Cryptography is a cornerstone of securing information systems. It involves encoding data to ensure only authorized parties can access it. By converting data into an unreadable format, cryptography protects sensitive data from being exposed in the event of security breaches.
The primary objectives of cryptography include confidentiality, integrity, and authentication. These pillars help organizations to protect their critical systems and maintain the trust of their users or clients. However, cryptographic strategies need to evolve to keep up with emerging cyber threats, and that is where the concept of cryptographic agility comes in. This article explains what crypto agility means and why it is important for your organization’s security posture.
What is Cryptographic Agility?
Cryptographic agility, often shortened as crypto-agility, is the capacity of an information system to switch out cryptographic primitives and algorithms swiftly and efficiently without causing system disruption. This capability is crucial for maintaining systems and data security in a dynamic threat environment. Crypto agility is essential for organizations as it allows them to be flexible and adaptable to emerging threats, vulnerabilities, and regulatory requirements. It also plays a significant role in the incident response of security teams and contributes to an organization’s cyber resilience.
A crypto-agile system refers to its ability to change cryptographic algorithms and primitives quickly and efficiently when needed. This evolution could be due to new vulnerabilities discovered in the current cryptographic standards or advancements in quantum computing power.
Why is Cryptographic Agility Important?
Cryptographic agility provides flexibility in switching and updating cryptographic algorithms and standards, ensuring the security and confidentiality of data against emerging cyber threats and vulnerabilities. Cryptocurrency agility plays a pivotal role in maintaining cyber resilience by enabling a swift response to potential risks and keeping your systems compliant with industry regulations. It equips organizations to counter threats posed by quantum computing advances, thus playing an invaluable role in future-proofing cryptographic systems.
Crypto-agile systems help organizations with continuous compliance with industry standards, remaining prepared for unanticipated shifts in the encryption mechanisms and embracing and maintaining crypto agility for future-proofing security infrastructure.
Types of Cryptographic Algorithms
Cryptographic algorithms are integral in securing data and can be categorized into three main types:
Hash Functions
Hash functions, such as the secure hash algorithms (SHA) series, create a fixed-size output from any input data. They are commonly used in password storage and data integrity checks.
Symmetric
Symmetric encryption, like Advanced Encryption Standard (AES) or Triple Data Encryption Standard (3DES), uses the same key for encryption and decryption. It is faster and more efficient than asymmetric encryption but poses risks if the key is lost or stolen.
Asymmetric Algorithms
Asymmetric algorithms, such as the RSA algorithm, use different keys for encryption and decryption, enhancing security. They are primarily used in key exchange, digital signatures, and secure email services.
Why is Algorithm Agility Important in Cryptographic Agility?
Algorithm agility refers to the ability to use multiple cryptographic algorithms and switch between them as needed. It is the backbone of cryptographic agility as it increases the adaptability and security of systems to new threats and vulnerabilities.
Algorithm agility allows security teams to replace compromised or outdated cryptographic primitives swiftly and replace them with stronger, more secure alternatives. Using possible quantum cryptography systems ensures the system’s resilience against threat actors.
Conceptual Framework of Cryptographic Agility
The conceptual framework of crypto agility emphasizes flexibility and adaptability, robust key management, prioritizing sensitive data, and maintaining compliance with regulatory standards. It recognizes that as no single algorithm is flawless, cryptographic systems should be capable of supporting multiple algorithms, thereby ensuring continuous protection and the ability to respond efficiently to potential threats. It emphasizes that transitioning to different algorithms should be performed without disrupting the system’s infrastructure. Regular audits are crucial for identifying latent weaknesses and suggesting necessary improvements while maintaining compliance with industry standards to guide an organization’s cryptographic best practices.
What is a Crypto-Agile Strategy?
Crypto-Agility Strategy is a comprehensive plan that organizations adopt to prepare for the advent of quantum computers and post-quantum cryptographic algorithms. It involves using various encryption methods and continuously updating and auditing the security infrastructure.
How to Implement a Crypto-Agile Strategy in Your Organization
Implementing a crypto-agile strategy in an organization involves a systematic approach toward evaluating and updating current cryptographic practices. Organizations should start by conducting an in-depth evaluation of their cryptographic practices and identifying potential vulnerabilities. They then need to research suitable new cryptographic standards, keeping abreast with the latest technological advancements and industry recommendations. This helps formulate a concrete plan for transitioning from current practices to more secure and efficient cryptographic algorithms.
However, implementing a crypto-agile strategy isn’t just about plugging vulnerabilities and upgrading to newer standards—it also involves meticulous planning to ensure a smooth transition that doesn’t disrupt the system’s performance or functionality.
