Data security has never been more critical. Hardware Security Modules (HSMs) are pivotal in safeguarding the cryptographic infrastructure of numerous global enterprises. HSMs have come a long way, from niche, hardware-based security tools to integral components of modern cybersecurity architectures, which is remarkable. Initially tailored for highly specialized applications, HSM technology has evolved to address a broader spectrum of data security challenges.
This evolution reflects the growing sophistication of cyber threats and the expanding need for robust data protection measures across industries. So, what exactly is an HSM? In this article, we look at HSMs in detail, how they work, their features, and how they enhance PKI security.
What is a Hardware Security Module?
A Hardware Security Module is a specialized, physical computing device designed to securely manage, process, and store cryptographic keys and perform other security-critical functions. These highly secure devices are engineered to protect sensitive data security keys within a tamper-resistant hardware environment, ensuring that cryptographic operations such as generating keys, encryption, decryption, and digital signing are executed with the highest level of security.
Tailored to prevent unauthorized access and manipulation, HSMs serve as the foundation for robust data security infrastructures, supporting Public Key Infrastructure (PKI) systems, facilitating secure transactions, and enforcing strong authentication mechanisms. By safeguarding cryptographic keys—the linchpins of data security—HSMs play a crucial role in defending against data breaches, unauthorized data access, and other cyber threats, making them indispensable in information security and compliance.
What is PKI HSM?
Public Key Infrastructure (PKI) is the foundation for establishing trust in the digital space. It manages digital certificates and public keys, facilitating secure data exchange over the Internet. PKI is crucial for authenticating identities and encrypting sensitive information.
Integrating HSMs into PKI architectures elevates the security of cryptographic keys and operations. HSMs ensure that private keys, the linchpins of PKI security, are generated, stored, and managed in a hardware-ensconced environment, impervious to external threats. This synergy fortifies the trustworthiness and integrity of the PKI framework, protecting against breaches and unauthorized access.
How HSMs Work
HSMs operate on secure, controlled processes to protect cryptographic keys and perform sensitive operations within a hardened, tamper-resistant device. The core functionality of an HSM includes a series of critical steps and mechanisms designed to ensure the utmost security and integrity of data:
- Key Generation: Utilizing secure random number generators (RNGs), HSMs create cryptographic keys with high entropy, making them difficult to predict or replicate. This randomness is crucial for the security of cryptographic systems.
- Encryption/Decryption: HSMs encrypt sensitive data using these cryptographic keys, ensuring data confidentiality. Conversely, they decrypt data, allowing authorized access only.
- Digital Signing and Verification: They generate and verify digital signatures, establishing the authenticity and integrity of digital documents and transactions.
- Secure Key Storage: Cryptographic keys are stored within the secure confines of the HSM. Access to these keys is strictly controlled, and mechanisms prevent unauthorized extraction.
- Key Management and Lifecycle: Beyond generation and storage, HSMs manage the entire lifecycle of keys, from activation to expiration and deletion, in compliance with security policies and standards.
By executing these operations in a dedicated hardware security module rather than in software on a general-purpose server, HSMs ensure that encryption keys and operations are protected against physical and logical attacks. This makes HSMs important for secure data encryption, digital signing, and authentication processes in numerous high-stakes environments.
Types of Hardware Security Modules
There are two main types of Hardware Security Modules:
LAN-Based HSMs
LAN-based HSMs provide secure cryptographic services across networked environments, balancing security and accessibility. They are particularly suited for organizations that require high-performance data security key management and cryptographic processing across distributed systems.
PCIe-Based HSMs
For applications demanding extreme throughput and minimal latency, PCIe-based HSMs offer a solution. They are directly integrated into servers via the Peripheral Component Interconnect Express (PCIe) interface, providing fast, direct access to cryptographic functions. This type of HSM is ideal for high-volume transaction environments like financial institutions and cloud service providers.
Key Features of HSM Security
The security features provided by hardware security modules are paramount to the protection and management of encryption keys and the execution of high-assurance cryptographic operations. These features are meticulously designed to offer a secure anchor for many data security protocols, ensuring that sensitive data and digital transactions are always safeguarded. They include:
Generating Cryptographic Keys Securely
HSMs employ secure random number generators (RNGs) to produce cryptographic keys. This process ensures the keys generated possess high entropy, making them virtually impervious to brute-force attacks and predictions. The security of cryptographic systems begins with the strength and unpredictability of its keys, a feature HSMs adeptly provide.
Storing Private Keys with Maximum Security
A distinguishing capability of HSMs is their ability to store private keys securely within a physically tamper-resistant environment. This secure storage is critical in preventing unauthorized access and key extraction, thereby protecting the foundational elements of encrypted data and digital signatures from potential breaches.
Managing Key Lifecycle on HSM
A core function of HSMs is managing cryptographic keys’ lifecycles, from creation and usage to retirement and deletion. By enforcing strict policies and procedures throughout these lifecycles, HSMs ensure that each key remains effective and uncompromised, bolstering the organization’s overall security posture.
Digital Signatures and Authentication
HSMs facilitate the secure generation and verification of digital signatures, thereby certifying the authenticity and integrity of digital documents and transactions. Furthermore, they enable robust authentication mechanisms, ensuring only authorized parties can access sensitive data or systems.
