Key Points
- The DoD PKIs directory management is challenged by its massive scale, lack of granular access control, and issues with distributing large certificate revocation lists in tactical environments.
- To address these challenges, the DoD is evolving its PKI architecture to be more centralized for policy enforcement and more decentralized for certificate management.
- A Managed Cloud PKI offers a modern solution that can enhance the DoD's efforts by providing a low-maintenance, automated platform for passwordless authentication.
The Department of Defence Public Key Infrastructure (DoD PKI) is a vital component in strengthening the Department of Defense’s (DoD) digital communications and data-sharing infrastructure. Fundamentally, DoD PKI is an advanced system designed to protect data integrity throughout military networks and systems, authenticate users, and encrypt sensitive data. This infrastructure, which consists of intricate components and procedures, is essential to maintaining the privacy, availability, and integrity of sensitive data necessary for national security.
Learn how SecureW2 helped a healthcare provider seamlessly deploy a cloud-based 802.1X network with Cloud RADIUS and PKI, enhancing security for managed and BYOD devices.
This article will investigate DoD PKI, its various uses, complex operations, ongoing difficulties, and possible solutions that might influence its future.
Understanding DoD PKI
The Department of Defence issues DoD certificates to individuals and non-person entities (such as web servers, network devices, routers, and apps) to support DoD missions and commercial operations. The DoD PKI (Public Key Infrastructure) operates on the Sensitive but Unclassified Internet Protocol Network (NIPRNet) as a hierarchical system with a Root Certification Authority (CA) at the top and several issuing CAs that provide scalability and disaster recovery. This PKI offers certificates for Common Access Cards (CACs) and software certificates to meet application requirements.
The Department of Defence (DoD) operates CAs on the Secret Internet Protocol Network (SIPRNet) through the National Security System (NSS) PKI DoD Root CA, which serves all federal agencies with users or systems on secret networks. The NSS PKI offers certificates for the SIPRNet hardware token and software certificates to meet application requirements.
The DoD PKI and the DoD part of the NSS PKI are centralized infrastructures for managing keys and certificates throughout their lives (from issue to revocation or expiration). These infrastructures enable directory services that supply CA certificates, certificate revocation information, and user encryption certificates.
The architecture of DoD PKI
DoD PKI (Public Key Infrastructure) is the foundation of Information Assurance, providing secure data transfer across the Global Information Grid while protecting crucial information locally. It oversees various functions, from creating and distributing public key certificates to maintaining, revocating, and monitoring private keys. These private keys, which are required for identification and encryption, are housed in smartcards, which look like credit cards but include microchips. This sophisticated system is based on commercial off-the-shelf hardware and software, with NSA-specific applications added.
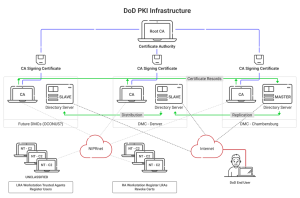
Systems such as the Defence Enrollment Eligibility Reporting System (DEERS) and Secret DEERS, which provide personnel data for certifications, as well as Certification Authorities headquartered inside the Defence Information Systems Agency (DISA) Enterprise Service Centres, are critical to its operations. The evolution of DoD PKI occurs in stages, with Increment 1 already implemented on the NIPRNet and Increment 2 in the works, promising improved access for members, coalition partners, and other stakeholders. Furthermore, deploying NPE certificates signals the formation of painstakingly specified network domains, critical for improving intrusion protection and detection procedures.
External Certification Authority (ECA) PKI
The Department of Defence launched the External Certification Authority (ECA) program to let industry partners and other external individuals and organizations get DoD-approved PKI credentials they would not otherwise have access to. DoD PKI certificates provided under the ECA program enable these businesses to securely connect with the DoD and authenticate against DoD Information Systems. The ECA PKI comprises a DoD root CA maintained at the same facility as the DoD PKI Root CA and subordinate CAs that authorized vendors manage. The ECA Program website provides further information on the program.
DoD Approved External PKIs
Current regulation mandates that all federal agencies provide Personal Identity Verification (PIV) cards to their employees and affiliates. Some of DoD’s industrial partners have established internal PKIs (Public Key Infrastructure), while others have obtained certificates from commercial PKIs. In addition, several of the Department of Defense’s overseas allies and coalition partners have developed PKIs to issue and install certificates for their people. As a result, the DoD has adopted an external interoperability strategy that relies on certificates issued by external PKIs that fulfill DoD standards for safe information sharing with external partners.
The following are examples of DoD-approved external PKIs on NIPRNet:
- External Certification Authority (ECA) supported by the DoD.
- Issuers of PIV certificates by federal agencies.
- Commercial PKI whose operating organizations have executed Memorandums of Agreement with the DoD, whose operating organizations have been tested for interoperability by the DoD Joint Interoperability Test Command (JITC), and whose certification by the Federal PKI Policy Authority as satisfying their Medium Hardware requirements.
- Other partner PKIs expressly authorized by the DoD include those Combined Communications Electronics Board (CCEB) members.
DoD-approved external PKIs on SIPRNet include the following:
- Federal agency CAs that are a component of the NSS PKI and run under the NSS PKI Root CA
- Other partner PKIs expressly authorized by the DoD for interoperability on secret-level networks include PKIs from CCEB member nations.
