Key Points
- Active Directory (AD) is Microsoft’s hierarchical directory service that centralizes storage and access to users, devices, files, servers, and more across corporate networks
- AD is built on modular components—AD DS (core directory and authentication services), AD CS (certificate issuance), AD FS (single sign-on), and AD RMS (data rights protection)
- Its structure—including objects, OUs, domains, forests, and trusts—allows flexible hierarchy, granular control, and domain-to-domain access management.
Directory servers make it easy for admins to store and access resources including user and device information, computers, files, server, and much more.
Back in the old days, in order to look up a file, a user needed to know the file name, the server its on, and the folder pathname. This is troublesome for organizations with thousands of users and devices. Luckily, online directories allow users to locate resources from anywhere. Active Directory is the most popular online directory.
What is Active Directory?
Active Directory (AD) is a directory service by Microsoft that started back in 2000 and has since exploded with over 90% of organizations using it. AD is structured like a hierarchy for efficient data storage and retrieval.
Similar to a physical directory with contact information, AD is a digital directory service that allows admins and users to search for resources (files, printers, computers, servers) stored anywhere on the network.
What Services Does AD Provide? AD DS
AD DS
Active Directory Domain Services (AD DS) describe the main functions of AD, including on-
prem authentication, object management, and group policies.
AD CS
Active Directory Certificate Services (AD CS) are the services provided for Microsoft environments to deploy digital certificates. Certificates need a Public Key Infrastructure (PKI) to operate and AD CS lays the foundation for Windows admins to build their own PKI.
AD FS
Active Directory Federation Services (AD FS) is the Microsoft component that performs Single-Sign-On (SSO). It provides authentication access for Windows applications that don’t support Integrated Windows
AD RMS
Active Directory Rights Management Services (AD RMS) helps protect sensitive data with information rights management and access policy enforcement. AD RMS controls access to information on Microsoft documents, emails, web pages to protect from outside threats.
Key Takeaways:
- AD DS (Active Directory Domain System) performs the core functions of active directory.
- AD CS (Active Directory Certificate Services) deploys digital certificates by paving the way for Window admins to build their own PKI
- AD FS (Active Directory Federation Services) performs authentication access for Windows applications (SSO).
- AD RMS protects confidential data from outside threats with information rights management and access policy enforcement.
AD Structure
Group Policy
Group Policy is a feature that network admins use to configure and enforce many different Windows settings. Admins use Group Policy to limit network access to users based on their standing in the organization.
For example, an admin can enforce a policy where the company page is the home screen or block access to certain folders.
Objects
In AD, objects can be defined by two categories: resources and security principles. Resources make up devices like printers, fax machines, and the like while security principles make up users, computers, groups, servers, etc.
Each object in an organization is represented by an entity in AD and assigned a name and attributes for identification.
Forests, trees, domain
An AD structure can be broken down into three categories: domain, tree, and forest. To simplify, a domain is a group of objects, a tree is a group of domains, and a forest is a group of trees.
