If we were to define our platform briefly, we’d say that SecureW2 makes it easier to transition to passwordless security by providing an easy Public Key Infrastructure (PKI) and RADIUS platform. Put together, PKI and RADIUS lay the foundation for network access that doesn’t rely on insecure password-based authentication. Of course, we also provide similar certificate-driven security for other use cases, including application security and code-signing.
But the rollout for our solutions varies greatly depending on your unique environment and needs. In another article, we addressed what this looks like if you need us to integrate with a device management platform. Here, however, we’re going to describe what the rollout process looks like if your environment includes BYODs/unmanaged devices you’ll need to enroll for certificates.
If you think supporting BYODs is complex, the good news is that it doesn’t need to be. Let’s talk about how our platform empowers self-service, end-user device onboarding without compromising on security and without being a hassle to set up.
Overview of the SecureW2 Setup
The full adoption and rollout process differs based on your environment. One of the key factors for determining what it will be like is whether you’re securing managed or unmanaged devices with our platform. We’ve already created an article on what this process looks like for MDM integrations, and you can read more about it here.
Since this article is focused on setting your end-users up for self-service enrollment, we won’t be discussing MDM integration here. As a quick summary, you’ll generally go through these steps as you get set up:
- A series of 2 or more initial configuration calls (the exact number depends on your environment)
- A meeting to confirm the policies and authentications you need
- A follow-up call to ensure your deployment went smoothly
In general, these meetings are spread out over anywhere from 2-4 weeks. However, this is entirely dependent on whatever timeline your organization is most comfortable with. We’ll detail the calls more below.
How Many Calls?
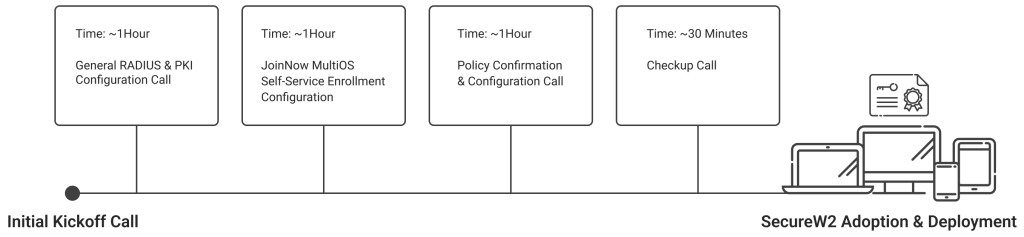
The process of adoption starts with a series of calls in which your team will meet with our support team. Exactly how many calls varies based on your infrastructure and the number of things we’ll need to configure integrations with. We’ll have a kickoff meeting where we outline the process for you, and during this meeting, we recommend scheduling all other calls so all parties have a clear plan. If possible, we’ll also ask you for a rollout date here, which will help us define your schedule and prepare for any extra support you may need as the date approaches.
At a very basic level, you’ll have at least one hour-long call in which we configure general features of our RADIUS and PKI with your infrastructure. Then, to set your organization up for self-service certificate enrollment through JoinNow MultiOS, there will be another hour-long call.
Afterward, we’ll want to confirm the policies you need set up and that everything is working correctly. This takes another hour.
That’s all it takes in the beginning. On these calls, our support team will work with you to provide a white glove deployment experience, helping you set up exactly which policies you need and integrating with your Identity Provider. We’ll answer any questions you need, provide you with any necessary documentation, and walk you through it.
Later on, just to confirm everything is working smoothly for you, we’ll follow up again with a 30-minute checkup call. The purpose of this call is to ensure your implementation was successful and address any concerns you may have. If you have time, we can even make these calls recurring on a quarterly basis, although you can reach out to our support team whenever you need help.
Who Needs to Be on the Calls?
Who we need to talk to from your organization can differ based on your unique infrastructure and needs. Since job titles vary from organization to organization, we’ll list out what attendees need to have access to rather than specific titles.
Generally, we’ll need people with the following types of administrative-level access:
- Access to your Identity Provider (IDP)
- Access to your network infrastructure (controllers and RADIUS, if you have an on-premise RADIUS)
These people will be meeting with one or more of our support team members and someone from our customer success team to ensure a smooth transition.
What are the Goals of the Calls?
The calls we have are generally segmented into one of two types: calls in which we are setting up for deployment in an environment for unmanaged devices/BYODs, and those managed by an MDM. As you can imagine, the specifics and goals depend on which category of call.
However, the overall goal is to implement successfully and test your implementation to make sure everything is running smoothly. Afterward, we want to ensure you have time to test our platform off-call and get a feel for how it works.
If there are any issues, the goal in our next scheduled call will be to resolve those issues and determine why they occurred in the first place. At the end of the day, our ultimate goal is to ensure that you understand how our solutions work and how to use them to your greatest benefit.
