Continuous Access Evaluation (CAE) is an essential security feature in Azure Active Directory (Azure AD) that constantly monitors and evaluates user access to resources. Through CAE, Azure provides a proactive approach to maintaining a secure environment and safeguarding sensitive data from potential threats.
This article will detail how to configure Azure AD Continuous Access Evaluation for RADIUS, the relationship between CAE and RADIUS, the role of Access Tokens, and the implementation of Strictly Enforced Location Policies with Continuous Access Evaluation.
Continuous Access Evaluation in Azure Active Directory (AD)
Azure Active Directory (Azure AD) is Microsoft’s robust cloud-based identity and access management service (IDaaS). It facilitates seamless access to multiple users, allowing them to use applications on-premises, in the cloud, and on mobile devices. With Azure AD, businesses can secure their organization by ensuring the right people access the correct information.
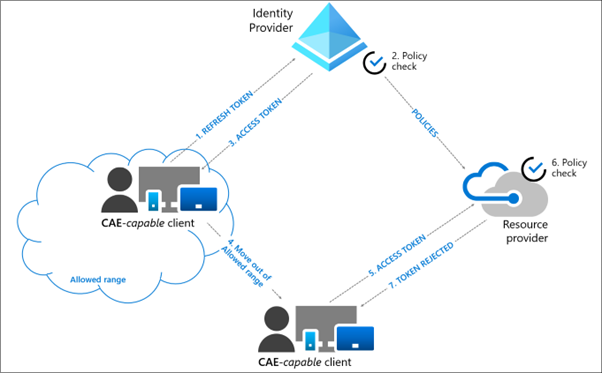
The Azure Continuous Access Evaluation is a robust security feature that constantly evaluates user access to Azure AD services. CAE involves two scenarios: critical event evaluation (when a user should lose access) and conditional access policy evaluation (when a user should lose access to a resource based on an administrator-defined policy).
By continuously assessing user access in harmony with the dynamic nature of cloud services, Azure CAE significantly reduces attack surfaces and increases the organization’s ability to respond to potentially harmful changes or activities.
In Azure, CAE is enabled at the tenant level and impacts various workload identities like user accounts, service principals, and managed identities. Once enabled, CAE constantly monitors and responds to specific security incidents. These include a user’s account deletion or disablement, forced password reset, admin-enforced user sign-outs, and changes in a user’s role or directory role membership. In the event of such changes, CAE forces the active session tokens to expire, thus blocking access until the user successfully re-authenticates.
Continuous Access Evaluation and RADIUS
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service. As an AAA server, RADIUS remotely authenticates users through unique credentials and authorizes their access based on predefined policies. Furthermore, RADIUS accounts for users’ activities during their connection, providing a detailed report of their interactions with the network resources.
Source: microsoft.com
Interaction Between Continuous Access Evaluation and RADIUS
CAE and RADIUS interact closely in managing access controls and maintaining the security of network resources. As RADIUS becomes a resource provider, CAE leverages it to evaluate user access to the network continuously. Once a user is authenticated by RADIUS and given an access token, CAE comes into play and monitors the user’s session. It checks for any change in the user’s status or any critical event that may threaten security, such as password changes, suspicious IP addresses, or changes in group membership.
Why is it Important to Implement Continuous Access Evaluation with RADIUS?
The strategic combination of RADIUS and CAE can significantly enhance an organization’s security posture. RADIUS provides a sturdy foundation for user authentication and authorization, while CAE adds an extra layer of security by monitoring the authenticated sessions continuously. This collaborative approach allows for immediate reaction to security-critical events, thereby minimizing the window of opportunity for malicious actors. Consequently, if a user’s access should be revoked following a critical event, the system instantly blocks that user’s access, thus maximizing the security of network resources.
Configuring Continuous Access Evaluation for RADIUS in Azure AD
Before setting up CAE in Azure AD, it’s important to note that the feature is not enabled by default. It is also essential to note that not all cloud apps support CAE, and you may need to review the apps’ CAE support before proceeding. To configure CAE, you need to follow these steps:
- First, navigate to the Azure portal and select Azure Active Directory.
- Click on ‘Security,’ then ‘Conditional Access.’
- Create a new Conditional Access policy.
- Configure the policy according to your organization’s needs. This might include setting conditions such as user risk, location, and device state.
- Enable the policy you’ve created.
Checking if Continuous Access Evaluation is Enabled by Default
To check if CAE is enabled by default, navigate to the Conditional Access page in the Azure portal. There, you’ll find information regarding the status of CAE in your Azure Active Directory settings.
How to Turn Off Continuous Access Evaluation in Azure AD
If you wish to disable CAE, navigate to the Conditional Access policies section in Azure AD. Choose the policy where CAE is enabled, then click ‘Delete.’ Remember, turning off CAE may expose your Azure AD to potential security threats.
What is an Access Token in Continuous Access Evaluation?
An access token is a crucial security asset that validates user identities during session interactions with an identity provider like Azure AD. It is a string representing authorization granted to the user by the identity provider. The token encapsulates critical information about the user, including their identity, roles, and permissions, and is precisely what the user uses to access resources.
What is the Role and Functionality of Access Tokens in CAE?
