Key Points
- The three Three Key Components are– Supplicant (device), Authenticator (switch/AP), and RADIUS (server) handle authentication.
- 802.1X requires unique credentials to block attacks like man-in-the-middle and ARP spoofing.
- SecureW2 simplifies 802.1X with cloud-based RADIUS and certificate management.
The 802.1X system has three primary components: the supplicant, the authenticator, and the authentication server. The supplicant is the part of the device that requests access, the authenticator is the network device (such as a switch or access point) that manages access, and the authentication server (often a RADIUS server) validates credentials and permits or refuses access.
802.1X improves network security by requiring unique credentials or certificates for each device, which reduces the risk of man-in-the-middle attacks and ARP spoofing.
To learn more about 802.1X and how it works, click here.
What is 802.1X Authentication Standard?
802.1x is the most extensive standard of 802.1 IEEE of Ethernet security todayIt is a form of port-based Network Access Control (PNAC) mechanism and specifies authentication for clients that must connect to the network via a wireless access point or a wired switch.

This standard aims to provide clients (end devices) with a consistent, universal approach to prove their identification and permission to be on a network. This is accomplished by authenticating to a network device via a central AAA (authentication, authorization, and accounting) security server or RADIUS server, supporting the authentication.
Components of 802.1X Authentication
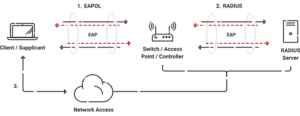
802.1X requires only a few components to function properly. You most likely already have everything you need for secure wifi, if you have access points and server space. For small installations, access points with built-in 802.1X software can even run without a server.
Client/Supplicant
Devices need supplicants in their network stacks to participate in 802.1X authentication. A supplicant is needed to negotiate the EAP transaction with the switch or controller and package the user’s credentials in accordance with 802.1X. If a client does not have a supplicant, the switch or controller will reject EAP packets and will not be able to authenticate.
Fortunately, the majority of devices support 802.1X. Most exceptions are consumer electronics like gaming consoles, entertainment devices, and printers. These devices should make up less than 10% of your network and should be viewed as an exception.
Controller/Access Point/Switch
The switch, or wireless controller, acts as a “broker” in the 802.1X transaction, which involves client and switch communication.
The switch/controller sends the client an EAPOL-Start packet when it connects to the network. The Wireless Security Settings determine which RADIUS server receives client answers. After authentication, the switch/controller decides whether to authorize network access depending on the user’s status and maybe the RADIUS server’s Access_Accept packet.
After authentication, the RADIUS server may deliver an Access_Accept packet containing information on how to connect the device to the network. Common characteristics determine a user’s VLAN or ACLs (Access Control Lists) once joined. Since the RADIUS server judges user credentials, this is dubbed “User Based Policy Assignment.” Common use cases include pushing guests to a “Guest VLAN” and workers to an “Employee VLAN”.
RADIUS Server
The network’s “security guard” is the RADIUS server, which authenticates and authorizes users. A user can access the network after registering for a PKI certificate or verifying credentials. The RADIUS verifies the user’s certificate or credentials and blocks unauthorized users when they connect.
Server certificate validation is a critical RADIUS security measure. This ensures that the user only connects to the intended network by setting their device to verify the RADIUS server certificate. The device will not deliver a certificate or authentication credentials if the certificate is not the right one.
Users from other organizations can be authenticated using RADIUS servers. RADSEC and Eduroam employ RADIUS servers as proxies. For example, a student visiting a neighboring institution can use the RADIUS server by validating their status at their home university and be granted secure network access.
Network Security with 802.1X and SecureW2
Implementing 802.1X authentication is critical for securing wired and wireless networks against unauthorized access and attacks. A RADIUS server helps organizations provide safe, user-specific authentication without compromising network integrity. Without the proper tools, though, controlling 802.1X may be difficult. With managed certificate services, cloud-based RADIUS authentication, and user-friendly PKI solutions, SecureW2 streamlines deployment and replaces dependency on shared passwords. Strong security policies, credential theft prevention, and improved user experience are just a few of the things SecureW2 lets organizations implement.
Contact us to help build a safe and scalable network architecture.