Making the Rollout for BYOD Enrollment Easier
In many ways, with BYODs in the picture, there’s more involved in preparing your end-users than if you were just pushing certificates to them through an MDM and SCEP. You need to rely more on end-users, with their various devices, to understand and go through the process, which can be seem daunting initially. There’s a bit of social engineering involved to get them to onboard themselves, but we’ve seen many organizations do it – and we know yours can, too.
We’ll go over some common strategies we’ve seen organizations use to prepare their end-users.
Make sure you explain the benefits to your users in clear, understandable terms.
The easiest way to get your users to quickly enroll themselves for certificates is to ensure they understand why you’re making the change. It’s easy to frame certificate-based authentication in a way that benefits everyone – because it really does.
Start by explaining at a high level how certificate-based authentication works. We often use the metaphor that certificates are like photo IDs; more secure than passwords, because they’re linked to a specific person or device. They’re also easier to use and don’t require resets or complex parameters like passwords, which means fewer disconnects from important resources.
Additionally, certificates can be used to access multiple resources. It’s like having a master key to most things you users will need; they can use certificates to connect to the Wi-Fi if you’re doing EAP-TLS, they can use it to access cloud applications, and they can even use certificates for desktop login.
Now that’s much easier than having different passwords for everything. Or, worse yet, using the same password for everything and putting accounts at risk.
Give your users plenty of advance notice.
Although our JoinNow MultiOS platform is easy to use, it’s better not to spring it on your users unexpectedly. You’ll get more cooperation if they’re aware of what’s coming up.
We recommend sending out emails in well in advance – possibly even reminders as the rollout date approaches. You know your organization best, so you likely understand how much notice your users need.
However, we also know emails aren’t always the best way to reach everyone. Consider other methods of notifying your organization, such as posters in public spaces like break rooms. You could even include QR codes to the JoinNow MultiOS onboarding page for your organization here to simplify the process for your users.
Use a vanity URL that’s easy to remember.

Everyone has differing levels of technical literacy. Most may be comfortable with navigating to the JoinNow MultiOS onboarding page entirely on their own, but others may have different preferences or need more assistance. We recommend having a few alternative ways to get them there.
An easy one we see organizations use a lot is vanity URLs. They’re much easier to remember than standard URLs. You could call yours something such as “Wifi.yourdomain” or “Wifi.yourorganzationname” or whatever else you feel is appropriate.
We’ve also seen organizations utilize QR codes. If you’re alerting users to the change with posters or emails, you could include these QR codes there for easy access.
You can also provide an onboarding Wi-Fi network with whitelisted access to only the resources users need to enroll. Have it bring visitors directly to your JoinNow MultiOS splash page so they can begin the process of certificate enrollment. Once they’re there, our dissolvable application will guide them the through the rest.
Transition your users gradually.
If you’re using JoinNow MultiOS to configure your users for EAP-TLS, you don’t need to move them all over at once. You can segment users into different groups, and start by moving those who will be least impacted by any sort of disruptions over onto your secure SSID.
In the meantime, you can have your existing SSID running concurrently, allowing everyone without certificates to stay connected and continue working. You can gradually phase these types of connections out over time. Once you’re ready, you can shut this SSID off entirely.
Rolling Out the JoinNow Platform: the Basics
How Long Does it Take?
We estimate the process can take anywhere from 2-4 weeks to fully deploy, but that is entirely dependent on your schedule. As we mentioned above, there are a few calls you’ll need schedule and people you’ll need to get together for those calls. However, we can meet your needs as quickly as you need, so if you have a faster timeline in mind, don’t hesitate to let us know.
The sooner we can get through the implementation calls with your administrators, the faster you can roll out our platform. Off-call, you can take as much time as you need to acclimate.
When Should it Be Done?
When you should go through each phase of the rollout process is another question our customers face. This is especially common with educational facilities that may be closed during the summer or for holiday breaks, but it also applies to enterprises. Many administrators worry about disrupting end-user network access and may therefore put off the process of implementing our platform longer than necessary.
The answer is that it depends on your organization and availability. Our support team is experienced and has worked with thousands of enterprises, though, and you can rest assured that we can help you deploy as quickly and smoothly as possible with minimal disruption to your environment.
What Needs to Be Configured?
With JoinNow MultiOS, the main thing we’ll need to configure is connecting to your SAML Identity Provider. This involves linking our portal to your IDP, creating a SAML application in your IDP, and then mapping certificate attributes and policies.
