In Wi-Fi security, one protocol stands out for its widespread adoption and significant role in protecting data: WPA2-PSK. This protocol, short for Wi-Fi Protected Access 2 – Pre-Shared Key, has been instrumental in securing wireless networks against unauthorized access and data breaches. However, as with any security measure, it’s critical to fully understand its strengths and vulnerabilities to leverage its protective capabilities.
This article explores WPA2-PSK in-depth, from its operational mechanics to best practices for maximizing security.
The Evolution of Wi-Fi Security: From WEP to WPA2-PSK
The journey of Wi-Fi security protocols began with Wired Equivalent Privacy (WEP), which was soon found to be fraught with security vulnerabilities. This led to the development of the first-generation Wi-Fi Protected Access (WPA), which significantly improved security but fell short against sophisticated attacks. The need for a more robust solution culminated in the advent of WPA2-PSK. This second-generation protocol introduced stronger encryption methods and improved key management, setting a new standard for wireless network security.
What Is WPA2-PSK?
WPA2-PSK is a Wi-Fi Protected Access 2 – Pre-Shared Key, a security protocol designed to secure wireless networks through advanced encryption standards. At its core, the PSK in WPA2-PSK refers to a pre-shared key, or password, used for the initial authentication between devices and the network access point. This pre-shared key serves as the foundation upon which a secure connection is established, safeguarding data as it travels across the wireless network.
How Does WPA2-PSK Work?
The operational heart of WPA2-PSK is its authentication and encryption mechanism. The protocol employs a four-way handshake to authenticate devices attempting to connect to the network. This handshake process ensures the access point and the device have the correct credentials (i.e., the WPA2 password) without transmitting the password itself over the air. Upon successful authentication, encryption keys are dynamically generated and used to encrypt the data transmitted between the device and the network. This ensures that even if network traffic is intercepted, it remains indecipherable to unauthorized users.
Temporal Key Integrity Protocol: The Backbone of WPA2-PSK Security
The Temporal Key Integrity Protocol (TKIP) plays a crucial role in the security framework of WPA2-PSK. TKIP enhances the security of data packets by dynamically changing the encryption key used for each packet, making it significantly more difficult for potential intruders to decrypt data by capturing packets over the network. This dynamic key generation process is essential in preventing attackers’ exploitation patterns, thereby ensuring a robust encryption mechanism that safeguards user data effectively.
WPA2 Passwords: Your First Line of Defense
A WPA2-PSK network’s security largely hinges on the complexity and strength of its WPA2 password. This password acts as the gatekeeper to the network, preventing unauthorized access by encrypting the communication between the device and the access point. A strong WPA2 password is your first and most crucial line of defense against potential intruders.
Best Practices For Setting a Strong WPA2 Password
Creating a strong WPA2 password is paramount in maximizing the security of your wireless network. Here are some best practices to consider:
- Length and Complexity: Ensure your password is at least 16 characters long and includes a mix of uppercase and lowercase letters, numbers, and special characters.
- Unpredictability: Avoid common words, phrases, or patterns that can be easily guessed or cracked by brute force attacks.
- Unique Passwords: Use a unique password for your WPA2-PSK network to prevent cross-network vulnerabilities.
- Regular Updates: Regularly changing your WPA2 password can help minimize the risk of unauthorized access, especially in environments where passwords may be shared with numerous users.
Strengths and Weaknesses of WPA2-PSK
Despite its robust security features, WPA2-PSK is not without its vulnerabilities. The protocol’s strength lies in its use of strong encryption and dynamic key generation, which provide a solid defense against most casual intruders and data breaches. However, it remains susceptible to more sophisticated attacks such as the KRACK (Key Reinstallation Attack), which exploits weaknesses in how WPA2 implements its four-way handshake.
Is WPA2-PSK Good Security? Can It Be Hacked?
WPA2-PSK provides good security for most home and small business networks, effectively protecting data from unauthorized access. However, no system is entirely hack-proof, and WPA2-PSK is no exception. Its vulnerability primarily lies in the strength of the WPA2 password. Weak or commonly used passwords can be cracked using brute force or dictionary attacks, granting attackers access to the network. Furthermore, the KRACK attack highlights a significant flaw in the WPA2 protocol, potentially allowing attackers to intercept and manipulate data. Despite these vulnerabilities, with strong, regularly updated passwords and awareness of the latest security patches, WPA2-PSK remains a secure choice for wireless network security.
WPA2-PSK Non-Attack Disadvantages
Beyond direct attacks, WPA2-PSK faces challenges related to password management and user convenience. The need to regularly update and manage strong passwords can lead to password fatigue among users, potentially compromising security practices. Additionally, managing a Pre-Shared Key (PSK) in environments with many users can be administratively burdensome, as each device needs the updated key every time it changes, posing a significant overhead for network administrators.
Which Is More Secure, WPA-PSK or WPA2-PSK?
