With an increasing number of cybersecurity risks and the necessity for secured access to network resources, organizations are implementing various authentication methods. RADIUS certificate-based authentication is one of these techniques, adding another level of security to the RADIUS protocol. 80% of breaches in 2020 involved lost or stolen credentials or brute force.
Using a RADIUS is an effective way to boost network security and visibility, especially when considering that more than Each organization must choose between two RADIUS options: On-Site RADIUS or Cloud RADIUS. This organization decided to use SecureW2’s Cloud RADIUS because they wanted to get rid of all their on-premise servers.
In this article, we will discuss RADIUS certificate-based authentication and explain how it works.
Overview of Certificate-Based Authentication
In today’s digital age, the security of sensitive data is paramount. Passwords are no longer regarded as being a secure enough authentication method because they are so readily stolen or predicted. This is where certificate-based authentication comes into play.
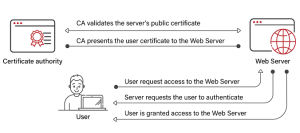
Certificate-based authentication is a type of authentication that makes use of digital certificates. An electronic document known as a “digital certificate” comprises details on the identity of an entity, such as a user or device, as well as the public key connected to that entity. The certificate is signed by a Certificate Authority (CA), a trustworthy third-party entity.
What Is the RADIUS Protocol, and How Does it Work?
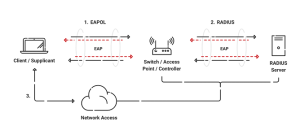
The Remote Authentication Dial-In User Service (RADIUS) protocol is used for remote access to network resources. For users or devices connected to the network, it offers centralized management of authentication, authorization, and accounting (AAA).
The RADIUS protocol has a client-server architecture in which the RADIUS server is situated in a centralized location and the RADIUS client is typically found on the access device, such as a router or switch. When a user or device tries to connect to the network, the access device sends the user’s credentials to the RADIUS server. The RADIUS server then validates the user’s credentials and responds to the access device, granting or denying access to network resources.
The centralized control provided by RADIUS makes it easier for network administrators to manage and safeguard network access. Network administrators may simply add or delete users from the network, modify user rights, and manage access to network resources because the authentication process is centralized. Additionally, RADIUS offers a monitoring and accounting system that enables network managers to monitor network usage and activities.
The network is made more secure by using the RADIUS protocol in combination with certificate-based authentication. RADIUS certificate-based authentication ensures that only authorized parties can access the network resources by utilizing digital certificates to verify the identity of users or devices.
RADIUS Certificate-Based Authentication
RADIUS certificate-based authentication is a technique for verifying the identity of individuals or devices connected to a network through RADIUS by using digital certificates. Using digital certificates to prove the identification of individuals or devices adds another layer of security to the authentication process.
Digital certificates include details about the identification of the entity, like the user’s name or type of device. This information is encrypted and can only be decoded by the RADIUS server using the CA’s public key. If the certificate is legitimate, the RADIUS server can be sure that the person or device connecting to the network is allowed to do so.
The digital certificate is essential in certificate-based authentication since it certifies the identity of the entity connected to the network. When connecting to the network, a user or device gives its digital certificate to the RADIUS server. The RADIUS server then validates the certificate using the CA’s public key. If the certificate is valid, the RADIUS server grants access to network resources.
The usage of a trusted third-party organization, such as a Certificate Authority, is required for certificate-based authentication. The CA is in charge of issuing digital certificates and confirming their validity. When the CA is satisfied with the identity of the entity requesting the certificate, it issues the certificate. Additionally, the CA keeps a list of certificates that have been revoked, which aids in preventing unauthorized network access.
Drawbacks of On-Premise RADIUS Servers
Despite being a popular choice for network authentication, on-premise RADIUS servers have a number of issues that might compromise the security and effectiveness of the authentication procedure. We will go through a few of the main disadvantages of an on-premise RADIUS server in this section.
⦁ Cost and Maintenance
⦁ Scalability and Flexibility
⦁ Security Concerns
Cost and Maintenance
An on-premise RADIUS server can be expensive and time-consuming to install and operate. To keep the server operating efficiently, network managers must make investments in hardware, software licenses, and regular maintenance. On-premise servers also need room, electricity, and cooling, which can raise the total cost of ownership.
Scalability and Flexibility
The scalability and flexibility of on-premise RADIUS servers may be constrained. It may be necessary to make additional hardware and configuration changes, which can be time-consuming and challenging to manage, in order to accommodate more users or devices on the network. It can be difficult to scale up the server to support larger networks, and it might call for buying new hardware or upgrading existing hardware.
