Security keys are useful tools for hardening your devices with an additional factor of authentication. Did you know that same protection can be extended to your network?
SecureW2, a Yubico Partner, has developed an industry-first software solution that allows you to reconfigure your Yubikey to authenticate with certificates instead of credentials.
While Yubikeys are already a powerful multi-factor authentication device, making the switch to certificates increases their security exponentially. Certificates have a number of advantages over credentials, including:
- Certificates are tied to the identity of a person or device, unlike credentials, meaning you know exactly who is using the network and for what. A person can’t ‘lend’ their coworker their certificate to login.
- Certificates are the best protection against over-the-air-attacks like the man-in-the-middle attack.Certificates are virtually impenetrable, unlike passwords. Even if a bad actor managed to intercept your data during login they would still lack the vital private key, rendering the attack useless.
- Certificates reduce burden on your IT department because they eliminate the need for password-reset policies, which inevitably cause massive confusion every 60 or 90 days. Certificate lifetimes are 20+ years.
In order to utilize certificates in your organization, you need a WPA2-Enterprise network that uses the EAP-TLS authentication protocol for 802.1x. If you aren’t already using EAP-TLS , SecureW2 can integrate into your existing infrastructure and fill in the gaps to create a fully-featured EAP-TLS-based network with no forklift upgrades.
Advantages of Security Key Wi-Fi Logon
Using a security key to access Wi-Fi has benefits both to the individual and the organization as a whole.
Security keys are simply convenient. It totally removes the need to remember credentials (and to rememorize passwords every couple months). You can keep one at your desk or on your key ring and access the Internet with the same ease you normally do.
If you happen to lose your key or forget it at home, you’re not necessarily locked out of the network. You can use backup authentication methods such as credentials or one-time keys sent to a phone.
Not to mention the incredible security provided by physical security tokens. Methods of authentication fall into one of a few categories:
- Something you know
- Something you are
- Something you have
Most security measures depend on the first of those methods (a password is ‘something you know’). Biometric security, while not ubiquitous, is a fairly common ‘something you are’ route.
Rarely does cybersecurity venture into ‘something you have’ territory. That’s exactly what security keys are – and it makes the system they protect practically immune to most standard attacks. The asymmetric cryptographic foundation is virtually uncrackable and hackers aren’t known for physically stealing objects off of your person.
There are few cybersecurity measures as cost-effective and easy to implement as security keys.
How to Login to Wi-Fi with a Yubikey
The only way to use a Yubikey to access WiFi is with SecureW2’s unique security key-certificate solution. Here’s our guide on configuring Yubikeys for certificates.
Once your Yubikeys have been enrolled for and issued certificates, you can use them to access WiFi. Here’s an overview of the process:
Install the SecureW2 Yubikey Configuration Client
With your Yubikey inserted into the computer, run the Yubikey Configuration. The link can be found in your SecureW2 Management Portal. Below is a GIF summary of the process – it only takes a couple minutes!
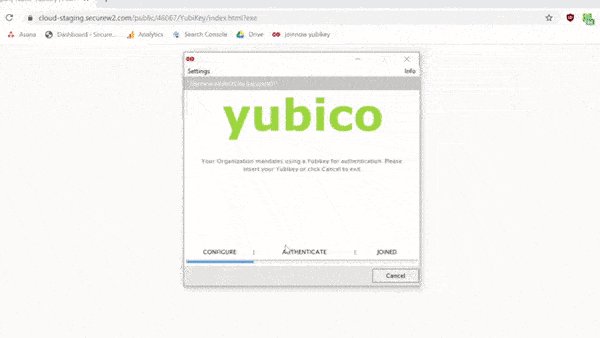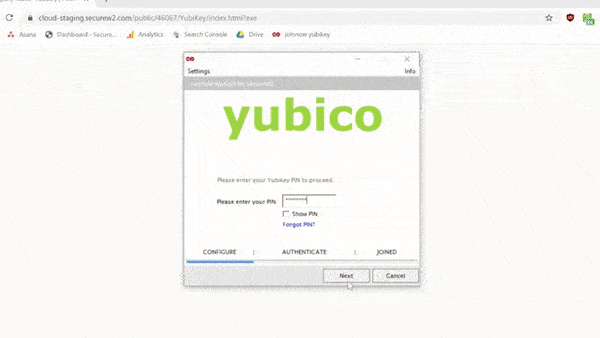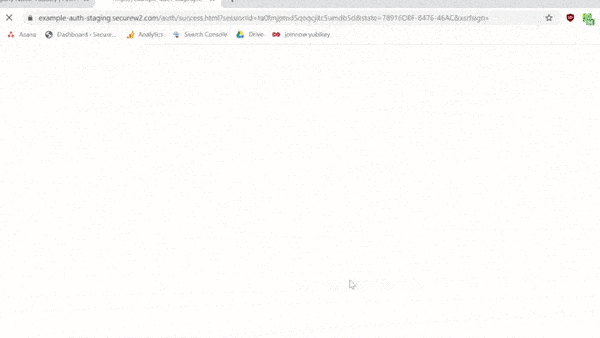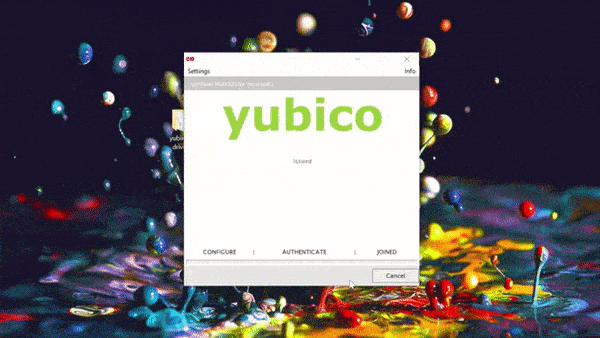
Follow the instructions to complete setup.
Accessing WiFi with a Yubikey
After setup is complete, open your Network and Internet Settings menu and locate the SSID that you previously configured to authenticate with certificates. Select it and click Connect.
A dialogue box similar to the following should pop up:
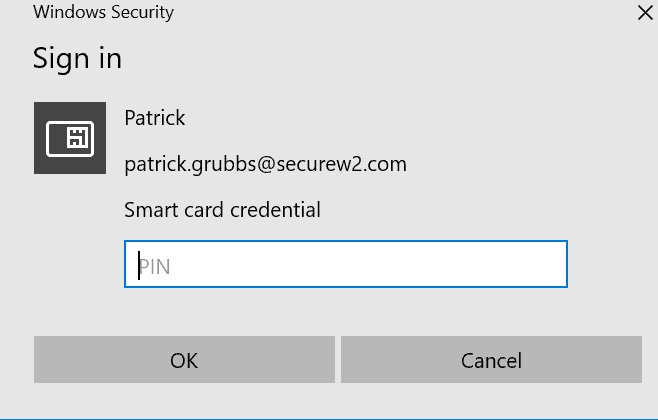
Enter the PIN attached to the connected Yubikey for Wi-Fi access.
From now on, access to the secure Wi-Fi network will be restricted unless the user has a properly configured security key.