Ensuring network users are able to securely authenticate to the wireless network is paramount to the overall safety and security of your organization. So many attacks are aimed at exploiting the authentication process. According to IBM’s X-Force Threat Intelligence Index, 35% of exploitation activity involves Man-in-the-Middle Attacks.
The most widely used wireless network protocols today are the Extensible Authentication Protocols (EAP) used in WPA2-Enterprise. Utilizing an EAP authentication method ensures that users’ information is sent over-the-air using encryption and avoids interception. Read here how SecureW2 helped a marketing firm provide comprehensive authentication security for all their personal and managed devices.
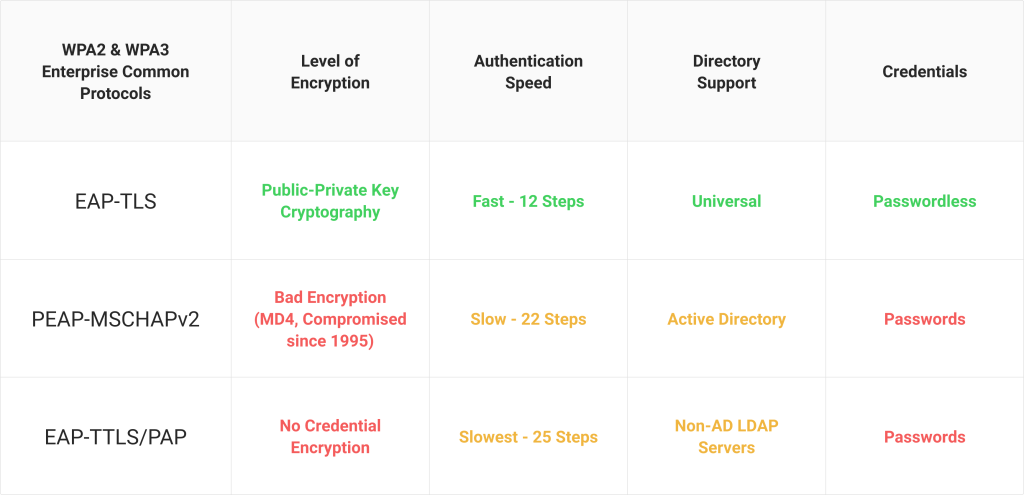
Two of the most common EAP methods, EAP-TLS (SecureW2 provides everything an organization needs for EAP-TLS) and PEAP-MSCHAPv2, are commonly used and accepted as secure authentication methods, but how do they work? And how do they differ in providing security?
Configuration of the Secure EAP Method
While the configuration process for both EAP-TLS and PEAP-MSCHAPv2 is different, they have one thing in common; you should not allow users to manually configure their devices for network access. When left to their own devices, the average network user has ample opportunities to misconfigure their device, leaving them open to MITM and Evil Twin attacks.
The process for EAP-TLS involves enrolling for and installing a digital certificate, and both protocols require server certificate validation configuration in order to remain effective against over-the-air credential theft attacks. And this hardly covers all the steps involved. For the average network user, the process is complicated for both and manual configuration should be avoided at all costs.
To bypass the support tickets and security risks of manual configuration, it’s recommended that you deploy onboarding software to automatically configure new users. SecureW2’s JoinNow onboarding solution configures users accurately within a few steps. They simply identify themselves and once approved, their devices are securely configured for network access using EAP-TLS or PEAP-MSCHAPv2 authentication. The process is fast, simple, and ensures all users are correctly configured.
Authentication With EAP-TLS and PEAP-MSCHAPv2
Both protocols are considered EAP methods, so they each send identifying information through the encrypted EAP tunnel. This encrypted tunnel prevents any outside user from reading the information being sent over-the-air.
However, the process for the end-user differs significantly between the two protocols. With PEAP-MSCHAPv2, the user must enter their credentials to be sent to the RADIUS Server that verifies the credentials and authenticates them for network access. EAP-TLS utilizes certificate-based authentication. Rather than sending credentials to the RADIUS Server over-the-air, credentials are used for a one-time certificate enrollment, and the certificate is sent to the RADIUS server for authentication.. Over the course of the user’s lifetime with the organization, being able to auto-authenticate without having to memorize a password or update due to a password change policy is a huge benefit to the user experience.
