In today’s world, VPNs (Virtual Private Networks) are very important for individuals and small and large-scale business owners. However, utilizing a VPN can be tricky due to some common difficulties in authentication.
Extensible Authentication Protocol (EAP) helps to offer secure network connections to different types of devices. The authentication process happens by using digital certificates to ensure the validity of the user and the VPN server. The mutual authentication process will help ensure that only users with legal authorization can access the VPN to mitigate the risk of unauthorized access and data breach issues.
This article will explain the authentication process for VPN and the Extensible Authentication Protocol-Transport Layer Security (EAP-TLS).
How Does EAP-TLS Authentication Work with VPNs?
EAP-TLS Authentication provides Certificate-Based Authentication, which is the gold standard of authentication. The authentication process runs with the help of three parties: the Supplicant (on the User’s device), the Authenticator (Switches or Controller), and often an authentication server such as a RADIUS server. Some VPNs, however, support certificate-based authentication but not necessarily RADIUS-backed authentication.
EAP-TLS Authentication can work with some VPNs by offering a secure network connection through certificates and Multi-Factor Authentication (MFA). Multi-factor authentication provides a fast authentication method that incorporates more than one form of authentication, such as certificates, passwords, one-time tokens, or even biometrics in some cases. VPNs like Palo Alto, SonicWall, Fortinet, Meraki AnyConnect, and Open VPN support certificates without RADIUS Authentication by integrating with our Certificate Authority. VPNs like NetMotion, Azure, StrongSwan, and WatchGuard don’t support Certificate-Based Authentication (EAP-TLS).
Does EAP-TLS authentication use RADIUS?
Yes. EAP-TLS authentication depends on RADIUS (Remote Authentication Dial-In User Service) as the backend authentication server. The RADIUS Server allows the client to request access to a network resource by validating the client’s certificates. Additionally, EAP-TLS ensures secure authentication by enabling mutual authentication between the client and server using digital certificates. In other words, both the client and RADIUS server verify each other at the time of authentication, which is precisely what makes EAP-TLS so ironclad.
Why Should You Implement EAP-TLS with VPN?
VPN security can be enhanced by allowing network access to valid users and devices by implementing digital certificates and EAP-TLS authentication. If you don’t use robust authentication methods like EAP-TLS and digital certificates, your VPN connections could be vulnerable to unauthorized access and other security risks like the following:
Authentication Bypass
Privilege Escalation
Command Injection
VPN hijacking
Man-in-the-Middle attacks
Malware Infection
DNS leak
Split tunneling.
What is the key length of EAP-TLS?
The standard key length of EAP-TLS authentication is 128 bits.
VPN & EAP-TLS Considerations for Different Operating Systems
Windows 10/11 EAP-TLS configuration
Windows 10/11 EAP-TLS configuration can help create a new wireless network connection that uses EAP-TLS Authentication. In Windows 10/11, select Control Panel > Network and Sharing Center. Then, manually set the latest network connection to connect to a wireless network. Later, type the Network name and set the Security type to WPA2-Enterprise network. Set the Encryption type to AES.
II.) After it’s created, you can change the wireless connection by selecting Change Connection Settings.
Windows VPN General authentication method
Windows VPN General has different VPN authentication methods, such as password-based, certificate-based, token-based, and biometric authentication. It allows you to select the most appropriate method by analyzing these options based on your organization’s unique requirements.
VPN Authentication Information On Mac Devices
The VPN Authentication information on a Mac device can be received through the prompt that asks you to enter the Mac password. The pop-up will reappear on the devices if you enter the password and click OK or Cancel. The below steps can solve the VPN password issue.
- On your Mac device, Open System Preference, then go to Network.
- You can notice the service associated with VPNs by clicking on it.
- At the bottom, click the Minus button to delete the related interface.
- It’s also necessary to restart your computer.
How to Configure EAP-TLS Authentication for VPNs
Prerequisites:
To set up EAP-TLS authentication for VPN, you’ll need access to the following:
- A Public Key Infrastructure (PKI) for managing and configuring digital certificates.
- A VPN solution that supports certificate-based authentication.
- An auto certificate enrollment solution for easy distribution of certificates to end users.
Overview:
- As PKI is the base for configuring EAP-TLS for VPN authentication and it’s tough to manage a PKI, one can depend heavily on PKI-as-a-Service providers like SecureW2. The following configuration guide assumes you are using the SecureW2 managed PKI and RADIUS services.
- Create a new Network Profile by using Getting Started option and having EAP authentication method as ‘EAP-TLS.
