The adoption of remote work, cloud computing, and integrated IoT devices leads to complexities of securing computer networks and network security infrastructures. The evolution of cyber threats—from sophisticated malware attacks to zero-day exploits—requires a meticulous, multi-layered security approach. Chief Information Security Officers (CISOs) are under great pressure to safeguard network resources and maintain seamless network performance while ensuring compliance with rigorous security policies and regulations.
This article looks into critical aspects of network security, core components, prevalent threats, and viable network security solutions for modern organizations. The article aims to help security teams design and implement effective network security strategies that fortify their defenses against growing threats.
What Constitutes Network Security?
Network security refers to the set of technologies, processes, and practices to safeguard computer networks and network security infrastructures from unauthorized access, misuse, and cyber threats. It involves implementing comprehensive security measures to protect networked data’s confidentiality, integrity, and availability. This includes deploying access control mechanisms, encryption protocols, and intrusion prevention systems to monitor and manage network traffic, ensuring that only authorized users can access network resources. Network security aims to protect valuable data and maintain the seamless operation of network services, shielding the organization from both internal and external threats that could compromise network performance and lead to data breaches or other critical security incidents.
How is Network Security Different from Information Security?
While network security focuses on protecting the integrity, confidentiality, and availability of data as it traverses across computer networks, information security is a broader domain encompassing the protection of information in all its forms. Information security addresses data security whether it is stored, processed, or in transit, incorporating aspects such as data loss prevention (DLP), and compliance with security policies. On the other hand, network security focuses on safeguarding network infrastructure through firewalls, VPNs, and intrusion prevention systems to ensure secure access and data flow across network segments, mitigating risks from cyber threats and unauthorized users.
Components of Network Security
Effective network security is built on several core components:
- Firewalls: Act as the first line of defense by filtering incoming and outgoing traffic.
- Intrusion Detection and Prevention Systems (IDPS): Detect and prevent malicious activities.
- Antivirus Software: Protects against malicious software.
- Virtual Private Networks (VPNs): Ensure secure remote access.
- Network Access Control (NAC): Manages access to network resources.
- Security Information and Event Management (SIEM): Monitors and analyzes security events.
We will discuss these components in subsequent sections.
Essential Concepts in Network Security
Let’s explore some important concepts in network security.
Network Access Control
Network Access Control (NAC) is a key concept in network security that enforces security policies by controlling which devices and users can access network resources. It ensures that only authorized users and compliant devices gain access, minimizing security risks. NAC systems evaluate the security posture of devices, ensuring they meet predefined criteria such as having up-to-date antivirus software and security patches. By continuously monitoring and managing network traffic, NAC solutions help maintain the integrity and confidentiality of data within the network, shielding it from potential threats posed by unauthorized users and compromised devices.
Physical and Logical Security
Network security involves a comprehensive approach that addresses both physical and logical aspects. Physical security pertains to protecting the hardware and infrastructure from threats like theft, sabotage, and natural disasters. This includes securing server rooms, network devices, and data centers against unauthorized physical access. Logical security, conversely, focuses on protecting data and system resources through software-based measures like access control, encryption, and user authentication mechanisms. Logical security ensures that data remains secure during transmission across network segments and that only authorized users can interact with sensitive information, thereby reducing the risk of cyber threats.
Network Integrity and Authentication Mechanisms
Ensuring network integrity involves maintaining the accuracy and consistency of data as it traverses the network. This is crucial for preventing tampering and ensuring data remains unaltered during transmission. Authentication mechanisms are integral to this process, verifying the identities of users and devices before granting access to network resources. Common authentication methods include:
- Passwords: A basic form of authentication, albeit prone to weaknesses.
- Multi-Factor Authentication (MFA): Combines two or more verification factors.
- Biometrics: Utilizes unique physical characteristics for verification.
- Digital Certificates: Employ public-key cryptography to authenticate users.
These mechanisms fortify network integrity, ensuring only authenticated and authorized users can access sensitive data and network segments.
