We are living in an age where basically every person has an online footprint, whether it be for entertainment or to conduct business. Since millions of people are taking their businesses online, that means a lot of private data is uploaded and accessible on a LAN or WLAN. In response, there needs to be security measures in place to ensure only approved users can access the network and private data stays protected.
Some businesses have enabled WPA2-PSK network authentication to secure their data. However, WPA2-PSK relies on authenticating passwords, which are no longer secure because there are too many vulnerabilities associated with credential authentication. Several cyber attacks, such as the man-in-the-middle attack, can easily bypass password-based security, steal credentials, and be granted access to private data.
Historically, many Microsoft networks authenticated their users with credentials through the PEAP-MSCHAPv2 protocol, but that protocol has a major vulnerability that gives attackers that ability to slip into the network and farm network credentials.
Why Businesses Need 802.1x Authentication
The best practice for securing online communications and private data is deploying WPA2-Enterprise with 802.1x authentication. WPA2-Enterprise is the gold standard for wireless security because it provides over-the-air encryption and is the highest level of network authentication security being used today.
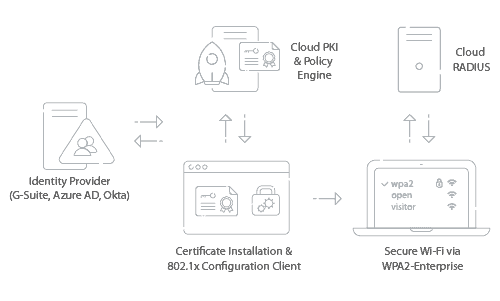
802.1x and WPA2-Enterprise require a RADIUS server, which serves as the “bouncer” for network access. Any device requesting access to a network must first connect with the RADIUS so it can examine the device credentials. If the credentials are in the system, the user is granted access based on network policies.
802.1x is able to encrypt the authentication session between the user and the network AP. This prevents anyone else from accessing the session, viewing the traffic, and stealing credentials.

How to Use Office 365 for 802.1x? Sync with Azure AD (Microsoft Entra ID)
We’ve gotten the question a lot lately, “how do I use my Office 365 credentials for 802.1x network authentication?” Simply put, Office 365 admins can use 802.1x RADIUS security by syncing Office 365 with Azure AD (Microsoft Entra ID) so the RADIUS server has a directory to authenticate users.Not only can this be easily accomplished, but it’s free because an Office 365 subscription includes an Azure AD subscription.
This seems like an easy setup, but configuring Azure for WPA2-Enterprise and 802.1x is much more complicated compared to AD. Back in the day, Microsoft designed an entire environment for 802.1x authentication that could easily be setup on-premise with AD. Today, setting up 802.1x with Azure AD is much more difficult because Azure AD is a cloud-based Identity Provider, and was not designed to work with Microsoft’s on-premise 802.1x solutions.
Configuring Azure AD for 802.1x & WPA2-Enterprise
Azure does not have the same capabilities to support WPA2-Enterprise compared to Active Directory, but AD’s on-prem connection holds environments back from effectively migrating to the cloud.
Integrate Azure with SecureW2’s Managed PKI to enable 802.1x onboarding and provision a certificate onto every device. SecureW2 offers automated onboarding software, relieving admins from the labor-intensive task for manually configuring every device. End users only need to press a few buttons and they are authenticated for wireless access and will automatically connect every time they login going forward.
SecureW2 also offers Cloud RADIUS, which is an integral part of WPA2-Enterprise and 802.1x. Cloud RADIUS can be integrated with your user directory so it can effectively authenticate network users. RADIUS ensures only approved users will be granted network access and any suspicious devices will be rejected.
Cloud RADIUS also comes with industry-exclusive technology that doubles these security measures with redundancy. Cloud RADIUS dynamically communicates with any IDP to corroborate that the user that is trying to connect to the network is approved and did not circumvent the CRL due to human error from a slip of the administrator.
- Use SecureW2’s Getting Started Wizard
- SecureW2’s PKI services are completely turnkey because all the necessary tools for PKI implementation are set up through our Getting Started wizard.
- Our Getting Started Wizard also allows admins to enable 802.1x authentication for secure user authentication. Only approved users equipped with CA-signed certificates will be granted network access.
- Configure a SAML Application in Azure
- SecureW2’s service allows admins to integrate their IDP by creating a SAML Application in SecureW2’s Management Portal.
- The SAML application serves as the medium for end user devices to enter their credentials, get verified by the IDP, and be issued a certificate.
- Integrate AD with Azure SAML Application
- The SAML Application needs a directory to efficiently identify network users. SecureW2 gives admins the ability to integrate Azure AD with the SAML application so it has a list of active users to compare against devices requesting network access.
- Configure Group Policies and Attribute Mapping
- SecureW2’s GUI allows Azure admins to easily create network groups and map user attributes to certificates based on the groups they were assigned to.
- Once the Azure IDP identifies an end user, it will send the attributes to SAML, which then relays the attributes over to SecureW2.
- Integrate SecureW2 Cloud RADIUS with Access Points / Controllers
- SecureW2 can integrate with any major access point and controller.
- No matter the environment or vendor, admins can leverage their user database with SecureW2’s Managed PKI and Cloud RADIUS to deliver secure user authentication with 802.1x EAP-TLS.
- Use SecureW2 Certificate Delivery Mechanisms to Enroll Devices
- It can be difficult for admins to configure every user-owned device for network access, luckily SecureW2 provides the JoinNow Suite for BYOD onboarding. BYODs can download the JoinNow app (available for every major OS) and after a few clicks, the device is automatically configured for 802.1x and provisioned a certificate.
Dynamic Cloud RADIUS with Azure
SecureW2 uses industry-first technology to allow Cloud RADIUS to talk to any IDP, or in this case, Azure AD. This allows admins the power of dynamically changing policies for their users based on their needs without the need of revoking or reissuing certificates through their IDP. For more information about our Dynamic Cloud RADIUS, contact us here.
Deploy 802.1x for Office 365 with SecureW2
By integrating Office 365 and Azure AD with SecureW2, admins can seamlessly enable 802.1x authentication so their networks stay protected and only approved users will be granted access.
SecureW2 provides an easy-to-use solution that gives admins full control over network access, certificate management & issuance, attribute mapping, revocation, and much more. Our software services can integrate with any major vendor and access point to provide you with everything you need for 802.1x authentication and there’s no need to forklift your current infrastructure. Clean, simple, and affordable.