- The IASE website’s External and Federal PKI Interoperability page lists every NIPRNet DoD-approved external PKI and provides further details, such as permissible certificate assurance levels, certificate trust chains, and other helpful data.
Applications of DoD PKI
DoD Public Key Infrastructure (PKI) is more than just a technology framework; it provides the foundation for secure military communications and operations. Increment 2 of DoD PKI exhibits this by offering a strong cryptographic capability, permitting DoD members and authorized staff access to the highly secure Secret Internet Protocol Router Network (SIPRNet) and allowing them to encrypt and sign emails. This incremental improvement builds on the success of Increment 1, which improved access to the Non-secure Internet Protocol Router Network (NIPRNet) using Common Access Cards (CACs).
The impact of DoD PKI extends beyond traditional network security. It includes the issue of SIPRNet tokens, which are sophisticated electronic IDs that allow safe resource access across many SIPRNet nodes. Once fully implemented, authorized users and Non-person entities (NPE) enabled devices can easily access restricted websites and access online services. Despite operational effectiveness and logistics obstacles, DoD PKI remains critical for commanders, allowing them to validate identities using CACs or SIPRNet tokens. This authentication grants DoD members, coalition partners, and others access to restricted resources, internet services, and encrypted communication channels.
Furthermore, DoD PKI plays an important role in strengthening military network infrastructure. It improves intrusion detection and security by making creating fully recognized network domains easier using NPE certificates. As DoD PKI matures, tackling difficulties and embracing technological breakthroughs, its role in protecting military operations and national security grows, guaranteeing a future of robust and secure military communications.
Challenges in DoD PKI Directory Management
The DoD Public Key Infrastructure (PKI) directory is complicated since certificates are required for every DoD member, contractor, and vendor. This requires a potentially enormous centralized directory with millions of entries, which presents substantial administrative issues. One way to address this issue is to use a meta directory to supervise numerous smaller directories, allowing replication approaches to ease maintenance. However, questions are raised about foreign organizations’ readiness to allow access to their directories, thus undermining the benefits of a meta directory.
A further challenge is managing attributes and controlling access. Standard features such as unique directory names cannot provide granular access control. Role-based or need-to-know characteristics need standardized and centrally controlled systems, which raises concerns about attribute modifications and certificate administration, especially in a dynamic military setting. Alternative options, such as attribute certificates or trusted directories, provide additional difficulties and downsides that affect certificate administration and access control procedures.
Universal Security Clearance Policy and Sophisticated Threats
Implementing a universal security clearance strategy, in which everyone gets a certificate, introduces security vulnerabilities and reduces granular access control. Furthermore, competent adversaries might use weaknesses in PKI, such as compromised certificates or encrypted email, for nefarious purposes. Concerns are also raised about tactical operations, where limited bandwidth and large CRL (Certificate Revocation Lists) files hamper certificate dissemination. Tactical Certification Authorities (TCA) provide logistical issues, such as duplicating functions and losing control of certificates in fast-paced contexts.
Possible Solutions
Policy changes, such as removing the need for individual encryption certificates, can reduce misuse and administrative overhead. Reorienting the PKI architecture towards decentralized certificate management and centralized policy enforcement improves scalability and security. Furthermore, integrating single-sign-on capabilities via client apps or smart cards streamlines access control while resolving security issues. These solutions compromise security needs and operational efficiency, resulting in reliable PKI deployment across various military contexts.
Advantages of SecureW2’s Managed Cloud PKI
SecureW2’s managed cloud-based PKI as a service provides a seamless solution for organizations that want strong security without the hassles of traditional on-premise PKI solutions. SecureW2 provides robust PKI administration tools that enable safe, passwordless authentication for Wi-Fi, VPN, Single Sign-On, and other applications.
The platform streamlines certificate administration by automating the entire process, from issuance to revocation. It seamlessly integrates with various device management systems and supports managed and BYOD settings, ensuring that all devices are securely authorized. SecureW2 delivers a dependable, low-maintenance PKI solution that improves security while lowering expenses and administrative overhead.
Not only does SecureW2’s managed cloud-based PKI have many capabilities, but our committed support staff also provides outstanding customer service. Our professionals help at every stage, from initial setup to continuous maintenance. They guarantee a seamless and effective deployment by offering individualized assistance and troubleshooting. Our support staff ensures businesses get the most out of SecureW2’s solutions and improve network security with the least hassle or disturbance possible.
The Vital Role of DoD PKI and Innovative Solutions
The Department of Defence Public Key Infrastructure (DoD PKI) protects military communications and data transmissions. It includes comprehensive techniques for data encryption, user authentication, and sensitive information security on both the NIPRNet and the SIPRNet. Despite its complexity and challenges, such as directory management and emerging security threats, DoD PKI is still critical for ensuring the integrity and secrecy of national defense activities.
Adopting solutions like SecureW2’s managed cloud PKI can provide considerable benefits by streamlining PKI administration and improving security through automated certificate management and passwordless authentication. Integrating modern PKI solutions is a smart decision for organizations wishing to boost their digital security infrastructure with the least trouble.
Contact us to learn how our solutions help safeguard your organization’s communications.