One of the main problems in online communication is trust. Let’s say you communicate with your bank through their website: how can you be sure the bank’s page is real and that a third party is not imitating it and attempting to steal your data?
Your device and the bank’s page need to establish trust. Trust is based on the fact that we can have a method to identify an entity correctly. When communicating over the internet, entities can use certificates as their identities. A digital certificate, defined in the Internet-standard X.509, is a secure method of guaranteeing the identity of entities that communicate online. It uses advanced and secure cryptography to provide an efficient way to work with users’ identities. The complex cryptography ensures that users are protected from outside threats when online.
This article will simplify certificates by covering the basics of root vs. intermediate certificates, certificate authorities (CAs), and why SSL/TLS certificates are widely used for internet browsing.
Client vs. Server Certificates
Before we define root certificates, intermediate certificates, and certificate authorities, let’s cover the difference between a client certificate and a server or SSL certificate. It’s pretty straightforward: The client certificate verifies the identity of the end-user device, and the server certificate verifies the server’s identity.
Let’s consider how the architecture of a web application works. It usually has a server where the application is stored and the functions to be executed behind it, as well as probably a database, among other elements. The web page, visual elements, and everything the end-user interacts with is part of the web client. This server-client relationship is also present in the way certificates are defined.
With this setup, we have a certificate at the server level and a certificate for the client. In this way, each certificate verifies the respective identities of both the server and the client. The client certificate verifies the end user’s identity, and the server certificate authenticates the site’s owner with whom we communicate.
For example, if we search Wikipedia, the domain name “www.wikipedia.com” has an SSL certificate that your web browser can use to verify that you are connecting to the Wikipedia page and not elsewhere.
What are Certificate Authorities (CAs)?
Certificate Authorities (CAs) are trusted entities responsible for issuing digital certificates. These certificates serve as digital passports, providing authentication and enabling encrypted connections between web servers and browsers. By verifying the identities of individuals and organizations, CAs help to create a trusted environment where data can be securely exchanged. They form the backbone of secure online communication, ensuring users can confidently navigate the web, engage in e-commerce, and exchange information without fear of interception or fraud. Through a rigorous validation process, CAs maintain the integrity and trustworthiness of the internet. Let’s now look into root certificates and intermediate certificates.
What are Root Certificate Authorities?
Root certificate authorities are the top-tier authorities in the certification hierarchy. They own the master certificates, the root certificates, that lie at the heart of trust for the internet. These root certificates are pre-installed in major browsers and operating systems’ trust stores, making them inherently trusted by devices worldwide. The trust model of root certificate authorities relies on the inherent trust placed in them by software manufacturers, application developers, and end-users. Their certificates are embedded into browsers and devices, making them automatically trusted by users worldwide.
Root CAs are established through a rigid and secure process that involves generating a unique root certificate. This root certificate’s private key must be guarded with the highest level of security, as its compromise could undermine the trust model of literally every certificate issued under its hierarchy. Despite their critical role, root certificate authorities are not without their limitations and vulnerabilities. The security of the entire trust model relies on the secure storage and handling of the root certificate’s private key. Any compromise could have far-reaching implications for online security.
What are Intermediate Certificate Authorities?
Intermediate CAs serve as the bridge between the root certificate authorities and the end-user or server certificates. They act under the authority of root certificate authorities but take on the day-to-day responsibilities of validating and issuing certificates to end entities. After performing the required checks and validations, they function by issuing certificates to entities or individuals.
They use a certificate signed by a root CA, which adds assurance that they are trusted to issue secure and valid certificates. Unlike root certificate authorities, intermediate CAs can be more freely distributed and do less risk to the overarching trust model if compromised due to their position in the certificate chain of trust being one step removed from the root CA itself.
Benefits of Using Intermediate CAs
Using intermediate CAs offers several advantages. They reduce the risk to root CAs by acting as a buffer. If an intermediate CA is compromised, its certificate can be revoked without affecting the root certificate authorities or other intermediate certificate authorities. This structure also allows for more flexible management and distribution of certificates, enabling businesses and organizations to issue their certificates under the guidance of an intermediate CA without direct interaction with the more sensitive root CA.
What is the Relationship Between Intermediate CAs and Root CAs?
The relationship between intermediate CAs and root CAs is symbiotic. While root CAs provide the ultimate source of trust, intermediate CAs extend the reach of this trust by issuing certificates down the certificate chain. This structure allows for scalability in issuing certificates, with the root CA only needing to manage a relatively small number of intermediate CAs directly.
