It wasn’t too long ago that accessing a school network meant logging onto a stationary desktop in a computer lab. In today’s IT environment, however, more and more devices are able to access school resources both on-site and even remotely.
While many K-12 schools and other educational institutions utilize managed 1:1 devices, such as Chromebooks, there are still numerous unmanaged devices to consider. Students and staff alike have a variety of devices with Wi-Fi capability, including things like smartphones and even gaming consoles. These types of devices are even more prevalent in higher education campuses where students live on-site.
Fortunately, protecting your school’s wireless network doesn’t have to be complicated – even where BYODs are involved. In this blog, we’ll look at how you can improve your student BYOD Wi-Fi security.
BYODs in School Networks
Allowing BYODs in schools has plenty of positives. For starters, BYODs allow students and staff to use devices they’re already familiar with, making navigating the difficulties of communication and research easier to get past. Costs are also reduced for the school if they rely on BYODs more than managed devices, as the school doesn’t have to purchase devices for all their end-users.
Furthermore, BYODs can inherently work remotely. End-users were already using these devices from their home or on the move. After the onset of the Coronavirus pandemic, remote education and the devices that enabled it became significantly more important.
However, unmanaged devices also present a range of unique risks that aren’t faced in MDM-controlled environments.
Potential Threats Faced by BYODs
Implementing a BYOD policy has its benefits, but there are also threats you should be prepared for. These threats include the following:
- Device Diversity
- Misconfiguration
- Access to Non-School Resources
- Password Mismanagement
Device Diversity
Since unmanaged devices aren’t issued by the school, there’s no way to guarantee that they all have the same capabilities and operating systems. Different operating systems have different settings, and can therefore interact with your school network in different ways.
This poses a serious challenge when it comes to onboarding. If you’re going to require your students and faculty to adhere to a specific authentication protocol, for instance, you’re going to need to ensure that all devices with network connectivity can even support that authentication protocol. For example, some devices are incompatible with 802.1X, a widely used authentication standard that requires individual network credentials and a RADIUS server for authentication.
Misconfiguration
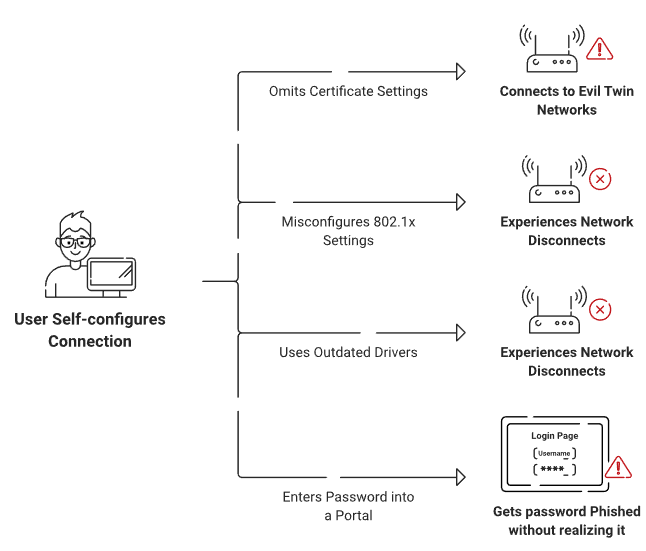
With unmanaged devices, there is also a high risk of misconfiguration. If you’re requiring students to utilize specific security settings, it can be difficult to ensure these are properly enabled.
In a K-12 environment, your end-users encapsulate a wide range of ages and levels of technical literacy. It’s possible for older children and teens to follow detailed configuration steps, but the same cannot be said for elementary-age students.
You could have administrators manually configure end-user devices themselves. Unfortunately, this creates a strain on their time and resources. Even more unfortunately, the consequences for misconfiguration can be serious, including possibilities like missing important security patches and lacking proper malware protection. For these reasons, a user-friendly onboarding solution is imperative when you have a BYOD policy.
Access to Non-School Resources
You cannot guarantee what types of resources students and staff will visit in their spare time on an unmanaged device. Furthermore, there’s no way to guarantee that the things they do access will be safe.
In fact, in 2022, Kaspersky found that cyber attacks on devices used by children had increased by 57%. Many of these attacks pose as files for popular gaming franchises played by students around the world, leading to malware installations on said devices. Once a compromised device accesses your network, there are a number of attacks that can be deployed to gain access to sensitive resources.
Password Mismanagement
Another common pain point is problems associated with using credentials. These days, everyone has usernames and passwords to dozens of different services. It’s hard to keep track of, and this can lead to poor password management.
Both employees and students may accidentally repeat passwords, use weak passwords, or write down passwords in places where they can be stolen. Even if they don’t do any of these things, frequent password expiration policies are bound to frustrate anyone struggling to keep on top of all their credentials.
