Forgetting your password is one of the worst things about the internet. Unfortunately, it is encouraged to create complex passwords, making remembering them more difficult.
Consequently, a considerable number of users elevate their vulnerability to cyber threats by either resorting to the practice of recording their passwords or adopting the habit of utilizing identical passwords across multiple accounts.
Drawing from the presented evidence, it can be inferred that passwords pose several challenges, including but not limited to being prone to forgetfulness, requiring complex management across multiple platforms, being susceptible to significant security breaches, and causing frustration among users.
Fortunately, technology has progressed past the need for multiple passwords thanks to innovative Single Sign-On and passwordless solutions. This article will discuss the configuration of certificates for authentication with Okta, Google Workspace, and Azure Active Directory, three of the most commonly used SSOs.
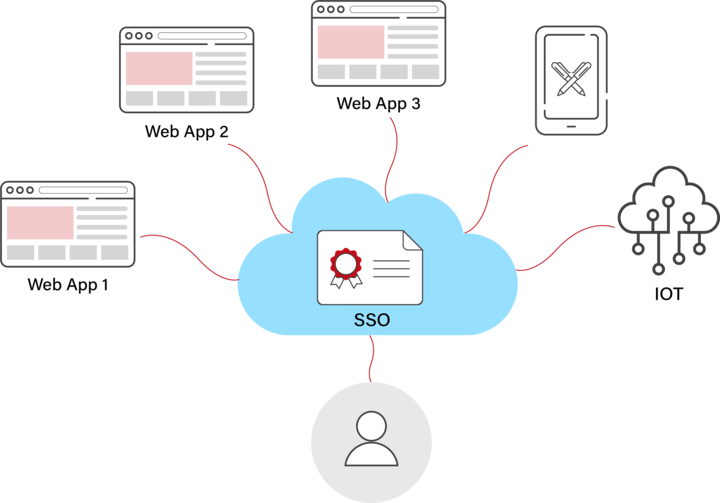
What Is an SSO?
Single sign-on (SSO) is an identity verification mechanism that eliminates the requirement for users to repeatedly input their login information when transitioning between different applications or platforms. In numerous designs, authentication tokens, also known as cookies, are employed for this objective. In Single Sign-On (SSO) systems, tokens retain the authentication status of a particular user across all constituent applications within the SSO framework.
SSO authentication systems can improve the safety of the internet in two main ways:
- By strengthening the passphrase.
- By simplifying administration and security by centralizing approaches.
How does SSO work?
The four-step SSO procedure is as follows:
- First, a user accesses a website or app.
- Next, the site sends the user to a centralized SSO login screen to enter credentials.
- Finally, SSO domains perform verification, identification, and token production using the entered credentials.
- Finally, the token acts as ‘proof’ for the authentication, and the user is then redirected to the original site with access to associated apps and web pages.
How Do Passwords Make SSO Vulnerable?
For starters, if an attacker obtains a user’s password, they will have access to all systems and apps for which that person has SSO privileges. In addition, the password that an employee uses for SSO may be weak, already hacked, or the same one that they use for several other accounts. Finally, it’s also possible that workers may divulge their credentials to others.
The primary goal of SSO is to eliminate the need for users to provide several sets of credentials when gaining access to multiple interconnected systems or databases containing sensitive information. Hence, privileged users and sessions are not safeguarded in any way. In the next section, we will analyze how, contrary to using passwords, digital certificates provide the highest level of security and enhance user experience.
How Can Digital Certificates Enhance SSO Security?
Certificate-based authentication (CBA) is a security mechanism that involves the issuance of digital certificates to users for the purpose of verifying their identities when accessing systems or applications that are integrated into the Single Sign-On (SSO) network. The uniqueness of the certificates employed in CBA renders them impervious to replication or theft, thereby endowing CBA with superior security features compared to passwords.
To read more about digital certificates, please visit this page.
The following are several methods by which CBA enhances the SSO procedure:
- More Secure Authentication
- Better End-User Experience
- Improved Scalability
More Secure Authentication
CBA is deemed a highly secure method for authenticating users and devices due to its utilization of public key cryptography, a sophisticated security technique. This is due to the utilization of a cryptographic system that involves a pair of keys, namely a private key and a public key. The data can only be deciphered by the corresponding private key. Furthermore, the information is encrypted during transmission or while being transmitted wirelessly, thereby rendering it indecipherable to unauthorized individuals attempting to gain access through hacking or phishing tactics.
Better End-User Experience
Certificate-based solutions require little input from the end user. The system requires a few internal resources for maintenance. The increased security is obtained without further work on the user’s behalf. Expanding security measures might result in unintended consequences.
Improved Scalability
When it comes to supporting a large number of users and devices, authentication systems based on certificates perform very well. This is because users are relieved of password management responsibilities when certificates are issued and revoked by the CA on their behalf.
