Key Points
- Connect Active Directory to Wi-Fi using 802.1x and certificate-based authentication for stronger security.
- Move from password-based logins to EAP-TLS certificates with Cloud RADIUS for zero trust and seamless access.
- Implement Cloud RADIUS with Managed PKI to automate certificate issuance, enforce dynamic network policies, and reduce IT intervention.
Organizations that leverage Microsoft Active Directory (AD) often want to connect their core user identities to their Wi-Fi network. The goal is to enable users to authenticate uniquely to the network in order to increase security.
The best practice for secure authentication is using 802.1x, which requires a RADIUS server to authenticate users and authorize access levels. The most common RADIUS setup for Windows networks is Microsft NPS, for obvious reasons. But as organizations continue to move to cloud-based operations, NPS has become a less favored solution. NPS and AD do not come inherently with a cloud solution, so choosing the right add-on solution to enable cloud-based authentication is key.
Modern 802.1x deployment solutions allow admins to leverage digital certificates for authentication instead of passwords. For this, a Public Key Infrastructure (PKI) must be set up to administer and manage certificates. This can be easy to do with a Managed PKI, like SecureW2’s Cloud PKI that also comes with Cloud RADIUS. Read about how one of our customers switched from their on-prem AD servers to a full cloud infrastructure without any forklift upgrades.
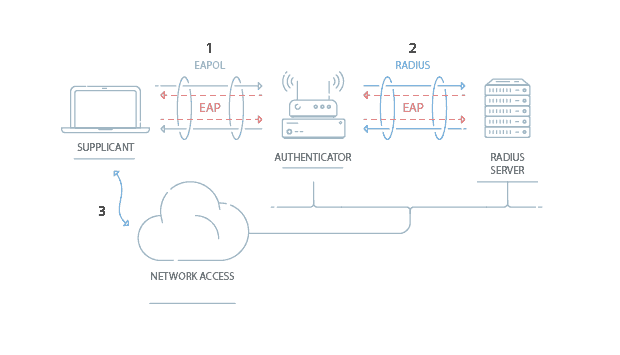
802.1x Authentication with Active Directory
IEEE 802.1x is a networking protocol that defines the standards for port-based network access control (PNAC). The most common implementations use a RADIUS server as the authentication server. A RADIUS Server checks Active Directory during authentication to confirm that the client’s credentials are valid. At the same time, the RADIUS server can apply any access privileges or group policies to segment network access.
The RADIUS server can also be configured to authenticate certificates, instead of credentials. In order for this to work, the RADIUS server needs to be equipped with the Certificate Authority (CA) that has issued the client certificates the devices are using for network authentication.
In order for credential-based RADIUS server authentication to work, the RADIUS needs access to the organization’s directory, which is usually done through a SAML or LDAP protocol. However, if you replace passwords with x.509 certificates for authentication, the RADIUS server doesn’t have to be connected to your directory.
PEAP-MSCHAPv2 is the authentication protocol used with Active Directory and RADIUS servers, but recent issues with the protocol have caused a lot of organizations to switch to certificate-based authentication. Let’s go over the main authentication protocols.
Configuring Wi-Fi Authentication: Which Protocol to Use
EAP-TTLS/PAP
EAP-TTLS/PAP is a credential-based protocol that was created for an easier setup because it only requires the server to be authenticated, while user authentication is optional. TTLS creates a “tunnel” between the client and the server and gives you multiple choices for authentication. But TTLS includes many vulnerabilities.
The configuration process can be difficult for inexperienced network users, and a single misconfigured device can result in significant loss to the organization. The protocol allows credentials to be sent over the air in Cleartext, which can be vulnerable to cyber attacks like Man-In-The-Middle and easily repurposed to accomplish the hacker’s goals. This makes TTLS/PAP the least secure 802.1x authentication protocol and fails to meet the zero trust standard.
PEAP-MSCHAPv2
PEAP-MSCHAPv2 is another credential-based protocol that was designed by Microsoft for AD environments. Although it’s the usual protocol for WPA2-Enterprise authentication, PEAP-MSCHAPv2 does not require the configuration of server-certificate validation, leaving devices vulnerable to Over-the-Air credential theft.