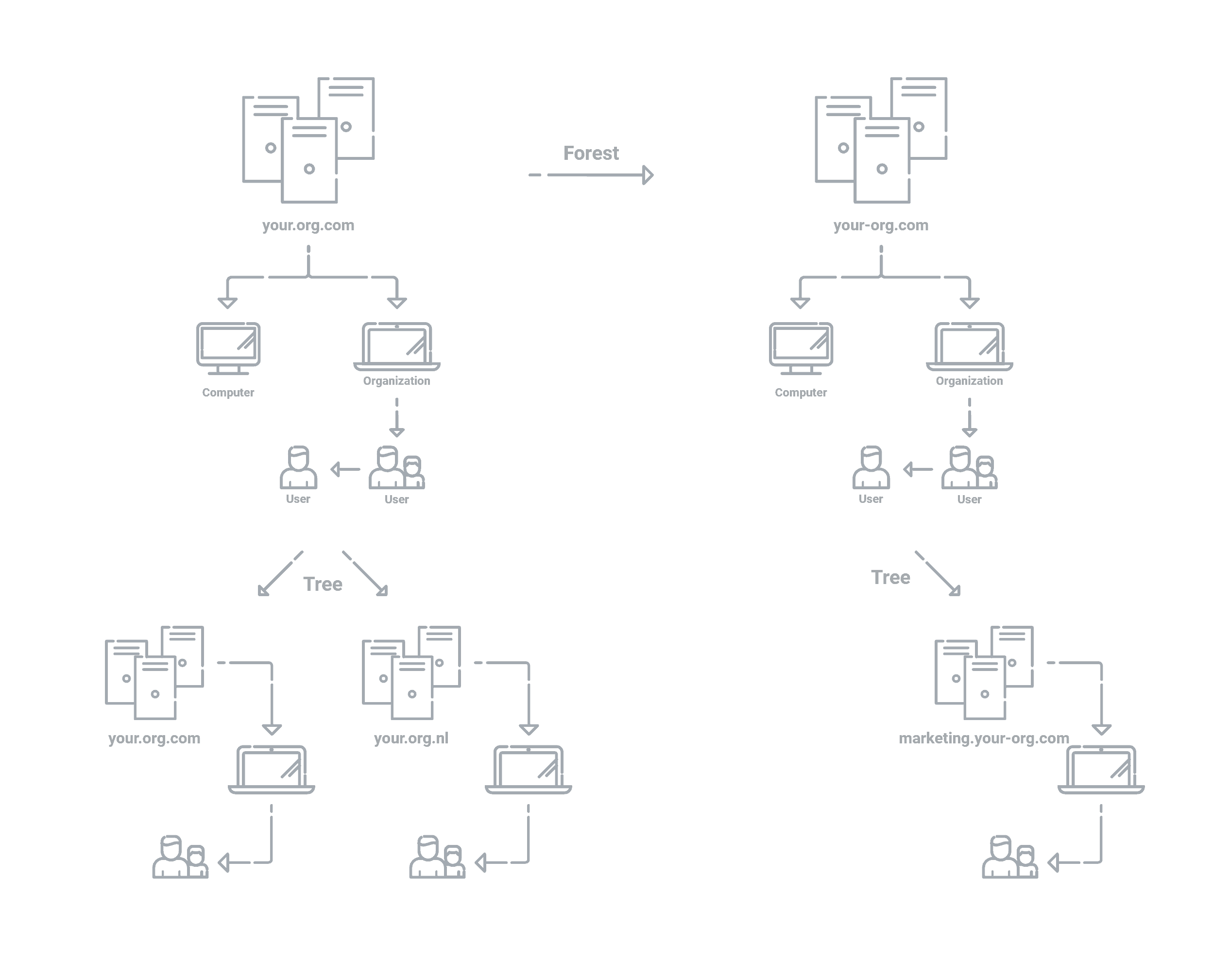
If a new domain is created within a domain, the new domain is referred as the “child” with the other domain being the “parent”.
Organizational Units (OU)
OUs are containers in AD that organize objects within a domain into specific groups. OUs provide a hierarchy within a domain that can mirror an organization’s physical environment. For instance, Company A has offices in several major cities. In an AD structure, the cities are represented by domains, the departments (HR, marketing, sales) are represented by OUs, and the employees are represented by objects.
Trusts
AD Trusts allow domains to communicate with each other and users in one domain to access resources in another domain. A domain establishes trust with another domain and provides permissions to that domain. This describes a one-way trust where one domain can access the resources of another, but not the other way around. Two-way trusts allow both domains to share resources with each other.
Trusts can also be characterized as transitive (extending past two domains) or non-transitive (only between two domains). Parent-child trusts are two-way transitive trusts established when a new domain is added. The child automatically trusts the parent.
Key Takeaways:
- Group policy allows admins to limit network access to users.
- The term “object” in active directory usually refers to resources and security principles.
- AD Trusts allows permissions to users in one domain to access resources in other domains.
AD Ports
Below we’ll cover the network ports used for AD communications. These ports have been categorized into AD replication and authentication to AD servers and applications. In order to enable basic AD communication, admins need to open at least the LDAP port 389 and RPC 445.
AD Replication
These ports when opened enable AD replication across firewalls. AD replications ensure AD information is shared across all domain controllers (DC) and updated. Replicating AD across multiple DCs improves network security because it helps mitigate a security breach.
