The definition for a Public Key Infrastructures (PKI) varies among cyber security professionals, but is generally considered a collection of components that give everything an organization needs to issue and manage X.509 digital certificates.
Cloud PKIs are more versatile and are a third the cost of on-premise legacy PKIs, like with Microsoft AD CS. SecureW2’s PKI is pre-configured with a Cloud RADIUS server and allows admins to configure EAP-TLS authentication, the strongest 802.1X authentication protocol because certificates are used instead of passwords. See how easy it was for one of our customers to switch to a cloud-based PKI and ditch passwords across the network.
PKIs can be configured to provide authentication for multiple services, such as Wi-Fi, VPN, Web Apps, E-Mail and more.
Why a Microsoft Enterprise PKI?
Passwords are not good forms of authentication as they can be lost or stolen, meaning networks that use credential-based authentication are always at risk of over-the-air credential theft. Plus, credential-based authentication setups require password reset policies, which are annoying for both network administrators and end users.
Digital certificates provide better identification because they can be locked onto devices and serve as the device or user’s identity in the digital landscape. With certificates, admins can easily configure devices for certificate-based 802.1X authentication, or EAP-TLS. PKIs serve as the foundation for admins to build a certificate-based network
Managed PKI vs On-Prem PKI

The cyber security industry is teeming with robust PKI solutions, so it can be challenging finding the right one. Microsoft’s Active Directory Certificate Services (AD CS) allows admins to build an on-premise PKI, and it may seem like a no-brainer for Windows customers.
However, on-prem PKIs are incredibly expensive, labor-intensive, and take months to set up. Microsoft enterprises have to pay for hardware and software implementation, licensing fees, infrastructure, eventual replacement and much more. Plus, on-prem PKIs require a team of professionals to manage, meaning Azure enterprises have to dedicate time and resources to either train their IT department or find new employees.
None of this is necessary with a managed PKI service, which is a fourth of the cost of on-prem PKIs because it’s all on the cloud, can be set up in a few hours, and costs a fraction of the price of on-prem PKIs. Enterprises only need one part-time PKI manager, no expensive team of experts required. SecureW2’s Managed Cloud PKI is the actual no-brainer because it’s a turn-key PKI solution that requires no forklift upgrades.
Configuring a Microsoft PKI
Building a PKI from scratch is a grueling task, unless you choose SecureW2’s Managed Cloud PKI that streamlines the implementation process and takes away the workload from the admin. Below we’ve laid out just how easy it is to deploy our PKI for your network.
Use Our Getting Started Wizard
SecureW2’s PKI services are completely turnkey because all the necessary tools for PKI implementation are set up through our Getting Started wizard. This easy-to-use wizard will set up a Root and Intermediate CA, Base and Delta CRL, RADIUS Server, Network Policies and everything else you need to set up a PKI.
Microsoft Enterprise PKI + AD
SecureW2’s service allows admins to integrate their SAML or LDAP Identity Provider (IDP), like AD or Azure AD, in SecureW2’s Management Portal. Now, the SecureW2 certificate enrollment clients can use the IDP as a Single-Sign-On (SSO) for certificate enrollment, ensuring only members of the organization are issued certificates. Next, admins will need to configure a RADIUS server that can reference the directory and securely authenticate and authorize users.
Microsoft Enterprise PKI and RADIUS
In order to integrate a PKI with a RADIUS server, admins will need to complete 3 tasks. The first is importing the root and intermediate CAs onto the RADIUS server, which is already set up on SecureW2’s CloudRADIUS. Next, all network devices need to be configured for Server Certificate Validation so they only connect to RADIUS servers with domain-approved certificates. This requires onboarding software, which isn’t offered by all RADIUS server providers. Luckily, our PKI services include JoinNow onboarding software. The last task is configuring devices for Identity Lookup so the RADIUS server can refer to their directory to check a user’s status before authorizing network access.