While PEAP is more secure than TTLS/PAP, it still requires end user interaction. When left to the end users, device misconfiguration is relatively common, which is why most organizations rely on Onboarding Software to configure devices for PEAP. The best 802.1x protocol requires little to no end user interaction.
EAP-TLS
EAP-TLS is a certificate-based protocol that is widely considered one of the most secure EAP standards because it eliminates the risk of over-the-air credential theft. EAP-TLS fits perfectly into the zero trust model because users can be verified by their certificates instead of typing in their login credentials every time.
It’s also the protocol that provides the best user experience, as it eliminates password-related disconnects due to password-change policies. In the past, there was a misconception that certificate-based authentication was difficult to set up and/or manage, but now EAP-TLS is regarded by many to actually be easier to set up and manage than the other protocols.
The RADIUS implementation is just as important as the authentication protocol, so it’s imperative to choose a RADIUS solution that follows the zero trust model. Next, we’ll break down the most common RADIUS integrations and how they each compare for zero trust access.
Setting up a RADIUS Server for Active Directory Wi-Fi Authentication
Microsoft NPS
NPS has been a staple for institutions using Active Directory for 802.1x. It is commonly accomplished using EAP methods, such as PEAP-MSCHAPv2 or EAP-TLS because these methods use a server certificate. Users can be easily tricked into sending authentication information to the wrong RADIUS if they fall victim to an attack known as a Man-in-the-Middle attack.
If their RADIUS employs server certificate validation, the user’s device will check for the RADIUS server certificate and validate that this is the correct server to authenticate to. Using password-only authentication and not checking for the server certificate can easily lead to unauthorized entry by an outside actor who has farmed network credentials.
FreeRADIUS and OpenLDAP
FreeRADIUS is an open-source RADIUS service that gives admins the most freedom because they can configure RADIUS for any functions they choose for their environment. OpenLDAP is the same in that regard as it’s also an open-source service to implement LDAP. While this gives admins the most freedom to configure their environment, that means admins have to implement FreeRADIUS/OpenLDAP by themselves. It’s relatively easy for a seasoned IT member, but will they have the time to implement this change.
Many IT staff have the capabilities of configuring open-source software for their environments, but just as many IT staff are bogged down with other tasks, namely support tickets. Plus, getting end users on board with new features is easier said than done. The best practice is a cloud-based RADIUS solution that’s monitored 24/7 by reliable staff.
Cloud-based RADIUS
Thousands of customers are moving away from implementing and managing their own RADIUS server for a cloud-based option. Cloud-based RADIUS solutions succeed where their on-prem and FreeRADIUS counterparts fail: easy implementation, cost-effective, and strong security measures.
A Cloud RADIUS server saves an organization thousands of dollars because it’s less than a third of the cost of the equivalent on-premise servers. There are no hardware and associated costs and no physical installation required. The IT department is relieved of the time-consuming labor involved with the implementation and management of the servers. There’s also no man-hours or training required for maintaining the server, critical as the RADIUS server can never go down.
This is why SecureW2 created Cloud RADIUS, a turnkey RADIUS solution that can be implemented into virtually any environment because it works with all major SAML and LDAP Identity Providers like Google, Okta, and Azure. Designed from the ground up for certificate-based authentication, it eliminates the risk of sending credentials over the internet and eliminates the risk for credential theft.
Cloud RADIUS is the only RADIUS Server that comes with an industry-exclusive Dynamic Policy Engine that integrates natively with Azure and Intune, empowering organizations with certificate-based authentication for ultra-secure Wi-Fi and VPN authentication.
Security and user experience are bolstered by Cloud RADIUS because it performs digital certificate-based authentication and comes set up with SecureW2’s Managed Cloud PKI. Our PKI gives admins the ability to effortlessly deploy WPA2-Enterprise with 802.1x authentication, the gold standard for wireless security. Everything you need for certificate-based authentication can be set up in under an hour!
Configuring MFA for Wi-Fi Authentication
Can I set up MFA with Active Directory?
It’s not easy to seamlessly integrate MFA into IT resources with Active Directory, even when it comes to Windows machines and especially non-windows machines.