Encryption and Decryption Processes
At the forefront of HSM functionalities is the secure encryption and decryption of data, ensuring the confidentiality and integrity of information, whether at rest or in transit. By providing a highly secure process for converting plain text into encrypted data and vice versa, HSMs are essential in maintaining privacy and preventing unauthorized data access.
Secure Code Execution within HSM
HSMs offer a secure execution environment for sensitive cryptographic functions, ensuring such processes are isolated from external threats and vulnerabilities. This capability is paramount in protecting the integrity and confidentiality of the operations themselves, making HSM an indispensable tool in establishing and maintaining secure digital ecosystems.
HSM Certificate Management
Managing digital certificates through Hardware Security Modules (HSMs) involves a sophisticated mechanism that ensures the secure issuance, renewal, and revocation of certificates, pivotal for encrypted data communication. This process involves several key activities deeply integrated within the secure confines of HSM devices:
- Secure Issuance of Certificates: HSMs use a private key to sign digital certificates securely. This process authenticates entities’ identities and facilitates the encryption of data exchanged over networks.
- Storage and Protection of Private and Encryption Keys: HSMs securely store the private key and encryption keys associated with digital certificates within the tamper-proof hardware. This secure storage is crucial to prevent unauthorized access and use of these keys.
- Decryption Keys Management: HSMs manage decryption keys, which are essential for accessing and using encrypted information. By securely storing and handling decryption keys, HSMs ensure that encrypted data remains confidential and tamper-resistant.
- Certificate Renewal and Revocation: HSM devices can renew certificates before they expire and revoke them if they are compromised. This management ensures the integrity and trustworthiness of the cryptographic system.
SecureW2’s PKI Backed by HSM Security
At the heart of SecureW2’s managed Public Key Infrastructure (PKI) is the unwavering security provided by Hardware Security Modules. This integration simplifies the complexity traditionally associated with managing a PKI. By harnessing the robust security features of HSMs, SecureW2’s PKI ensures the generation, storage, and management of cryptographic keys and digital certificates with unparalleled security, thwarting unauthorized access and potential breaches. Key elements such as secure key generation, encryption and decryption processes, and digital signing are executed within the impervious confines of HSMs, providing a solid foundation for SecureW2’s managed PKI.
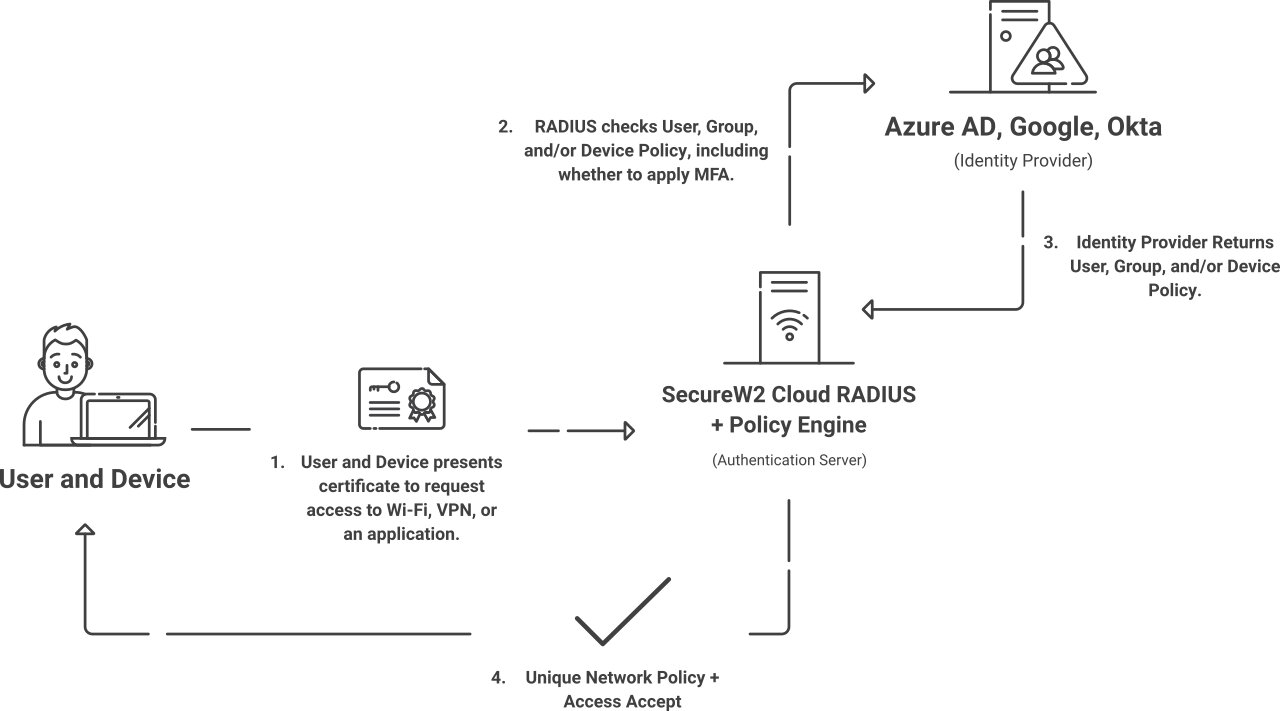
Through SecureW2’s PKI, businesses can confidently secure their digital transactions, communications, and identities, underpinned by the formidable security of HSM technology. Click here to see our pricing.