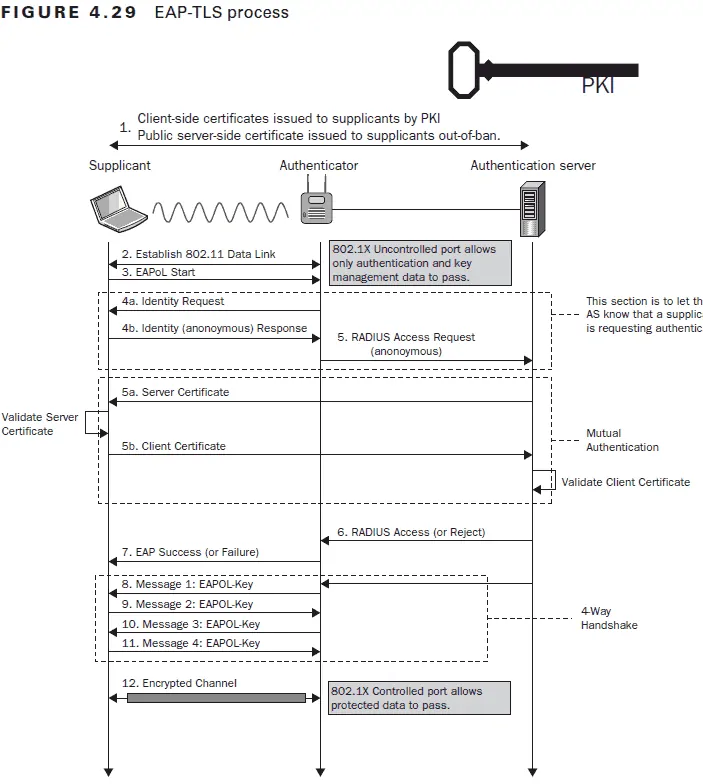
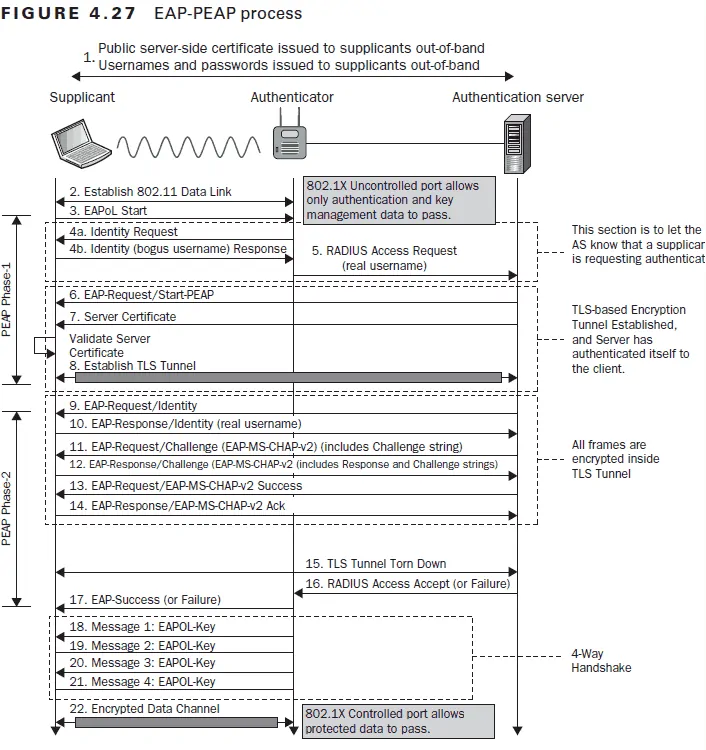
While the information exchanged between the client device, Access Point (AP), and RADIUS server may be different between EAP-TLS and PEAP-MSCHAPv2, they both undergo a TLS Handshake. This is the communication process in which the server and client exchange identifying information. The two sides will verify one another’s identity, establish encryption algorithms, and agree on session keys to securely authenticate to the network. Below are images from the Certified Wireless Security Professional Study Guide detailing the process for both authentication protocols.
The primary difference to highlight between the authentication processes above is the number of steps involved. The EAP-TLS process has almost half as many steps to authenticate.
On an individual authentication basis, this is an extremely short amount of time difference. For a single authenticating user, the difference is nearly imperceptible. Where this difference of steps comes into play is during the event of a large authentication event.
If there is a situation where a large number of users are attempting to authenticate at the same time, the shortened process becomes a significant advantage. There’s a much smaller chance of a slowdown in authentication occurring. Additionally, if your RADIUS is overloaded with authentication requests and does not have redundancy measures, your network could experience request denials and time-consuming delays. For the sake of productivity, a shorter process can make a big difference.
The Risks of Each Authentication Method
Comparing the security risks of certificate-based authentication and credential-based authentication reveals that certificates are far more secure than credentials. From an identity standpoint, credentials are not reliable. Certificates cannot be transferred or stolen because they are linked to the identity of the device and user; meanwhile, stolen credentials can be used without a method for identifying if the authenticated user is actually who they claim to be.
Beyond identity issues, there are several attack methods for stealing valid credentials. A man-in-the-middle attack can be used to farm credentials from users authenticating to the incorrect network. A dictionary attack can be performed remotely by sending countless authentication requests until the correct password is sent. And phishing is an extremely common psychological attack method to trick users into giving up their passwords. Overall, weak passwords and simple hacking attacks can threaten the integrity of a secure network.
Keep in mind that your network is comprised of multiple interconnected parts. A hacker can steal one set of credentials and begin digging deeper into your network from there. This issue is worsened by the fact that the majority of people reuse their passwords; capturing one set of credentials can be like snatching a master key that bad actors can use to access additional resources and wreak havoc on an organization-wide scale.
In contrast, certificates cannot be stolen over-the-air or used by an outside actor. They are protected with private key encryption and cannot be used by another device. The only legitimate exploit to get around certificate security is a convoluted process where the hacker impersonates an employee and tricks a PKI vendor to distribute them a valid certificate. The process is extremely difficult and can be avoided by venting your vendor and ensuring they use basic security best practices.
Add Device Context for Network Authentication with SecureW2
While both EAP methods protect the data being sent over-the-air, they differ in overall security, efficiency, and user experience. EAP-TLS with certificate-based authentication is simply more secure and offers a superior user experience with benefits in efficiency and protection.
You get more context with digital certificates, increasing your capacity for device trust; a certificate can show you a number of factors, including a person’s role in the organization, their operating system, and when the operating system was last updated. As an example, you can refer to the illustration above to see the information a certificate provides you as opposed to the information you can gather from credential-based authentication.
If you’re looking for the gold standard for authentication, SecureW2 offers a turnkey EAP-TLS solution that includes device onboarding software, Managed PKI Services, and a Cloud RADIUS Server. Check out our pricing page to see if SecureW2’s solutions are a fit for your organization.