The standards used to protect wireless/Wi-Fi networks have evolved over the years to keep up with emerging threats and protect sensitive data. WPA2 and WPA3 are some of the more recent additions to wireless network security settings. Distinguishing between WPA2 and WPA3 is pivotal for maintaining robust security standards.
This article offers a comprehensive analysis aimed at an expert-level audience, detailing the technical nuances, advantages, and potential downsides of transitioning from WPA2 to WPA3. It delves into key differences in encryption algorithms, attack resistance, public network security, and the implications of these advancements for the future-proofing of wireless networks against contemporary cyber threats.
What is Wi-Fi Protected Access (WPA)?
Wi-Fi Protected Access (WPA) is a security protocol and security certification program developed by the Wi-Fi Alliance to secure wireless computer networks. Introduced as an interim solution to the inherent weaknesses in WEP (Wired Equivalent Privacy), WPA was designed to provide a higher level of data protection and network access control. It incorporates Temporal Key Integrity Protocol (TKIP) for dynamic encryption key generation and Message Integrity Check (MIC) for avoiding tampering. The evolution from WEP to WPA was pivotal in enhancing wireless network security by addressing vulnerabilities and implementing a more robust method of encrypting data. Despite WPA’s improvements, it still retained vulnerabilities, leading to the development of WPA2 and WPA3, with each version introducing stronger security measures like AES (Advanced Encryption Standard) and SAE (Simultaneous Authentication of Equals).
What is WPA2?
WPA2 is the successor to the original WPA standard, introducing mandatory support for AES alongside optional use of TKIP. Officially ratified in 2004, WPA2 became the de facto security protocol for all Wi-Fi networks due to its enhanced security features. Notably, WPA2 deploys the CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol) as the default encryption protocol, which offers a significant security advantage over WPA’s TKIP, making it resistant to numerous attack vectors that plagued its predecessor.
This shift marked a pivotal transition in wireless security protocols, providing stronger data protection via AES’s more complex encryption algorithms and longer encryption keys. WPA2 is available in two configurations: Personal (Pre-shared key, PSK) and Enterprise (802.1X authentication), catering to different network environments and security requirements. However, vulnerabilities like the Key Reinstallation Attack (KRACK) have exposed limitations within WPA2, prompting the development and adoption of WPA3 for even higher wireless network security standards.
What is WPA3?
WPA3 represents the latest advancement in wireless security protocols, officially introduced by the Wi-Fi Alliance in 2018. Building upon the foundation of WPA2, WPA3 introduces crucial security enhancements and counters vulnerabilities that persisted in its precursor. A key highlight of WPA3 is the implementation of the SAE protocol, which replaces the Pre-shared Key (PSK) mechanism of WPA2, offering a more secure initial key exchange process and significantly improving protection against offline dictionary attacks. Additionally, WPA3 enhances data protection through the incorporation of 192-bit encryption in its Enterprise mode, adhering to the Commercial National Security Algorithm (CNSA) suite, which mandates higher cryptographic strength.
WPA3 introduces features like Forward Secrecy and Individualized Data Encryption, providing robust protections against eavesdropping and ensuring backward security. These advancements mark a significant step forward in securing modern wi-fi networks against evolving cyber threats, offering both enhanced encryption capabilities and improved user security practices in personal and enterprise environments.
What are the Key Differences Between WPA3 and WPA2?
When dissecting WPA3 and WPA2, several key differences emerge:

The Role of Protocols in Wireless Network Security
Protocols serve as the architectural backbone in enhancing wireless network security, establishing a framework for data encryption, integrity checks, and secure authentication mechanisms. These set of rules and standards dictate how data is securely transmitted across wi-fi networks, ensuring confidentiality and protection against unauthorized access.
WPA2 Protocols & Security
- Advanced Encryption Standard (AES): A powerful encryption algorithm used for encrypting data transmitted over the network, significantly more secure than the TKIP used in WPA.
- Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP): Replaces TKIP in WPA2 as the encryption protocol, providing strong data protection and integrity by applying AES in a more secure mode.
