The Health Insurance Portability and Accountability Act (HIPAA) has impacted the way healthcare organizations operate since its introduction in 1996. Its goal, ultimately, was to protect patient data by imposing requirements for how that data is accessed and maintained.
Complying with HIPAA extends far beyond physical measures located on-site; the quality of your network security is also of the utmost importance. 802.1X is an IEEE network standard that prevents unauthorized network access through the use of an authentication server (RADIUS) as well as individual credentials for each user accessing the network. As some of our customers have discovered, building HIPAA compliant 802.1X can go a long way towards safeguarding sensitive electronic Protected Health Information (ePHI) – here’s how.
HIPAA Compliance and Wi-Fi Network Security
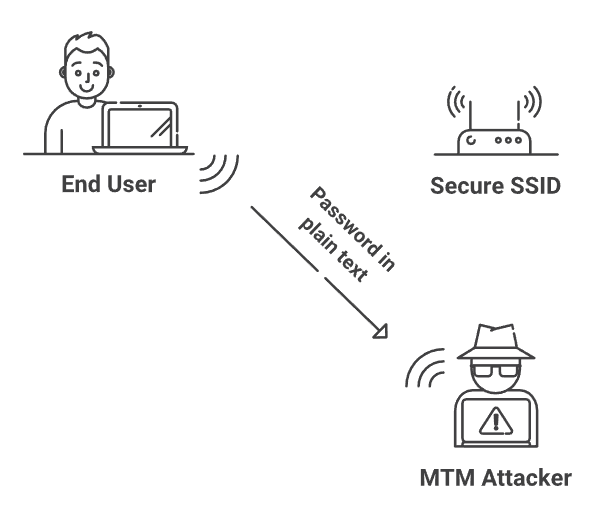
To understand how vital Wi-Fi network security is to HIPAA compliance, you need to realize just how many threats there are that can exploit your Wi-Fi network today. If your organization just uses the standard PSK (preshared key) Wi-Fi setup (one shared password to access your wireless networks), it’s simple for hackers to obtain the password even if your network is only ostensibly available to staff.
Hackers can crack usernames and passwords through a variety of methods, including dictionary attacks and brute force attacks. Attacks don’t necessarily have to be active; some hackers set up false Wi-Fi access points to connect to in evil twin attacks or passively gather information in over-the-air attacks. Even malicious parties that aren’t tech-savvy can attempt to harvest credentials through phishing attacks that rely on tricking legitimate users into volunteering those credentials.
Furthermore, IoTs on your network can be easily exploited. In fact, over 80% of medical devices experienced a cyber attack in 2019 alone.
These facts are especially harrowing given today’s complex, multi-provider healthcare system. In the modern world, medical professionals will frequently need to handle ePHI and PHI over-the-air, exposing that information to the potential view of unauthorized third parties. This is true in numerous environments, from a hospital network setting to a private medical practice. The importance of protecting your network from that unauthorized access cannot be understated, and 802.1X can help you achieve that.
Is Wi-Fi HIPAA Compliant?
It’s not impossible to have Wi-Fi that’s HIPAA-compliant, but it’s more of a challenge than establishing the same kind of Wi-Fi setup you have at home. There isn’t a specific HIPAA security rule that lays out the standards for Wi-Fi; however, it does establish a set of requirements that can be and are applied to your Wi-Fi security.
These standards include the following considerations:
- Each user must have their own unique set of credentials.
- These credentials must be authenticated.
- Users should have different levels of access.
- After periods of inactivity, users’ network access should be cut off until they log in again.
- Administrators must keep and audit logs to ensure no suspicious activity is occurring.
- Some kind of alert system needs to be established in the event of a breach.
- Data has to be backed up and recoverable after an emergency.
- Any physical infrastructure that stores ePHI has to be cleared when it is used for new functions.
How Do I Make My Wi-Fi HIPAA Compliant?
By far the easiest way to make your Wi-Fi HIPAA compliant is to deploy 802.1X. This requires some changes to your infrastructure, including an authentication server (RADIUS) and individual login credentials for each user on your network.
We’ll talk in more detail about those infrastructure changes below.
Wi-Fi Protocols: WPA2-PSK vs WPA2-Enterprise for Healthcare
The commonly used WPA (Wi-Fi Protected Access) protocol has a lot of variations. In the home setting (and even in some small business settings), you’ll often see the use of WPA2-PSK, which is when one shared password is required to access the network.