- RPC endpoint mapper: port 135 TCP
- LDAP: port 389 TCP, UDP
- LDAP over SSL: port 636 TCP
- Global catalog LDAP: port 3268 TCP
- Global catalog LDAP over SSL: port 3269 TCP
- DNS: port 53 TCP, UDP
- Kerberos: port 88 TCP, UDP
- SMB over IP (Microsoft-DS): port 445 TCP
- RPC: Dynamically-assigned ports TCP, unless restricted
Authentication to AD
These are the ports that enable user and computer authentication for AD systems and applications. Authentication is crucial for network security because it ensures that only approved users can access certain network resources. Learn how you can improve AD authentication with Cloud RADIUS.
- SMB over IP (Microsoft-DS): port 445 TCP, UDP
- Kerberos: port 88 TCP, UDP
- LDAP: port 389 UDP
- DNS: port 53 TCP, UDP
- RPC: Dynamically-assigned ports TCP, unless restricted
Key Takeaways:
- LDAP port 389 and RPC 445 are the minimum required ports to enable AD.
- To improve network security, enable AD replication across firewalls as it helps to mitigate a security breach.
AD in the Cloud
Since being rolled out back in 2000, AD has become the most widely used database service due in no small part to Microsoft cornering the software market.
However, AD rose to popularity when on-premise infrastructure was the only option for networks. With the introduction and subsequent rise in cloud computing services, AD has had a difficult time keeping up, resulting in Windows network admins scrambling to find solutions to get their ADs on the cloud.
Microsoft noticed the industry quickly adopting cloud-based services and released Microsoft Azure.
What is Azure AD?
Azure AD (Microsoft Entra ID) was rolled out to help Windows network administrators transition their ADs to the cloud, but don’t be fooled because Azure AD is not the same thing as AD. Compared to AD, Azure AD is much more limited in services provided. For instance, Azure AD doesn’t support LDAP, Kerberos and NTLM authentication, nor group policy.
Azure AD is also limited when it comes to supporting WPA2-Enterprise Wi-Fi and has no real solution for enabling 802.1x authentication, both of which provide the best network security. With cyber security attacks as dangerous as ever, organizations can’t afford to skimp out on security.
LDAP vs SAML
LDAP is designed for on-premise AD infrastructures and serves as the language for AD to speak. Being that LDAP is on-prem, it doesn’t adapt well to an industry adopting cloud-based software. Not even Azure AD supports LDAP, instead using cloud-based SAML technology. Dozens of Windows network admins have been trying to migrate their networks to the cloud, but have been stuck with on-prem hardware with no real solution.
AD with 802.1x and Cloud RADIUS
So if you want to migrate to the cloud and not be stuck with on-prem AD hardware, use Microsoft Azure as a SAML provider. By doing that, you can easily set up a WPA2-Enterprise network equipped with Cloud RADIUS and 802.1x settings. Check out our guide on configuring Azure AD for 802.1x for more info.
Key Takeaways:
- Azure AD offers no native solution for enabling 802.1x authentication.
- LDAP requires on-prem hardware that isn’t conducive to adopting cloud-based software, making it difficult to transition on-prem AD environments to the cloud.
Improving Security for AD with a PKI and Digital Certificates
The best way for admins to configure WPA2-Enterprise, 802.1x, and migrate their networks to the cloud is with digital certificates.
Admins can implement certificates for their environment by equipping them onto every network device and server. After locking into a device, the certificate serves as the identifier for that device or user. Instead of logging on the network with credentials, users will be automatically connected through the certificate.
However, many admins in the past have avoided implementing digital certificates because getting a certificate onto every single device is no small task. Plus, certificates need a PKI which itself requires a team of experts to construct.
What about AD CS?
AD CS does provide admins the ability to build their own PKI, but it’s on-premise. Compared to cloud-based PKIs, on-prem PKIs are more expensive, harder to implement, and not as secure.
On-premise PKIs come with a plethora of individual expenses, including software and hardware licensing, maintenance fees, secure storage, data backup, disaster recovery, and much more. Plus, organizations will have to hire and train an entire team of PKI experts.