- 802.1X Authentication: Offers a robust framework for authenticating and managing users on enterprise networks, using an authentication server for verifying user credentials.
WPA3 Protocols & Security
- Simultaneous Authentication of Equals (SAE): Introduces a more secure initial key exchange process than WPA2’s PSK, significantly enhancing protection against offline dictionary attacks.
- 192-bit Encryption Standard: In WPA3-Enterprise mode, provides a higher level of security conforming to the CNSA suite, safeguarding sensitive government and financial data.
- Forward Secrecy: Ensures that the current session keys cannot be used to decrypt past sessions, even if they are compromised, providing an additional layer of security.
How to Configure a Network for WPA2
Configuring a network for WPA2 security necessitates a series of precise steps aimed at optimizing wireless network protection. Following these guidelines ensures that the network utilizes WPA2’s security capabilities effectively:
- Access Router Settings: Log in to your wireless router’s administrative interface using its IP address. This typically involves entering the router’s IP into a web browser’s address bar.
- Select Security Options: Navigate to the wireless security settings section. Here, you will find options to choose the type of wireless security protocol you wish to implement.
- Choose WPA2: From the available security protocols, select WPA2-PSK (AES) for personal networks or WPA2-Enterprise (AES) for networks that require user authentication through a RADIUS server.
- Set a Strong Password: For WPA2-PSK, input a robust, complex password that includes a mix of letters, numbers, and symbols to enhance security.
- Save and Apply Settings: After configuring the network for WPA2, save the settings and apply them. It may require the router to reboot for changes to take effect.
- Connect Devices: Ensure devices connecting to the network support WPA2 and reconnect them using the new security settings.
This configuration secures the wireless network with WPA2, leveraging AES encryption to protect data transmission against unauthorized access and eavesdropping.
WPA2-Enterprise can provide some of the robust Wi-Fi security available today when combined with passwordless authentication such as digital certificates in place of passwords. Of course, this requires additional infrastructural elements such as a Public Key Infrastructure. You can learn more about configuring a passwordless 802.1X network in our guide for WPA2-Enterprise certificate-based authentication.
How to Set up a WPA3-Supported Network
Setting up a network to take full advantage of WPA3’s enhanced security features requires attention to compatibility and configuration details. Implementing WPA3 involves the following steps:
- Verify Device Compatibility: Ensure both the wireless access point (router) and client devices support WPA3. This may necessitate firmware updates or hardware upgrades for older devices.
- Access Router Configuration: Log into the router’s admin interface, typically through a web browser using the router’s IP address.
- Select WPA3 Security: In the router’s wireless settings, locate the security options and select WPA3-Personal or WPA3-Enterprise, depending on your network requirements.
- Configure Encryption Settings: For WPA3-Enterprise, additional configuration for the RADIUS server may be required. Ensure encryption settings are aligned with WPA3 standards, specifically selecting the 192-bit encryption for enterprise setups.
- Set a Robust Password: For WPA3-Personal, create a strong, complex password to maximize the protocol’s resistance to brute-force attacks.
- Save and Implement Changes: Apply and save the new settings. The router may need to reboot to activate WPA3 security enhancements.
- Reconnect Devices: Reconnect client devices to the network, ensuring they’re configured for WPA3 security. This may involve selecting the network afresh and entering the new password.
Advantages of WPA3 Over WPA2
WPA3 introduces several enhancements over WPA2, fortifying wireless network security against contemporary threats. Highlighting six key advantages:
Enhanced Encryption
WPA3 employs SAE, a modern key establishment protocol, offering stronger protection than WPA2’s PSK approach. It also introduces 192-bit encryption in enterprise mode, adhering to the CNSA suite for higher security standards.
Improved Attack Resistance
The SAE mechanism significantly mitigates risks associated with offline dictionary attacks, a vulnerability in WPA2, by necessitating interaction with the network for each password guess attempt.
Forward Secrecy
Unlike WPA2, WPA3 supports forward secrecy, ensuring that a compromise of current session keys does not jeopardize the confidentiality of past transmissions.