To make matters worse, there are tons of attacks designed to snatch credentials, and poor password management makes it easier. Brute force and dictionary hacks can quickly crack weak passwords. Man-in-the middle (also called MITM) attacks can snag a user’s credentials by creating convincing rogue access points for them to connect to.
Certificate-based authentication is a secure alternative to credentials. Digital certificates allow end-users to access school resources without having to deal with the frustration of passwords, empower administrators to develop granular network segmentation policies, and protect your users from credential theft.
Addressing BYOD Vulnerabilities
It’s easy to feel a little overwhelmed when you acknowledge the numerous threats and risks associated with using BYOD and managed devices on your school’s network. The good news is that SecureW2 offers you a solution in easy certificate-based authentication – and everything you need to quickly implement it.
We can address many of the pain point associated with BYOD Wi-Fi security through a range of technologies, including:
- Secure Certificate-Driven Authentication
- Complete Certificate Lifcycle Management
- Efficient Onboarding Technology
- Managed RADIUS-Backed Authentication
Secure Certificate-Driven Authentication
Relying on a Pre-Shared Key (PSK) network unnecessarily puts your school’s network at risk. Many people share passwords with friends, family, and coworkers, so you can be virtually certain that a single password for your Wi-Fi will be leaked to unauthorized parties quickly. But even using individual usernames and passwords for a WPA2-Enterprise network can be risky, thanks to password mismanagement and weak passwords.
Digital certificates solve all these issues and more. By tying your network access to digital certificates, you can ensure that only authorized users connect to your Wi-Fi, since certificates cannot generally be transferred.
Certificates also reduce reliance on passwords – and therefore reduce the risk of credential theft. If there isn’t a password being used to connect to the school Wi-Fi, then there isn’t a password to steal.
Beyond these benefits, certificates increase network visibility drastically by providing more information on each connected device. A username and password can be used by anyone, but a certificate is tied to a specific device or user. They also contain significantly richer context in their templates, so administrators have more information at their disposal.
Complete Certificate Lifecycle Management
If you don’t have the right tools, managing your users’ certificates can be a bit of a hassle. Both students and teachers in your school will come and go, requiring you to frequently issue and revoke certificates. Some staff may be promoted and require a change to the level of authorization afforded to them by their certificates.
Our managed Public Key Infrastructure (PKI) gives you all the tools you need to manage your certificates every step of the way, from issuance to revocation. All of this information is at your fingertips with an intuitive management portal, as well as a knowledgeable support team that has worked on hundreds of deployments with schools.
Efficient Onboarding Technology
One of the biggest challenges with digital certificates is last-mile distribution. Getting them onto each BYOD, with all the differences in operating systems, can initially seem like a headache.
This is why efficient onboarding technology is crucial. JoinNow MultiOS is a downloadable and dissolvable client designed for this express purpose. Once it is installed and run, the end-user can self-configure their own devices in just several clicks. It streamlines and simplifies the configuration process for students, their parents, and school faculty. As a result, your IT team has more time to focus on other issues.
It follows a few simple steps:
- The user navigates to your established onboarding page.
- MultiOS detects which operating system the user’s device has.
- The user downloads and runs the application.
- The user enters their school credentials once and waits briefly while MultiOS enrolls their device for a certificate and configures their device.
JoinNow MultiOS is compatible with all major operating systems, and many less common or obsolete ones, too. The client can also detect your operating system and provide a detailed, step-by-step user flow if the operating system in question is unsupported.
Managed RADIUS-Backed Authentication
If you’re using digital certificates for authentication, you’ll need something to authenticate them with. In a secure WPA2-Enterprise network, that means a Remote Authentication Dial-In User Service (RADIUS) server.
Setting up a RADIUS server yourself can be costly, time-consuming, and difficult. The alternative is a managed RADIUS service such as Cloud RADIUS.
Cloud RADIUS takes all the hassle out of maintaining a RADIUS server. Your school’s IT staff no longer need to worry about security patches and paying for costly regular hardware updates for an on-premise RADIUS server. Additionally, Cloud RADIUS allows for extremely granular network policies that can restrict access to your school network. Policies can be based upon a range of qualifiers, such as time of day, MAC address, or the issuing CA for a certificate.
BYOD Policies Don’t Have to Leave the School Network Vulnerable
Unmanaged devices have the potential to pose a risk to any network without rigorous network access control policies. Updating network access control policies doesn’t have to be lengthy, expensive, or difficult, though. With a completely passwordless platform – and the onboarding technology you need to implement it – you can reduce the risks presented by BYODs on your Wi-Fi.
Certificates drop the risk of credential theft while simultaneously ensuring secure and streamlined network access for all of your users. Our self-service onboarding application and Cloud RADIUS bolster these certificates further by making it simple to enroll for them and by providing you with a powerful policy engine you can use to build network access policies from.
Talk to our network security specialists today about how our solution fits into your infrastructure.