Key Points
- The primary purpose of a PKI is to manage digital certificates They are a powerful security tool that supports numerous operations.
- It is possible to create your PKI without external help, but that could lead to network misconfiguration. Misconfigured certificates in a network do more harm than good, as they can leave your network vulnerable to MITM and brute-force attacks.
- A managed PKI like our JoinNow Connector PKI provides an automated certificate management platform, so you can provision all your end users and devices with digital certificates and authenticate them safely to the network.
Corporate data, social media pages, applications, and user data are crucial assets of an organization, and any theft or misuse of these could lead to huge financial losses. They not only result in loss of business opportunities, but organizations are also liable for hefty fines for violating data privacy and overlooking the need for data protection.
Unidentified users and devices on a network are the biggest reasons for data theft and misuse by malicious actors. The downside of detecting a network breach late is that the hacker would have gained access by the time he is detected. The best way to prevent malicious users or devices from accessing your network is to identify all the users and devices on your network through a well-established Public Key Infrastructure (PKI).
However, a PKI is generally expensive to set up and maintain. If you want to set up a hassle-free PKI solution for your network, this article is for you. Read to know more about PKI and how you can leverage PKI with digital certificates to secure your network.
What is a Public Key Infrastructure (PKI)?
A well-established Public Key Infrastructure (PKI) is integral to data security, network integrity, and privileged access control for secure communication between users, devices, and a network. A PKI lets you issue and manage digital certificates that can be used to authenticate users and devices to a network. Digital certificates (public key certificates) can also be issued for web pages and servers to verify their authenticity.
- A Certificate to authorize access to applications on a server.
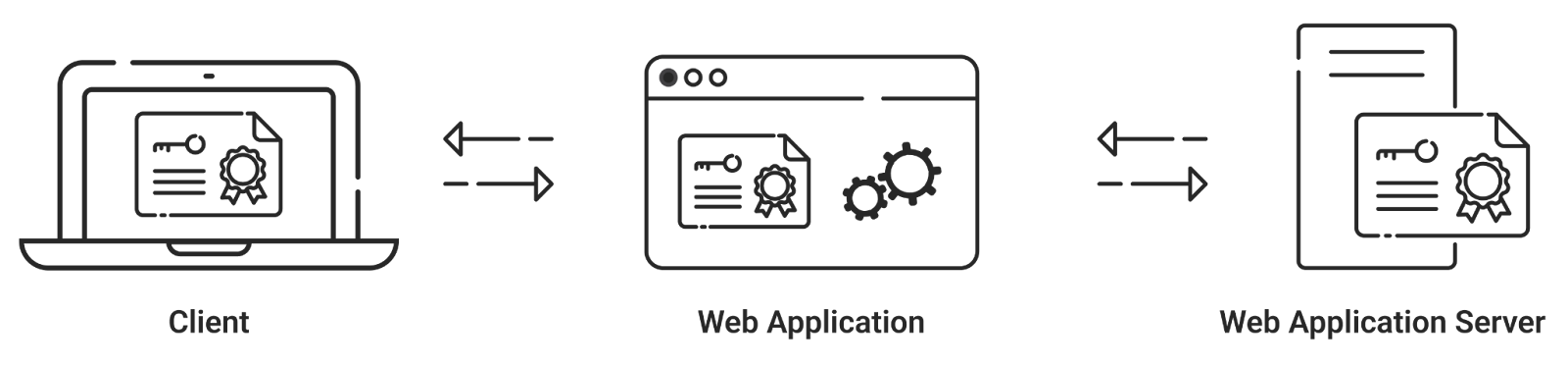
How Does a PKI Work?
A PKI provides a secure way to exchange information on a network with digital certificates through public-private key encryption that ensures confidentiality and authenticity of the data transmitted over a user, device, and the internet. A PKI uses private and public keys wherein the public key is kept with a user or a device, and the private key is a secret key used to decrypt information. A digital certificate authenticates the public keys and is issued by a trusted certificate authority (CA) to verify user or device identity.
When two parties try to establish communication, they use the public key to encrypt data, making sure only the intended recipient with a private key can decrypt the secret message. An SSL certificate, often used by websites, is also presented to a browser against a list of certificates issued by a trusted CA. If a website proves legitimate, the user certificate establishes secure communication between the user and the website for secure transactions.
What are Digital Certificates?
A PKI or digital X.509 certificate contains digital signatures similar to an identity card or driver’s license and can be used as a digital identity. They are used to ascertain the identity of a user, device, or server by signing codes and documents over an untrustworthy network. It also encrypts data and communication.