- Download the respective Root and Intermediate CAs from PKI -> Certificate Authorities section.
- Upload the downloaded CAs to your VPN server.
- Now you’ll need to distribute the end-user certificates for your users to use certs to authenticate into the VPN service.
a.) If you have an MDM you can easily configure them with SecureW2 so that all your managed devices get the certificates.
b.) For BYOD SecureW2 has JoinNow MultiOS through which users can run a dissolvable client to get enrolled to a certificate. - Now end-users can use their certificates to authenticate to their VPN service.
- Additionally, if you have a RADIUS in place or need one for compliance, you could additionally direct the authentication requests to RADIUS before reaching the VPN server. SecureW2 has a world class Cloud-RADIUS solution which can be used.
Configuration Steps to use EAP-TLS Authentication for a VPN:
SecureW2 Managed PKI is a turnkey service that offers smooth certificate enrollment through the generated root and intermediate certificate authority. The admin can simply establish certificate auto-enrollment for every device. The certificates are issued through our PKI service to provide secure and passwordless authentication (Certificate-based authentication). The Certificates can be issued and installed on the user device after enrollment and can be used for VPN Authentication.
Creating a Network Profile:
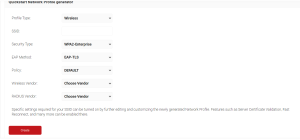
- Go to Device Onboarding> Getting Started in the Management Portal.
- The Quickstart Network Profile Generator page will appear on the screen.
- Enter the SSID Name, select the Security Type as WPA-2 Enterprise, EAP Method as EAP-TLS, Wireless Vendor, RADIUS Vendor relevant to your profile.
- Then click Save.

Create a New Intermediate Certificate Authority:
The following steps create and download a new Intermediate Certificate Authority.
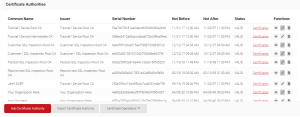
- Go to PKI> Certificate Authorities in the JoinNow Management Portal.
- Click Add Certificate Authority. Select the relevant CA from General Certificate Authority. drop-down and Intermediate CA from Type Drop-Down list.
- You have to select Default Root CA from the Certificate Authority.
- Then you have to enter the Common Name and select the Key size and Signature Algorithm, and Validatity time period.
- Click Save.
- Then you can download your New Intermediate CA from the Certificate Authority.
Once this process is over, you can distribute the user certificates to the clients that will be authenticating to your VPN of choice. Certificate-Based Authentication for VPN is applicable for both MDM and BYOD/unmanaged devices, although the certificate distribution process varies for them.
For MDMs, the SecureW2 platform utilizes gateway APIs that integrate with all major MDM vendors to issue certificates automatically through the Simple Certificate Enrollment Protocol (SCEP). On the other hand, for unmanaged devices, our platform provides JoinNow MultiOS, which is a self-service and dissolvable application that allows end users to quickly configure their own devices for certificate-based authentication.
Integrating RADIUS Server to authenticate with VPN:
Certificates need to be authenticated by something, and for that purpose, we recommend our Cloud RADIUS as an authentication server. However, in order for this to work, you’ll need to integrate Cloud RADIUS with your VPN.
Through your access point, you connect to the VPN for the configuration. Once your VPN is connected to your office access point, you can experience the security of RADIUS Authentication for network access.
Follow these steps to integrate Cloud RADIUS with your VPN:
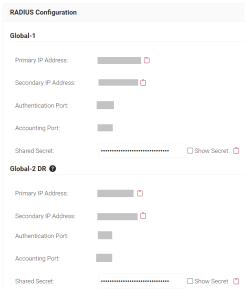
- Navigate to the RADIUS>RADIUS Configuration.
- You need to copy the Primary and Secondary IP Address, Authentication Port, and Secret Shared for the subscribed region and paste them in the respective VPN server.
Transform Your VPN Authentication with SecureW2’s Cloud-Based & Passwordless Authentication.
SecureW2 provides advanced technology to safeguard your data and offers a secure connection for your devices with our simple passwordless authentication platform. We provide you everything you need to apply passwordless authentication to VPNs that support it, including a managed, cloud-based PKI and Cloud RADIUS server.
Plus, our onboarding process is designed to offer efficient and user-friendly service and ensure a seamless transition for administrators and end-users. We offer onboarding for both managed and unmanaged devices/BYODs. Our self-service onboarding platform for unmanaged devices is fast, simple, and can be used at all technical literacy levels.
We have experience helping hundreds of organizations move to passwordless VPN authentication. Contact us today to learn more and see how it works.