ECC, or Eliptical Curve Cryptography, isn’t a new technology – it’s relatively old, actually, Despite being around since 1985, it has just recently begun to gain popularity as an alternative, possibly superior, form of public key cryptography.
So what’s the big deal about ECC?
The TL;DR of ECC
We won’t get deep into the nitty-gritty here because some real math whizzes have already covered the finer points of elliptical curve cryptography in other guides. Instead, we’ll just give you a high level overview of the algorithm so that you can understand why the method is poised to deliver top-notch cryptography to an expanded variety of devices.
As we touched on before, ECC was invented some 30-odd years ago. It’s a type of public key cryptography, so at it’s core it operates using a public-private key pair. Anyone can see your public key and use it to encrypt a message. However, it can’t be decrypted without the private key that only you know.
Public key cryptography forms the foundation of most secure communications today because it doesn’t require the two parties to communicate before the message is encrypted, as is the case with pre-shared keys – which has a potential to be compromised before the communication is even started.
Back to ECC. ECC is what’s called a trap-door function, meaning it is easy to compute in one direction and hard to compute in the other. In practice, that means that it’s very easy (therefore fast) to decrypt a message if you are working from the direction where you know part of the equation (the private key), and extremely difficult if you’re working from the other direction (don’t know the private key).
The thing that makes ECC is unique is how it generates the numbers used for the public private key pair. RSA, the incumbent public key cryptographic method, multiplies together two very large prime numbers and uses those, plus the product, to secure communication. ECC uses the projective property of elliptical curves to select points on the graph which appear to be random unless you know the seed point (the private key) that generated the curve.
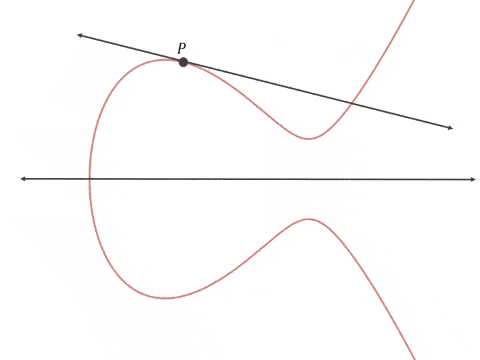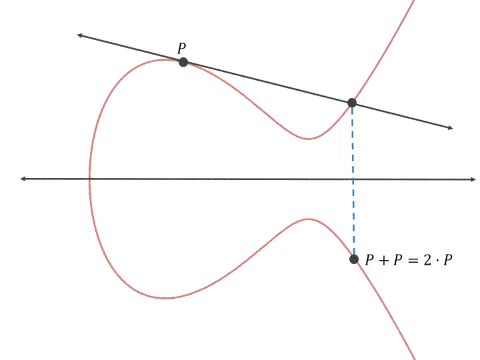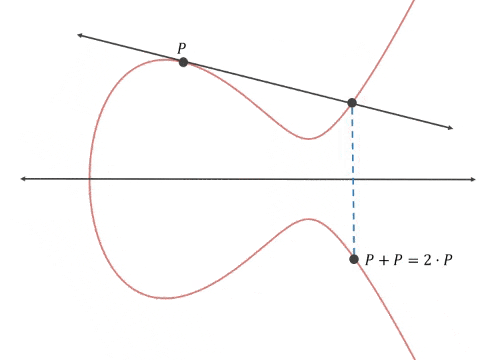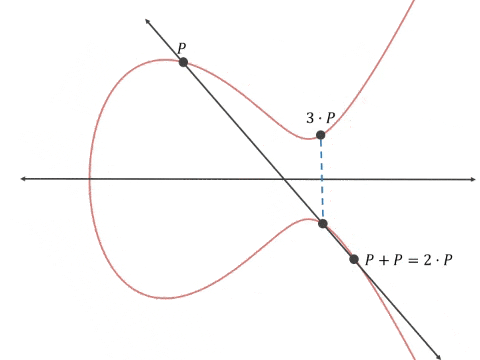
From GrayBlock on Medium.