When comparing WPA-PSK to WPA2-PSK, it’s clear that WPA2-PSK offers enhanced security measures. The advanced encryption standard (AES) used in WPA2-PSK provides stronger data protection than the TKIP of WPA-PSK, which has been deemed vulnerable to attacks over time. Additionally, WPA2-PSK improves on the key management and encryption protocols, making it the more secure option of the two. Thus, for individuals and organizations prioritizing network security, WPA2-PSK is the recommended choice.
How to Set Up and Manage WPA2-PSK
Setting up and managing WPA2-PSK involves accessing your router’s settings and configuring the network security options. Here’s a general guide:
- Accessing Router Settings: Open a web browser, enter your router’s IP address in the address bar, and press enter. You’ll be prompted to log in using your router’s admin credentials.
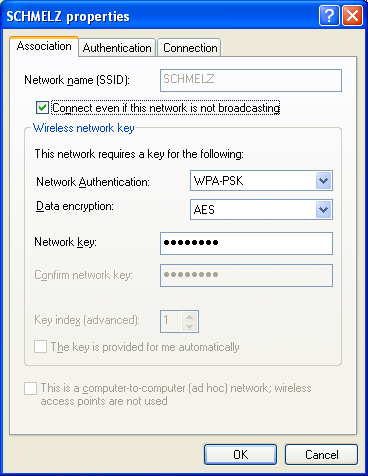
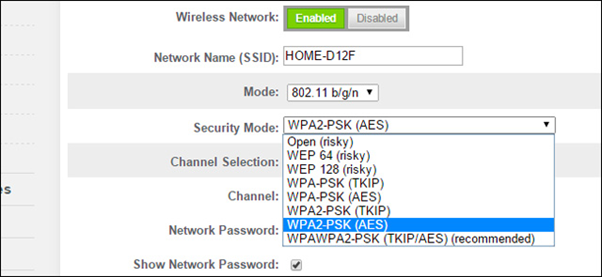
- Configuring WPA2-PSK Security: Navigate to the wireless security settings. Select WPA2-PSK as your security protocol and enter a strong password that adheres to the best practices mentioned earlier.
Where are the WPA2 Settings on a Router?
The specific location of WPA2 settings within a router’s interface can vary depending on the manufacturer and model. However, these settings are typically found under the “Wireless,” “Security,” or “Network” sections of the router’s admin panel. Once there, you should see options to select the security protocol (choose WPA2-PSK) and a field to enter or change the network’s password.
Where are WPA2-PSK Passwords Stored on a Router?
WPA2-PSK passwords are stored within the router’s configuration settings, specifically within the section where the wireless network’s security settings are managed. These passwords are stored in an encrypted form to prevent direct access or viewing by unauthorized users. However, it is crucial to ensure that router access is secured with a strong password to prevent unauthorized changes to the network’s security settings.
Enhance WPA2-PSK Security: Advanced Configuration Tips
Beyond basic setup, several advanced configurations can be employed to enhance the security of a WPA2-PSK network further. Implementing these additional measures can give users extra protection against potential vulnerabilities.
Customize WPA2-PSK Settings for Maximum Security
- Disable WPS (Wi-Fi Protected Setup): WPS can be a handy feature for easily connecting devices to your network, but it also presents a security risk. Disabling WPS can help prevent unauthorized access.
- Update Firmware Regularly: Keeping your router’s firmware up-to-date ensures that the latest security patches and features are applied, closing known vulnerabilities.
- Adjust Beacon Intervals and DTIM (Delivery Traffic Indication Message): These advanced settings can help manage how your network signals its presence to devices and manages power-saving features, but they should be adjusted carefully as they can affect network performance.
Leverage RADIUS Servers with WPA2-PSK for Enhanced Authentication
For businesses or tech-savvy users, integrating a RADIUS server into the WPA2-PSK setup can provide a more secure authentication method. RADIUS servers manage network access through centralized authentication, adding an additional layer of security by verifying users before granting access to the network.
Implement MAC Address Filtering with WPA2-PSK
MAC Address Filtering: This feature allows network administrators to specify which devices can connect to the network based on their MAC addresses. While not foolproof (as MAC addresses can be spoofed), it adds an extra hurdle for unauthorized devices trying to access the network.
Enhancing Network Security with SecureW2
Transitioning your Wi-Fi network away from traditional password-dependent security towards a more robust, certificate-based model marks a significant leap in safeguarding your digital infrastructure. SecureW2 offers an innovative and comprehensive suite of solutions designed to elevate network security to unprecedented levels. SecureW2’s managed PKI demystifies the complexities of deploying and managing certificates, making the transition to a secure, passwordless network not only feasible but also remarkably simple.
SecureW2 also integrates a RADIUS server designed to authenticate each access request rigorously. This ensures that network access is tightly controlled and consistently aligned with the latest security protocols. Organizations can significantly mitigate the risk of unauthorized access by utilizing SecureW2’s sophisticated passwordless authentication system, which is adept at applying current network policies through direct identity lookup from your IDP. SecureW2’s tools provide a clear pathway to a more secure, efficient, and user-friendly network authentication environment, paving the way for a future where Wi-Fi security is not just about passwords but about comprehensive, advanced protection. Schedule a free demo to discover the best way to keep your wireless network safe.