Integrating Microsoft’s Group Policy Object (GPO) with RADIUS authentication effectively improves network security and access control. GPO enables administrators to apply policy settings for specific user groups, ensuring that individuals only have access to the required resources, preventing unauthorized access, and protecting internal systems. When paired with RADIUS, GPO improves authentication security and substantially controls network access.
For example, SecureW2 assisted an engineering firm in achieving passwordless Wi-Fi authentication by integrating certificate-based authentication with their identity platforms, such as Active Directory, Azure, and Google, streamlining the process for both Managed Devices (MDMs) and Bring Your Own Devices (BYODs). Read more. This integration improves security and delivers a consistent and efficient user experience across all devices and platforms.
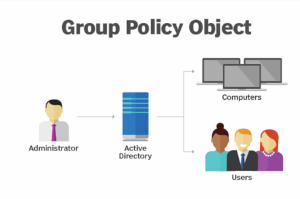
What is Group Policy Object?
A GPO is a pre-written task execution template, script, or command that can govern many Windows OS systems and policies. Microsoft Active Directory is the default management tool for GPOs and comes with them. System administrators may deploy GPOs to people, computers, or software across the whole organization using Active Directory.
System administrators may modify and customize using GPO, including registry-based policies, security settings, software installation and maintenance choices, script options, and folder redirection options. Simply put, GPOs allow administrators to remotely control whole fleets of hardware and software using Active Directory.
When used correctly, GPSs may strengthen an organization’s computer security by protecting against external and internal hackers and insider threats. GPOs can block users from accessing certain information or performing operations that could compromise vital systems or data, among other things. They can also assist in safeguarding your company’s network.
GPOs can be broadly classified into three categories:
Local GPOs:
A set of group policy configurations limited to the local machine and the users logged in to it. When policy settings need to be applied to only one Windows computer or user, local GPOs are utilized. By default, every Windows PC has a local GPO.
Non-local GPOs:
They are employed when policy settings need to be applied to one or more Windows users or machines. Once Windows PCs or users are connected to Active Directory objects like sites, domains, or organizational units, non-local GPOs take effect.
Starter GPOs:
Starter GPOs, which debuted in Windows Server 2008, are templates for Group Policy configurations. These objects help an administrator establish and maintain a collection of preconfigured settings that serve as a foundation for future policy creation.
Once you’ve determined which GPO types to deploy throughout your network, you should know the sequence in which GPOs are handled.
Group Policy and Intune Policy
Microsoft offers two policy management solutions: Although they target various devices and situations, they have certain commonalities. Let’s examine their features and differences:
Group Policy:
Within a Windows domain context, group policy, a Microsoft Windows Active Directory component, is used to manage and modify settings for users and machines. It is primarily designed for Windows-based devices, such as laptops and desktops, and gives administrators access to different parts of the operating system and apps. This is accomplished by applying settings based on Active Directory Organisational Units (OUs) using the Group Policy Object (GPO) architecture. When devices are linked to the on-premises Active Directory domain, Group Policy settings are implemented.
Intune Policy:
Intune Policy is a cloud-based mobile device management (MDM) and mobile application management (MAM) solution component of Microsoft Intune. It is intended to manage Windows 10 devices, including PCs and mobile devices like iOS and Android. Because it enables administrators to apply settings and rules over the air, it may be used with devices administered remotely or not connected to the local network.
Differences:
1. Device Types
Group Policy principally targets Windows-based PCs in an on-premises Active Directory domain. However, Intune Policy supports Windows 10 devices, including PCs and mobile devices (iOS, Android), both on-premises and remotely.
2. Scope of Management:
Group Policy is intended for an Active Directory system for on-premises management. Intune, on the other hand, is cloud-based and appropriate for remote and mobile device management scenarios since it enables over-the-air device administration.
3. On-premises vs. cloud-based:
While Intune Policy settings are maintained and deployed via the cloud-based Intune management dashboard, Group Policy settings are applied from on-premises Active Directory domain controllers.
4. Independence of Platforms:
Because Intune Policy is platform-independent, it can be used in various modern, heterogeneous IT settings and manage devices running different operating systems, such as Windows, iOS, and Android.
In conclusion, Intune Policy is intended to control mobile devices (iOS, Android) and Windows 10 devices on-premises and remotely through a cloud-based solution. Group Policy concentrates on managing Windows-based devices within an on-premises Active Directory domain. Organizations may manage a mixed IT environment with Windows and mobile devices by combining the two systems.
How are GPOs Processed?
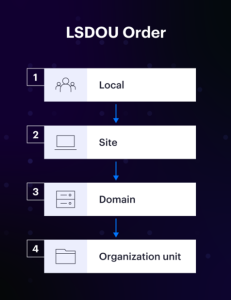
The processing of GPOs follows the LSDOU order, which stands for local, site, domain, and organization unit (OU). This implies that the local computer’s policy is processed first. Active Directory policies from the site to the domain level come next. The organizational unit is the target of the following processing order. When GPOs are nested inside organizational units, they start at the nearest OU and work outward. The most recent applicable policy will be prioritized and applied in the event of a disagreement.
Configuring group policy objects requires three stages.
The Group Policy Management Console (GPMC) typically creates, modifies, and deletes GPOs. GPMC is often present on domain controllers by default. If not, use the Install-WindowsFeature command line to install it on your radius servers easily. After gaining access to the GPMC interface, you can start configuring and setting up your GPOs.
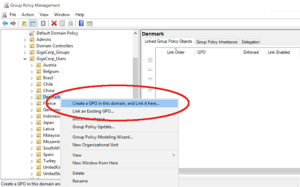
Link group policy to the domain in step one.
