As we increasingly rely on the internet for both personal and professional activities, understanding the potential threats to our online security becomes essential. A prevalent and significant risk is DNS Poisoning, a cyber attack that manipulates and exploits vulnerabilities in the Domain Name System (DNS).
This article delves into the workings of DNS Poisoning, illustrating its different aspects, impact on organizations, and common attack methods. Additionally, it offers insight into effective strategies for preventing such attacks, ensuring effective cyber security strategies in organizations.
What is DNS and How Does it Work?
The Domain Name System serves as the Internet’s phone book. While we interact with the Internet using human-friendly domain names such as (www.example.com), behind the scenes, these names are converted into machine-friendly IP addresses. This is achieved through a DNS lookup process where a DNS server, functioning like an automated directory assistance service, interprets the domain names into their corresponding IP addresses. This conversion is critical for loading Internet resources. When you type a URL into your browser, the DNS system translates it into the specific IP address where the website is hosted, allowing your browser to access and load the requested webpage.
The Role of a DNS Server
A DNS server acts as a directory, maintaining a comprehensive database of public IP addresses and their associated domain names. When a domain name (URL) is entered into a web browser, it’s the DNS server’s job to find the correct IP address connected to that domain and return it to the browser. This system of translation is essential for any internet-based activity, allowing for easy navigation and load-up of online resources.
What are DNS Poisoning Attacks?
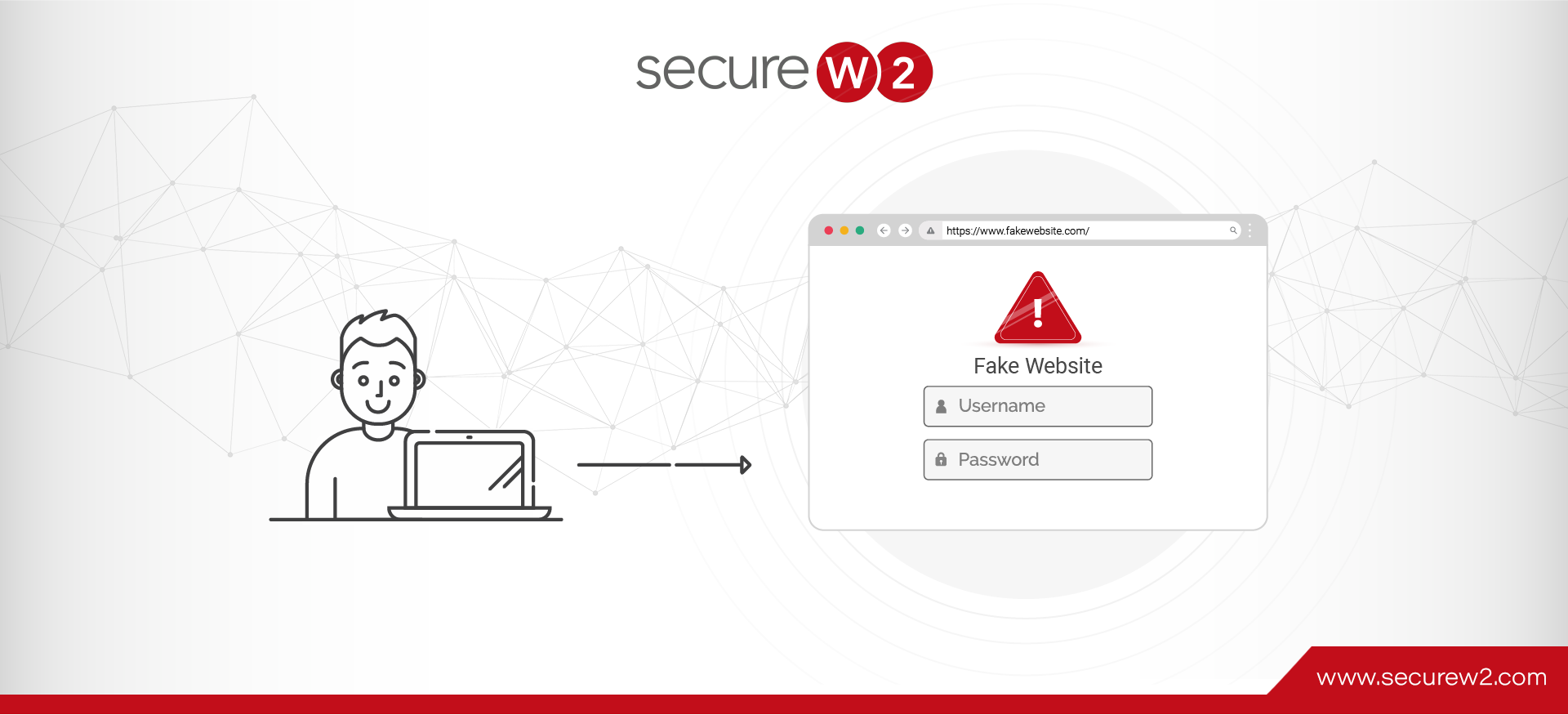
DNS poisoning attacks are a type of cyber attack that targets the inherent vulnerabilities of the DNS. Under this type of attack, a hacker manipulates the DNS server or DNS cache, injecting it with fraudulent address resolutions. As a result, when a user makes a DNS request for a specific website, the DNS resolver unknowingly redirects the request to a completely different IP address, often a malicious website set up by the hacker. The unsuspecting user, thinking they’re logging into a legitimate website, may then inadvertently provide personal information or login credentials, falling prey to data theft or malware installation.