Quantum Computing and Cryptographic Agility
Quantum computing is a looming threat to cryptography. The inherent power of quantum computers allows them to break algorithms that today’s computers cannot, potentially exposing sensitive data. This makes crypto agility critical in staying ahead of the curve and preparing for quantum threats. The mere existence of quantum computing may render many current cryptographic standards obsolete, making crypto agility essential in maintaining security.
Cryptographic Agility and Crypto Assets
Crypto agility extends its importance to crypto assets as well. Crypto assets rely greatly on strong cryptographic algorithms for their security and integrity. Investors and exchanges handle significant amounts of sensitive data that must be protected from threats.
However, the looming presence of quantum computing could potentially render current cryptographic standards obsolete. This is where cryptographic agility comes into play. Being crypto-agile allows such organizations the flexibility to swiftly switch out cryptographic algorithms as needed, ensuring the continued security of crypto assets.
How Crypto Agility Affects PKI Management
Public Key Infrastructure (PKI) management is integral to maintaining the security and integrity of cryptographic systems. The ability to change cryptographic algorithms in PKI systems is essential to meeting security needs. Crypto agility and PKI management are linked because the ability to switch algorithms is key to maintaining the security of PKI systems. As threats evolve, so must the cryptographic principles protecting our information.
Enhancing PKI Management with Crypto Agility
Crypto agility augments the robustness of PKI management by permitting a quick response to potential threats via efficient and effective algorithm switches, hence maintaining the integrity and security of PKI systems.
Best Practices for Crypto Agility Implementation
Some best practices for implementing a crypto-agile strategy in your organization include:
Adaptability
Organizations need to be adaptable. This adaptability includes being ready to change cryptographic algorithms as advancements occur or new vulnerabilities are discovered.
Multiple Algorithm support
As no single algorithm is perfect, having multiple algorithm support is crucial. If one algorithm fails, another can be used as a backup, ensuring continuous protection. For this reason, managed PKIs like the SecureW2 PKI support multiple algorithms simultaneously, including SHA and RSA.
Plan for Algorithm Transition
Transitioning to different algorithms should be smooth and without disruption. This requires proper planning and considering the impact of the switch on the existing system’s infrastructure.
Regular Audit
Regular audits are needed to ensure the continuous effectiveness of cryptographic practices. Audits can identify potential security weaknesses and pave the way for necessary improvements.
Strong Key Management
Possessing strong key management practices is vital. This includes generating strong keys, storing them securely, and deleting them when no longer needed. SecureW2 practices secure key management to ensure the certificates generated by our private PKI are protected from compromise.
Prioritize Sensitive Data
Sensitive data should always be prioritized for maximum protection. The encryption for such data should be strong and resistant to potential threats.
Regulatory Compliance
Following regulatory standards can guide an organization’s cryptographic best practices. Compliance ensures that an organization’s cryptographic practices meet the necessary specifications.
Stay On Top of Cryptographic Advances with a Managed PKI
Harnessing the strength of crypto agility can be challenging for organizations of varying scales. SecureW2 offers a comprehensive managed PKI solution that simplifies deploying, managing, and securing digital certificates.
SecureW2’s Managed Cloud PKI as a Service is designed with an underlying foundation of cryptographic agility. This adaptive architecture allows organizations to adjust and update their cryptographic standards swiftly and smoothly as the threat landscape evolves. Our PKI solution ensures that organizations are not left vulnerable due to outdated or compromised cryptographic algorithms.
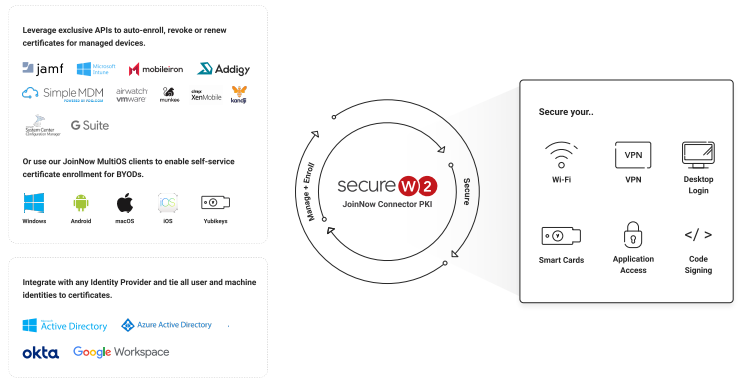
SecureW2’s Managed Cloud PKI service embraces crypto agility, preparing for future threats by supporting multiple encryption algorithms. Furthermore, our PKI simplifies safeguarding all your endpoints with digital certificates by streamlining certificate management. SecureW2 allows organizations to stay ahead of the curve and be truly crypto-agile through affordable and custom options for all organizations. See our pricing.