ECC vs RSA
With that basic understanding, it might appear that ECC is just another way of algorithmically creating “random” numbers… and that’s sort of true.
It’s true that computers can’t generate true randomness, so any key that is determined algorithmically is technically crackable. The real challenge of cryptography is finding algorithms that are so incredibly difficult to crack that it’s just not worth trying. Computers, which can process information exponentially faster than people, have made that process much more complex.
RSA is, by all standards, a very excellent example of a trap door public key cryptographic function. Choose two enormous prime numbers, multiply them together, and hand out the product as your public key. The only way to find the private key (and decrypt the message) is the naive approach – which isn’t an insult, it means you have to brute-force the equation by guessing prime numbers.
The thing is, computers are fast and only getting faster. Quantum computing in particular has the potential to totally break these sorts of systems. Computers can guess a lot of numbers in a short time, so in order to make it unlikely to be decrypted, you have to use increasingly enormous numbers for your RSA hash, which ends up significantly slowing the process for the computers that aren’t trying to hack stuff.
Computers with good processors can handle it, but we have lots of devices that need security and don’t have a lot of space or power to devote to processors – smartphones, home assistants, medical devices, and more.
On top of that, there are some special algorithms like the quadratic sieve which take a little of the guesswork out of the process, further undermining RSA.
Elliptical curve cryptography doesn’t need huge numbers to maintain security. Using any positive whole numbers up to your (hidden) predefined, prime max (after which it rolls over back to 0, as it does in RSA) you can plot points on a graph using the curve equation.
In order to illustrate how much more secure this method is, Arjen Lenestra published a paper that introduced the concept of “Global Security”. Instead of trying to wrap your head around the bits and bytes, you can translate algorithm security by calculating how much energy it would take a computer to crack the code and how much water that same amount of energy could boil.
To crack a 228-bit RSA key would require the same amount of energy as needed to bring a teaspoonful of water to boiling point.
To crack a 228-bit ECC key, you’d need an amount of energy capable of boiling all of the water on the entire planet Earth. An equivalent RSA key would require 2380-bits.
Given the impossibility of acquiring that much energy, you can say that ECC is effectively uncrackable with current technology… and it uses only a fraction of the resources of RSA.
ECC as a Solution for IoT Security
The significantly reduced size of an effective ECC is a huge boon – much more impactful than a phone that is 0.1mm slimmer than last year’s version.
In order to effectively perform cryptographic functions, most devices need some sort of dedicated cryptographic processor like a hardware security module or a smartcard. These are pretty small already, small enough to be embedded as a microchip in a credit card in the case of a smartcard.
ECC having such a low data-requirement allows us to use smaller, faster, and cheaper cryptoprocessors, which vastly expands the range of products they can be integrated with. That’s why ECC has become the standard for issuing certificates to IoT devices.
And with more and more devices requiring network access for critical functions, the need to secure the ever-increasing vectors of attack is extreme.
Many of those devices can’t utilize the standard WPA protocols for wired and wireless security, much less WPA2-Enterprise with EAP-TLS and digital certificates setup that you would need for truly ironclad security. There’s a need for easily deployable, custom IoT network security.
There have already been examples of Wi-Fi networks being hacked through a connected smartbulb or other smart-device. There are lots of devices that have unique operating systems (or no true operating system at all) that still need to connect to networks – advanced medical devices, for example – that don’t support standard wireless security protocols.
The potential consequences of compromised IoT devices are just as serious as compromised computers. Imagine the chaos and harm a hacker could inflict if they infiltrated an MRI machine or a respirator machine. Even just exploiting a device to gain access to the network and medical records would be devastating.
Protect IoT with ECC Today
Most organizations have myriad IoT devices connecting to their network. Even if you aren’t using specialized equipment or smart-home accessories in your office, your employees and customers use IoT devices on your network – the ubiquitous smartwatch, for example.
You need an ECC-based encryption to keep your network and your devices safe. SecureW2 has pioneered a cutting edge IoT platform that empowers organizations to enroll IoT devices for certificates using ECC quickly and securely. Contact our specialists today to find out if we’re the right fit for your organization’s IoT security needs.