In CAE, access tokens serve as proof of granted user access. During user sessions, CAE continuously monitors these tokens. If a critical event that could compromise security occurs, the assigned user’s access token is immediately invalidated. The user must then re-authenticate to regain a valid access token and, thus, access to the resources.
How to Safeguard a User Account with Access Tokens
Access tokens play an integral role in fortifying the security barriers of user accounts. By constantly re-evaluating the validity of an access token, CAE ensures that only authenticated users have the required access. If there is any hint of compromise based on the critical events monitored, the involved user’s access is instantly blocked, minimizing the risk of unauthorized access. Thus, CAE creates a secure fortress around user accounts alongside the judicious use of access tokens.
Conditional Access Policies in Continuous Access Evaluation
Conditional Access Policies are customizable rules in Azure AD that enforce certain conditions before granting user access. They can be based on user roles, location, device status, and risk level. CAE integrates with Conditional Access Policies to monitor and evaluate user access continuously.
If a user doesn’t meet the conditions of the Conditional Access policy, their access is automatically revoked, further bolstering your security. Conditional Access Policies provide a dynamic and context-aware way of managing user access. When integrated with CAE, these policies allow organizations to respond swiftly to any critical event that may pose a security risk.
Context-aware or Risk-Based Authentication
Context-aware authentication is a security measure that considers the context of a user’s access request, such as physical location, IP address, and device state. This form of authentication provides a more robust security approach than conventional methods. Context-aware authentication plays a critical role in continuous access evaluation, helping to validate users’ authenticity continuously. This ensures only authorized users can access data and resources, enhancing the security framework.
By granting certificates for Context-Aware Authentication, you provide an additional layer of security. Certificates act as ‘digital passports,’ verifying the identities of users and devices accessing your network.
Strictly Enforced Location Policies with Continuous Access Evaluation
Strictly Enforced Location Policies dictate user access based on the user’s geographical location. They restrict access to sensitive resources from IP ranges or locations considered high-risk.
Enforcing location-based policies with CAE allows you more control over who accesses your network and from where. This can significantly enhance your security posture and help prevent unauthorized access.
How to Configure Strictly Enforced Location Policies with Continuous Access Evaluation
To configure location-based policies with CAE;
- Navigate to the Azure portal and select Azure Active Directory.
- Click on ‘Security,’ then ‘Conditional Access.’
- Create a new Conditional Access policy.
- In the ‘Conditions’ section, choose ‘Locations.’
- Select ‘Configure’ and then ‘Yes.’
- Specify the locations you want the policy to apply.
- Define your desired access controls and save the policy.
Dynamic Authentication on Cloud RADIUS
Dynamic Authentication on Cloud RADIUS is a feature that ensures only authenticated users gain access to network resources. It revolves around the principle of evaluating the credentials of a user dynamically.
Cloud RADIUS vs Azure Continuous Access Evaluation
Both Cloud RADIUS and Azure CAE aim to secure user access to resources. However, they differ fundamentally. Cloud RADIUS focuses on dynamically validating user credentials, while Azure CAE emphasizes constant monitoring and real-time response to critical events.
While both systems have their merits, they also come with trade-offs. Cloud RADIUS offers multifactor authentication but lacks the continuous monitoring attribute of Azure CAE. Conversely, Azure CAE provides continuous monitoring and immediately blocks access following a critical event, but it might not support all cloud applications.
SecureW2’s Modern Passwordless RADIUS Designed for Cloud Identities
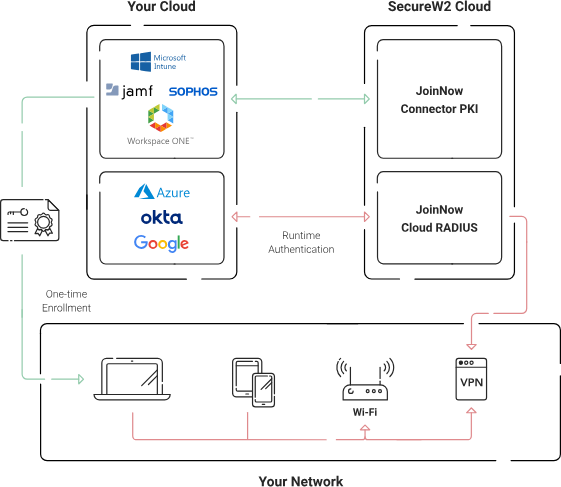
SecureW2 provides a modern passwordless RADIUS server designed specifically for cloud identities that integrate seamlessly with Azure AD, enhancing its capabilities with its unique features.
SecureW2’s Cloud RADIUS communicates directly with Azure AD, eliminating the need for a separate directory sync tool. This enables you to leverage your existing Azure AD users and groups without replicating. Furthermore, the Cloud RADIUS server can authenticate and enforce policy based on any Azure AD user or group attribute, giving you granular control over your network access policies.
In addition to its compatibility with Azure AD, SecureW2’s Cloud RADIUS offers additional security measures such as PKI authentication, which is more secure than traditional username/password authentication, and Dynamic Cloud RADIUS, which supports dynamic policies and eliminates the need for static VLANs.
With its robust capabilities and innovative features, SecureW2’s modern passwordless RADIUS provides a flexible, secure, and efficient solution for managing access to network resources, complementing Azure AD’s Continuous Access Evaluation to give you a holistic solution for your cybersecurity needs. Check out our offerings and prices today.