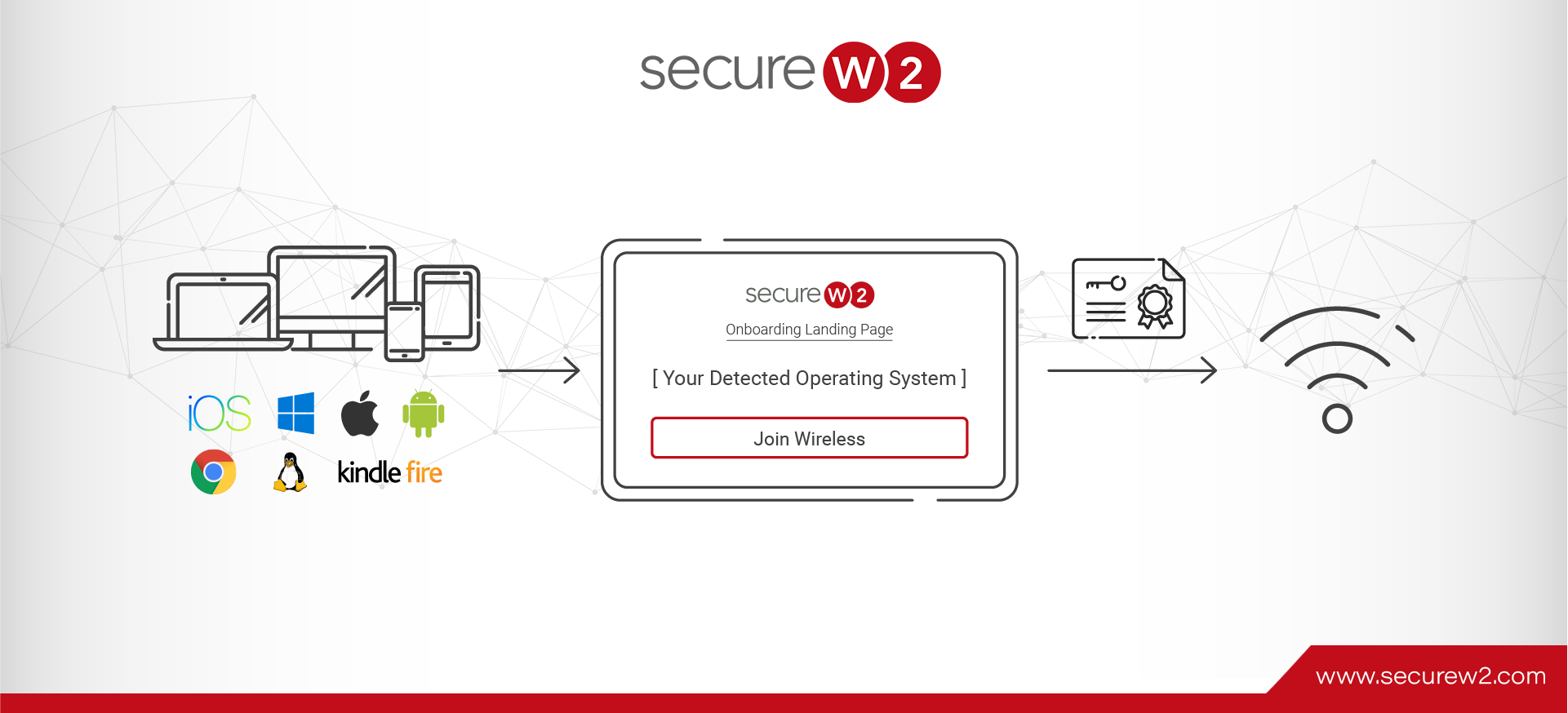
At the end of the day, you’ll have an onboarding page for users to access on their BYODs that will configure their devices for certificate-based authentication. It generally follows this flow:
- The user connects to your device onboarding SSID.
- They’re brought to the JoinNow MultiOS page, where they’re prompted to enter their SAML IDP credentials.
- After they’ve been authenticated and their credentials verified, JoinNow MultiOS runs and installs the proper Wi-Fi profile (if you’re doing EAP-TLS) and certificates for them.
SecureW2 Makes it Simple to Securely Support BYODs in Enterprise Environments
Allowing BYODs/unmanaged devices in a business setting can leave administrators feeling nervous. There’s no guarantee that they’ll all be secure and it also means you have a wide range of operating systems to deal with, each with their own quirks.
But our platform was designed to integrate with every environment, including ones that have unmanaged devices. JoinNow MultiOS prevents any end-user misconfiguration with an ultra-simple dissolvable application that only needs to be run once.
If you’d like more details on how it works, check out our guide on using SAML for WPA2-Enterprise authentication. You can also reach out to our knowledgeable team with any additional questions or concerns. We pride ourselves on a deployment process that’s being continuously refined; there’s a reason so many customers rave about our support team on G2.