A PKI or digital certificate uses public-key cryptography that leverages public and private keys to identify who owns the public key. It stores information about the public key owner and pertinent data along with the public key. The purpose of a digital X.509 certificate is to act as a gatekeeper to secure shared digital information. There are several types of certificates, but the two most common broad types we see used are the following:
- SSL/TLS Certificates
- Client Certificates
Server (SSL) Certificates
An SSL/TLS certificate authenticates an online server’s identity by changing the website protocol from HTTP to HTTPS. An SSL certificate encrypts any information sent to the server from a user and protects it from unauthorized access. A CA is a trusted third party, that issues an SSL certificate after validating that it matches the issuer and server identity. Upon verification of the SSL certificate, the user can access the website as a secure communication has been established.
If you want to check the security of any website, you can click on “Settings”, choose “Connection is secure,” and click on “Certificate is valid” to view the website’s SSL certificate.
Client Certificates
Client certificates contain unique information and attributes about a device or a user that helps authenticate them to a server. A Client certificate validates and verifies a user or device against an identity provider and authenticates them to use specific resources like applications, websites, or more. Client certificates offer more security than passwords as they are phishing-resistant and cannot be cracked through brute force or MITM attacks. They are considered the best choice for organizations looking at robust and foolproof mechanisms to secure their network.
What is a Certificate Authority in A PKI?
A certificate signing process commences when a client generates public and private keys. The certificate is signed with a private key and sent to the CA to generate an X.509 certificate. A PKI contains the framework for a certificate signing request (CSR), and it helps users and servers get digital certificates like SSL and TLS certificates. A CSR is sent to the CA to obtain a Digital certificate. It contains the public key, domain name, and the signatures needed for a new certificate. Upon verification, the CA sends the certificate to the applicant.
What Are Root CAs and Intermediate CAs?
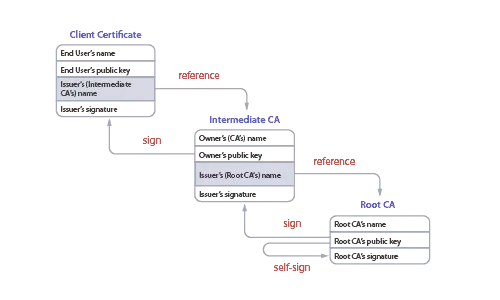
The Root CA is the most trusted entity in a PKI as it verifies the identity of a user and signs the certificate. If the root CA is compromised, the whole PKI is at risk of attacks and unauthorized access. Thus, the root CA’s certificates are not issued to the end clients. Root certificates are issued to the intermediate CA, which issues the end-user certificates.
The Intermediate CA is trusted and forms the chain of trust between the Root CA and the end-user certificate. The Root CA is signed and passed on to the Intermediate CA, thus passing the baton of trust to the Intermediate CA. Any certificates issued by the Intermediate CA are as safe as if they were signed by the Root CA. Organizations should consider creating an Intermediate CA as a best practice for distributing end-user certificates.
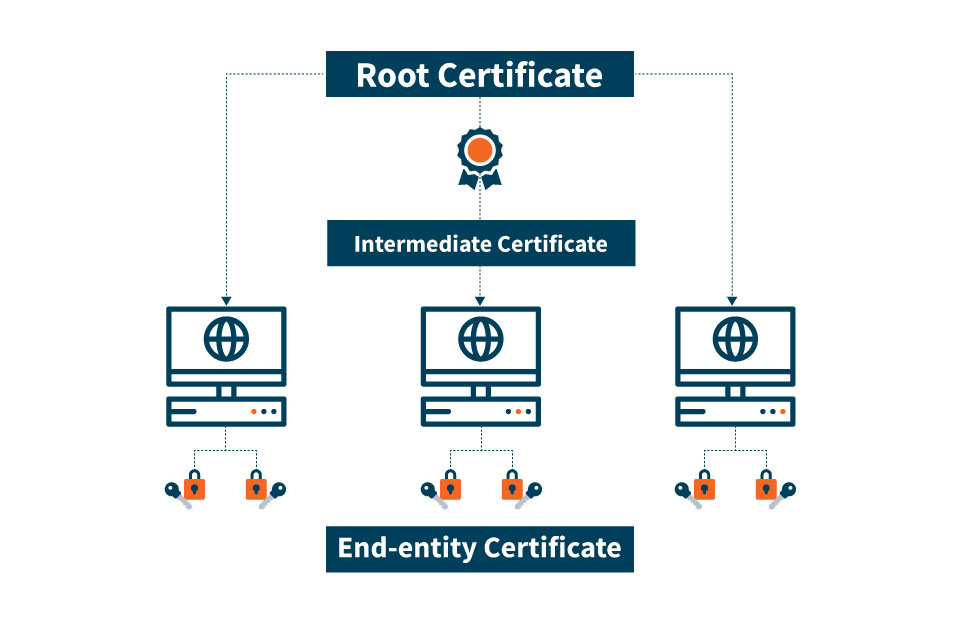
Image Courtesy: Sectigo
Understanding the Certificate Lifecycle Process
Certificate-based authentication requires a Public Key Infrastructure setup (PKI) and a RADIUS server with a typical lifecycle of
- Enrollment
- Issuance
- Validation
- Revocation
- Renewal
Certificate Enrollment
The first stage of the Certificate lifecycle starts with user enrollment, where every user or device must enroll for an X.509 certificate. This certificate has unique attributes about every user and device, making it difficult for malicious hackers to steal or misuse. Certificate management services make enrolling for certificates easy for users and devices. They provide easy user interfaces so that a user can self-enroll for certificates through SSIDs.