The Chain of Trust
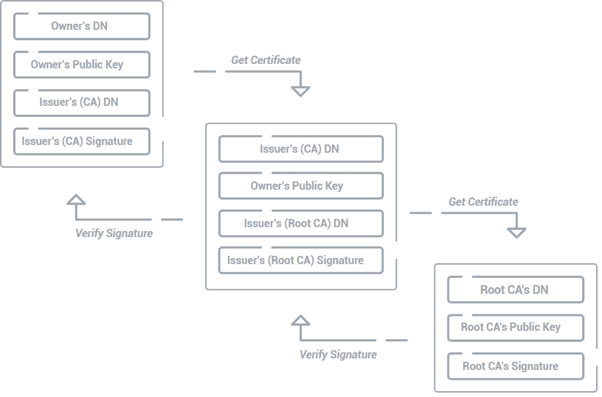
In a public key infrastructure (PKI), certificates are issued in a very specific order in what is known as a Trust Chain. A chain of trust is a series of certificates linking an end-user or server certificate to a trusted root certificate. This chain ensures that any given certificate is legitimate and can be traced back to a root CA that is widely recognized and trusted. CAs build the certificate chains by issuing certificates signed with their private key. When a certificate is verified, the signature is checked against the public key of the issuing CA. If it matches, the process continues until it reaches a root certificate authority recognized by the device’s trust store. The diagram below shows us a certificate chain and how each aspect is featured.
How do Root Certificates Establish Trust?
Root certificate authorities lie at the foundation of the trust model. Their root certificates are the ultimate source of trust, against which all other certificates are validated. Since these root certificates come pre-installed in trust stores of major browsers and operating systems, any certificate chain that links back to these root CAs is considered valid. This foundational trust is why root CAs operate under extremely strict guidelines to ensure the security and integrity of the root certificates they issue.
How Intermediate Certificates Extend Trust
Intermediate CAs extend this trust by issuing certificates to end entities while being directly linked to a root CA. This extension allows for a more flexible and secure distribution of certificates. It also enables root CAs to keep their keys more secure by not using them frequently, which reduces the risk of compromise. Intermediate CAs act as a buffer, taking on the risks of certificate issuance while protecting the root certificate’s integrity.
Differences Between Root and Intermediate CAs
Now let’s look at the difference between root and intermediate CAs:
| Root CAs | Intermediate CAs | |
| Authority and Hierarchical Position | At the top of the certification authority hierarchy; they have the ultimate authority. | Sit below root CAs in the hierarchy; they derive their authority from a root CA. |
| Trust and Certification Paths | Serve as the starting point of trust; their root certificates are directly installed in trust stores. | Extend trust; their intermediate certificates are not directly installed in trust stores but are trusted through their chain back to a root CA. |
| Issuance Policies and Constraints | Subject to the most stringent issuance policies due to their foundational role in trust. | Operate under policies set by the root CA, with some flexibility based on the scope of their issuance. |
| Security Measures and Practices | Employ the most rigorous security practices to safeguard their private keys and root certificates. | Also maintain strong security measures but operate under the oversight of root CAs. |
| Scope of Issued Certificates | Typically do not issue root certificates widely; their primary role is to create intermediate CAs. | Actively issue intermediate certificates to end entities like websites, email servers, and users. |
| Audit and Compliance Requirements | Undergo the most strict audit requirements to ensure their operations and security measures are impeccable. | Subject to rigorous audits as well, but the focus is more on how they manage issuance and maintain the chain of trust. |
| Vulnerability and Compromise Impact | A compromise can have widespread implications, potentially undermining trust in a wide array of services and applications. | While a compromise is severe, its impact can be more contained, and the intermediate CA can be more easily replaced or its certificate revoked. |
SecureW2: Simple PKI Certificate Management for You
SecureW2 offers an end-to-end public key infrastructure service that significantly simplifies the management of certificate authorities, making it easier for organizations to deploy and maintain a robust security framework. With capabilities that include the automation of certificate issuance and renewal processes, SecureW2 ensures that the chain of trust remains unbroken and secure across all user devices and applications. This managed service eliminates the traditional complexities associated with certificate management, such as manual certificate signing requests (CSRs), enrollment, and installation, thereby reducing the incidence of misconfigured certificates and vulnerabilities.
SecureW2’s Cloud PKI as a Service that Seamlessly Fits Your Environment
SecureW2’s cloud-based PKI solution integrates seamlessly with existing directories, does not require any hardware, and offers a user-friendly experience, making it ideal for organizations of any size looking to bolster their security posture. By leveraging SecureW2’s Managed PKI, organizations can ensure that their Root and Intermediate CAs are managed efficiently, aligning perfectly with this article’s focus on creating a trustworthy and secure internet environment. Check out our pricing page for more information.