Wi-Fi connection integrity is critical for organizations securing sensitive data or individuals protecting personal information. This requirement has created many authentication methods, each attempting to balance usability and security. LEAP authentication is one example of a protocol created to provide a reliable method for validating users’ identities before authorizing access to Wi-Fi networks.
LEAP, commonly known as the Lightweight Extensible Authentication Protocol, is a popular network authentication mechanism. It authenticates users through their credentials, usually usernames and passwords, before providing them with network access. In this article, we’ll look at the details of LEAP authentication, including how it works, what security features it has, and how it helps protect Wi-Fi networks from cyber attacks.
Understanding LEAP Authentication
LEAP is a Wi-Fi authentication protocol created by Cisco. Its main characteristics are dynamic WEP keys and mutual authentication between wireless clients and RADIUS servers. This authentication strategy enables frequent reauthentication, guaranteeing that clients obtain new WEP keys after successful authentication. This strategy aims to reduce the window of opportunity for attackers to crack WEP keys, improving Wi-Fi network security. LEAP, like EAP-MD5, has long been vulnerable to dictionary attacks, with Joshua Wright’s publication of tools like Asleap in 2003 revealing the protocol’s flaws. Despite Cisco’s claim that LEAP can stay safe with sufficiently complicated passwords, real-world use of such passwords is frequently limited owing to usability issues for average users.
In contrast to LEAP, newer authentication protocols such as EAP-TTLS and PEAP overcome LEAP’s restrictions by creating secure TLS tunnels for the MS-CHAPv2 user authentication session. This solution improves security by encrypting authentication data and reducing the dangers associated with dictionary attacks. Furthermore, EAP-TTLS and PEAP are not limited to Cisco devices, making them more adaptable options for securing Wi-Fi networks with many access points. As organizations strive to improve their network security posture, adopting these newer protocols provides a practical solution to the increasing issues of Wi-Fi authentication while also assuring comprehensive protection against cyber attacks.
LEAP does not have native support in any Windows operating system. To use LEAP, you’ll need to follow Microsoft’s configuration guide first.
How does LEAP Work?
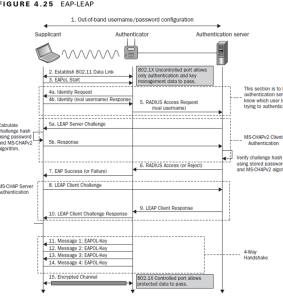
LEAP operates by using security mechanisms like dynamic WEP keys. This enables the client to authenticate several times with a RADIUS server. It also prevents an attacker from obtaining and utilizing the security key indefinitely.
The Authentication process (challenge/response) is performed using a modified version of MS-CHAPv2. However, the username is transmitted in cleartext, allowing an attacker to get it.
Should you use LEAP?
At the time of development, Cisco developed LEAP as something that was designed to be a more secure authentication method for wireless networks. Its enhanced security and accessibility were due to several factors.
One of the biggest reasons organizations chose LEAP was that there was no need to install or configure digital certificates. Because LEAP used mutual authentication, man-in-the-middle attacks were neutralized. LEAP’s biggest flaw, however, was that it implemented MS-CHAP, which meant that it inherited MS-CHAP’s security vulnerabilities, particularly the key issue of data transfer in plaintext. Many organizations, including Microsoft, advise moving away from protocols like MSCHAP and MSCHAPv2 to prevent credential theft.
Comparing LEAP and PEAP
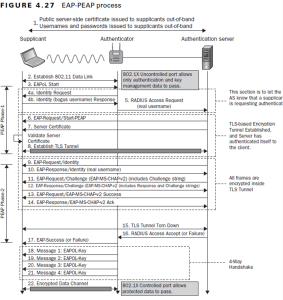
LEAP (Lightweight Extensible Authentication Protocol) and PEAP (Protected Extensible Authentication Protocol) are two authentication methods often used in Wi-Fi networks, however, they have different features and functionalities. While both authenticate users through a username and password combination, PEAP takes a more secure method by enclosing EAP (Extensible Authentication Protocol) behind an encrypted TLS tunnel, improving user credentials’ secrecy during authentication. This basic variation in authentication methods determines their applicability for different network settings and security needs.
Many variables are considered while evaluating the security protocols, such as simplicity of use and interoperability of LEAP and PEAP. With TLS encryption, PEAP provides better security than LEAP, which depends exclusively on username/password authentication. Furthermore, PEAP is considered easier to install because of its standardized protocol and extensive support across many operating systems and devices.