SecureW2’s CloudRADIUS is an improved version of RADIUS because it’s powered by a Dynamic Policy Engine which revolutionizes the way organizations authenticate users and enforce policies. Dynamic RADIUS operates in fundamentally the same way as regular RADIUS, but it has one extra step: the RADIUS server to reference an entity’s directory entry, both to confirm that the entity is authorized for access, and to read any other user information there.
PKI + Access Points
This configuration is relatively easy because all you need to do is create a secure SSID that authenticates using WPA2-Enterprise with 802.1X EAP-TLS. Then, enter in the RADIUS IP address and shared secret in the SSID settings.
Configuring Microsoft Devices for PKI
In order to use certificate-based authentication, devices need to be enrolled for a certificate and configured for EAP-TLS 802.1x network authentication using their certificate. Neither of these tasks are simple, unless you use SecureW2’s JoinNow onboarding software.
BYODs
SecureW2’s JoinNow solution makes it easy for admins to onboard BYODs through certificate autoenrollment and Server Certificate Validation configuration. JoinNow is able to recognize any device on the market and automatically configure it for network access.
Managed Devices
SecureW2 provides Gateway APIs for admins to send out payloads to end user devices so they are enrolled for certificates and configured for 802.1X. Instead of manually configuring every single device or leaving it up to the end user, admins are able to issue a certificate to every managed network device. Plus, SecureW2’s Management Portal gives admins increased network visibility. If your organization uses Microsoft Intune, check out our article on integrating SCEP with Intune to deliver EAP-TLS certificates.
Managing Microsoft Certificates
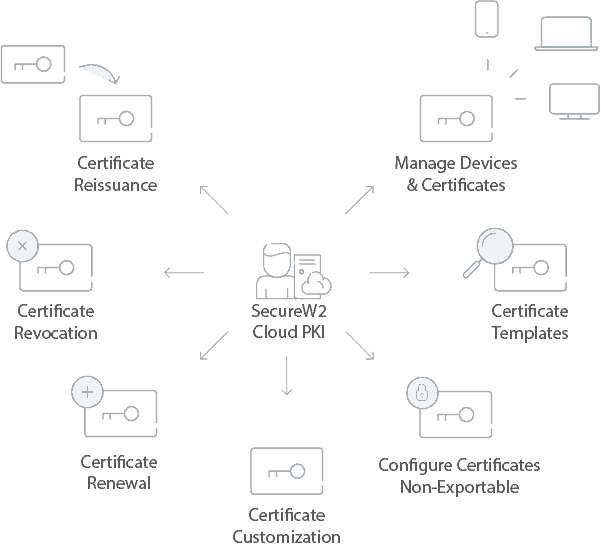
After devices have been configured for 802.1X and issued a certificate, the next part is managing issued certificates. SecureW2’s Managed PKI provides admins with CRLs, Identity Lookup, and the advanced Certificate Management GUI.
A Certificate Revocation List (CRL) is the standard used to notify the RADIUS server of all revoked certificates. While it’s an effective method, a long CRL can slow down authentication speeds.
One way to alleviate that concern is using a Base and Delta CRL. The RADIUS server can store a cached version of the “Base” CRL and only needs to use the Delta CRL for authentication. The Delta CRL contains all revoked certificates from the previous Base CRL update. Admins can even adjust Delta CRL update intervals in the SecureW2 Management Portal.
Identity Lookup allows admins to look up certain certificates and identify end users. Microsoft organizations can use Identity Lookup to verify active users by checking their information in AD. It used to be that only LDAP providers could use Identity Lookup, but SecureW2 expanded it to include SAML providers like Azure AD.
Our easy-to-use Certificate Management GUI simplifies all certificate management functions, and is much better than the logs of back in the day. Our GUI has loads of features like automated email notifications when a certificate is about to expire, custom certificate templates, manual revocation, and much more. Having a GUI also makes it straightforward for the Help Desk because all the attributes (MAC address, common name, computer model) are easily searchable.
Configuring a PKI for Microsoft can be an incredibly laborious task, unless you incorporate SecureW2’s Managed PKI and CloudRADIUS which can be implemented in a matter of hours and increased network security. Plus, our PKI services come at a much more affordable price.