If the user has a managed device, the MDM prompts the device to enroll for a new certificate via device gateway API like SCEP, JSON, and WSTEP. A device can configure itself for EAP-TLS and certificates without any input from the user.
Certificate Issuance
The next stage in a certificate lifecycle is distributing certificates to end users and devices in an organization. An admin can manage certificate distribution in small organizations. However, manual certificate distribution is cumbersome for bigger organizations. Thus, a PKI automates the certificate issuance through onboarding software that issues certificates seamlessly to all users and devices.
Certificate Validation
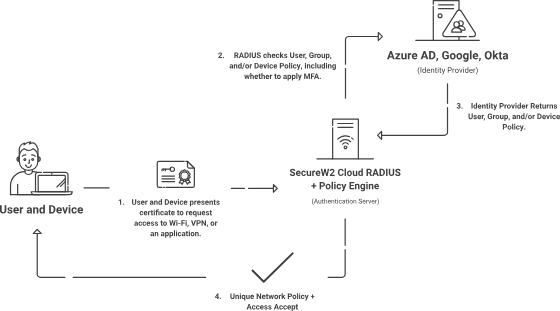
The third step is Certificate validation, where issued certificate authentication happens numerous times daily. The authentication process varies depending on what the certificate is being used for. In Wi-Fi authentication, for example, certificates can be authenticated through the EAP-TLS protocol, which is highly recommended for WPA2-Enterprise networks.
SecureW2 also provides the option of performing Dynamic RADIUS authentication. With real-time identity lookup, Cloud RADIUS can communicate with major SAML Identity Providers such as Azure AD/Entra ID, Google, OneLogin, and Okta to apply the most current network access policies to users as they authenticate.
Certificate Revocation
Lastly, certificate revocation is an essential step in the certificate management process, as unrevoked certificates pose a considerable security threat by enabling unauthorized users to access applications on the network.
SecureW2 Managed Gateway API uses a Certificate Revocation List (CRL) that makes certificate revocation easier in JAMF and Intune-managed devices based on specific groups in these MDMs.
Certificate Renewal
Once an existing certificate is revoked because it has expired or been revoked, renewal of certificates becomes necessary. However, this can often be challenging if the lifecycle has to be managed manually. Suppose you want to enhance your network security by renewing certificates later. Doing it manually can be a nightmare, especially in an enterprise network. Using a certificate management system (CMS) to automate the entire certificate lifecycle management process can help make it a more efficient ecosystem.
How Do Certificates Enable Network Access?
Digital X.509 certificates enable policy-based network access for managed and unmanaged devices as they integrate with RADIUS servers and access control systems. A certificate contains device and user identity information and is used to authenticate devices or Users that want to connect to a network. At the time of authentication, Cloud RADIUS can use the information on a certificate to see which group a user or device belongs to and apply the correct policy based on existing policies in your Identity Provider.
An example of a common network access policy RADIUS can enforce is VLAN segmentation by group, such as putting different departments on their VLANs.
The RADIUS server is critical in implementing roles and policy-based network access. The RADIUS server checks the information on a certificate before authenticating devices and allowing them access to the network. The RADIUS server also checks the validity of the certificates and ensures the information matches the role-based policies given for network access.
Implement SecureW2’s PKI for Certificate-based Network Authentication
Organizations are increasingly going passwordless in implementing a zero-trust network architecture to safeguard their network. The need to go passwordless has led organizations to embrace means like digital certificates to provide robust network security. However, implementing certificate-based authentication requires a managed PKI to make it manageable and effective.
SecureW2s Managed Gateway API is the perfect solution for implementing a fully passwordless solution for your organization. Our PKi solution works with any existing identity provider and MDM solution to seamlessly issue certificates to users and devices quickly without needing extra upgrades. The user friendly onboarding process also makes certificate management simpler and effortless for all.
The powerful Cloud RADIUS also authenticates each user and device based on certificates using the robust EAP-TLS protocol, which is considered the gold network security standard. Cloud RADIUS also provides real-time look-up with significant identity providers like OKTA and Azure AD/Entra ID for a complete passwordless security solution.
Click here to learn more about our passwordless solutions for your network.