However, LEAP’s simplicity can benefit certain situations, notably in legacy settings where complex security protections may be impractical or unnecessary. Understanding these distinctions is critical for picking the best authentication mechanism for each network deployment’s security requirements and infrastructure limits.
Security Concerns With LEAP
LEAP, commonly used with RADIUS authentication in wireless devices such as Cisco Aironet, has lately come under fire owing to security flaws. Cisco expressed concerns about LEAP’s susceptibility to typical dictionary attacks, in which remote adversaries attempt to guess the shared secret password. This flaw stems from LEAP’s dependency on MS-CHAPv1 (Microsoft Challenge Handshake Authentication Protocol version 1), which sends usernames and encrypted passwords across the wireless network in a potentially interceptable way. Once intercepted, attackers can undertake offline dictionary attacks on the seized encrypted passwords until they locate a match, undermining network security. Despite its widespread use, this security issue highlights the significance of mitigating the risks of LEAP authentication.
In response to these security issues, Cisco recommends that its clients assess their security policies and consider establishing tighter password rules or switching to alternate authentication mechanisms like PEAP or EAP-TLS. PEAP, for example, creates a secure TLS tunnel between the WLAN user and the RADIUS server, reducing the possibility of dictionary attacks. Similarly, EAP-TLS uses pre-issued digital certificates for user authentication, which improves network security. While LEAP authentication may still be useful in certain situations, particularly when switching to alternative methods is not an option, organizations must carefully examine the risks and take adequate precautions to protect their Wi-Fi networks from possible attacks.
EAP-TLS and its Benefits
EAP-TLS (Extensible Authentication Protocol-Transport Layer Security) is a strong alternative to standard password-based authentication techniques, providing exceptional security and dependability for Wi-Fi networks. Unlike password-based techniques such as LEAP, EAP-TLS uses digital certificates for user authentication, avoiding the risks associated with passwords spreading over the network.
EAP-TLS uses cryptographic algorithms and reciprocal authentication between clients and servers to guarantee that only authorized users with valid certificates may access the network. This considerably lowers the danger of unauthorized access and security breaches. This improved security posture protects sensitive data and instills trust in users by ensuring the network’s integrity and protection against harmful activity.
Furthermore, EAP-TLS has various advantages that help improve the overall security of Wi-Fi networks. One significant advantage is its resilience to popular attacks like dictionary attacks and brute-force password guessing, as no credentials are communicated during authentication. Furthermore, EAP-TLS promotes reliable communication by building encrypted TLS tunnels between clients and servers, which protect data integrity and confidentiality during transmission.
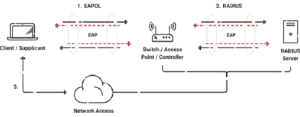
Leveraging RADIUS For Enhanced Security
RADIUS (Remote Authentication Dial-In User Service) servers improve Wi-Fi network security by offering centralized authentication, authorization, and accounting services. RADIUS servers function as gatekeepers, authenticating each network access request and ensuring that only authorized users and devices can access network resources.
SecureW2’s Cloud RADIUS solution modernizes RADIUS authentication and is particularly intended for passwordless authentication. It improves authentication security by using user and device certificates rather than susceptible passwords. This certificate-based method eliminates the complexities and hassles of password management and considerably lowers the risk of credential theft and unauthorized network access.
Furthermore, SecureW2’s Cloud RADIUS expands on standard RADIUS servers by seamlessly connecting with Identity Providers (IDPs) to do real-time identity lookups during authentication. This allows organizations to implement the most recent network regulations based on the data in their source of truth. Organizations receive extensive monitoring and segmentation capabilities by linking user and device identities to every connection, increasing network visibility and control.
Accessible EAP-TLS with SecureW2’s Managed PKI & Cloud RADIUS
Understanding the limits of outdated authentication protocols such as LEAP, which rely on credentials and are subject to dictionary attacks, emphasizes migrating to more secure alternatives. Organizations may successfully avoid these risks by using certificate-based authentication, such as EAP-TLS, and installing current RADIUS systems, such as SecureW2’s Cloud RADIUS.
SecureW2’s comprehensive offerings enable a seamless transition to passwordless authentication, removing the difficulties of password management while increasing security. SecureW2’s Managed PKI and Cloud RADIUS provide a strong framework for guaranteeing the integrity and confidentiality of Wi-Fi networks in today’s changing security landscape.
Contact us today to learn more about protecting your Wi-Fi network successfully.