You can see your domain’s whole OU structure while you’re using the GPMC tool. A group policy must be linked to an OU to be applied. The policy will start to apply to users, devices, or clients in the associated OU and any sub-OUs as soon as you attach the GPO. Just right-click the OU to which you want the policy attached and take effect to establish a new GPO in GPMC. Next, choose “Create a GPO in this domain, and Link it Here.”
Go into settings and configure your GPO in step two.
After choosing the Create GPO option, a GPO will be generated to modify your preferred settings. Additionally, you should be aware of the distinction between the GPO link and the real GPO. The connection guarantees that the GPO is implemented on the appropriate people and/or devices throughout the OU. If you wish to reassign the OU, you can do so by deleting the link, but you must be careful not to remove the OU itself in the process. Furthermore, more than one OU can be connected to a single GPO. All linked OUs and linkages will be impacted when a single GPO is modified.
Configure the GPO appliance order in step three.
The sequence you want your GPOs to apply in the OUs to which they are connected should be configured last. As a general guideline, you should immediately refrain from setting up conflicting settings in your GPOs. When processing, GPOs with a lower link order—like 1—will take precedence over those with a higher one. Additionally, GPOs placed at a higher level OU will not take precedence over GPOs set at a lower level OU. Thus, establish the most crucial GPOs at the lowest link order and OUs, working your way down the list.
Using RADIUS Attributes to Apply Group Policies
RADIUS attributes allow wireless users to be subject to unique network regulations when used with group policies. To achieve this, a group policy set in the Dashboard may be named and used as a RADIUS attribute.
Requirements
This setup assumes that one or more group policies have been defined in the Dashboard and that an SSID has already been configured to carry out WPA2-Enterprise authentication using RADIUS.
Note: Only SSIDs that employ a local (customer-premise) RADIUS server for authentication at association time can have defined group policies for user groups.
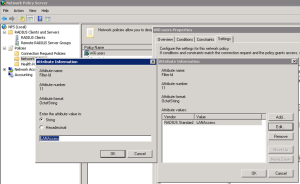
The name of a group policy specified in the Dashboard (as a String) must also be included in the attribute the RADIUS server configures to deliver with its accept message. For this, the Filter-Id property is typically utilized. The network policy in Windows NPS network policy that is set up to pass the name of a Dashboard group policy (“LANAccess”) within the Filter-Id attribute is seen in the picture below:
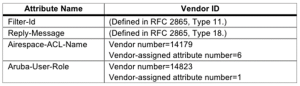
RADIUS Attribute Details
The following RADIUS attributes can be used to specify a group policy:
Dashboard Configuration
Following the completion of the aforementioned prerequisites, the Dashboard group policy will be linked to the defined RADIUS attribute through the subsequent setup steps:
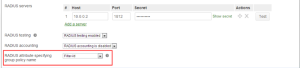
- Choose the proper SSID by navigating to Wireless > Configure > Access control.
- Choose the previously configured attribute under the RADIUS attribute that specifies the name of the group policy. The attribute utilized in the screenshot below is Filter-Id:
GPO Authentication Security with Credentials or Certificates?
Two primary methods are used for authentication security: credentials and certificates. Credentials are by far the most common, as they have been the standard for decades, but like most decades-old technology, they’re severely outdated. Credentials are incredibly easy to crack or steal, and many data breaches originate with poor password security. They simply cannot stand up to modern cybersecurity needs.
On the other hand, certificate authentication security is prepared to face the endless challenges cybersecurity professionals face. Credential-based EAP methods don’t stack up regarding authentication security compared to EAP-TLS. Certificates surpass credentials when looking at end-user experience, admin experience, and overall security. GPO can be easily integrated with 802.1X authentication methods to push out policy settings configured onto a user’s certificate.
Powerful RADIUS Authentication Security With GPO
Of course, to maintain internal network security, your authentication method must be ironclad. Providing a powerful RADIUS server to block outside access and enforce GPO policy settings is critical. If your organization authenticates users with certificates, a RADIUS is required to organize and protect the network.
Certificates are loaded with identifying information that the RADIUS analyzes to segment them into user groups. While this is undoubtedly a good security measure, it can be a hassle when an organization member needs updated network permissions. In the case of a promotion, a user will likely need new policy settings—and, in turn, new certificates. Re-issuing all new certificates for every device the user has isn’t exactly efficient.
With SecureW2’s Dynamic Cloud RADIUS, you can edit a user’s information in the IDP and update their policy settings in real time. Instead of replacing every certificate, Cloud RADIUS communicates directly with the IDP to grant the user authentication and access based on the new settings. This empowers you to easily apply your Azure AD Access Policies to your GPO-managed devices. The authentication process is secure throughout, and the user can access new resources immediately.
Managed devices can also be easily equipped with certificates and authenticated by the RADIUS. SecureW2 utilizes SCEP/WSTEP gateways to push out a certificate payload without interaction from the end user. The certificate is populated with the user’s information and GPO-based policy settings and is ready to authenticate the Cloud RADIUS. This can be used with GPO to auto-enroll devices for certificates and allows organizations to easily support certificate authentication with any MDM, such as Jamf, Intune, Workspace One, and more.
GPO and RADIUS Server Security Maximize Network Efficiency
Using Microsoft Group Policy Objects (GPO) with RADIUS authentication is a very effective way to improve network security and precisely control user access. Network administrators may protect internal resources from internal and external threats by using GPO to create detailed policy settings for various user groups. When paired with RADIUS, GPO guarantees strong authorization and authentication procedures. This is particularly true when utilizing certificate-based security, which is more effective at preventing breaches than standard credentials. This dynamic combination greatly improves an organization’s security posture and operational efficiency by enabling real-time upgrades and seamless policy enforcement throughout the network.
Check out SecureW2’s pricing page to see if our certificate solutions can equip your network with robust security and a streamlined user experience.