Security Concerns
On-premise RADIUS servers may also pose security risks. They need to be maintained and updated on a regular basis to keep up with the latest security threats and vulnerabilities. Additionally, on-premise servers could be exposed to physical security risks like theft or damage, which could jeopardize the authentication process’ security.
Now that we have seen the drawbacks of on-premise RADIUS servers, you must be wondering how to eliminate or minimize the risks associated with these servers. In the next section, we will look at how migrating RADIUS servers to the cloud has numerous benefits in the long run.
Advantages of Cloud RADIUS
RADIUS servers existing on the cloud, such as SecureW2’s Cloud RADIUS, are a more efficient and secure alternative to on-premise RADIUS servers. We will explain some of the main benefits of using Cloud RADIUS in this section.
⦁ Cost-effective and easy to maintain
⦁ Scalable and flexible
⦁ Enhanced security
Cost-Effective and Easy to Maintain
Cloud RADIUS is a low-cost, easy-to-manage solution that eliminates the need for on-premise hardware and software. The Cloud RADIUS provider manages all hardware and software maintenance and upgrades, allowing network administrators to focus on other things.
Scalable and Flexible
Cloud RADIUS also offers better scalability and flexibility. It is quick and simple to add more devices or users to the network, and expanding the server’s capacity to support larger networks is also straightforward.
Additionally, Cloud RADIUS offers more flexibility in terms of authentication protocols and methods, enabling organizations to use other authentication protocols and methods, such as certificate-based authentication.
Enhanced Security
Cloud RADIUS offers increased security features as well. Cloud RADIUS providers secure the authentication process with advanced security measures, including multi-factor authentication and encryption.
Cloud RADIUS servers are also often kept in extremely secure data centers that offer both physical security and protection against theft and damage.
The Role of CBA in Ensuring the Security of Your Organization
Compared to traditional password-based authentication techniques, certificate-based authentication (CBA) has a number of security benefits. In this section, we’ll talk about how CBA improves authentication security and mitigates some of the negative aspects of password-based authentication.
Stronger Authentication
Digital certificates used in CBA are far more secure than conventional passwords. Digital certificates are cryptographic keys that are created and validated by Certificate Authorities (CAs), reputable third-party entities. They offer a more secure method of authentication than passwords because they are specifically linked to the user or device and are therefore challenging to copy or forge.
Password Elimination
CBA also minimizes the risk of password-related security breaches by doing away with the requirement for users to remember and manage complex passwords. Because they are so readily broken, stolen, or guessed, passwords are frequently the weakest link in the authentication process. CBA streamlines the authentication process and eliminates the need for users to remember passwords, making it easier for individuals and safer for organizations.
Reduced Risk of Credential Stuffing
Credential stuffing is a form of cyberattack in which hackers use usernames and passwords taken from one website to obtain unauthorized access to another website. This form of attack is getting increasingly common since people tend to reuse passwords across multiple websites. By using distinct digital certificates for each user or device, CBA decreases the risk of credential stuffing and makes it considerably more difficult for attackers to enter the network.
Cloud RADIUS: The Key to Secure and Flexible Certificate-Based Authentication
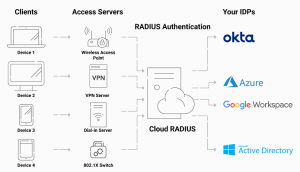
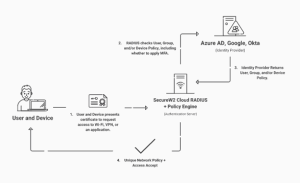
SecureW2’s Cloud RADIUS server offers multiple benefits to organizations looking to deploy certificate-based authentication. Our Cloud RADIUS server enables organizations to authenticate certificates and validate user, group, and device information in any Identity Provider (IDP) at the time of authentication, in addition to offering a secure and scalable solution. This means that organizations can use their existing identity management systems to authenticate people and devices without the requirement for extra infrastructure or management overhead.
Organizations can take advantage of real-time access control and policy enforcement with the help of our cloud-based RADIUS server. The server enables organizations to create access policies based on user, group, or device information and automatically enforce those restrictions at the time of authentication. This enables organizations to reduce the risk of unauthorized access while remaining in compliance with security policies and regulations.
Contact us today to learn more about how our Cloud RADIUS can improve your organization’s network security.