Types of Network Security Threats
Some of the common network security threats include:
| Malware | Malware, or malicious software, encompasses viruses, worms, trojans, ransomware, and spyware. These programs are designed to infiltrate and damage computer systems, steal sensitive data, or disrupt network operations. Organizations must deploy robust antivirus software and advanced threat detection systems to mitigate the risk of malware attacks. |
| Phishing Attacks | Phishing attacks trick users into revealing sensitive information through deceptive emails or websites. These attacks exploit human psychology and trust to access confidential data like login credentials and financial information. Email security measures and employee awareness programs can significantly reduce the risk of phishing attacks. |
| Man-in-the-Middle Attacks | Man-in-the-Middle (MitM) attacks occur when a cybercriminal intercepts and manipulates communication between two parties without their knowledge. These attacks can compromise sensitive information and disrupt network services. Encryption protocols like TLS/SSL are essential for preventing MitM attacks by ensuring secure data transmission. |
| DDoS Attacks | Distributed Denial of Service (DDoS) attacks overwhelm a network or service by flooding it with an excessive amount of traffic, rendering it unavailable to legitimate users. Combatting DDoS attacks requires a multi-faceted approach including traffic analysis, traffic filtering, and leveraging services from DDoS mitigation providers. Effective DDoS response plans should be integral to any robust network security strategy. |
| Insider Threats | Insider threats pose significant risks as they involve individuals, such as employees or contractors, who intentionally or unintentionally compromise security. Mitigating insider threats requires strict access controls, continuous monitoring, and comprehensive security awareness training. Implementing Data Loss Prevention (DLP) technologies can also help identify and prevent unauthorized data transfers. |
| Zero-day Exploits | Zero-day exploits target vulnerabilities that are unknown to the software vendor or security community, making them highly dangerous. Since no patches or fixes are available, these exploits can cause severe damage. Organizations must employ proactive threat intelligence, regular vulnerability assessments, and real-time monitoring to detect and respond to zero-day threats promptly. |
Vulnerability Assessment in Network Security
Regular vulnerability assessments are vital for identifying and addressing security weaknesses in network infrastructure. These assessments involve:
- Identifying assets and potential threats: Mapping out all network resources.
- Scanning for vulnerabilities: Using automated tools to detect weaknesses.
- Evaluating impact and likelihood: Assessing the potential impact of identified vulnerabilities.
- Prioritizing remediation: Addressing vulnerabilities based on their severity and potential impact.
Several tools assist in conducting thorough vulnerability assessments, such as Nmap, Nessus, Qualys and others. After conducting a vulnerability assessment, it is crucial to analyze the results to prioritize remediation efforts. This involves:
- Identifying critical vulnerabilities: Focus on those with the highest impact.
- Tracking remediation progress: Ensuring that identified vulnerabilities are addressed promptly.
- Reassessing and verifying fixes: Conducting follow-up scans to confirm the effectiveness of remediation efforts.
Virtual Private Network (VPN)
A Virtual Private Network is a critical network security solution that creates a secure, encrypted connection over the internet, often referred to as a “tunnel,” which protects data from interception and unauthorized access. VPNs ensure secure remote access to an organization’s network, enabling remote users to connect to the company network securely. Setting up a secure VPN involves precise configuration and adherence to best practices. The key steps include:
- Selecting a Reliable VPN Provider: To ensure user privacy, choose a provider with strong encryption standards, robust security features, and a strict no-logs policy.
- Configuring VPN Protocols: Implement secure protocols such as IPsec or OpenVPN to establish encrypted tunnels.
- Multi-Factor Authentication (MFA): To enhance security, add MFA to the VPN login process, requiring multiple verification methods.
- Regular Software Updates: Ensure that the VPN software and associated firmware are regularly updated to protect against known vulnerabilities and emerging threats.
Limitations of VPNs in Network Security
While VPNs offer significant security benefits, they come with inherent limitations:
- Performance Impact: The encryption process can introduce latency and reduce network performance.
- Complex Configuration: Properly configuring VPNs can be complex and time-consuming, requiring specialized expertise.
- Single Point of Failure: VPN servers, if compromised, represent a critical vulnerability.
- Limited Scope: VPNs cannot protect against all forms of network security threats, particularly insider threats or application-level attacks.
Despite these limitations, VPNs remain a cornerstone in securing remote access and protecting sensitive data in transit.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access represents a fundamental shift in network security paradigms, moving away from traditional perimeter-based defenses towards a model that assumes no implicit trust. Under ZTNA, every access request is meticulously authenticated, authorized, and encrypted, regardless of the user’s location or device. ZTNA enforces the principle of least privilege, granting access only to the necessary network segments and resources required for specific tasks. This granular control minimizes the attack surface and mitigates risks from potential unauthorized users and insider threats.
Implementing ZTNA involves integrating with existing security tools and deploying robust access control mechanisms, continuous monitoring, and real-time risk assessment. Unlike traditional VPNs or firewalls, ZTNA dynamically adapts to changing security conditions, ensuring that device compliance and user identity verification are maintained throughout the session. Benefits of ZTNA include enhanced security posture, improved regulatory compliance, and streamlined access management. As cyber threats evolve and networks become more complex, adopting ZTNA is crucial for organizations aiming to protect their network infrastructure comprehensively.
Network Security Protocols
Network security protocols are fundamental for protecting data and ensuring secure communication within computer networks and network security infrastructures. These protocols define how data packets are transmitted and safeguarded across networks. Key network security protocols include:
- Transport Layer Security/Secure Sockets Layer (SSL/TLS)
- IPsec (Internet Protocol Security)
- Secure Shell (SSH)
- Hypertext Transfer Protocol Secure (HTTPS)
How TLS/SSL Secure Data Transmission
TLS/SSL protocols are essential for securing web traffic by encrypting data transmitted between clients and servers. They use a combination of asymmetric and symmetric cryptography to establish a secure connection. The process involves:
- Handshake Protocol: Initiates a secure session by exchanging cryptographic keys.
- Record Protocol: Ensures that data transmitted during the session is encrypted and integrity-protected.