DNS poisoning attacks are a serious threat in the arena of internet security, with the potential to disrupt operations and compromise data at both individual and organizational levels. Understanding how these attacks work allows for better strategies for mitigating risks and ensuring a safer browsing environment.
DNS poisoning vs DNS cache poisoning vs DNS spoofing
While DNS Poisoning, DNS cache poisoning, and DNS spoofing often get interchanged, they have subtle differences. DNS Poisoning is a broad term encompassing any attack that introduces incorrect IP addresses into the DNS. In DNS Cache Poisoning, a subset of DNS Poisoning, the attacker corrupts the DNS cache data specifically, leading to misdirected queries.
On the other hand, DNS Spoofing involves the attacker responding to a DNS request with false data, causing the server to forward traffic to an incorrect or malicious IP address, hence orchestrating a successful deception.
Components of DNS Poisoning Attacks
To understand how DNS poisoning works, we first need to delve into the functionalities of DNS resolvers and how DNS caching operates.
DNS Resolvers
At the heart of DNS operations lie DNS resolvers. These are devices or software applications that perform DNS lookup, i.e., they acquire the IP address corresponding to a domain name. Every time a user types in a web URL, it is the DNS resolver that facilitates the actual, machine-understandable IP address from the domain name.
DNS Caching
To expedite this process of address resolution, DNS resolvers rely upon a temporary database known as DNS cache. This cache stores the details of all recent and attempted website visits, reducing the DNS lookup time for frequently visited sites by fetching IP addresses directly from the cache instead of initiating a fresh lookup.
How Do DNS Poisoning Attacks Work?
Step 1: Initiating the Attack – Poisoning the DNS Cache
Here lies the crux of DNS poisoning attacks – the manipulation of the DNS cache. Using various methods, attackers trick the DNS resolver, substituting the authentic IP addresses in the cache with false ones. This alteration in a DNS cache is known as a DNS cache poisoning attack, a specific form of DNS poisoning.
Step 2: The Attack Unfolds – Redirecting to Malicious Sites
Post attack, when a user attempts to visit a website, the DNS resolver looks up the poisoned DNS cache and retrieves the wrong IP address. Consequently, the user is redirected to a malicious website controlled by the attacker instead of the intended site. This switch often goes unnoticed, and unsuspecting users, thinking they’re on the legitimate site, may input their sensitive data, providing the attacker with an opportunity for data theft or malware installation. In this way, a single successful DNS poisoning attack can impact multiple users who all share the same DNS cache.
Step 3: Perpetuating the Attack – Spreading Across DNS Servers
Since DNS caches regularly share information with other DNS servers to keep their data updated, a poisoned DNS cache can spread its corrupted data to other caches. This propagation of false DNS information across multiple domain name servers amplifies the impact of the attack, leading to a more widespread compromise of user data and network security.
DNS Spoofing Attack Methods
While DNS spoofing attacks can cause serious security concerns, having a grasp of them can help you anticipate, recognize, and thwart potential threats. Some of the common methods employed by attackers in DNS spoofing include:
Interception of DNS Requests
In this method, attackers intercept DNS queries in transit from the DNS resolver to the DNS server. By doing this, they gain the ability to return fake DNS responses. The manipulated DNS server then unknowingly directs unsuspecting users to malicious sites, facilitating potential data theft or malware installation.
DNS Server Overloading
In a technique akin to a Denial of Service (DoS) attack, attackers target vulnerable DNS servers, overloading them with multiple simultaneous DNS requests. The server, unable to handle the load, crashes, giving attackers an opportunity to poison the DNS cache with malicious IP addresses.
Exploiting Insecure DNS Configuration
If a DNS server is improperly configured or lacks robust security measures, attackers can exploit these weaknesses to perform DNS spoofing. Here, vigilance in maintaining updated and secure DNS configurations is essential to prevent DNS poisoning attacks.