Robust Public Network Security
WPA3 enhances user privacy on open networks through individualized data encryption, a feature absent in WPA2, protecting users from data eavesdropping in public spaces.
Protection Against Brute-Force Attacks
WPA3’s design inherently defends against brute-force attacks by making such attempts more challenging and resource-intensive.
Simplified Device Connection
WPA3 includes the Easy Connect feature, which simplifies the process of connecting devices to the network, especially for devices with limited or no display, enhancing usability without compromising security.
Potential Downsides of WPA3
Despite the robust security enhancements WPA3 brings to the table, it is not without its challenges and limitations, especially during the transition phase from WPA2. Notable disadvantages include:
- Compatibility Issues: Older hardware may not support WPA3, necessitating firmware updates or, in many cases, complete hardware upgrades to maintain network security standards, potentially incurring significant costs.
- Deployment Complexity: Implementing WPA3, especially in enterprise environments, requires a nuanced understanding of its new security features. The transition can be complex, involving updates to network infrastructure and devices to ensure compatibility and optimal security.
- Adoption Rate: As a relatively new standard, WPA3’s adoption is gradual. This slow uptake means mixed-network scenarios are common, where devices supporting different WPA standards must coexist, potentially complicating network security management and reducing the overall security posture due to fallbacks to WPA2 in certain scenarios.
Enhancing Wireless Network Security with SecureW2
SecureW2 offers robust solutions designed to tackle some of the inherent challenges faced by organizations transitioning to more secure Wi-Fi standards, including WPA2-Enterprise. Our suite of tools simplifies the deployment and management of a more secure, passwordless authentication environment through its managed Public Key Infrastructure (PKI) and RADIUS server capabilities.
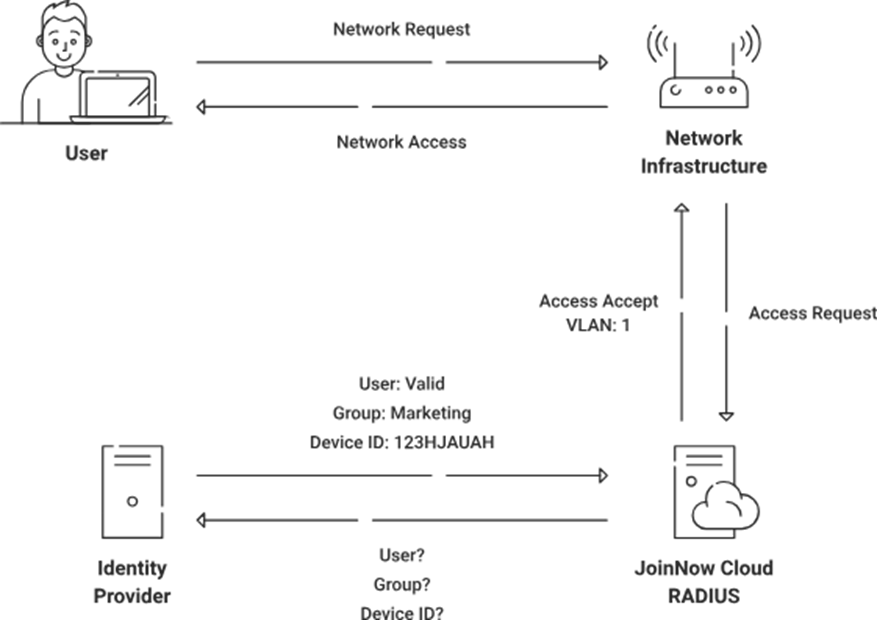
Even if you’re not in a position to implement WPA3, we can help enhance the security of your wireless networks through certificate-based Wi-Fi authentication. We provide everything you need to go passwordless, including a cloud PKI to manage the entire certificate lifecycle and a RADIUS service to authenticate those certificates. Leveraging SecureW2’s capabilities can help your organization adopt a more holistic approach to securing wireless networks, ensuring adherence to current and future security standards. Contact us today and see how SecureW2 can strengthen your defense against Wi-Fi vulnerabilities.