Without protection, your organization’s network is vulnerable to cyber attacks. The 802.1X protocol heightens network security by introducing RADIUS servers for authentication, and Lightweight Directory Access Protocol (LDAP) has commonly been used alongside RADIUS due to its ability to quickly search directories for information like credentials.
In the past, the use of LDAP in 802.1X has been perfectly sufficient. As we move into the future, however, it’s becoming increasingly clear that LDAP is riddled with problems, such as its reliance on passwords and outdated on-premise hardware. What if we were to tell you that many SecureW2 customers have discovered you don’t actually need LDAP for 802.1X?
We’ll explain why and what you can do to leave LDAP in the dust.
Is 802.1X Still Used Today?
It’s no secret that the cybersecurity landscape is constantly changing. A common practice today is likely to fall out of use in just a couple of years, if not even sooner than that.
With that being said, 802.1X is still a rigorous standard in wide use by security-conscious organizations today. It remains a security goal to strive for, given the protective power a RADIUS server lends to your authentication flow.
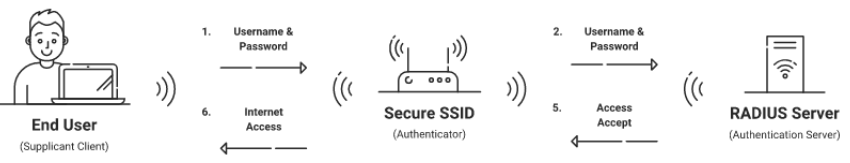
In fact, the presence of a RADIUS server is the key difference between 802.1X WPA2-Enterprise and the standard WPA2-PSK Wi-fi you’re used to seeing at home. RADIUS servers, in a nutshell, are like virtual gates – they check a user’s credentials prior to allowing them access. Historically, the use of LDAP has made such authentication possible by querying a person’s username and password in an LDAP-compatible directory such as the ubiquitous Active Directory.
You can get a general idea of how 802.1X works in the illustration above, as well as where RADIUS servers sit in the network landscape. Ultimately, while the individual components of 802.1X may change, the framework and idea behind it are likely here to stay. One particular component we’ve watched falling out of favor is the use of LDAP.
3 Problems with LDAP
Example of How LDAP Works in a Network Using Okta as the IDP
LDAP has been an integral part of many organizations, but it’s beginning to show its age. There are numerous reasons why organizations should move away from it while building their own 802.1X networks, but here are the key reasons:
- LDAP is not compatible with cloud-based identity providers.
- LDAP is tied to on-prem equipment.
- LDAP is insecure.
LDAP is Incompatible with Cloud-Based IDPs
Cloud-based identity management is vital to businesses today. Common examples of identity providers (IDPs) include Azure AD, Okta, and Google, and the use of such cloud directories allows organizations to build strong security practices and reduce reliance on on-premise infrastructure.
The prevalence of cloud IDPs is precisely what makes LDAP’s inability to communicate with them directly so devastating. In the extremely common scenarios where businesses want to have an 802.1X network that uses information contained in a cloud IDP’s directory, reliance on LDAP ends up actually being reliance on an unnecessary LDAP server that functions as a go-between.
LDAP Relies on Outdated On-Premise Systems
LDAP is generally tied to on-premise equipment, such as Active Directory servers. It is actually used so commonly with on-premise AD servers that the terms “Active Directory server” and “LDAP server” are sometimes used interchangeably.
Such designs are becoming increasingly costly, unnecessary, and infeasible as the industry moves to cloud computing. Aside from taking up extra space, on-premise equipment requires you to enact physical security measures to protect it from on-site dangers, such as outages and bad actors. It also needs personnel dedicated to its maintenance. All of these things add to your expenses.
LDAP’s Insecurity
LDAP’s greatest weakness is its dependence on credentials (usernames and passwords) for authentication. To say passwords are a lackluster authentication method is a massive understatement – passwords are an enormous, costly liability that hackers can easily exploit through a plethora of cyber attacks.
At the end of the day, a door is only as strong as its lock. If that lock can be picked with minimal effort – just like a password can be – then it isn’t an effective deterrent for thieves.
How to Build an 802.1X Network without LDAP
We’ve spent time explaining why you shouldn’t use LDAP, but haven’t yet explained the alternatives. So, how exactly do you jump to 802.1X network authentication without using LDAP at all?
The answer is especially important if you, like countless others, use a cloud-based identity management system. Here it is: a passwordless authentication platform with native cloud integration through modern protocols such as SAML and OAuth.
Security Assertion Markup Language (aka SAML) is seeing increasingly widespread use, especially when it comes to the cloud. You can picture the SAML protocol as a way RADIUS servers can communicate with cloud-based directories.
It comes with a range of benefits. The first is that it was designed for use in a cloud environment, making it much more relevant for the future than LDAP is. This means that SAML doesn’t have the same ties to on-prem equipment.
Another benefit is SAML’s use in SSO (single sign-on), which allows logins to tap into another existing directory to verify users. The result is that users are able to log into multiple applications using one set of credentials.
Reducing the number of passwords someone needs to use is beneficial on numerous levels. You reduce the risk of password mismanagement, such as reused passwords and forgotten passwords. Additionally, having to generate fewer passwords is simply a more user-friendly experience – no one wants to have to come up with dozens of unique, complex passwords for all the services they need to log into.
At the end of the day, however, passwords are still a vulnerability. The good news is that you can eliminate them entirely by using digital certificates instead.
LDAP, SAML, and Certificate-Based Authentication
Certificates inherently are a superior authentication method to passwords. You can’t steal a password if it doesn’t exist; similarly, you can’t forget it or struggle to come up with a new one when there’s no need for one to begin with.
Another issue with LDAP, however, is that certificates make it redundant. Remember, LDAP is generally used with credentials (username and password), which certificates can replace. Certificates are also based on templates that contain a number of user or device attributes, allowing you to enact role-based policy access – yet another quality that enables them to usurp LDAP in the world of authentication.
SAML, in comparison, can be and often is used alongside certificate-based authentication. Its cloud-based design permits direct communication with cloud IDPs. RADIUS servers capable of identity lookup, like our dynamic Cloud RADIUS, are able to communicate with your cloud IDP using SAML.
LDAP-Less 802.1X isn’t Just Possible – It’s Easy with SecureW2
SecureW2 has built a full suite of tools necessary to upgrade the mechanisms you use to safeguard your network with secure digital certificates. Certificate-based authentication has had a reputation in the past for being more trouble than it’s worth, but that’s no longer the case.
Our powerful Cloud RADIUS was designed for certificates, and it can even reference your cloud Identity Providers in real-time during authentication – no need for an extra LDAP server in between. Additionally, we offer a managed Public Key Infrastructure (MPKI) which streamlines all parts of the certificate lifecycle, from enrollment to revocation. We even have self-service onboarding software to equip your unmanaged devices with certificates and managed device gateways that automatically push configuration profiles to company-owned devices through a range of APIs like JSON, SCEP, and WSTEP.
We’ve been part of many organizations’ plans to leap to passwordless authentication, working with organizations of all sizes and verticals. Having worked with all kinds of organizations, we have extensive experience with all kinds of infrastructure, as well. Try our Free Demo to see how we can help you leave LDAP behind.