Overall, organizations end up spending hundreds of thousands of dollars every year for an on-premise PKI that offers subpar network security. It’s also impossible to equip every network device with a digital certificate because AD CS doesn’t work with non-Windows devices.
Configuring AD with a Managed Cloud PKI
Luckily, SecureW2 offers a Managed PKI service that fits into any Azure environment. Integrating Azure with SecureW2 allows Windows admins to deploy WPA2-Enterprise and 802.1x for Wi-Fi, VPN, web apps, and much more.
SecureW2’s software is built to run on certificate-based EAP-TLS authentication, using certificates instead of credentials to authenticate users. This eliminates the threat of over-the-air credential theft because EAP-TLS encrypts the server-client connection, preventing any outside threats from infiltrating. Plus, SecureW2 provides Server Certificate Validation, meaning both the client and server are equipped with certificates. The device will always know which RADIUS server is the correct one.
Key Takeaways:
- AD CS requires on-premise hardware, making it a poor option for certificate-based authentication to cloud directories like Azure AD.
- Windows admins can easily integrate Azure AD with SecureW2’s Managed PKI to enable certificate authentication on WPA2-Enterprise networks.
Configuring AD-Domain Devices with Certificates
SecureW2’s PKI is a turnkey solution that allows every network device (managed and BYOD) to safely authenticate and access the network. Users only need to enter their AD credentials once at the beginning and the device is set for life.
Managed Devices
SecureW2 gives Windows admins the ability to build SCEP gateway APIs for certificate enrollment. Instead of manually configuring every device, admins can configure a SCEP gateway to push out payloads that enable managed devices to configure themselves for certificate enrollment.
BYODs
Non-Windows devices can also connect to the network easily with our JoinNow onboarding software. By downloading the JoinNow app, users can self-service their devices to be configured for 802.1x and equipped with a certificate.
Setting Up AD with RADIUS
The RADIUS server is an important part of network security because it’s the entrance for connecting devices and where cyber attacks attempt to infiltrate. RADIUS authenticates users attempting to connect, so the server needs access to AD.
NPS integration
Most RADIUS implementations in Windows are done with Microsoft Network Policy Server (NPS). While it’s intended purpose is to enforce network access policies on any level, NPS is commonly used either as a RADIUS server or a proxy that connects to a third party server. Many Windows admins also use NPS as a workaround for client authentication by tying it with AD to authenticate clients against.
However, NPS and AD connection is an on-prem legacy service, thus does not support cloud-based technologies. There are no native ability to connect with cloud directories, so admins will need to connect a third-part cloud-based RADIUS.
Cloud RADIUS for AD through Azure
SecureW2 can partner with Microsoft Azure for flawless wireless security and efficient network authentication. By itself, implementing Azure is an enormous task that requires stripping down your current infrastructure and build from the ground up. Admins need to maintain network security, re-enroll every user and device, and successfully transition without network downtime.
Fortunately, Cloud RADIUS simplifies this process because it’s a turnkey solution that will help transition your environment from on-prem to the cloud without any forklift upgrades. Our RADIUS software has helped countless organizations migrate to an all-cloud environment with Azure.
Cloud RADIUS offers an exclusive Dynamic Policy Engine that integrates natively with Azure and performs run-time level policy decisions based on dynamic user attributes. Standard issued certificates are static, meaning you can’t edit permissions. If admins need to change user attributes, they’d have to revoke the old certificate, create a new one, sign it, and distribute to the user. Dynamic RADIUS takes that away by allowing admins to edit the user’s attributes instead of going through the certificate management process.
Key Takeaways:
- As NPS and AD Connection are on-prem services, you need a third party RADIUS like our Cloud RADIUS to connect to a cloud directory like Azure AD.
Secure Your AD with a PKI
Active Directory has been around forever and plays a critical role for Windows environments. But with an industry rapidly adopting cloud-based technologies, Windows admins are getting stuck attempting to update their AD. On-prem technology just doesn’t offer the same versatility or security, which is why many admins are looking to Azure and Azure AD.
By integrating Azure AD with SecureW2’s PKI and Cloud RADIUS, organizations can implement WPA2-Enterprise and 802.1x certificate-based authentication. SecureW2 offers solutions for organizations of all sizes and comes at an incredibly affordable price.