Key Points
- Hackers develop fake Wi-Fi networks that appear genuine and deceive users into connecting and collecting critical data. These attacks typically target public areas, such as cafés and airports.
- The most effective technique to prevent evil twin attacks is to use Server Certificate Validation (SCV) and EAP-TLS authentication, which ensure that devices only connect to trustworthy networks. A complete EAP-TLS solution, such as our RADIUS and PKI services, facilitates setup and management.
- MultiOS assists users in configuring unmanaged devices for 802.1x, ensuring they do not overlook essential security settings such as Server Certificate Validation.
- Avoid using public Wi-Fi for important work, create strong passwords, keep your electronic devices up to date, and use a VPN to encrypt your connection.
- Turn off automatic Wi-Fi connections, double-check network names before connecting, and be wary of login screens that prompt for credentials.
Imagine you’re out shopping, getting coffee, or waiting for a flight. You quickly want to check your messages or search for something, so hop on a free public Wi-Fi network. But what if that network was only there to gather your information?
Hackers can create false Wi-Fi networks that look authentic and fool users into connecting. Everything you do on their network, from signing into accounts to entering sensitive information, is visible to them. As more individuals work remotely and rely on public Wi-Fi, these attacks, known as “evil twin” attacks, are spreading.
Understanding how evil twin attacks operate and how to protect yourself might help you stay secure while remaining connected.
Learn more about different Wi-Fi hacks and effective ways to prevent them.
What is an Evil Twin Attack?
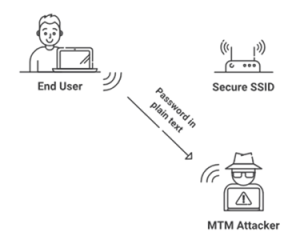
An evil twin attack is when an attacker sets up a fake Wi-Fi access point that looks identical to a legitimate one and tricks users into connecting. Once connected, all the data they send and receive passes through a server controlled by the attacker. This allows the attacker to intercept sensitive information like login credentials and personal data. Attackers can create an evil twin using readily available software and devices, including smartphones. These attacks are especially prevalent on public Wi-Fi networks, which are often unencrypted, making it easier for attackers to exploit unsuspecting users.

Evil twin attacks are dangerous because, if they are successful, they give hackers direct access to your device. This allows them to steal login credentials, financial data, and other sensitive information. Additionally, attackers can use the connection to install malware on your device. Attackers often use malware to maintain long-term access, steal more data, or even move into your corporate networks laterally. The risks go far beyond the initial attack from keyloggers that capture every password you type to remote access trojans (RATs) that give attackers control over your device. Once infected, your device could also be used to spread malware, mine cryptocurrency, or even launch more extensive cyberattacks—all without you realizing it.
How Do Evil Twin Attacks Work?
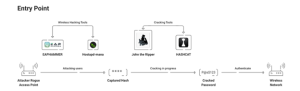
Target high-traffic areas
Evil twin attacks are frequently carried out in popular public spaces such as cafés, libraries, and airports, where Wi-Fi networks might have identical names. This makes it easier for a fake network to blend in and avoid detection.
Imitate a WiFi Network
Attackers copy the name (SSID) of a valid Wi-Fi network, making it virtually impossible for users to distinguish between genuine or fraudulent connections. These networks can be created using easily accessible technology, including cell phones, laptops, and portable routers.
Lure Users to Join The Network
The fake network might show a stronger WiFi signal than the real network, making it a favored option for unsuspecting consumers.
Mimic the Login Page
Many public Wi-Fi networks require users to sign in via a captive portal. Attackers can easily recreate these login screens to deceive users into entering their credentials, which can then be stolen.
Intercept Sensitive Information
Once connected, the data transferred over the network is routed through the attacker’s machine. This allows them to track behavior, steal login information, and even implant malware on the victim’s device. If a user connects to a sensitive account, the attacker may get access to personal or financial information.
Best Practices To Keep Yourself Safe From An Evil Twin Attack
While public WiFi is convenient, it is critical to be careful and take precautions to reduce the risk of falling victim to an evil twin attack. Here are some tips to protect yourself and your devices:
1. Network Awareness and Assessment
Disable automatic WiFi Connections: Configure your devices not automatically to connect to accessible WiFi networks. This allows you to carefully evaluate and select the correct network name before connecting.
Examine Network Names: Be aware of WiFi network names that closely resemble legal ones, particularly those that include mistakes or additional letters. Hackers sometimes utilize slight differences to deceive users. Look for continuity in the establishment’s name or signage.
Verify Network Security (if applicable): Even if a public network requires a password, you should proceed with care. While a password may not provide total protection, it might dissuade casual efforts by intruders. Specific devices allow you to see details about linked networks. Look for discrepancies in network encryption (WPA2 is preferred over WEP) or unusual network addresses that do not correspond to the establishment’s location. While not infallible, this information should raise red flags.
Use Server Certificate Validation (for 802.1x Networks): If you are utilising a credential-based 802.1x network, make sure server certificate validation is enabled. This keeps attackers from mimicking genuine access points.
Use EAP-TLS: The most secure way to guard against evil twin attacks is to use EAP-TLS authentication, which eliminates credential-based vulnerabilities in favour of certificate-based authentication.
2. Mitigating Damage If You Connect to a Malicious Network
Software Updates: Make sure you regularly complete software updates on all your devices, including operating systems, browsers, and security apps. Updates often address vulnerabilities that hackers use to gain access to your device or network.
Strong Passwords and Password Managers: Create strong, unique passwords for your online accounts. A password manager allows you to generate and maintain complicated passwords across several platforms. Avoid using the same password on several accounts.
Antivirus and Anti-malware Software: Consider installing a reliable antivirus and anti-malware package on your devices. These tools assist in detecting and blocking malicious software that may be inserted as part of an evil twin assault.
3. Securing Your Data on Public Networks
Enable Multi-Factor Authentication: Even if your login information is compromised, MFA provides an extra layer of security by requiring a second verification step, such as a number delivered to your phone or biometric authentication. This might help you avoid unauthorized access to your accounts.
Use a Virtual Private Network (VPN): Consider using a trusted VPN provider, particularly on public WiFi. A VPN encrypts your internet traffic, making it more difficult for attackers to intercept your information, even if they fool you into connecting to a false network. Select a VPN service with a solid reputation for security and privacy.