Unfortunately, having an Active Directory instance set up as your core IdP isn’t enough to enable MFA. In order to do that, you’ll need an additional application or service to add those capabilities, both to AD and your individual IT resources. Generally, the way this will work is to enable MFA at the point of login on the Windows machine. Since the Windows machine login is basically the gateway to access everything within the domain, you would add a second step here by forcing MFA. Unfortunately, Microsoft doesn’t do this natively with AD, so you’ll likely need an add-on solution.
Does Azure AD provide MFA capabilities?
You can use MFA on an Azure AD Free subscription if you elect the per-user or per-authentication billing/usage model. This is basically the minimum Azure setup you’ll need to enable MFA.
However, Azure’s MFA extends only to certain web apps, so it can’t be used in conjunction with managing all Windows machines, on-prem apps, file servers, or networks. It is not really a replacement MFA option when logging into the domain with AD. If you have accounts that belong to a global administrator role in Azure AD, you can activate Azure MFA for free, but it’s only free if the account you’re setting it up for is a “Work” or “School” account.
Configuring Certificates with MFA
We often receive questions about using MFA for Wi-Fi authentication, but currently, it is not supported by 802.1x protocols. If your network authenticates users with a RADIUS server, the technology to implement MFA does not exist.
If it does become an option in the future, it would be difficult to justify using MFA for that purpose. The costs associated would be high, and the time-consuming user experience would be a common complaint. Entering multiple levels of authentication every time a user connects to the network would be a hassle and could lead to users browsing with personal data or on insecure networks.
For Wi-Fi authentication, a highly recommended option is the use of certificates with onboarding software. This allows users to configure their devices in minutes to be authenticated by the RADIUS, and they never have to enter credentials to get on the network. MFA could be a step in the certificate enrollment process.
Using Windows Certificates for Wi-Fi Authentication
Should I Use Active Directory Certificate Services?
It’s understandable why Microsoft clients who want to deploy certificates would choose AD CS and an on-premise PKI to fully integrate their AD, but in doing so they are adding extra work for their IT department and authenticating with sub-par protocols. In essence, an on-prem PKI is more work and expenses for less security and capabilities.
On-premise PKIs are incredibly expensive to set up because there are so many components to include, each with its own price tag. Enterprises need to pay for hardware and software implementation, maintenance fees, software licensing, secure hardware storage, data backup, disaster recovery, and much more. All of these expenses often come as hidden costs, meaning enterprises aren’t aware of these costs until it’s too late.
All of this planning and setup means that on-premise PKIs take months to fully implement, and we haven’t even discussed personnel. Once an enterprise has decided to deploy an on-prem PKI, they will need to hire and train a team of cryptography and server experts. Training current employees means more work for the IT department and can lead to faster employee burnout. The administrative and HR costs of hiring new employees add up as well. The overall expense of an on-prem PKI makes it an illogical investment.
Using a Cloud-based PKI Service
Managed PKIs are far better for Microsoft environments because they do not require time-consuming implementation and are a fraction of the price of on-prem. Since it’s all on the cloud, there’s no need to overhaul infrastructure, relieving IT departments from the extra workload and saving the enterprises hundreds of thousands of dollars.
Personnel costs are also greatly reduced because enterprises using a managed PKI only need one part-time employee to cover PKI management instead of an expensive team of experts.
Migrate from Active Directory to Azure Cloud
AD has cornered the market in online directories, but with the adoption of cloud-based solutions AD’s on-prem infrastructure has become a hindrance for many organizations trying to migrate to the cloud. SecureW2 cloud services include a cloud PKI to distribute every user a certificate and Cloud RADIUS to authenticate and authorize users based on their certificates.
With our Dynamic Policy Engine, every time a user is authenticated for network access, admins can enforce network policies in real-time. Cloud RADIUS automatically checks user status, what groups they’re in, if they’ve changed departments, and ties them to custom network policies created by administrators in our easy-to-use management system. All the benefits of historic LDAP authentication, with none of the risks associated with credential-based authentication.
With SecureW2 you can have your secure network set up in a matter of hours and have a support team ready to assist you with any of your questions. Check out our pricing page to see if our solutions can help secure your network.