While this is generally fine in home environments, it’s not very secure for hospital networks or other healthcare environments. For one thing, you can’t guarantee that only legitimate parties have access to that password; it can easily be shared with malicious parties that are looking to initiate over-the-air attacks in public spaces. Furthermore, if you update the password periodically, you have to deal with the frustration of all connected devices being disconnected until you input the new password on all of them.
WPA2-Enterprise, a Wi-Fi protocol that requires unique passwords from each user, is much more secure. Because users have their own credentials, you can track which users are connected through the use of their unique credentials. You can also grant them varying levels of access since they are not all using the same password. However, this setup needs a RADIUS server for Wi-Fi authentication.
RADIUS Server Security for Healthcare
RADIUS servers, also known as AAA (authentication, authorization, and accounting) servers, heighten your Wi-Fi security even further through a number of means, as well. Here’s a summary of the HIPAA-relevant security features RADIUS can extend to your network:
- Authentication for each individual set of credentials or certificate.
- Event logs for each device or user attempting to access your network.
- Application of attribute or role-based access control through policies in your IDP.
The main benefit to RADIUS is obvious: the RADIUS server checks each device’s certificate or credentials as it attempts to access your Wi-Fi, confirming that the user or device is authorized. If the certificate is expired or has been revoked, the device will be denied access. Similarly, if you’re using credentials, credentials linked to invalid accounts will also be denied access.
RADIUS servers also generate event logs. The detail of the event logs themselves may vary from RADIUS to RADIUS, but with SecureW2’s Cloud RADIUS, your administrators can see every single network connection attempt in the logs. Our logs are also designed to be highly searchable; you can search with various attributes such as the user’s email address, the timestamp of the connection attempt, or even the certificate’s serial number for efficient troubleshooting or monitoring.
Finally, features like Identity Lookup allow Cloud RADIUS to apply role-based access control policies. When a device authenticates to the RADIUS, it will cross-reference your IDP to see which groups the device belongs to and apply the policies accordingly. For example, if you have designated that the device can only go n a specific VLAN, the RADIUS will apply that policy based on what it finds in your IDP.
Certificate-Based Authentication (CBA) for Healthcare
Using digital X.509 certificates rather than passwords for authentication offers you a range of Wi-Fi security benefits that are relevant to HIPAA compliance:
- Elimination of credential theft.
- Improved user experience.
- Ability to extend role-based access control policies from other parts of your infrastructure, such as your Identity Provider.
- Increased network visibility through rich context for each connection.
Unlike passwords, digital certificates can’t be stolen by hackers. The lack of passwords isn’t just beneficial for security; it improves end user experience. Employees no longer need to regularly reset their passwords, remember numerous passwords, or deal with annoying disconnects when their passwords expire. Instead, certificates are automatically presented to the authentication server by the device and the user is seamlessly authenticated without their input.
What’s more, certificates provide significantly more information regarding the devices connected to your network than passwords do. After all, anyone can log into an account if they know the username and password – this isn’t true for certificates, which are tied to specific devices and users through context-rich templates. You can therefore see tons of information for each connected device, such as the user’s email address, operating system, and much more with the assurance that the information is accurate.
Certificates can even be issued to many of the IoTs used in healthcare facilities, making them secure and giving your administrators control over their access. And in the event the IoT can’t store certificates, as is the case with some simple devices, you can always use MAC auth bypass to authenticate them to your network instead. With MAC auth bypass, a device can authenticate by providing its MAC address instead of a certificate.
However, if you’re using digital certificates or MAC auth bypass, you need something else to authenticate the certificates or MAC addresses, and that’s where a RADIUS server comes into play.
Protect Sensitive Data by Upgrading Your Wireless Network to 802.1X with SecureW2
In the past, 802.1X has been considered a difficult standard to achieve because its individual components – especially the PKI and RADIUS – require a large degree of technical expertise. With the right tools, however, it can be surprisingly simple.
SecureW2 offers you virtually everything you need to upgrade your wireless network to 802.1X. That includes Cloud RADIUS, a RADIUS service designed specifically for passwordless authentication, and JoinNow Connector PKI, a turnkey PKI that slots into your existing network. Additionally, we have easy self-service onboarding for unmanaged devices, zero-touch certificate auto-enrollment for managed devices, and MAC auth bypass for IoTs that can’t store certificates.
Take the steps towards HIPAA compliance today by building your own 802.1X network. Protecting ePHI alone is worth it, but it certainly helps that SecureW2 makes the switch simple and fast. Schedule a free demo today.