Man-In-The-Middle Attack
Under this attack method, attackers intercept DNS queries in transit between the client and the server, manipulating the data so the client connects to the attacker’s server. By controlling the server to which the client connects, attackers can further their malicious agenda.
Pharming Attack
In a pharming attack, attackers manipulate a website’s host file or domain name system to redirect users to a fraudulent website, even when they’ve typed the correct address into their browser.
DNS Hijacking vs DNS Poisoning
While both DNS Hijacking and DNS Poisoning are malicious techniques used by hackers to divert internet traffic, they operate in different ways. We’ve seen that in DNS poisoning, the attacker introduces corrupt DNS data into the DNS resolver’s cache, causing the name server to return an incorrect IP address.
In DNS Hijacking, the attacker redirects queries to a different DNS server. It usually involves the alteration of the local host files or the manipulation of the router. The purpose of this attack is to lead users to fraudulent websites, where the attacker can steal sensitive data, such as usernames, passwords, and credit card information. For example, a user may think they are visiting their online banking website when, in fact, they are being redirected to a fake version of the site created by the hacker.
DNS Hijacking is more about taking control of the server to redirect traffic, while DNS Poisoning is about corrupting the data within the server to misdirect traffic. Both these attacks are threats to user privacy and data security.
How Do DNS Poisoning Attacks Impact Organizations?
DNS Poisoning attacks have severe implications for organizations. Significant data theft is a common fallout, as the attack can expose confidential customer information, intellectual property, or sensitive internal data. Organizations can also face reputational damage, leading to loss of customer trust and potential business. The subsequent financial implications can be debilitating. Moreover, the infiltration into the organization’s network poses a threat of escalated cyber attack severity. Recognizing the profound impact these attacks may have is vital in prioritizing cybersecurity measures, mitigating risks, and safeguarding the organization’s data and reputation.
Best Practices to Prevent DNS Poisoning Attacks
Recognizing the potential risk DNS poisoning poses to internet users and organizations alike, it is essential to employ the best practices to mitigate these threats. Here are some ways to strengthen your defenses:
Vigilant Monitoring of DNS Activity
Constant monitoring of DNS activity allows for the detection of any suspicious entries in real-time. Using DNS Spoofing detection tools can help spot potential security threats before they become a problem. If abnormal traffic patterns or unrecognizable DNS responses are detected, it could indicate a DNS poisoning attempt.
Regular Updating of DNS Software
Make it a habit to keep your DNS software and operating systems updated. With each update, software developers improve security measures and patch known vulnerabilities that attackers might exploit.
Operating Your Own DNS Server
Running your own DNS server allows for better control over DNS requests and responses, thereby reducing the risk of DNS poisoning attacks. Having your own servers essentially ensures that DNS requests aren’t sent to compromised external DNS servers.
Use Private DNS Servers
A private DNS server only allows DNS requests from recognized and trusted sources, minimizing exposure to potential threats. Restricting who can make DNS requests to your server is another effective measure against DNS poisoning.
Use Virtual Private Networks (VPNs)
VPNs provide an additional layer of security by encrypting the communication between your device and the DNS server. This encryption makes it harder for attackers to intercept and change DNS data, thus significantly reducing the risk of DNS poisoning attacks.
Implement DNS Security Extensions (DNSSEC)
DNSSEC adds a layer of authentication to the DNS lookup process, verifying that the DNS response hasn’t been compromised. By ensuring the authenticity of the DNS data, DNSSEC goes a long way in preventing DNS spoofing attacks.
Implement Passwordless Security
One way to prevent credential theft from a DNS poisoning attack is to simply eliminate the use of credentials. Digital certificates, which are issued and managed by a Public Key Infrastructure, cannot be stolen or used by other devices. End-users can log into cloud applications, the wired or wireless network, or even a VPN using a digital certificate instead of a password.
How Can SecureW2 Protect Your Organization From DNS Poisoning Attacks?
SecureW2 offers robust and cost-effective solutions that protect against DNS poisoning attacks. Our managed PKI provides powerful end-to-end encryption, substantially reducing the risk of DNS spoofing attacks by using certificate-driven authentication instead of credentials.
SecureW2’s JoinNow Suite ensures that devices are securely onboarded onto the network with correctly configured settings. This reduces the possibility of connecting to fake or insecure networks, thus mitigating the risk of DNS cache poisoning.
In a nutshell, SecureW2 offers a comprehensive security suite for organizations, providing effective defenses against DNS poisoning attacks. By implementing SecureW2’s solutions, organizations can ensure a more secure network, protecting both their data and their users from potential cyber attacks. SecureW2 is not just about safeguarding your present, it’s about securing your future. Contact us for more information on how we can protect your organization.