What Do You Need to Implement Certificate-Driven SSO?
The utilization of certificates as a means of authentication enhances both the security and user-friendliness of Single Sign-On (SSO) systems. The utilization of certificates as a means of authentication enhances both the security and user-friendliness of Single Sign-On (SSO) systems. The implementation of digital certificates necessitates the presence of a public key infrastructure (PKI), which comprises a suite of tools encompassing hardware, software, regulations, processes, and protocols for managing public keys and digital certificates. The verification of the sender’s identity in digital communication can be accomplished through the utilization of the digital certificate linked to the cryptographic public keys.
Building and maintaining PKI in-house is not recommended for avoiding downtime. Dealing with a few or a few dozen servers may take time and effort. A server certificate must be updated, checked for problems, and removed when its validity ends.
SecureW2 provides certificate-based authentication solutions that are trusted by enterprises throughout the globe because they are safe, scalable, and simple to use, thanks to the power of public key infrastructure (PKI). In addition, SecureW2 offers affordable options for organizations of all sizes.
Setting Up Certificate Authentication for Okta
Okta is a frontrunner among identity and access management (IAM) solution providers for businesses of all sizes and regions worldwide. The Okta platform allows you to control which apps and devices your staff members can access. Administrators can even configure Okta SSO so end-users can utilize their Okta credentials to log into other workplace applications.
However, using passwords to log into sensitive resources still risks your network. So, instead of using credential-based SSO, Okta allows administrators to set up certificate-based authentication so users can verify with certificates instead of accessing multiple applications. At a high level, configuring Okta SSO with certificates and SecureW2 looks like this:
- In the SecureW2 Management Portal, add Okta as an IDP.
- Connect SecureW2’s certificate-issuing services to the IDP requires developing a SAML Application in Okta.
- Add Okta Metadata and Set up Attribute Mapping.
- Configure roles and enroll guidelines.
- Install and configure SecureW2’s Cloud RADIUS on your wireless network.
Please check out our Okta integration documentation for more detailed information on configuring Okta SSO.
Using digital certificates dramatically improves the user experience, boosting network security and efficiency. They have given enterprises additional security alternatives and made it simpler to switch from credential-based defenses. In addition, X.509 digital certificates are easy to migrate to, as one of our clients explains.
Setting Up Certificate Authentication for Google Workspace
Google Workspace customers can access the Single Sign-On (SSO) service, which provides secure authentication and authorization for web and mobile applications. In addition, like Okta, Google allows end-users to utilize their workspace credentials to log into other workplace applications.
In addition, users who have already signed in may securely sign in to Google Workspace with a single click, bypassing the need to enter their username and password a second time. However, despite being incredibly straightforward, password authentication is dangerous today.
Certificates and public keys created with the RSA or DSA method are compatible with the Google Workspace Single Sign-On service. The SSO may only access the necessary public and private keys, and X.509 certificates are generated. At a high level, configuring Workspace SSO with X.509 and SecureW2 looks like this:
- First, enter your login information into the SecureW2 Management Portal.
- Next, navigate to Identity Management > Identity Provider.
- To add an identity provider, click the Add button.
You can click here to learn more about Google Workspace and its configuration steps for certificate authentication.
Setting Up Certificate Authentication With Azure AD
Azure AD CBA allows users to authenticate to any Azure AD application using an X.509 digital certificate instead of a username and password. Digital certificates are virtual photo IDs with the device or user information. As discussed earlier, certificates are shielded from cybercriminals by asymmetric encryption, which makes them more secure than easily guessed passwords.
Once established, users can log into Azure AD applications using their certificate, which means no more complex passwords, no password resets every 60 days, no IT support requests, and, mo1st importantly, no password sharing.
At a high level, configuring Azure SSO with certificates and SecureW2 looks like this:
- First, create an IDP by logging in to the JoinNow MultiOS Management Portal.
- Next, go to Identity Management > Identity Providers and click Add Identity Provider.
- Under the Basic tab, enter the name and description.
- From the Type drop-down list, select SAML.
- From the SAML Vendor drop-down list, select Azure.
To learn more about configuring certificates for Azure SSO, please click here to view the detailed steps.
Implementing Digital Certificates to SSO Using SecureW2’s Intuitive Interface
Okta, Google, and Azure AD support SSO with certificate capabilities, thus enhancing security and user satisfaction. Manual enrollment of digital certificates for SSO is a time-consuming and laborious process.
In addition, the admins must possess top-notch technical skills to implement certificates. As a result, many firms have delayed enforcing them and are at risk of irreparable damage because of cyberattacks. Luckily, SecureW2 offers solutions for the problems mentioned above.
SecureW2’s Cloud RADIUS is perfect. Businesses can use their existing infrastructure to authenticate users with certificates and validate them.
Click here to inquire about pricing.