- Alert Protocol: Communicates security issues or errors in the communication process.
By leveraging digital certificates, TLS/SSL validates the server’s identity and creates a secure channel for data exchange, preventing interception and tampering by malicious actors.
IPSec Protocol
IPsec is a versatile protocol suite that secures IP communications through authentication and encryption. It operates in two modes:
- Transport Mode: Encrypts only the payload of the IP packet, leaving the header intact.
- Tunnel Mode: Encrypts both the payload and the header, creating a new IP packet.
IPsec utilizes two main protocols:
- Authentication Header (AH): Provides integrity and authentication.
- Encapsulating Security Payload (ESP): Offers encryption, authentication, and integrity.
IPsec is widely used to create virtual private networks (VPNs) and remote access VPNs, ensuring secure communications over untrusted networks.
Secure Shell (SSH)
Secure Shell is a protocol designed to provide secure access to remote computers. It encrypts data exchanged between the SSH client and server, safeguarding against interception, eavesdropping, and connection hijacking. The key features of SSH include:
- Strong Authentication: Uses keys or passwords for user authentication.
- Data Encryption: Ensures data confidentiality during transmission.
- Command Execution: Allows secure execution of commands on remote machines.
SSH is critical for secure remote administration and file transfers, making it an essential tool in any network security toolkit.
Network Security Tools and Technologies
Implementing a range of essential network security tools is crucial to effectively safeguarding a computer network and mitigating cyber threats. These tools encompass various technologies and practices designed to monitor, detect, and respond to security incidents, ensuring comprehensive network security protection.
Firewalls
Firewalls are pivotal network security devices that act as the first line of defense by filtering network traffic based on predefined security rules. They create barriers between trusted and untrusted networks, preventing unauthorized access to corporate networks and shielding critical data from external threats. Firewalls can be hardware- or software-based and are essential for maintaining secure and reliable access to network resources.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) are advanced security tools designed to detect and prevent malicious activities within computer networks. These systems monitor network traffic for suspicious patterns and behaviors, automatically blocking or mitigating potential threats. IDPS solutions play a vital role in identifying and responding to network security attacks, bolstering overall network security.
Network Security Monitoring Tools
Network security monitoring tools provide real-time visibility into network traffic, enabling security teams to detect and respond to anomalies swiftly. Tools like Wireshark, Snort, and Zeek analyze network traffic for unusual behavior, aiding in the early detection of potential security breaches and facilitating proactive threat management.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems aggregate, analyze, and respond to security events from various sources. SIEM solutions offer a centralized view of network security, correlating data from firewalls, IDPS, and other security controls to identify potential threats. By providing comprehensive insights, SIEM systems enable effective incident response and enhance overall network security protection.
In addition to these core tools, various other technologies are instrumental in fortifying network security:
- Secure Web Gateways: These solutions provide web security by monitoring and controlling web traffic, preventing access to malicious websites.
- Network Segmentation: Divides the network into smaller segments, limiting lateral movement of attackers and enhancing network security.
- Wireless Network Security: Protects against threats targeting wireless networks, ensuring the security of wireless communications and devices.
- Cloud Security: Addresses the unique security challenges of cloud environments, ensuring data protection and compliance with industry standards.
- Mobile Device Security: Ensures the security of personal mobile devices used to access the network, mitigating risks associated with mobile access.
- Industrial Network Security: Tailored for securing industrial control systems (ICS) and operational technology (OT) environments, critical to infrastructure and manufacturing.
- Web Security Solutions: Protects web applications from threats like SQL injection, cross-site scripting (XSS), and other web-based attacks.
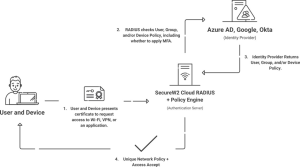
SecureW2’s Cloud RADIUS and JoinNowPKI: Enhancing Network Security with Zero Trust
SecureW2’s Cloud RADIUS and JoinNowPKI solutions adhere to the Zero Trust Network Access (ZTNA) principle, providing a transformative approach to network security. Our Cloud RADIUS offers a robust and scalable RADIUS server that delivers advanced authentication and authorization capabilities. It seamlessly integrates with existing network infrastructures, ensuring that only authorized users and compliant devices—managed or unmanaged—can access network resources. This minimizes the risk of security breaches and unauthorized access, reinforcing the organization’s overall security posture.
JoinNowPKI is a comprehensive Public Key Infrastructure (PKI) solution that simplifies the issuance and management of digital certificates. By leveraging SecureW2’s JoinNowPKI, organizations can enforce stringent network access control policies, ensuring that every device and user is authenticated before gaining network access. This aligns with the zero trust philosophy of “never trust, always verify,” providing an additional layer of security against potential cyber threats.
Together, these solutions enhance network security by offering secure, identity-based access for employees and guest users and streamlined certificate management. SecureW2’s Cloud RADIUS and JoinNowPKI fortify network infrastructure and simplify security management, delivering reliable and secure access to critical network resources.