway API.
- Add the isCompliant attribute to the Azure Lookup Provider in the management portal.
- Navigate to Identity Providers and click Edit on your Azure IDLP.
- Go to the Attribute Mapping section and Add an attribute.
- In Local Attribute, enter isCompliant
- In Remote Attribute:
- Select User Defined as the value in the drop-down
- Enter isCompliant as the value
- Click Update
- Click Update to save your Azure IDLP.
Next, we will create a role that only applies to compliant devices in Azure/Intune.
- Select Policy Management and then Roles Policies from the dropdown.
- Click Add Role, then name the role appropriately. We recommend naming it Device Compliance Intune/Azure.
- Click Save.
- Select the Conditions button at the top and choose your IDLP from the dropdown menu.
- Choose the Edit Attribute dropdown. Select isCompliant, and then Equals, and then True for the value.
- Click the Update button.
- Repeat steps 1-6, but change the attribute isCompliant to Equals False. This will allow you to create a separate failover policy for when a device fails the compliance check.
With these steps followed, Cloud RADIUS will now confirm through Identity Lookup at the time of authentication that a device is compliant. Your next step is to configure network policies that can utilize the compliant attribute we’ve just told it to check. To accomplish that, follow these steps:
- Select the Policy Management option, then choose Network Policy.
- Click the Add Network Policy button and name your policy. As we did previously, we recommend naming it something that references compliance. In this case, we’ve named the policy Compliance Check.
- Click the Save button. Two more buttons will appear at the top: Conditions and Settings.
- Select the Conditions option in the middle, and choose Add Rule.
- Click on the + button next to Identity to open the Identity menu.
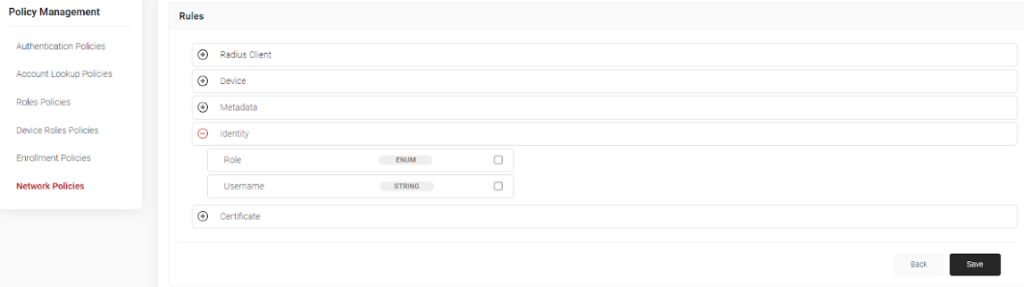
- Check the box next to Role, then click the Save button.
- You will be brought to a screen where you can choose the role the policy applies to. Choose the applicable role related to compliance we made in the previous steps, then click on the Update button.
- You will be brought back to a screen with your network policies. Choose the Edit icon on the policy we’ve just created.
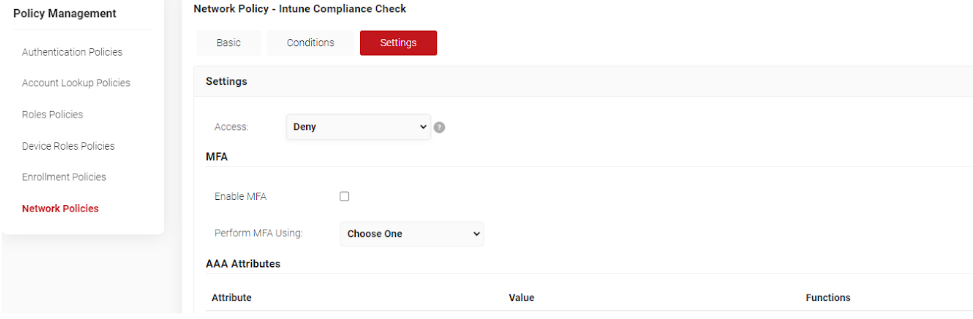
- Click the Settings button at the top. Choose Deny from the Access dropdown.
- Click on the Update button to save the network policy.
These steps ensure the creation of a role and network policy in SecureW2 to check a device compliance status for VLAN assignment. Suppose a user or device complies with a particular role. In that case, he can authenticate himself to the authentication server to gain access to a network, or else his access to a network is denied.
Leverage SecureW2’s Passwordless Platform for Robust 802.1X Authentication
Digital certificates are increasing in popularity and being recommended and adopted by organizations like Microsoft and Google to secure their 802.1X networks. This article has covered the setup of SecuredW2s Managed Gateway API with Intune to distribute digital certificates and secure authentication to a Cloud RADIUS server so that users and devices can authenticate themselves to an authentication server. The Managed Gateway API uses SCEP for automated certificate management.
It also provides auto-revocation of certificates on Intune, making certificate revocation easier. SecureW2 is also a proud partner of Intune and provides a feature-rich certificate management solution compared to any other solution.
Click here to learn more about our passwordless solution for Intune Managed Devices now.