TLS and EAP-TLS might seem identical initially since they depend on encryption and certificate-based authentication. TLS and extensible authentication protocols-transfer layer security (EAP-TLS) are often discussed in network security. They are used in various ways, though, and serve distinct purposes.
What is TLS?
Transport Layer Security (TLS) is a cryptographic system that supports secure network communication. It is typically used to replace Secure Sockets Layer (SSL) and encrypt data across the internet.
How TLS Works
TLS works by creating an encrypted link between two parties like:
- A website (HTTPS encrypted) and a web browser.
- A mail server and an email client.
- a VPN server and a VPN client.
This protocol guarantees three fundamental security principles:
- Confidentiality: Encrypting data to guard against unwanted access.
- Integrity: Preventing modifications to data while it is being sent.
- Authentication: Confirming the parties’ identities using digital certificates issued by a Certificate Authority (CA).
TLS uses a handshake, where the client and server trade keys and decide on encryption settings before securely forwarding data. In many common implementations (like HTTPS), only the server is authorized, even if both sides can be authenticated.
What is EAP-TLS?
Building on TLS, Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) protocol provides network authentication in 802.1X-secured environments like VPNs and corporate Wi-Fi networks.
How EAP-TLS Works
Before allowing network access, EAP-TLS is used to confirm the identity of users and devices. This is in contrast to regular TLS, which mainly secures communication across the internet.
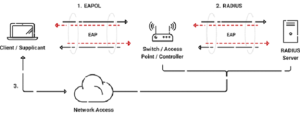
The 802.1X authentication architecture, which includes EAP-TLS, is typically preferred in:
- Wi-Fi networks for enterprises (WPA2-Enterprise & WPA3-Enterprise)
- Wired Ethernet networks
- VPN authentication
EAP-TLS is based on mutual authentication, meaning, the client, device or user, must have valid digital certificates as the authentication server.
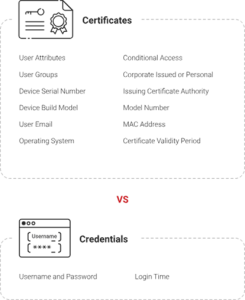
Important Distinctions Between TLS and EAP-TLS
Even though both TLS and EAP-TLS use encryption and certificate-based authentication, their functions and implementations differ.
a) Purpose and Use Case
The purpose of TLS is to protect data transfer over the internet. It is frequently used to encrypt VPN connections, email correspondence, and online traffic (HTTPS). TLS guarantees that your information is private and shielded from eavesdropping whenever you send an encrypted email, visit a secure website, or establish a VPN connection.
However, EAP-TLS is especially intended for network authentication before granting access. It confirms the identity of users and devices attempting to join a network, rather than protecting data while it is in transit. This ensures that only trusted users and devices may access business Wi-Fi networks (WPA2-business & WPA3-Enterprise) and VPN authentication.
b) Authentication Process
One of the main distinctions between TLS and EAP-TLS is how they authenticate users and devices.
How TLS Authentication Works
- By sending a “Client Hello” message, the client (such as a web browser) establishes a secure connection with the server.
- To verify its identity, the server replies with its TLS certificate issued by a Certificate Authority (CA).
- After the client confirms the server’s certificate, they establish a shared encryption key.
- After the handshake, the client and server securely send data to each other.
In most TLS implementations (like HTTPS), the client (user) does not need to present a certificate; only the server is authorized.
How EAP-TLS Authentication Works
- Using 802.1X authentication, a device (such as a laptop or smartphone) tries to connect to a Wi-Fi network.
- The RADIUS authentication server challenges the device to authenticate itself.
- The RADIUS server and the device display digital certificates to confirm each other’s identities.
- After successful authentication, the device is granted access to the network, and a secure session is created.
EAP-TLS necessitates mutual authentication, which means that both the client and server must have valid certificates, in contrast with standard TLS, which mainly authenticates the server. EAP-TLS is far more resilient to impersonation attacks because of this extra security measure.
c) Infrastructure Requirements
TLS requires a Certificate Authority (CA) to issue certificates, but in most circumstances, only the server needs one. For example, a website owner can secure their web server by purchasing an SSL/TLS certificate from a public CA. End users (like website visitors) do not require their own certificates, making TLS easier to implement.
However, EAP-TLS requires a comprehensive Public Key Infrastructure (PKI). This includes:
- A certificate authority (CA) is responsible for issuing and managing digital certificates.
- A RADIUS server will handle authentication requests.
- A certificate management system for distributing and revoking certificates on all devices.
EAP-TLS usually requires an internal (private) PKI since organizations must issue and manage certificates for their own users and devices, whereas TLS may rely on publicly issued certificates.
d) Security and Attack Resistance
TLS encrypts data in transit to protect it from interception. However, many TLS implementations (such as HTTPS websites and VPNs) continue to employ usernames and passwords for authentication, making them subject to phishing, brute force attacks, and credential theft.
EAP-TLS avoids password-based security vulnerabilities by requiring digital certificates instead. Because there are no passwords to steal or break, attackers cannot get access through phishing or brute force. Furthermore, mutual authentication verifies the client and the server before establishing a connection, making man-in-the-middle attacks almost impossible.
Why EAP-TLS is the Gold Standard for Network Authentication
Although PEAP-MSCHAPv2 and other password-based authentication techniques are still widely used in businesses, they are susceptible to over-the-air attacks, phishing, and credential theft.
For 802.1X networks, EAP-TLS is regarded as the most secure authentication technique because:
- Spoofing issues are eliminated via mutual authentication, which requires the client and server identity verification.
- Password-related attacks are eliminated since there is no password transmission or storage.
- Elliptic Curve Cryptography (ECC) and other more assertive encryption techniques eliminate brute-force attacks.
The main reason EAP-TLS is not widely used is because of challenges with deployment. Configuring a PKI for certificate management and issuance requires expertise, but cloud-based solutions like JoinNow from SecureW2 have significantly simplified the process.

Choosing the Right Protocol for Your Needs
When to Use TLS
- Securing web traffic (HTTPS).
- Encrypting emails (TLS for SMTP, IMAP, etc.).
- Protecting VPN traffic (TLS-based VPNs).
When to Use EAP-TLS
- Enterprise Wi-Fi networks (WPA2-Enterprise/WPA3-Enterprise).
- Genuine Trust security environments where user/device identity verification is crucial.
- VPN authentication without passwords.
EAP-TLS is ideal for enterprises seeking to enhance network security and eliminate password-related security threats.
Conclusion
Despite having identical cryptographic notions, TLS and EAP-TLS have different applications. TLS shields online communication, whereas EAP-TLS is meant for safe network authentication by mutual certificate validation.
EAP-TLS is currently the industry standard for commercial network security as it resists credential theft and man-in-the-middle attacks. Companies looking for a password-free authentication solution and improved security might consider using EAP-TLS via a cloud-based PKI provider for simpler deployment.
Contact us now to choose the optimal protocol for your security needs and enhance your cybersecurity posture.